The cryptocurrency Ethereum made numerous headlines this past week due to three separate multi-million dollar thefts: one due to a bug in the code of the Parity Ethereum client, one caused by a website hack that redirected funds meant for the Initial Coin Offering (ICO) of Coindash, and one tied to a hacker managing to steal VERI tokens during the ICO of Veritaseum.
The largest theft involved a bug found in the multi-signature wallet code used as part of Parity Wallet software, which led to 3 wallets being exploited and reports of more than 150,000 ETH (approximately $34 million) being stolen. As Parity noted, a total of 596 multi-sig wallets were vulnerable, but the vast majority of the funds in those wallets were commandeered by a group known as the White Hat Group in order to prevent the theft of an additional 377,000 ETH (approximately $85 million).
That theft followed an announcement from Coindash that an actor had managed to gain access to its official website during the company’s ICO and changed the text on the site to an ether wallet address likely controlled by the attacker — resulting in investors sending $10 million worth of Ether to the fraudulent address. The company’s developers said that “all CoinDash investors will get their tokens”; however, Coin Desk reported that individuals who made transactions after the website was shut down will not be compensated.
Finally, Veritaseum confirmed that a malicious actor stole $8.4 million worth of VERI tokens from the platform’s ICO on July 23. The attackers immediately resold the tokens during the “very sophisticated” attack. Not much was disclosed about the attack, but “there is at least one corporate partner that may have dropped the ball and be liable,” the company’s founder said.
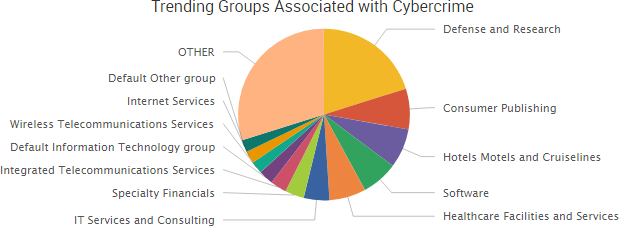
Other trending cybercrime events from the week include:
- More information exposed due to errors: Dow Jones & Company confirmed that at least 2.2 million customers had their data exposed due to an Amazon Web Services S3 bucket that was configured to allow any AWS “Authenticated Users” to download the data. In addition, the leak contained the details of 1.6 million entries in a suite of databases known as Dow Jones Risk and Compliance, a set of subscription-only corporate intelligence programs used largely by financial institutions for compliance with anti-money laundering regulations. Security researchers discovered an insecure database owned by the data services company DM Print that had 31,000 records, including administrative credentials for the database. With that information, anyone could access highly sensitive health information such as names, date of births, NIN numbers, addresses, investment data, and more. Travel company Flight Centre said that the personal information and customer passports “relating to some leisure customers in Australia was accidentally made available to a small number of potential third party suppliers for a short period of time.”
- Insider breaches: An employee at Bupa copied and removed insurance information relating to 108,000 international insurance plans affecting 547,000 customers. The company said the data included names, dates of birth, nationalities, and some contact and administrative information. Detroit Medical Center is notifying 1,529 patients of a breach at a contracted staffing agency where an employee provided their information to unauthorized individuals. The breach occurred between March 2015 and May 2016. The Nova Scotia Health Authority said that 337 patients had their personal health information accessed inappropriately in two separate incidents involving six employees.
- More energy sector warnings: The UK’s National Cyber Security Centre (NCSC) warned that state-sponsored actors are targeting the country’s energy sector and that “a number of Industrial Control System engineering and services organisations” have likely been compromised. The warnings followed similar alerts from U.S. agencies about hackers successfully targeting U.S. energy companies. While other sectors have been targeted, the focus of the attacks are engineering, industrial control, and water sector companies, the NCSC said.
- Other notable incidents: Domain name registrar Gandi said that an unauthorized connection that occurred at one of the technical providers it uses to manage a number of geographic TLDs led to 751 domains having their traffic forwarded to a malicious site exploiting security flaws in several browsers. There were 22 breach incidents in the Veterans Administration’s monthly reports to Congress between May 2016 and June 7, 2017, and only one of those breaches received any media coverage at the time, according to data obtained via a Freedom of Information Act request by databreaches.net. A dark web vendor going by the name “dnu2k” is selling data tied to dadeschools.net, k12.wi.us, and other “freshly hacked emails.” The latest dump of CIA documents from WikiLeaks involves contractor Raytheon Blackbird Technologies providing “Proof-of-Concept ideas and assessments for malware attack vectors” to the agency.
