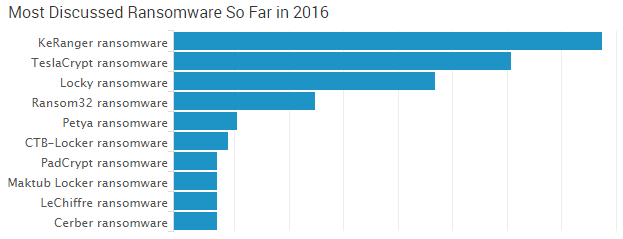
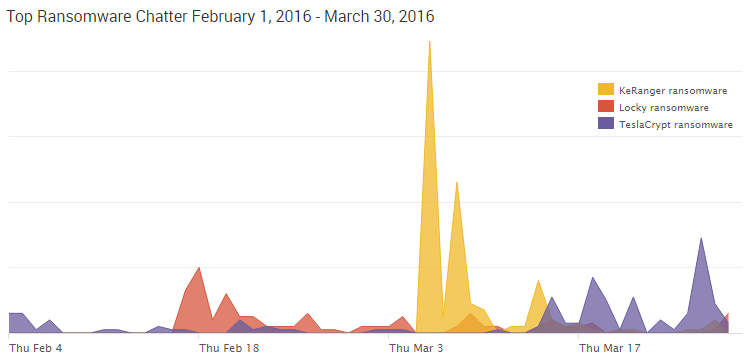
The password: love it or loathe it, this concept and practice have been a cornerstone of basic security for a long time. After covering cybercrime for the last few years, I have come to the conclusion that people hate passwords.
Let’s examine that – why do people hate passwords?
“I think people hate passwords because it’s something else to remember – and something else to forget,” said Aaron Bay, Chief Analyst for SurfWatch Labs. “The need to protect ourselves, and our information, has snowballed into this large, terrible thing we have in place now. Hardware and software have been developed to combat it, but there is still the problem of now someone else is in control of your access.”
Bay points to the compromise of the RSA’s SecureID and the recent vulnerability found in the password management program KeePass to further explain the complications of passwords.
“In 2011, the RSA SecureID was compromised, and the thousands of organizations – including the U.S. Government – that relied on their tokens were now at risk. The password manager KeePass recently had a flaw discovered that allowed attackers to steal passwords directly from the database. These are two examples where these beneficial systems have failed. It is safe to say that these systems, and others, will fail again at some point in the future.”
Without using programs to help with the process of utilizing strong passwords, the practice can be daunting. Listeners of the SurfWatch Cyber Risk Roundup who are familiar with our “Funny Story of the Week” have heard us talk about bad password practices. While some of the most common passwords are viewed in a humorous nature – “123456” tops the charts every year – there is a real security concern with this trend.
The Password Reuse Problem
The main problem is one of volume. Websites, work accounts, devices, iPhone or Android apps, and even credit cards all require passwords or pins. As a result of people reusing passwords, a number of companies have made headlines for cyber incidents, despite the fact they weren’t actually breached.
- Amazon: “We discovered a list of email addresses and passwords posted online. While the list was not Amazon-related, we know that many customers reuse their passwords on multiple websites. … We recommend that you choose a password that you have never used with any website.”
- United Airlines: “We recently learned that an unauthorized party attempted to access your MileagePlus account with usernames and passwords obtained from a third-party source. These usernames and passwords were not obtained as a result of a United data breach and United was not the only company where attempts were made.”
- Uber: “We investigated and found no evidence of a breach. … This is a good opportunity to remind people to use strong and unique usernames and passwords and to avoid reusing the same credentials across multiple sites and services.”
- Dropbox: “Recent news articles claiming that Dropbox was hacked aren’t true. Your stuff is safe. The usernames and passwords referenced in these articles were stolen from unrelated services, not Dropbox. Attackers then used these stolen credentials to try to log in to sites across the internet, including Dropbox.”
“Password reuse is very common and more often than not leads to additional compromises when peoples’ passwords are exposed in the latest data breach,” Bay said, adding that each website having slightly different requirements also makes it harder for users to create unique passwords they can remember. “We not only have to remember the different passwords, when we have to change our passwords we have to remember the rules and make sure the new password doesn’t break them.”
I think everyone understands that remembering passwords can be a hassle. Some people attempt to circumvent this step and simply write the password down next to their work terminals, but that completely negates the point of a password as it is now in view for everyone to see. If you don’t think your co-workers are capable of utilizing your password for malicious purposes – as well as a practical joke – don’t be fooled. Several experts and reports have indicated that insider activity is one of the leading threats organizations face in combating cybercrime. According to SailPoint’s 7th Annual Market Pulse Survey, “1 in 5” employees share their passwords and login information with members of their team.
“Compounding the problem, 56% of respondents admitted to some level of daily password reuse for the corporate applications they access, with as many as 14% of employees using the same password across all applications,” the survey found.
Moving Beyond Passwords?
What are the alternatives to passwords? Last year, Yahoo decided to create an option for users that would allow them to log into their accounts without using a password. Instead of a password, a link would be sent via text message to a user’s phone that would validate their access.
There is also the popular topic of biometrics. In a recent example, the U.K. bank Atom launched a biometric authentication tool that utilizes a customer’s face and voice instead of a password for validation. The option to use a password still exists and the new biometric method remains as an option for customers.
Biometrics seem to be a trend around the validation process, but passwords remain the authentication option at this time.
“Biometrics is now being regarded as ‘the next big thing’ to use to protect us,” Bay said. “When Apple introduced the fingerprint reader into the iPhone, biometrics were thrust into the public view. Millions of people, basically overnight, now had a fingerprint reader.”
Bay said the fingerprint readers do work and, for the most part, are secure.
“Is it perfect, not hardly. Is it the best we have, unsure. Is it better than many other implementations, yes, without a doubt. However, it still relies on hardware and software to be perfect. Unfortunately, history has shown that is not possible.”
Whether you like passwords or not, until a better, proven solution replaces this validation method it is imperative that your passwords are secure. This message needs to be communicated and driven home to employees – even if they hate passwords.