An old data breach came back to life this week as Ashley Madison users who had their data compromised back in July 2015 are once again being blackmailed — this time by an extortion group threatening to launch a public website and contact people in victims’ social media networks. The website will allegedly be launched on Monday, at which point it will be clear if the threat is just a ploy to extort victims who are low-hanging fruit or if the group will actually carry out their attempt at public shaming.
“On May 1 2017 we are launching our new site — Cheaters Gallery – exposing those who cheat and destroy families,” a group using a Ukrainian top level domain recently wrote in an email to some Ashley Madison users. “We will launch the site with a big email to all the friends and family of cheaters taken from Facebook, LinkedIn and other social sites. This will include you if do not pay to opting out.”
Robin Harris wrote on ZDNet that the email he received quoted his personal Ashley Madison profile and that the blackmail price for “opting out” of the Cheaters Gallery website was around $500. Of course, paying that blackmail won’t accomplish much unless the victims are willing to keep paying ransoms in an endless game of extortion whack-a-mole. The breached Ashley Madison data has been circulating for 20 months now — ever since the account details of around 32 million users were published on the dark web — and numerous other actors have attempted to extort the victims in the past via extortion emails and letters sent to victims and their spouses. The repeated blackmail campaigns indicate that either victims are paying up and the campaigns are profitable or that the actors behind them at least believed they would be worth the investment.
Seeing another round of Ashley Madison blackmail threats nearly two years after the breach is a reminder that once data is exposed, it remains exposed forever. As SurfWatch Labs noted in a report last year, the pool of compromised data never empties; it only grows. That means that malicious actors can use, reuse, build upon, and find new ways to monetize that expanding pool of data now and in the future.
Other trending cybercrime events from the week include:
- More payment card breaches: Chain restaurant Chipotle said that it is investigating a possible point-of-sale breach after detecting “unauthorized activity on the network that supports payment processing for purchases made in our restaurants.” The investigation is focusing transactions that occurred at locations from March 24, 2017 through April 18, 2017. Trading card dealer Blowout Cards announced a data breach due to “an exploit in the form of a modified payment .php file” that allowed the intruders to skim payment card information as customers checked out via its website. As a result, those who used credit and debit cards to check out via the site’s shopping cart between January 2017 and April 20, 2017, had their information compromised.
- Espionage groups behind South Korea, Israel attacks: Iran’s OilRig hacking group is behind a series of targeted attacks against 250 individuals in government agencies, high-tech companies, medical organizations, and educational institutions such as the renowned Ben-Gurion University. The attacks took place between April 19 and 24 and employed the just-patched Microsoft CVE-2017-0199 remote code execution vulnerability in the Windows Object Linking and Embedding (OLE) application programming interface. Two cyber-espionage groups linked to China have been observed launching a variety of attacks against South Korea’s government, military, defense companies, and a big conglomerate involved in deploying Terminal High-Altitude Area Defense, or Thaad, a U.S. missile-defense system designed to protect South Korea from a North Korean missile threat.
- FIN7 campaign uses social engineering: The FIN7 group (also known as Carbanak) is targeting large restaurant chains, hospitality, and financial service organizations with spear phishing messages centered around complaints, catering orders, or resumes. The group has also been observed calling stores at targeted organizations to ensure they received the email and attempting to walk them through the infection process, as it has done in previous campaigns.
- Phishing leads to fraud, data breaches: Fraudsters were able to convince more than 500 University of California students to hand over their health information, and that information was used to steal almost $12 million from the university by writing fake medical prescriptions in the students’ names. The Iowa Veterans Home is notifying 2,969 people that their medical and financial information may have been compromised after three IVH employees fell for phishing emails that compromised their email account credentials.
- Other notable cybercrime events: A vulnerability in a popular third-party library used by HipChat.com led to a data breach. The email addresses and unique IMEI numbers from Ciphr phone users have been dumped online, and Ciphr claims that the leak was carried out by a rival secure phone company. A hacker claims to have compromised the forums of R2 games. Concordia University said that approximately 9,000 students may have been affected by unauthorized access to its online course systems. The information of 8,000 Home Depot customers who had lodged complaints with its MyInstall program was found exposed online. Ransomware infected some City of Newark computers. WikiLeaks has published the user guide for the “Weeping Angel” tool allegedly developed by the CIA.
