Yahoo and Equifax were both back in the news this week due to new details emerging around their respective data breaches, including Yahoo revising the number of affected accounts to three billion and Equifax’s former CEO being grilled before Congress.
Yahoo had previously stated that its 2013 data breach affected one billion user accounts, which made it the most widespread data breach in history. On Tuesday Verizon Communications, which acquired Yahoo for $4.48 billion in June, tripled the number of impacted accounts to include all three billion of Yahoo’s users accounts. The breach was particularly egregious not only because of its size, but because it involved sensitive information such as the security questions and answers and backup email addresses used to recover accounts. Yahoo’s massive 2013 breach is in addition to a separate, previously disclosed breach that affected 500 million Yahoo accounts in 2014.
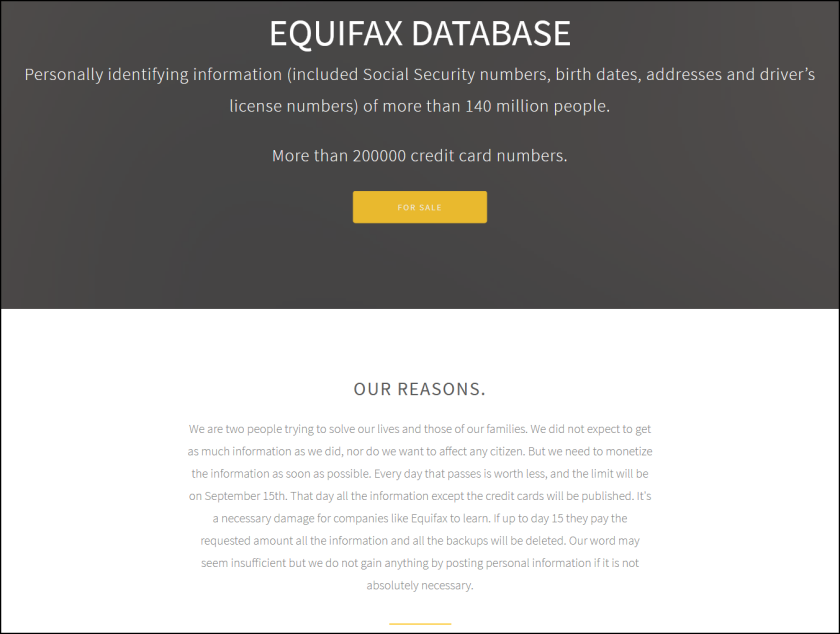
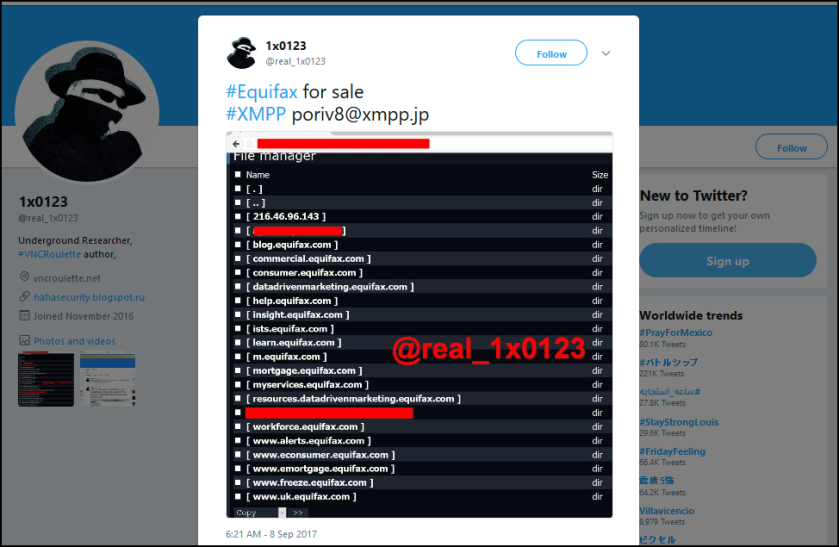
This week also saw the congressional testimony of Equifax’s former CEO Richard Smith. Smith said the breach was due to a combination of “both human error and technology failures” around implementing an Apache Struts patch made available on March 6, which was not patched for months despite a policy stating patches occur within a 48-hour time period. The testimony was met with harsh criticism from some lawmakers. For example, Sen. Elizabeth Warren (D-Mass.) questioned the entire business model of Equifax, claiming that the company has no incentive to protect consumer data and highlighting various avenues through which the company is making “millions of dollars off its own screwup.” Warren said that Equifax may “actually come out ahead” financially in regards to its breach, which affects 145 million people.
