The politics surrounding the “Unite the Right” rally and its counter-protests in Charlottesville spilled over into the cyber world this week as hacktivists took action against websites and a debate emerged around the ethics of hosting white nationalist websites as well as doxing individuals who attended the rally.
Under the hashtag #OpDomesticTerrorism, hacktivists have urged DDoS attacks against white nationalist websites and posted leaks of some of those websites’ alleged members. In addition, the hacking group known as “New World Hackers” said it carried out a DDoS attack against the Charlottesville city website to “deliver our own version of justice to the KKK and government.”
Other individuals began to search through the many images of the “Unite the Right” rally in order to publicly identify those who attended the event. The man behind the Twitter account “Yes, You’re Racist” called on users to help identify the “nazis marching in #Charlottesville” so he could “make them famous.” However, not all the doxing attempts were accurate. For example, an assistant professor at the University of Arkansas was wrongly identified and said he eventually had to call the police due to numerous threats being made against him and his wife as well as their home addresses being posted online. The man behind the Twitter account said he’s received death threats over the doxing as well.
Technology companies were also brought into the debate. GoDaddy, Google, Cloudflare, Zoho, Sendgrid, and Discord all cut services to the Neo-Nazi website The Daily Stormer, USA Today reported. However, those actions led to a rebuke from the Electronic Frontier Foundation for private companies “decid[ing] who gets to speak and who doesn’t.”
Other trending cybercrime events from the week include:
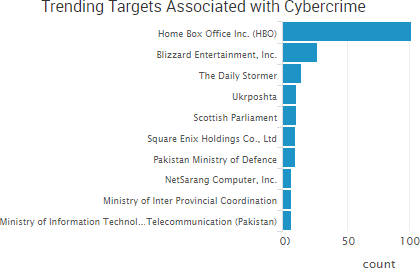
- HBO troubles continue: The hacking group OurMine temporarily hijacked several HBO social media accounts. In addition, the group of hackers that breached HBO in late July has continued to leak stolen episodes and other documents. Authorities also said that four current and former employees at Prime Focus Technologies, which handles Star India’s data, have been arrested on suspicion of leaking a Star India copy of the August 7 episode of Game of Thrones. Finally, a third-party vendor accidentally posted the August 20 episode of Game of Thrones on the HBO Nordic and HBO España platforms, and that episode was quickly pirated.
- DDoS attacks make headlines: DDoS attacks against Blizzard disrupted services for several popular games, including Overwatch and World of Warcraft. The website of Ukraine’s national postal service Ukrposhta was the target of a two-day long DDoS attack that caused slowdowns and interruptions for the website and its services.
- More ransomware infections: LG Electronics said that the self-service kiosks at some of its service centers were infected with ransomware, causing some access problems. The ransomware appears to have been identical to the WannaCry ransomware that made headlines in May, officials from the Korea Internet & Security Agency said. Pacific Alliance Medical Center said that a June 14 ransomware infection may have compromised the protected health information of patients.
- Data inadvertently exposed: Voting machine supplier Election Systems & Software exposed the personal information of more than 1.8 million Illinois residents due to an insecure Amazon Web Services device. ES&S said the exposed server did not include “any ballot information or vote totals and were not in any way connected to Chicago’s voting or tabulation systems.” The Texas Association of School Boards notified some school district employees that a server containing their names and Social Security numbers “inadvertently became visible on the Internet.”
- Other notable incidents: Surgical Dermatology Group in Alabama is notifying patients that their personal and healthcare information may have been compromised due to a breach at its cloud hosting and server management provider, TekLinks, Inc. City of Hope said that it is notifying patients that their medical information may have been compromised following an email phishing incident that led to four employee email accounts being compromised. OSHA has suspended access to its new Injury Tracking Application (ITA) after it was notified by the Department of Homeland Security of a potential breach of user information. The Scottish Parliament said it was the target of a brute force cyber-attack and members of parliament and staff with parliamentary email addresses were warned to make sure their passwords were as secure as possible. A former Columbia Sportswear information technology manager was charged with one count of computer fraud for allegedly accessing the company’s computer systems for more than two years after leaving the company.
