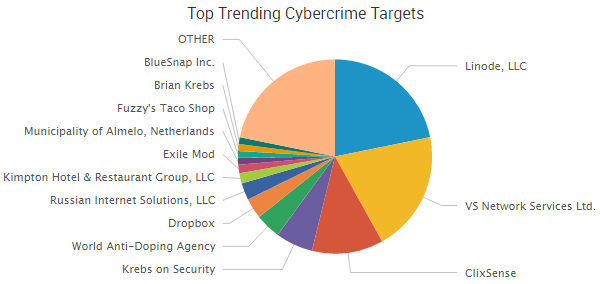
Three of this week’s top four trending industry targets centered around DDoS attacks. Linode, which made last week’s roundup over reported DDoS attacks, was targeted once again. The cloud hosting company has seen DDoS attacks throughout the month, with the latest attack coming on September 13, according to company logs. Additionally, Brian Krebs’ website was hit with DDoS attacks after his reporting on the booter service VDoS led to the arrest of two young Israeli men who allegedly ran the cybercrime-as-a-service operation.
Trending new data breaches and cyber-attacks recently observed in SurfWatch Labs’ data are shown below.
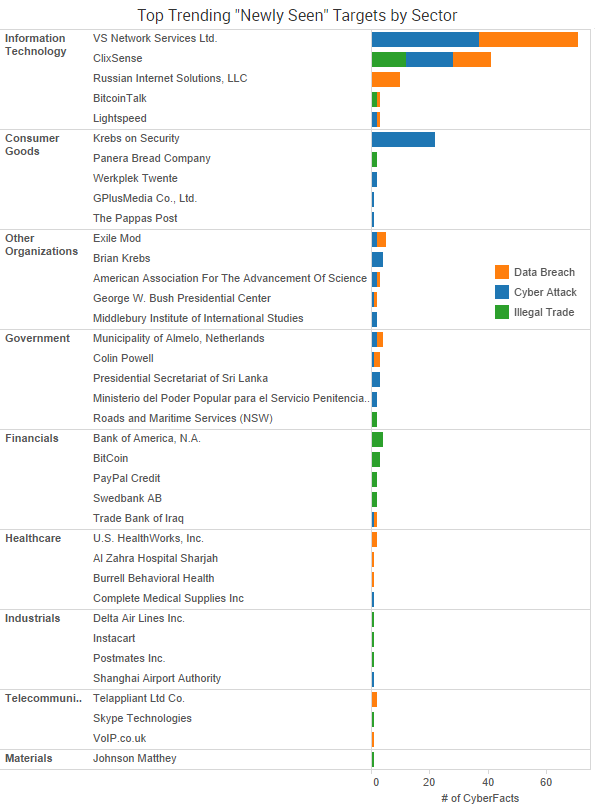
Noteworthy cybercrime events from the past week include:
- Variety of New Breaches Reported: Dutch news sources are reporting that hackers have stolen 22 gigabytes of data from municipal servers in Almelo, though at the moment it is unclear what data may have been compromised. London-based VoIP Talk is emailing customers about a potential breach after discovering “attempts to exploit vulnerabilities in our infrastructure to obtain customer data.” The paid-to-click site ClixSense suffered a data breach in which a hacker exposed 2.2 million subscriber identities and put another 4.4 million up for sale. The Exile Mod gaming forum website was hacked and the personal details of nearly 12,000 users was posted online by a group going by the name “Expl.oit.” EurekAlert!, which is used to distribute scientific press releases, temporarily shut down their website after a breach compromised usernames and passwords and two embargoed news releases were prematurely released. The personal information of 29 Olympic athletes has been stolen from the World Anti-Doping Administration. Finally, a data breach at Regpack, an online enrollment platform serving the private education industry, has led to 324,000 people having personal information exposed.
- More Extortion Attacks: A hacker attempted to extort Bremerton Housing Authority in Washington for 6 bitcoins (around $3,700) after gaining access to its website and stealing a database of 1,100 client names and the last four digits of Social Security numbers. University Gastroenterology in Rhode Island is notifying patients of a data breach after what sounds like a ransomware attack. In its notification letter, it wrote that an unauthorized individual had gained access to an electronic file storage system from Consultants in Gastroenterology, which it acquired in 2014, and “encrypted several files.”
- Political Parties Continue to be Targeted: State Democratic Party officials are being breached and impersonated by hackers, according to a warning from the Association of State Democratic Chairs. The message urged recipients to avoid searching the leaked DNC information posted by WikiLeaks due to concerns over malware being embedded in the links. Additionally, a “serious misconfiguration” on Donald Trump’s website exposed the resumes of prospective interns, according to security researcher Chris Vickery.