Despite the ongoing fallout, the IRS renewed a $7.25 million contract with Equifax to use its services to verify taxpayer identities. The contract drew major criticism; however, IRS Deputy Commissioner Jeffrey Tribiano said it was a necessary “stop gap” so millions of taxpayers did not lose access to their transcripts.
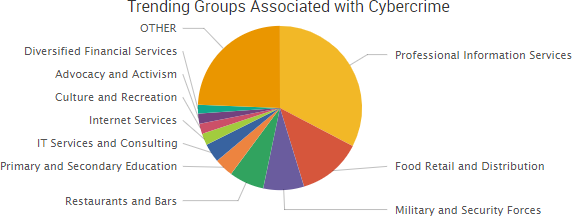 Other trending cybercrime events from the week include:
Other trending cybercrime events from the week include:
- Newly announced data breaches: Auburn Eye Care Associates of California was hacked by TheDarkOverlord and thousands of patients records were stolen from its electronic health record system. Cabrillo Community College District said that it discovered unauthorized access to a server containing a database with student orientation information. The Online Traffic School said that customer information was compromised due to an individual gaining unauthorized access to part of its network. Northwestern Mutual Life Insurance Company said that customer information was compromised due to a financial advisor falling for a scam that led to a malicious actor gaining remote access to a desktop computer multiple times. The law firm Clark Hill had its systems accessed by Chinese hackers and sensitive documents related to Chinese dissident Guo Wengui were subsequently released on Twitter. Phoenix Inn Suites is the latest hotel to issue a breach notification tied to the Sabre Hospitality Solutions SynXis Central Reservations system.
- Organizations expose data: A misconfigured database that collected data on activity on a number of NFL-related domains such as the National Football League Players Association’s website exposed the data of 1,133 NFL players and agents. The database also included a ransom message from February 2017 similar to the ones targeting other Elasticsearch servers earlier this year — indicating that the data was accessed by cybercriminals. FlexShopper said a database containing payment and other customer information may have been exposed on the internet for several days. National Bank of Canada said that 400 customers had their personal information exposed due to a website glitch. Graton Resort and Casino, Kenco, and North Carolina A&T State University all announced breaches related to inadvertently disclosing sensitive customer, employee, and student data via email attachments.
- Other notable incidents: U.S. government officials believe that the personal cellphone of chief of staff John Kelly was compromised, and the compromise may date back to December 2016. The R6DB gaming service, which provides statistics for Rainbow Six Siege gamers, said that an automated bot breached its PostgreSQL installation and wiped the database then demanded a ransom payment. Etherparty said it had to shut down its website for 90 minutes after discovering a fraudulent contribution address on the site just an hour after the ICO for its FUEL token went live. The City of Englewood said that it was hit with a ransomware infection. The UK National Lottery and Kazakhstan banks reported service disruptions due to DDoS attacks.
- Arrests and legal actions: A federal indictment alleges that a former Hewlett-Packard Enterprise Corp. employee intentionally caused damage to Oregon’s Medicaid Management Information System (MMIS) after being laid off, resulting in an eight-hour loss of functionality for the system. The former principal of Seven Peaks School in Oregon is being sued for allegedly downloading thousands of private documents related to the students and staff, including psychological evaluations of students.
