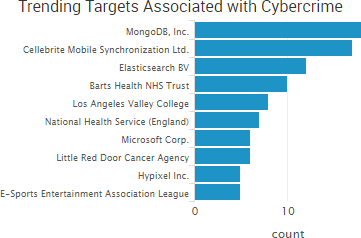
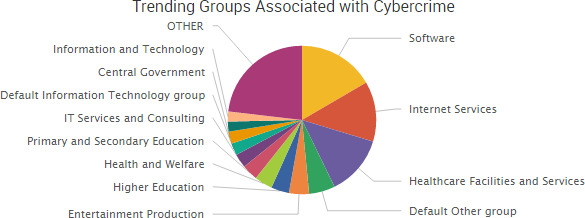
Extortion is once again the top trending cybercrime issue as concern continues around the theft, destruction and blackmail related to thousands of insecure MongoDB, Elasticsearch, CouchDB and Hadoop Distributed File System installations. While those stories led much of the past week’s discussion, there was also a steady stream of reports of organizations being infected with ransomware.
 The most impactful, publicly known ransomware attack of late involves the St. Louis Public Library. The attack hit 700 computers across all 17 of the library’s locations on Thursday, forcing the library to temporarily stop all book borrowing. A $35,000 ransom demand was made, but the library said it will wipe its computer system rather than pay. Checkout service was restored to all locations on Saturday, according to the St. Louis Post Dispatch, and the library’s next priority is to restore service to the publicly available computers – although as of Sunday morning the library’s website stated that the “use of reservable computers is suspended.” A spokesperson said the criminals managed to infect a centralized computer server, which also disrupted the staff’s email system.
The most impactful, publicly known ransomware attack of late involves the St. Louis Public Library. The attack hit 700 computers across all 17 of the library’s locations on Thursday, forcing the library to temporarily stop all book borrowing. A $35,000 ransom demand was made, but the library said it will wipe its computer system rather than pay. Checkout service was restored to all locations on Saturday, according to the St. Louis Post Dispatch, and the library’s next priority is to restore service to the publicly available computers – although as of Sunday morning the library’s website stated that the “use of reservable computers is suspended.” A spokesperson said the criminals managed to infect a centralized computer server, which also disrupted the staff’s email system.
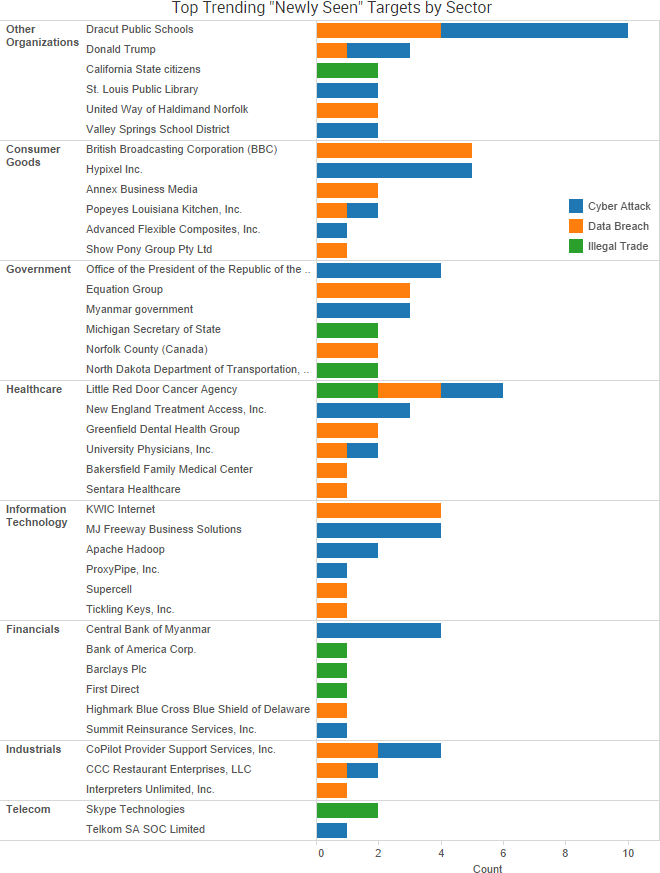
Other organizations to report disrupted services due to apparent ransomware attacks include Advanced Flexible Composites in Illinois, Valley Springs School District in Arkansas, and Kanawha County Schools in Virginia. Advanced Flexible Composites notified its customers that a January 17 hack of its computer system prevented the company from receiving emails and processing quote requests or orders. Not much information was provided about the attack; however, on the surface it sounds like a ransomware infection. Valley Springs School District’s superintendent said the school’s infection may lead to some information saved by teachers being lost such as lessons plans, curriculum and tests. Kanawha County Schools said that it was able to restore internal documents after its incident but that its website would take longer to bring back online.
Finally, the Delaware Department of Insurance is investigating an incident involving a ransomware infection and the unauthorized access of customer data at Summit Reinsurance Services and BCS Financial Corporation.