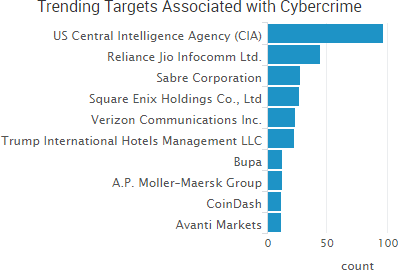
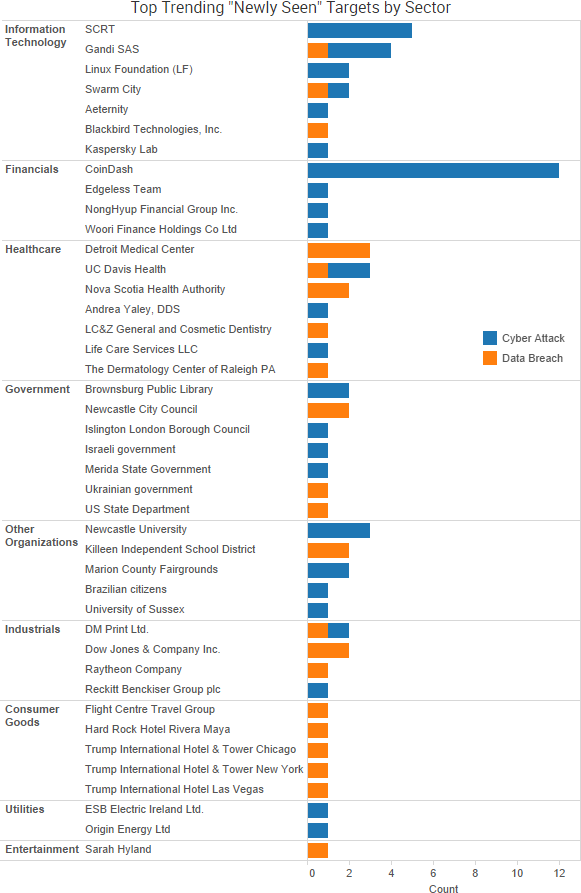
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
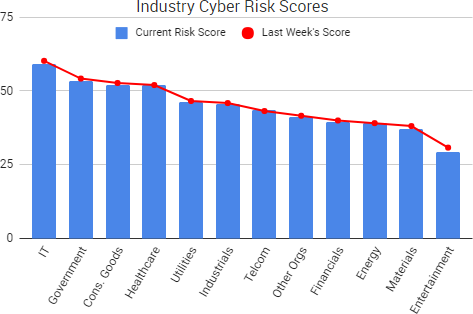
Cyber Risk Trends From the Past Week
The picture of the damage cause by the NotPetya global outbreak in late June continues to crystallize as more companies reveal the details and fallout of their infections.
For starters, FedEx said that some of the damage caused by the NotPetya attack may be permanent, particularly when it comes to TNT Express B.V., which FedEx acquired in May 2016. Some of TNTs customers were “still experiencing widespread service and invoicing delays” nearly three weeks after the NotPetya infection, according to SEC documents filed by FedEx.
“We cannot yet estimate how long it will take to restore the systems that were impacted, and it is reasonably possible that TNT will be unable to fully restore all of the affected systems and recover all of the critical business data that was encrypted by the virus,” FedEx wrote in its filing. That filing listed more a dozen types of costs and damages potentially resulting from the incident — ranging from operational disruption to remediation to permanent customer loss to litigation.
In addition, the France-based Compagnie de Saint Gobain SA said that a preliminary assessment of the NotPetya infection estimated the incident would cost the company approximately 1% of first half sales. That equates to approximately €200 million as a result of the attack, The Street reported.
Earlier this month, The Guardian reported that Reckitt Benckiser, a British consumer goods company, may lose around €100 million due to NotPetya. In addition, Mondelez, the maker of Oreo cookies, said that the attack had disrupted shipping and invoicing during the last four days of the second quarter and that in a few markets the company had “permanently lost some of that revenue due to holiday feature timing.”
NotPetya may not have generated nearly as much extortion money as other ransomware — if that was even its intention to begin with — however, the global attack has proven quite impactful for numerous organizations so far. The second half of 2017 will likely see the total costs of the attack become more clear as other organizations reveal more details about how NotPetya affected their operations — and how the fallout from the attack has impacted the year’s financial projections.


One thought on “Weekly Cyber Risk Roundup: Three Ethereum Heists and NotPetya Fallout Continues”