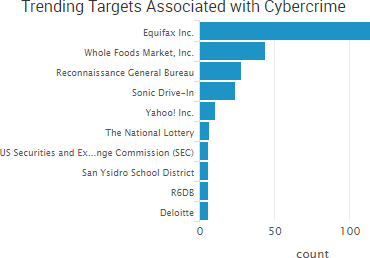
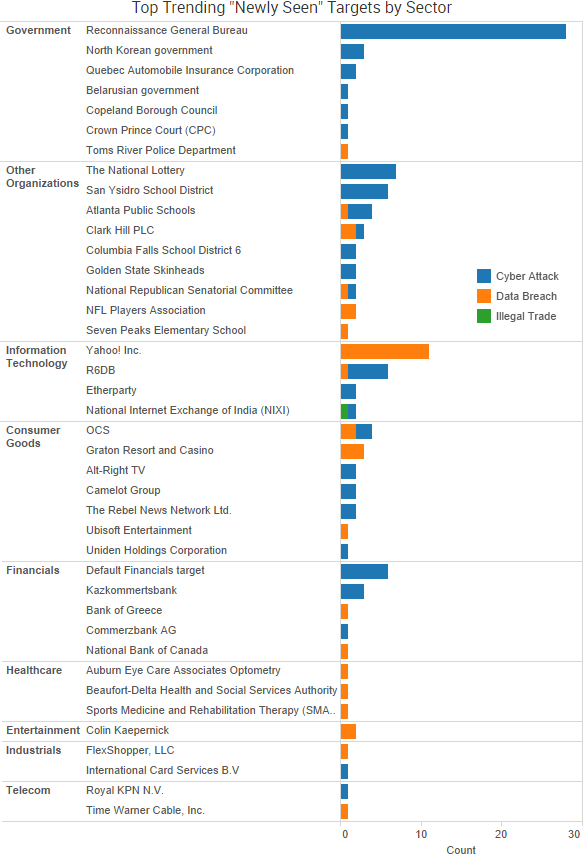
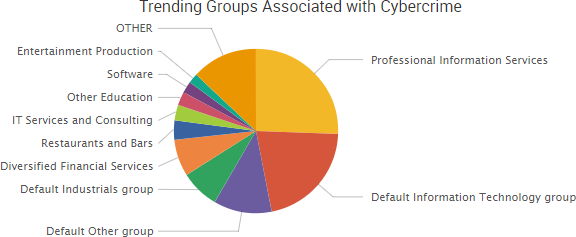
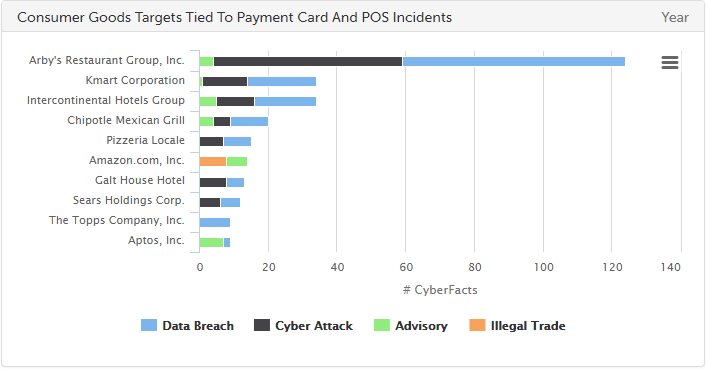
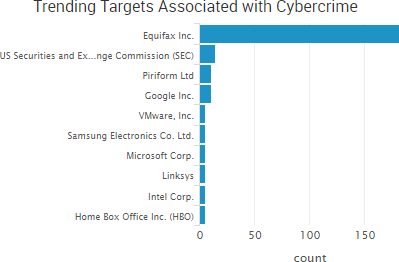
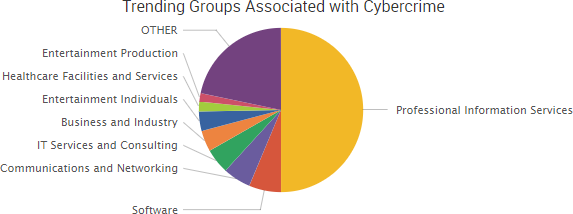
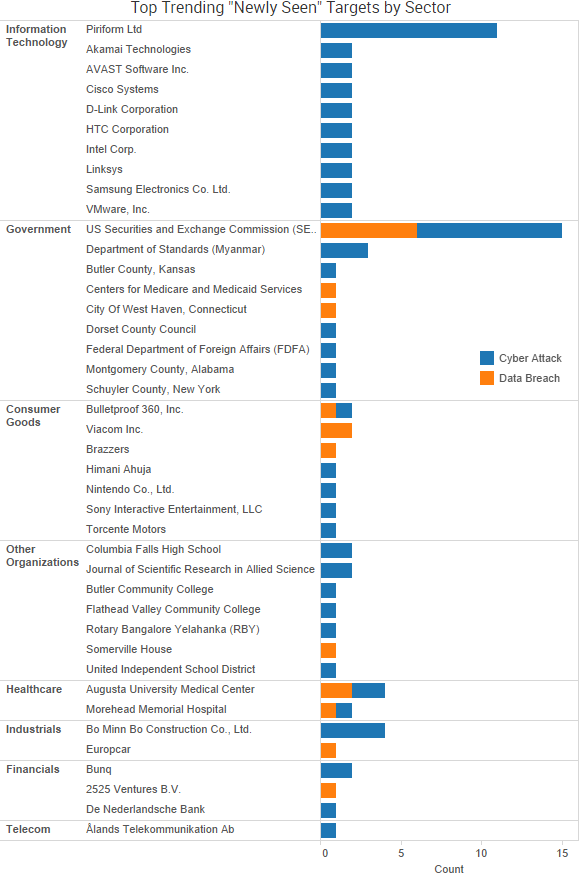
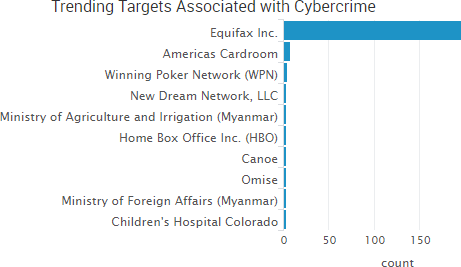
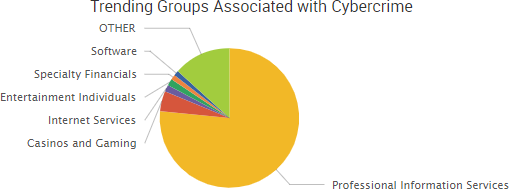
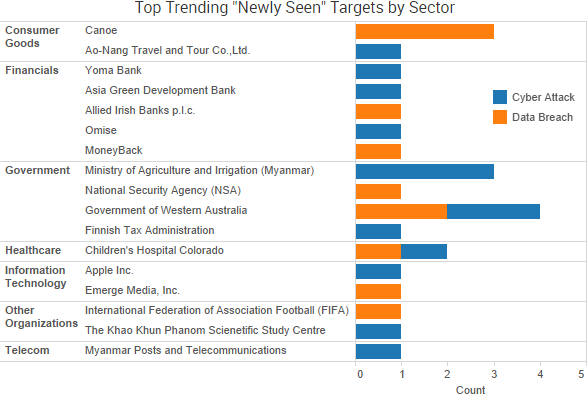
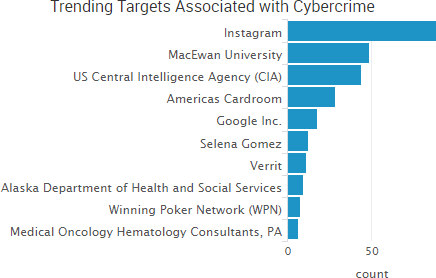
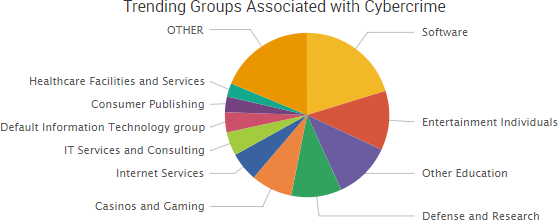
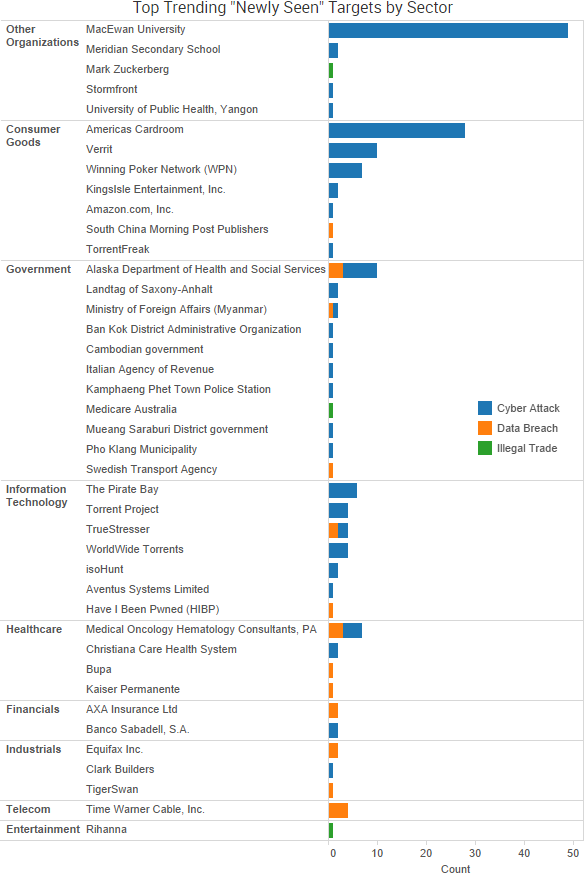
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
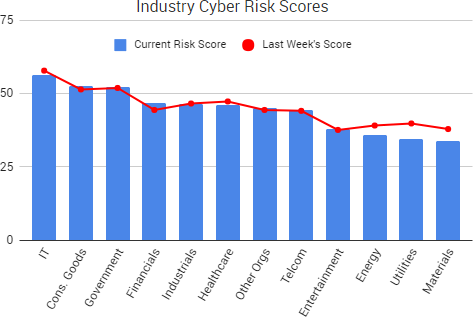
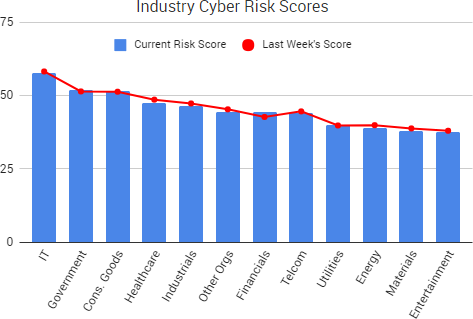
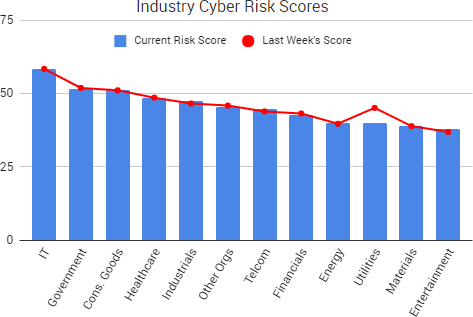
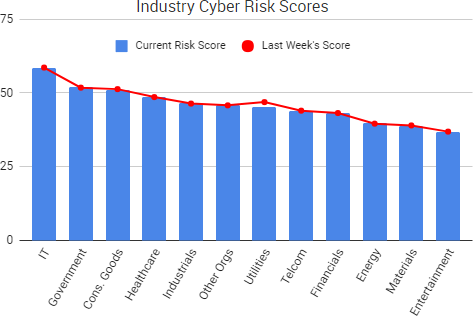
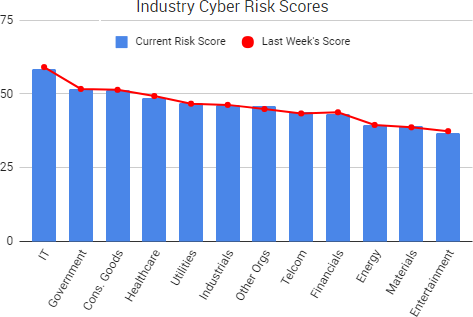
 Cyber Risk Trends From the Past Week
Cyber Risk Trends From the Past Week
 On Thursday, The Wall Street Journal reported that the Russian government was able to steal highly classified NSA material from an NSA contractor who removed the classified material and put it on his home computer without the NSA’s knowledge.