- Stolen Laptops Continue: M Holdings Securities, a subsidiary of M Financial Holdings, had a password-protected laptop with information on 20,000 clients stolen from the trunk of an employee’s car on July 29. Roughly 2,000 of those clients had Social Security numbers potentially compromised. U.S. Healthworks began notifying 1,400 patients of a data breach earlier this month after a laptop and the laptop’s password were stolen from an employee.
Other Noteable Cyber Risk News
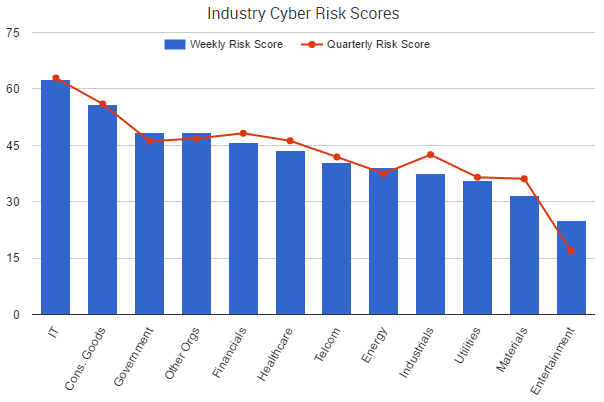
This week saw little movement among most sectors’ overall cyber risk scores. Other Organizations – which includes groups such as political parties, schools, and charities – saw the week’s biggest rise in risk, up 1.6%.
Ransomware was at the forefront of much of the week’s cybercrime news. CBC News reported that a school board and a support group for cancer patients, both in Canada, were infected with the Zepto ransomware, and the actor behind the attack demanded $20,000 in payment to decrypt the files. Those high prices may become more commonplace, the FBI warned in an alert published on Thursday. Recent ransomware variants have been seen targeting vulnerable business servers rather than individual users, and the actors behind these targeted attacks have been upping their ransom demands as the data they encrypt grows more valuable.
“This recent technique of targeting host servers and systems could translate into victims paying more to get their decryption keys, a prolonged recovery time, and the possibility that victims will not obtain full decryption of their files,” the alert warns. “Recent victims who have been infected with these types of ransomware variants have not been provided the decryption keys for all their files after paying the ransom, and some have been extorted for even more money after payment.”
The FBI isn’t the only government agency warning of the threat. In July, the Department of Health and Human Service stated that PHI being encrypted by ransomware qualifies as a “breach” in most circumstances, and FTC chairwoman Edith Ramirez warned this week that “a company’s unreasonable failure to patch vulnerabilities known to be exploited by ransomware might violate the FTC Act.”
It’s worth taking a moment to review this week’s advice on combatting ransomware from the FBI alert:
- Regularly back up data and verify the integrity of those backups. Backups are critical in ransomware incidents; if you are infected, backups may be the best way to recover your critical data.
- Secure your backups. Ensure backups are not connected to the computers and networks they are backing up. Examples might include securing backups in the cloud or physically storing them offline. It should be noted, some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real-time, also known as persistent synchronization.
- Scrutinize links contained in e-mails and do not open attachments included in unsolicited e-mails.
- Only download software – especially free software – from sites you know and trust. When possible, verify the integrity of the software through a digital signature prior to execution.
- Ensure application patches for the operating system, software, and firmware are up to date, including Adobe Flash, Java, Web browsers, etc.
- Ensure anti-virus and anti-malware solutions are set to automatically update and regular scans are conducted.
- Disable macro scripts from files transmitted via e-mail. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full Office Suite applications.
- Implement software restrictions or other controls to prevent the execution of programs in common ransomware locations, such as temporary folders supporting popular Internet browsers, or compression/decompression programs, including those located in the AppData/LocalAppData folder.
Tracking the exact number of ransomware victims is difficult, the FBI said, since many attacks go unreported. The FBI is urging victims to report ransomware incidents regardless of the outcome so that they can better understand who is behind the attacks and how they operate.


Great round up…..
I will say I like the way the VOIP TALK Data Breach was handled. They still can’t confirm there was a breach, but the second they learnt there was the possibility of one what did they do? They did the right thing and emailed everyone of their suspicions. Why oh why could Yahoo not do the exact same thing. Seriously?
In many ways, I’m hoping that VOIP talk hasn’t been breached. I’m a happy customer and now a loyal one because they had the guts and decency to find out about the possible breach from them and NOT the news
LikeLike