The CIA remained as the top trending cybercrime of the week as WikiLeaks released a fourth set of documents related to the agency. The new dump includes 27 documents from the CIA’s Grasshopper framework, which WikiLeaks described as “a platform used to build customized malware payloads for Microsoft Windows operating systems.” The leaked CIA tools will likely continue to dominate much of the cybercrime discussion in the coming weeks as WikiLeaks appears to have a slow-drip campaign designed around maximizing the leak’s publicity.
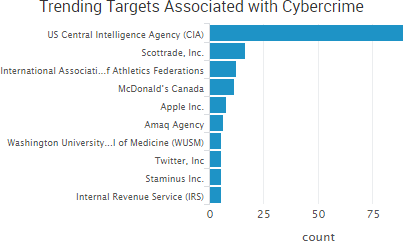
The top trending new cybercrime target of the week was Scottrade, which was one of several organizations to experience a data breach due to insecure, publicly exposed data. The Scottrade incident was caused by “human error” at third-party vendor Genpact, which uploaded a data set to one of its cloud servers without the proper security protocols in place. As a result, “the commercial loan application information of a small B2B unit within Scottrade Bank, including non-public information of as many as 20,000 individuals and businesses” was exposed, Scottrade said in a statement.
Security researcher Chris Vickery, who discovered the exposed database, said it contained 48,000 lessee credit profile rows and 11,000 guarantor rows, and that each row contained various types of personal information, including Social Security numbers. The database also contained internal information such as plain text passwords and employee credentials used for API access to third-party credit report websites.
Those who read this roundup each week know that breaches due to insecure databases are common, and in addition to Scottrade, Vickery also discovered “a trove of data from a range of North Carolina government offices, including Dept of Administration, Dept of Health and Human Services, Division of Medical Assistance, Dept of Cultural Resources, Dept of Public Safety, Office of State Controller, Office of State Budget and Management, NC IT Department.”
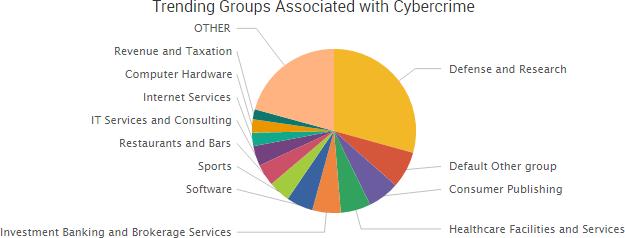
Other trending cybercrime events from the week include:
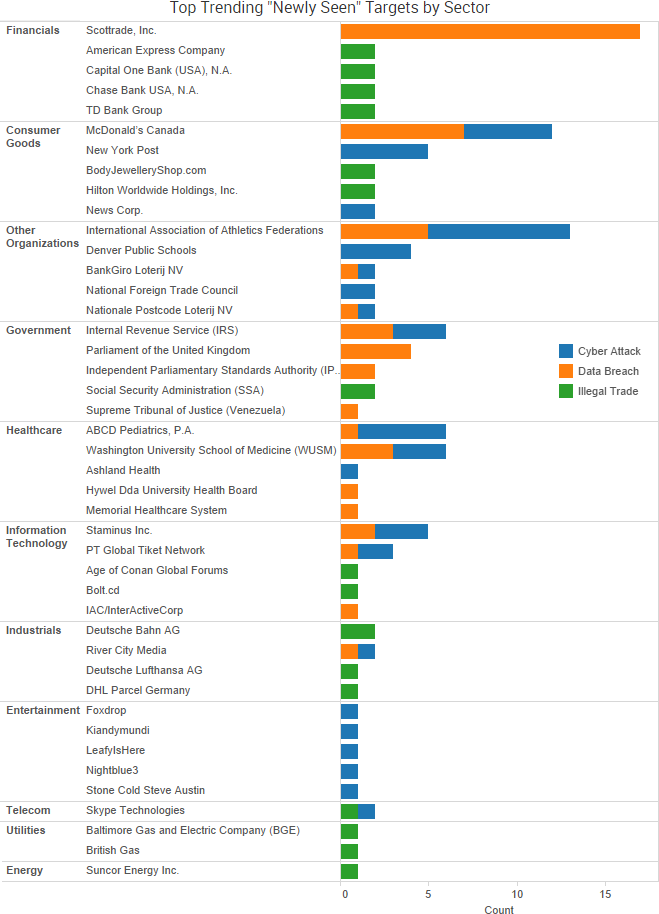
- IRS announces another data breach: The IRS is notifying 100,000 people that their tax information may have been compromised due to a data retrieval tool used when filling out the Free Application for Federal Student Aid (FAFSA). Officials first learned of the potential issue in September 2016, but the service was not disabled until suspicious activity was observed in February. Malicious actors could pretend to be students, start the financial aid application with relatively little stolen information, and give permission for the IRS to populate the form with tax data that could then be used for fraudulent returns.