On Thursday, The Wall Street Journal reported that the Russian government was able to steal highly classified NSA material from an NSA contractor who removed the classified material and put it on his home computer without the NSA’s knowledge.
The sources said that the breach, which occurred in 2015, was first discovered in the spring of 2016 and included details about how the NSA penetrates foreign computer networks, code it used for such spying, and details on how the NSA defends networks inside the U.S.
Sources told the WSJ that the hackers appear to have used the antivirus software created by Russia-based Kaspersky Lab in order to identify the files on the contractor’s computer. The paper also reported that it is the first known incident of the popular antivirus software being exploited by Russian hackers to conduct espionage against the U.S. government.
Kaspersky Lab said it “has not been provided any information or evidence substantiating this alleged incident, and as a result, we must assume that this is another example of a false accusation.”
The alleged NSA breach provides some insight into reports that the FBI has been urging private companies throughout the year to discontinue using Kaspersky products due to intelligence that indicated the company is an unacceptable threat to national security. In addition, the Department of Homeland security issued a directive in September ordering federal agencies to take actions to ultimately remove Kaspersky-related products from government computers.
The breach also appears to be separate from the incidents involving NSA contractor Harold T. Martin III, who hoarded large quantities of sensitive NSA data and hacking tools in his home, and TheShadowBrokers, a group that is best known for the April 2017 release of stolen NSA exploits such as EternalBlue, among others. As we noted in our August blog, officials have not linked TheShadowBrokers to Martin’s insider theft, and it appears the same can be said of the newly reported NSA breach. However, this new incident now makes two recent insiders who have successfully taken highly confidential NSA data home — and at least one case of that data then being successfully targeted by foreign hackers once it was in a less secure environment.





 Last week the developer of CCleaner announced that approximately
Last week the developer of CCleaner announced that approximately 
 Security researchers are advising people to ensure their Bluetooth connections are turned off when not in use after the discovery of a series of vulnerabilities that can be used to compromise billions of Bluetooth-enabled devices.
Security researchers are advising people to ensure their Bluetooth connections are turned off when not in use after the discovery of a series of vulnerabilities that can be used to compromise billions of Bluetooth-enabled devices.


 Security researchers are once again warning that the energy sector is the target of increased cyber-attacks. Symantec said that it has observed increased activity from the actors behind the Dragonfly 2.0 campaign and that there are strong indicators of recent attacks against organizations in the U.S., Turkey, Switzerland, and elsewhere.
Security researchers are once again warning that the energy sector is the target of increased cyber-attacks. Symantec said that it has observed increased activity from the actors behind the Dragonfly 2.0 campaign and that there are strong indicators of recent attacks against organizations in the U.S., Turkey, Switzerland, and elsewhere.