Cryptocurrency theft was among the week’s top trending cybercrime practices due to users at both South Korean cryptocurrency exchange Bithumb and Classic Ether Wallet reporting that their digital currency wallets were emptied due to cyber-attacks.
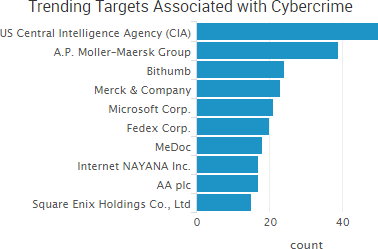
Bithumb reported that one of its employees personal computers had been hacked in February 2017 and that the personal details of 31,800 Bithumb website users (about 3 percent of total users) had been compromised as a result. The stolen data included users’ names, mobile phone numbers, and email addresses. The exchange said there was no direct access to funds stored on the exchange; however, it appears the attackers were able to use the contact information to carry out phishing attacks against Bithumb users in order to obtain the one-time passwords needed to gain access those users’ funds.
One user reported losing as much as 1.2 billion won ($1.04 million) in the attack. Bithumb said shortly after the attack that it would pay up to 100,000 won ($87) to victims. Additional compensation will be available once individual losses are verified, the company said, but it is unclear if victims will be fully reimbursed.
Users of the Classic Ether Wallet also reported having their wallets emptied earlier this month. That theft appears to be due to a malicious actor managing to socially engineer the service’s German hosting provider 1&1 into handing over access to the domain. The actor then switched the site’s settings to direct the funds to his or her own malicious server. Multiple users who visited classicetherwallet.com and provided their private key while the site was in control of the fraudsters reported that they had their account emptied. Exact losses due to the incident is unclear, but some media outlets reported it could be nearly $300,000 worth of Ethereum Classic cryptocurrency.
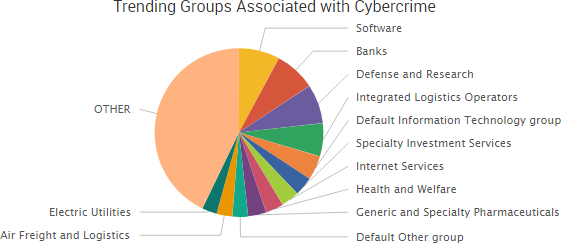
Other trending cybercrime events from the week include:
- Large databases exposed: Two databases containing the personal information of 3 million WWE fans were exposed to the Internet without requiring a username and password. The data included names, email and physical address, educational background, earnings, and ethnicity. UK car insurance company AA exposed the sensitive information of over 100,000 customers due to insecure database backups related to AA’s online store and never informed those customers of a breach, Motherboard reported. The database obtained by Motherboard included 117,000 unique email addresses, names, physical and IP addresses, details of purchases, and payment card information such as the last four digits of the card and its expiration date.
- Insiders lead to extortion, theft: A former Dentons litigation associate in Los Angeles has been charged with extortion over allegedly demanding that his former law firm pay him $210,000 and give him a piece of artwork or else he would leak sensitive data to the Above the Law blog. According to court documents, the man accessed confidential information when one of the firm’s partners gave him access to his email while working a case. A crime analyst with the Smyrna Police Department was charged with 31 counts of computer theft over the alleged theft of information without authorization, including the driver’s licenses and mobile data of 28 victims.
- Sabre confirms breach affecting multiple companies: Sabre said its investigation into a previously disclosed breach found that an unauthorized party was able to use compromised account credentials to gain access to payment card information and certain reservation information for a subset of hotel reservations processed through the SHS SynXis Central Reservations system. The breach occurred over a seven-month period from August 2016 to March 2017. Sabre said it notified partners and customers that use the reservations system, as well as some travel management companies and travel agencies that booked travelers that may have been affected. Sabre did not disclose the total number of individuals affected by the breach.
- Other notable incidents: A Georgia men pleaded guilty to charges related to a BEC scam that defrauded Sedgwick County out of $566,000. Anonymous Bulgaria has leaked files from the Azerbaijan Embassy in Bulgaria that claim Silk Ways Airlines has carried tens of tons of heavy weapons and ammunition headed to terrorists under the cover of 350 diplomatic flights. Cove Family & Sports Medicine said that a ransomware infection encrypted medical records as well as a portion of its backup records. Walnut Place said that while it was investigating a previous ransomware infection it was affected by a second ransomware incident. Medicaid members in Indiana are being warned that their patient information was potentially accessible between February and May of 2017. Wooster-Ashland Regional Council of Governments said that its computer network as breached on May 26 and more than 200,000 records were compromised. The Simcoe County District School Board is warning parents of a potential privacy breach at Collingwood Collegiate Institute involving their email addresses and phone numbers.