Other trending cybercrime events from the week include:
- New type of SWIFT attack: Malicious actors compromised the SWIFT systems of three Indian banks and created fake trade documents that may have been used to raise finance abroad or facilitate dealings in banned items. “There was fraudulent duplication of trade documents like letters of credit (LC) and guarantees which the hackers may have or planning to encash with some offshore banks,“ a source told ET Tech. “It’s also possible that hackers did not present the fake LCs to raise funds but to carry out trade of prohibited or illegal commodities.”
- Popeye’s point-of-sale breach: Point-of-sale malware was discovered at the restaurant chain Popeyes, and customers who used their payment cards at one of 10 infected locations between May 5, 2016, and August 18, 2016, likely had their information stolen, the company said in a press release. The ten locations include seven in Texas, two in North Carolina, and one in Georgia.
- More employee and third-party breaches: Police in the Netherlands are alerting 20,000 potential victims about a man who worked at various companies as a website builder and used his position to insert a special script that allowed him to steal usernames and passwords. Online fashion store Showpo is suing a former employee and an online retailer over allegations the graphic designer exported a database of 306,000 customers from MailChimp and passed the information along to online retailer Black Swallow. Customers of the Victorian Game Management Authority in Australia had their personal information potentially exposed when the authority accidentally sent customer data to eight individuals who were renewing their game license. A third-party advertiser that promotes Canada’s Grey Eagle Resort and Casino was hacked and fake text messages were sent to the casino’s VIP members telling them the casino “will be closed for the remainder of January due to infestation and rodent problems.”
- Healthcare-related breaches: TheDarkOverlord said it stole data from Little Red Door Cancer Services of East Central Indiana and attempted to extort the organization by threatening to release the data. CoPilot Provider Support Services announced a breach affecting approximately 220,000 individuals due to a database being illegally accessed in October 2015. Sentara Healthcare is notifying 5,454 vascular and thoracic patients that their medical information was compromised due to a breach at an unnamed third party. The orthopedics practice at The University of Maryland Faculty Physicians Inc. is notifying 1,500 patients that their information may have been accessed when an email account belonging to a physician assistant’s email account was hacked. Barts Health NHS Trust experienced a malware infection that led to taking numerous hard drives offline “as a precautionary measure” and using a manual backup for its computerized pathology results service.
- Other announcements: Hackers targeted a laptop belonging to the special investigation team probing South Korean President Park Geun-hye’s political scandal. Current and former employees of Dracut Public Schools had their Social Security numbers and other personal information compromised due to an employee falling for a phishing attack. A Russian-language version of the series finale of Sherlock circulated online before the episode was broadcast. The forums of Clash of Clans developer Supercell and MrExcel, both of which use vBulletin, announced data breaches.
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
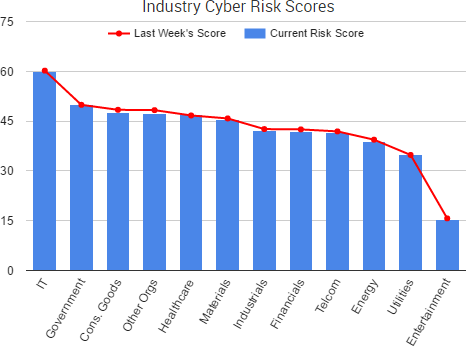
Cyber Risk Trends From the Past Week
 Security researchers frequently discover private data being exposed to the Internet due to technical errors such as poorly secured data backups, and this past week several new incidents along those lines.
Security researchers frequently discover private data being exposed to the Internet due to technical errors such as poorly secured data backups, and this past week several new incidents along those lines.
Chris Vickery’s discovery of multiple misconfigured Rsync instances at Canadian ISP KWIC appears to be truly massive potential breach, with CSO Online reporting that terabytes of information for all of its customers was exposed. The issue was fixed after the company was notified of the problem; however, it is unclear how long the information was available before the fix. The data exposed included credit card details, email addresses, passwords, names, home and business addresses, phone numbers, email backups, VPN details and credentials, internal KWIC backups, and more.
In last week’s roundup we noted that incorrectly configured databases exposed the data of 3.3 million Hello Kitty fans as well as thousands of patients of Canadian plastic surgery company SpaSurgica. The week before that data related to healthcare professionals deployed within the U.S. Military’s Special Operations Command (SOCOM) was exposed in a similar fashion. The week before that data belonging to Ameriprise clients was exposed due to an advisor synchronizing data between between his home and work and neither drive requiring a password.
This past week saw a similar story of a poorly configured backup drive. Interpreters Unlimited, a California-based translation and interpreter company, exposed thousands of sensitive documents due to an Internet-connected backup drive used by an IT manager that had no password protection and was online for four to six months. Files seen by ZDNet showed that the drive contained dozens of usernames, email addresses and passwords stored in plain text for the company’s infrastructure, including its website, hosted email and domain name servers, and remote desktop apps. The drive also contained the private data of clients and employees such as Social Security numbers and the amount of money translators earned.
The constant trickle of company, customer and employee data being leaked due to the poor practices of employees and partners should serve as a reminder for all organizations that data breaches often spring from mistakes made within the organization — not just external cybercriminals.


What’s up everyone, it’s my first pay a quick visit at
this web page, and article is really fruitful for me, keep up posting these types of articles.
LikeLike