Effective cyber threat intelligence is largely about gaining proper context around the risks facing your organization. As SurfWatch Labs chief security strategist Adam Meyer recently wrote, there are three pillars when it comes to evaluating those cyber threats: capability, intent and opportunity.
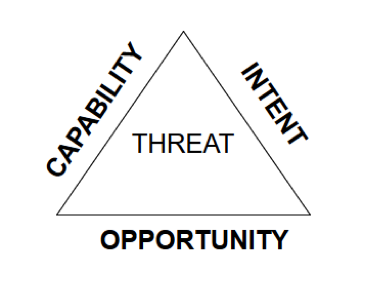 The first two, the capability and intent of threat actors, are mostly external aspects that you have no control over, but the third pillar, the opportunity for actors to exploit your organization, is something that can be controlled, evaluated and improved upon.
The first two, the capability and intent of threat actors, are mostly external aspects that you have no control over, but the third pillar, the opportunity for actors to exploit your organization, is something that can be controlled, evaluated and improved upon.
Malicious actors are relentless when it comes to finding information on that opportunity, and organizations need to use that same relentlessness when searching for potential weaknesses in their cybersecurity, according to a recent report from SurfWatch Labs.
“Knowing where attackers get their information and how they use it is an important piece of your overall cybersecurity strategy,” noted the paper, Top Sources of Information for Cyber Criminals: Where the Bad Guys Go to Conduct Research on Their Targets.
Over the past few months on this blog, we’ve profiled some of the top cyber threats and items for sale on various dark web marketplaces, but not all malicious activity occurs on this “underground web.” Much of it can be found wide out in the open — using simple tools and services that are available to anyone. Here are the top three public websites and tools used by malicious actors, as described in the paper, and how they can help those actors find the opportunity to attack your organization.
1. Shodan
Shodan was originally launched in 2009 by developer John Matherly and bills itself as “the world’s first search engine for Internet-connected devices.” This simple idea has grown from a basic list of IPs and ports to maps showing where devices are located to screenshots taken from these devices (including webcams, unsecured servers and workstations). The original focus for Matherly’s scans was to highlight the growing problem of the “Internet of Things,” but his research also uncovered industrial control systems, wide open computer systems, unsecured security cameras and more.
Researchers using Shodan frequently find publicly-exposed data that leads to breach notifications. Just one example is MacKeeper security researcher Chris Vickery discovering personal information from child tracking platform uKnowKids earlier this year.
“One of the uKnowKids databases was configured for public access, requiring no level of authentication or password and providing no protection at all for this data,” Vickery wrote. “There’s no way for me to know for sure how long this data was exposed to the public internet, although the information collected by Shodan.io suggests that the database had been up for at least 48 days.”
uKnowKids CEO Steve Woda reacted by describing Vickery as a hacker whose method “puts customer data and intellectual property at risk.” However, malicious actors can just as easily utilize Shodan to find opportunity for attacks.
As SurfWatch Labs’ paper summarized: “If it’s online, Shodan will find it. The lesson to be learned from this site, without a doubt, is secure something before it goes online.”
2. VirusTotal
VirusTotal describes itself as “a free service that analyzes suspicious files and URLs and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware.” But that simple tagline masks a deeper set of capabilities.

Security researchers have previously suspected that malicious actors use VirusTotal as a tool to help test and hone malware before sending it out in the wild, and in 2014 researcher Brandon Dixon confirmed those suspicions by discovering several hacking groups using the tool, including two nation-state groups.
Dixon said nation-state actors using a free online service to fine-tune their attacks was ironic and unexpected, but that speaks to the usefulness of VirusTotal.
“The power behind VirusTotal is how it adds and saves the metadata and behaviors of the files it analyzes,” noted SurfWatch Labs’ paper. “You can use the domain search to look at the IP history of the domain and get the current WHOIS for the domain, but VirusTotal will also show you a list of every time it detected something malicious on the site, as well as list all of the samples that attempted to communicate with the searched for domain.”