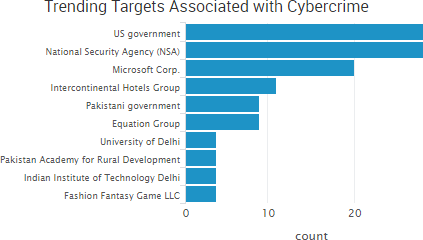
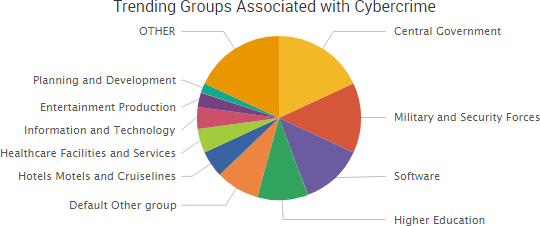
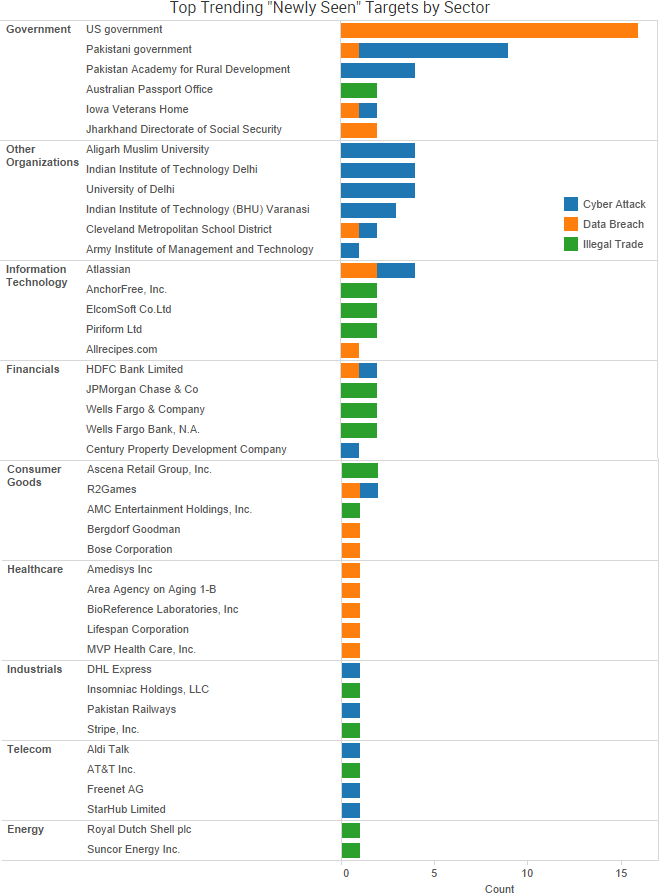
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
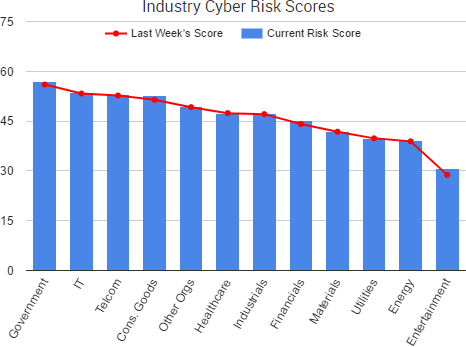
Cyber Risk Trends From the Past Week
 Facebook and Google confirmed this week that they were the victims of the $100 million phishing scheme announced by the Department of Justice of last month.
Facebook and Google confirmed this week that they were the victims of the $100 million phishing scheme announced by the Department of Justice of last month.
The scheme was carried out by Evaldas Rimasauskas, a Lithuanian man who allegedly impersonated the large Taiwan-based manufacturer Quanta Computer in order to dupe the companies into making a series of fraudulent payments. According to the indictment, Rimasauskas, registered and incorporated a company in Latvia with the same name as Quanta Computer and then forged email addresses, invoices, and corporate stamps in order to convince the accounting departments at the two tech companies to make transfers worth tens of millions of dollars over a two year span, stealing $100 million in total.
Facebook and Google both told Fortune that they have since recovered the bulk of the funds.
Acting U.S. Attorney Joon H. Kim said in a DOJ press release that “this case should serve as a wake-up call to all companies – even the most sophisticated – that they too can be victims of phishing attacks by cyber criminals.”
That same concern was echoed in a report from the Association for Financial Professionals published in early April. According to the report, 74 percent of finance professionals reported that their organizations were victims of business email compromise (BEC) scams in 2016, a 10-percentage point increase from the previous year.
Likewise, in December 2016 the FBI warned of a dramatic increase in BEC scams, which attempt to assume the identity of a person of authority within the company or — in the case of the Facebook and Google thefts — a trusted vendor before asking to initiate a fraudulent wire transfer.