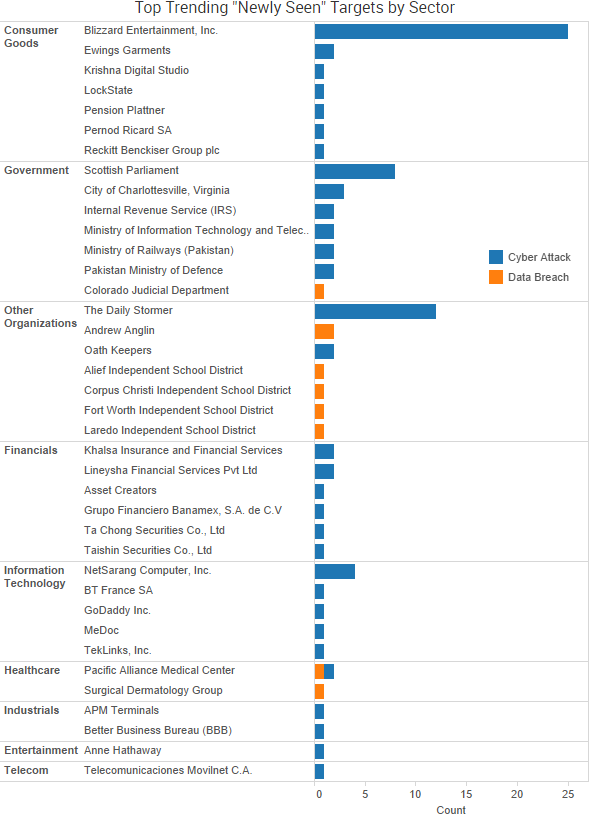
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
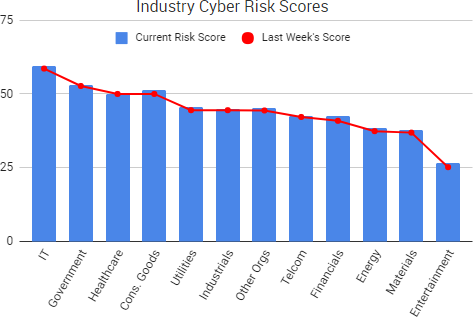
Cyber Risk Trends From the Past Week
 One of the week’s most notable advisories involved the software vendor NetSarang and a backdoor dubbed “ShadowPad” that was shipped out with a July version of the company’s products.
One of the week’s most notable advisories involved the software vendor NetSarang and a backdoor dubbed “ShadowPad” that was shipped out with a July version of the company’s products.
“Regretfully, the Build release of our full line of products on July 18, 2017 was unknowingly shipped with a backdoor, which had the potential to be exploited by its creator,” NetSarang said in a statement. “The fact that malicious groups and entities are utilizing commercial and legitimate software for illicit gain is an ever-growing concern and one that NetSarang, as well as others in the computer software industry, is taking very seriously.”
The issue was first discovered by a financial institution partner of Kaspersky Lab — which described the backdoor as “one of the largest known supply-chain attacks” — after discovering suspicious DNS requests originating on a system involved in the processing of financial transactions. Those requests were later discovered to be the result of a malicious module hidden inside a recent version of NetSarang software.
“If the attackers considered the system to be ‘interesting,’ the command server would reply and activate a fully-fledged backdoor platform that would silently deploy itself inside the attacked computer,” Kaspersky wrote. “After that, on command from the attackers, the backdoor platform would be able to download and execute further malicious code.”
That malicious module has been activated at least once in Hong Kong, but it is possible that other organizations have been infected, the researchers said. NetSarang said that the affected builds are Xmanager Enterprise 5.0 Build 1232, Xmanager 5.0 Build 1045, Xshell 5.0 Build 1322, Xftp 5.0 Build 1218, and Xlpd 5.0 Build 1220. Organizations using those builds should cease using the software until an update can be applied.