In addition to organizations using VirusTotal to help identify if they’ve been previously targeted, VirusTotal should be seen as a baseline site that can be used for detecting and analyzing suspicious and malicious files.
3. Your Own Company Website
The best way to get information about a particular company is often directly from the source: your own company website. Company websites can provide a treasure trove of information that can be leveraged by attackers to target a specific organization. This includes names of VIPs, email addresses of company executives and other employees, photographs, links to LinkedIn profiles and other social media, and more.
But beyond the surface level, there may be even more valuable information, as the paper explained:
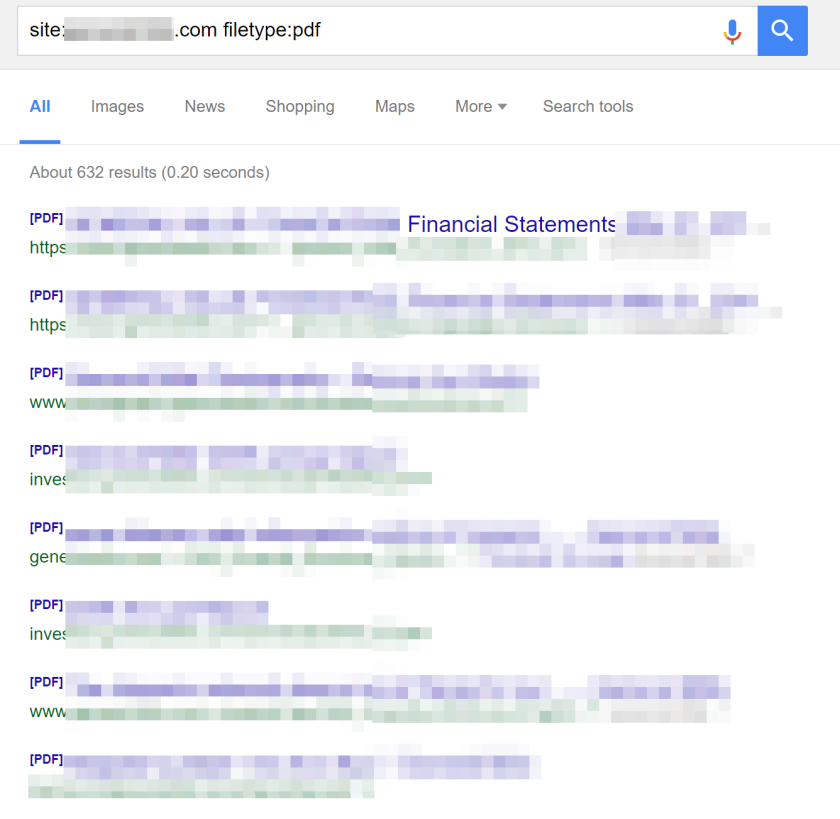
Are you hosting any PDFs for people to download? Word documents, or PowerPoint presentations? Did you remember to remove potential metadata from those documents that could potentially contain additional names, email addresses, usernames, or software versions of the program used to create it? Some pretty simple Google searches (just type “site:yourpublicsite.com filetype:pdf” into the google search box) can reveal much more information that you may not have been aware you were “leaking.”
These types of leaks can lead to costly data breaches.
Free tools and services such as the ones described above provide malicious actors with valuable insight into the opportunity for cyber-attacks, and they are certainly one of the first places those actors turn to gather information on your organization. To make matters worse, all of this information can be discovered with minimal effort or expertise.
The good news is that those same tools can be used to gather cyber threat intelligence and to ensure that you are performing the same level of diligence as the threat actors who are trying to harm your organization.
Download SurfWatch Labs Top Sources of Information for Cyber Criminals: Where the Bad Guys Go to Conduct Research on Their Targets for more information.


One thought on “Learning from Cybercriminals: Using Public Tools for Threat Intelligence”