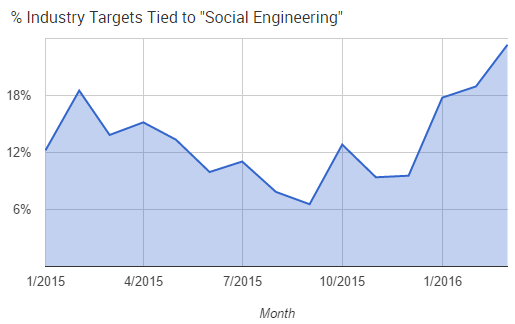
We’re already a quarter of the way through 2016, and a clear trend is the rise of social engineering. Based on the cyber event data that we’ve collected, roughly 25% of all targets can be tied to a social engineering attack. This is the highest percent we’ve seen since the beginning of 2015, and over the last 6 months the share of social engineering attacks have doubled.
Just a few examples of common social engineering practices include:
- Phone calls from a “Microsoft customer support representative” who needs remote access to your computer to fix an issue
- Leaving an infected USB stick in a parking lot that when found and inserted into a computer by an unsuspecting person, malware/spyware is dropped onto the machine
However, the largest percentage of social engineering attacks (25%+) revolve around different types of phishing. While email is the most common delivery method, phishing attempts are made through text messages, Facebook, etc.
Over the weekend I received several phishing emails from individuals I know. These emails weren’t spoofed to make it look like they were coming from people I know, but actually sent from their email accounts without their knowledge.
The emails were both related to a “signed document” that needed my attention — except I had no previous knowledge any e-docs to sign should be coming my way. Of course, that’s because they should not have been coming at all.
Having been in the security industry as long as I have, I am cautious (or some would say paranoid) — especially compared to friends and family who say they “get it,” but don’t really. Even still, these emails came from legit addresses from people within my circle, and the content within the emails also looked reasonable. Luckily, I knew better, but many don’t.
Here are some quick security tips to consider when it comes to phishing attacks:
- Watch out for spoofed email addresses. Confirm the sender of the email is an address you recognize/know. Don’t just check the name in the “From” field, but actually look at the email address. This tip would not have made a difference in the instance above, but it is still a good way to catch a phishing email.
- Do not blindly trust links within an email. Banks and credit cards are usually pretty good about directing you to type in the url to go to their homepage and how to navigate to a specific place if necessary, as opposed to including links in their communications to you. This is a good practice to follow with any emails that include links. In my situation the links sent looked like DocuSign links, with familiar DocuSign branding and all. But it was missing the security code. Links can also be spoofed, so make sure you know what it is you are clicking on before you click.
- If you have any questions, pick up the phone. Is a vendor asking you to provide information or is a contact of yours asking you to click on a link? Questioning it is good. Call the vendor or individual and have them confirm.
Social engineering is one of the trickiest types of attacks to prevent because it plays on human nature and less on technology. Looking at the intel so far in 2016, the bad guys are going back to a tried and true method for gaining access to sensitive information. Be aware and think before you click.


The other day a Facebook friend of mine sent me a message asking for a favor. I said “of course, how can I help you?” The friend responded with a link for me to click on, saying it was “very important” that I click on the link to help her out. I told this friend if they could tell me how we knew each other I would click on the link. They didn’t respond. I immediately notified my friend that their account was hacked.
LikeLike