The first half of 2016 is over, and SurfWatch Labs analysts have spent the past few weeks sifting through the huge amount of cybercrime data we collected — totaling tens of thousands of CyberFacts across more than 3,400 industry targets — in order to identify threat intelligence trends to include in our mid-year 2016 report.
“If anything,” the report notes, “the stories behind these breaches seem to contradict the increasingly familiar spin that follows most incidents: ‘We were the victim of a sophisticated attack. The incident has been contained.'”
Download the full Mid-Year 2016 Cyber Trends Report
To the contrary, the data behind the year’s many incidents indicates many cyber-attacks are neither sophisticated nor isolated.
For example, this year’s top trending cybercrime target was LinkedIn. In May 2016 LinkedIn announced that a 2012 breach, which was believed to have been contained four years ago by resetting passwords on impacted accounts, was much larger than originally thought. An additional 100 million members were affected. Since that announcement, reports continue to surface of secondary organizations having their data stolen due to a combination of those now exposed LinkedIn passwords, widespread password reuse among employees, and remote access software from services such as GoToMyPC, LogMeIn, and TeamViewer.
To make matters worse, LinkedIn was just one of several massive credential dumps to make headlines — not to mention the numerous high-profile breaches affecting personal information or other sensitive data.
Trending Industry Targets Tied to Cybercrime in 1H 2016

Malicious actors excel at taking one piece of information and leveraging it to perform further attacks, gain more information, and widen their reach. As we noted in May, this has led to many companies making headlines for data breaches — even though a breach may not have occurred. For example:
- Music service Spotify had a list of user credentials posted to Pastebin that were collected from other data breaches. This led to a series of articles about the company “denying” a data breach.
- China’s online shopping site Tabao had hackers use a database of previously stolen usernames and passwords to try to access over 20 million active accounts.
- GitHub, Carbonite, Twitter, and more have all forced password resets for users after large-scale targeting of user accounts or lists of user credentials appeared on the dark web.
- Other unnamed companies have confirmed to media outlets that sensitive information has been stolen recently due to password reuse attacks.
SurfWatch Labs’ data paints a picture of an increasingly connected cybercrime world where malicious actors leverage past successes to create new victims. The pool of compromised information widens; the effects of cybercrime ripple outwards.
However, those effects are largely dependent on industry sector and the types of information or resources that are attractive to different individuals, hacktivists, cybercriminal groups, and other malicious actors. SurfWatch Labs’ data so far this year reflects that fact.
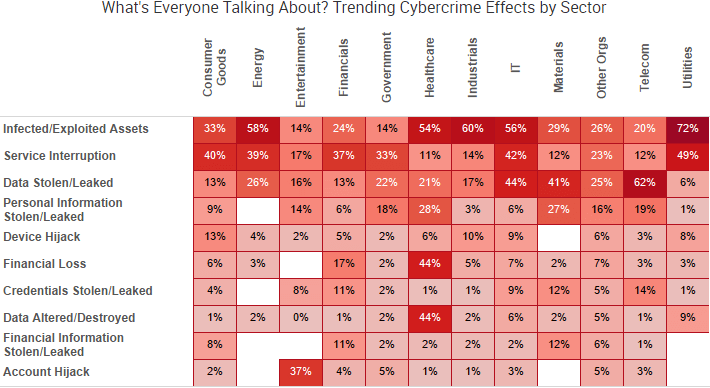
For example, SurfWatch Labs report identifies infected/exploited assets as the top effect category overall, although it only appeared in 14% of entertainment and government-related CyberFacts. In those sectors, the majority of discussion was around account hijacks (37%) and service interruption (33%), respectively, as actors targeted social media accounts with large followings or hacktivists utilized defacement and DDoS attacks to spread their messages.
Similarly, the healthcare sector saw increased chatter around the financial loss and data altered/destroyed categories due to several high-profile ransomware attacks and warnings from various bodies about potential extortion attacks.
Other interesting data points and trends from the report include:
- IT, global government, and consumer goods were the most targeted industries. Of all the CyberFacts analyzed, the information technology industry was hit the hardest in the first half of 2016. Microsoft was second behind LinkedIn as the top target. After IT, the government sector had the highest number of publicly discussed cybercrime targets, led by a breach at the Commission on Elections in the Philippines. The consumer goods sector made up the largest share of industry targets with information bought, sold, or otherwise discussed on the dark web.
- Employee data is being targeted more often. Some organizations reported falling victim to scams targeting data such as W-2 information even though they were able to successfully identify and avoid other more traditional wire fraud scams. Malicious actors may be trying to take advantage of these “softer” targets in the human resources, bookkeeping, or auditing departments by performing attacks that are not as easily recognizable as large-dollar wire fraud attempts.
- Point-of-sale chatter remains relatively low. Point-of-sale breaches are not making as many headlines, but breaches so far this year have proven that for many organizations the associated costs are as high or higher than they have ever been.
- Ransomware and extortion threats continue to grow. The first half of 2016 saw a spike in ransomware and extortion-related tags as researchers, organizations, and government officials tried to deal with the growing and costly problem of data or services being held hostage for ransom.
For more threat intelligence trends, download the full Mid-Year 2016 Cyber Trends Report from SurfWatch Labs.