- Highly sensitive patient data sold on the dark web: A breach at Behavioral Health Center appears to have compromised thousands of patients’ sensitive data, including evaluations, session notes, and records of sex offenders and sex abuse victims. An actor on the dark web claims between 3000 and 3500 unique individuals are in the data, which has since been sold to another actor. “These are not just basic fullz, these are the COMPLETE clinician notes from EVERY session with a patient, sometimes spanning hundreds of sessions over years,” read a listing on the dark web. “Everything confessed/discussed in complete privacy is in here for thousands of patients. All records are from 2007 to current date.”
- Healthcare organizations targeted: An amateur actor appears to be targeting healthcare organizations with spear phishing messages designed to infect victims with a variant of the Philadelphia ransomware, an unsophisticated ransomware kit that sells for a few hundred dollars. Researchers believe spear phishing messages containing a shortened URL that led to a malicious DOCX file on a personal storage site were used to infect a hospital from Oregon and Southwest Washington. ABCD Pediatrics said that its servers were infected with “Dharma Ransomware” and while investigating the incident the company also discovered suspicious user accounts that suggested a separate incident of unauthorized access.
- APT10 hacking group makes headlines: The APT10 hacking group has gained access to the systems of an “unprecedented web” of victims by first targeting managed outsourced IT service companies with spear phishing messages and custom malware and then using those companies as a stepping stone into their clients’ systems. The group also inserted malicious links into certain pages of the National Foreign Trade Council’s website in order to target individuals registering for specific meetings.
- Other notable cybercrime events: The International Association of Athletics Federations said information related to athletes’ therapeutic use exemption applications was compromised due to unauthorized access to its network by “Fancy Bear.” The Dutch National Charity Lotteries said that around 450,000 customers were impacted by a vulnerability in the computer systems of Lotteries’ supplier OpenOfferete. Cybercriminals stole $40,000 of direct deposit money meant for Denver Public Schools after numerous employees fell for a phishing email. A hack of digital content network Omnia affected a variety of popular YouTube channels. The New York Post app was hacked and used to send to out a series of false push notifications. Arrests were made in Dubai related to breaking into the emails of five senior White House officials and attempting to blackmail the officials with what a local law enforcement official described as “highly confidential information.”
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
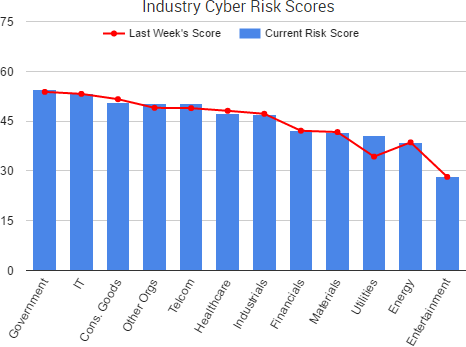
Cyber Risk Trends From the Past Week
While business email compromise scams and other digital fraud continues to impact numerous organizations, several stories this week proved that criminals are still attempting to steal physical cash from ATMs around the world.
The flashiest story involved a gang based out England that used explosives and stolen high-powered vehicles to rip ATMs from walls. The gang would then put the stolen ATMs inside a large truck and drive away, in at least one instance right by the very police looking for them. Police announced that several recent raids had led to the arrest of the gang. Less flashy attempted ATM thefts from hotels in Edmonton led police to advise business last month that owners should bolt ATMs to the floor and place them in well lit, high-traffic areas that are monitored by surveillance cameras.
A new, more discreet method of stealing money from ATMs involves emptying the cash stored in certain models by drilling a three-inch hole in its front panel and using a $15 homemade gadget that injects malicious commands to trigger the machine’s cash dispenser. Kaspersky Lab researchers first became aware of the attack in September 2016 when a bank client discovered an empty ATM with a golf-ball sized hole by the PIN pad. Since then, similar attacks using the drill technique have been observed across Russia and Europe. The researchers did not name the ATM manufacturer, but they said the issue is difficult to fix since it would require replacing hardware in the ATMs to add more authentication measures.
Kaspersky Lab also released findings on another series of ATM attacks first hinted at back in February when a series of attacks that used in-memory malware to infect banking networks were reported. Code from the penetration-testing software Meterpreter code was combined with a number of legitimate PowerShell scripts and other utilities to create malware that could hide in the memory and invisibly collect the passwords of system administrators. That access was then used to remotely install a new breed of ATM malware called ATMitch, Kaspersky Lab researchers said in a report issued last week.
The ATMitch malware communicates with the ATM as if it is legitimate software and makes it possible for attackers to collect information about the number of banknotes in the ATM’s cassettes as well as dispense money at the touch of a button. The attackers may still be active, the researchers noted, but it is unknown how many ATMs have been targeted by the malware since the malware self-deletes after the attack. What is clear is that ATM machines remain a popular target for criminals, and businesses should be aware of the evolving methods — both crude and sophisticated — being used to steal the cash inside them.