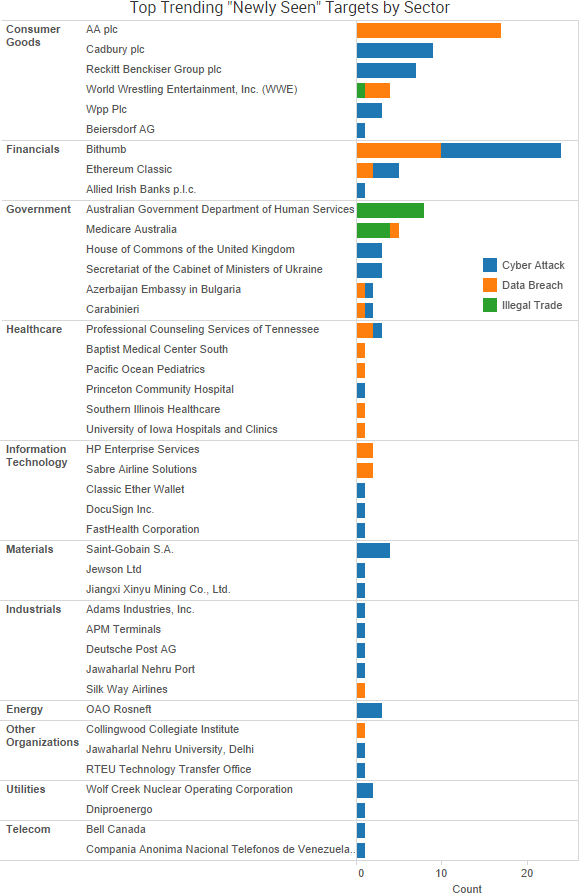
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
Cyber Risk Trends From the Past Week
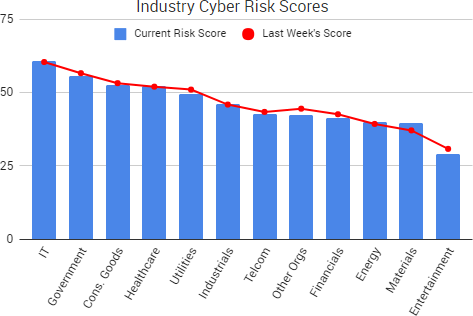 Russian state-sponsored hackers are responsible for recent cyber-intrusions into the business systems of U.S. nuclear power plants and other energy companies, government officials said. It is the first time Russian government hackers are known to have compromised the networks of U.S. nuclear plants, the officials added.
Russian state-sponsored hackers are responsible for recent cyber-intrusions into the business systems of U.S. nuclear power plants and other energy companies, government officials said. It is the first time Russian government hackers are known to have compromised the networks of U.S. nuclear plants, the officials added.
The statements followed a joint alert from the FBI and Homeland Security at the end of June that warned APT actors were targeting employees in the energy sector with phishing messages and watering hole attacks designed to harvest credentials that could be used to gain access to victims’ networks. The attackers were observed sending highly targeted messages to senior industrial control engineers containing fake resumes for control engineering jobs, as well as compromising websites commonly visited by their target victims and deploying man-in-the-middle attacks.
There is no evidence of any breaches or disruptions of the cores systems controlling operations at the plants, The Washington Post reported. Instead, the focus appears to be on systems dealing with business and administrative tasks, such as personnel. The New York Times reported that the joint DHS and FBI report concluded that the hackers appeared determined to map out computer networks — potentially with a goal of carrying out more destructive attacks in the future. Bloomberg reported that at least a dozen power plants had their networks breached by the APT actors, including the Wolf Creek nuclear facility in Kansas.
“There was absolutely no operational impact to Wolf Creek,” a spokeswoman for the nuclear plant said. “The reason that is true is because the operational computer systems are completely separate from the corporate network.”
However, as we’ve seen in attacks just this week, potentially compromised personnel and business data could be leveraged in future targeted phishing messages to gain more information or access — or to find a weak point or an individual that may be leveraged for future attacks.

