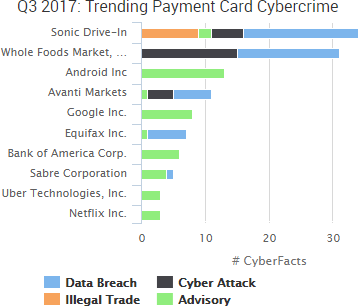
Uber was the week’s top trending cybercrime target due to the announcement of a year-old breach that affects 57 million customers and drivers. In addition, the company admitted to paying the hackers $100,000 in an effort to keep the breach out the public eye.
The data was stolen in October 2016, and it includes the names, email addresses, and phone numbers of 50 million Uber riders, as well as the driver’s licenses and personal information of approximately 7 million drivers. Bloomberg reported that two attackers accessed a private GitHub repository used by Uber software engineers, used login credentials they obtained there to access data stored on an Amazon Web Services account that handled computing tasks for the company, and then discovered an archive of rider and driver information they later used to extort the company.
The breach announcement is just the latest chapter is Uber’s security and legal woes, and Dara Khosrowshahi, who took over as chief executive officer in September, said that the company is “changing the way we do business” moving forward. The payment of $100,000 to conceal the breach and have the attackers delete the stolen information led to the firing of Uber’s chief security officer and another employee for their roles in the incident. Reuters reported that three senior managers within Uber’s security unit have since resigned as well.
Europe’s national privacy regulators have formed a task force to investigate Uber’s breach and the company’s attempt at concealing it from regulators. In addition, numerous state attorneys general have initiated investigations or lawsuits related to the breach. The breach also came a week before three senators introduced a national bill that would require companies to report data breaches within 30 days.
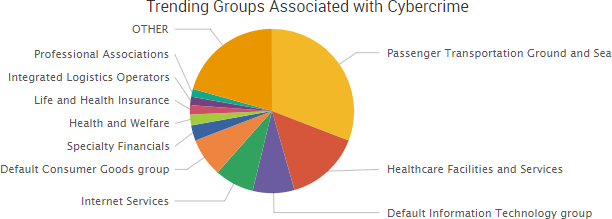
Other trending cybercrime events from the week include:
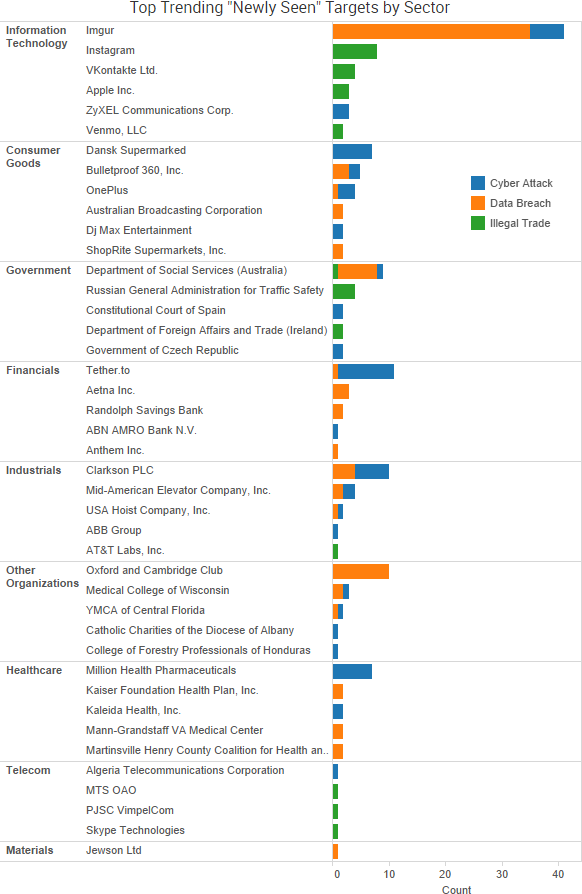
- Organizations continue to expose data: Researchers found 111 GB of internal customer data from National Credit Federation exposed online via a publicly accessible Amazon S3 bucket. Researchers discovered three publicly accessible Amazon S3 buckets tied to Department of Defense intelligence-gathering operations that contain at least 1.8 billion posts of scraped internet content over the past 8 years. Researchers discovered data belonging to the United States Army Intelligence and Security Command (INSCOM) exposed on the internet, including internal data and virtual systems used for classified communications. A security researcher discovered a file containing 11 million email addresses and plaintext passwords for users of Armor Games and Coupon Mom. Dalhousie University is notifying 20,000 individuals that their personal information was inadvertently saved to a folder accessible by faculty, staff, and students.
- Email incidents lead to breaches: YMCA of Central Florida is notifying individuals that an unauthorized person gained access to several employee email accounts, potentially compromising a variety of personal information including ID cards, financial information, and health information. The Medical College of Wisconsin said that 9,500 patients had their information compromised due to a spear phishing attack on the school’s email system. Ireland’s Central Statistics Office said that 3,000 former employees had their personal information exposed due to an error that resulted in their personal P45 information being sent via email.
- More extortion attacks: The British shipping company Clarksons said that it was the victim of a data breach and that the actors behind the breach have threatened to release some of the stolen data if a ransom is not paid. The Texas Department of Agriculture, which oversees school breakfast and lunch programs, said that several East Texas school districts were affected by a ransomware infection on a department employee’s computer. A server used by USA Hoist Company, Mid-American Elevator Company, and Mid-American Elevator Equipment Company to store employee and vendor information was infected with ransomware by a group claiming to be TheDarkOverlord.
- Other notable incidents: Imgur said that it was recently notified by a researcher of a data breach that occurred in 2014 affecting the email addresses and passwords of 1.7 million user accounts. Combat Brands is notifying customers of breach of payment card data involving cards used at fightgear.com, fitness1st.com, ringside.com, and combatsports.com between July 1, 2015 and October 6, 2017. The Australian Department of Social Services is notifying 8,500 individuals that data relating to staff profiles within the department’s credit card management system prior to 2016 has been compromised due to a breach at a contractor. Brinderson, L.P. is notifying employees that their personal information may have been compromised due to unauthorized access to one of its computer systems.
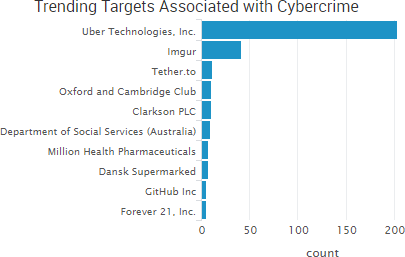
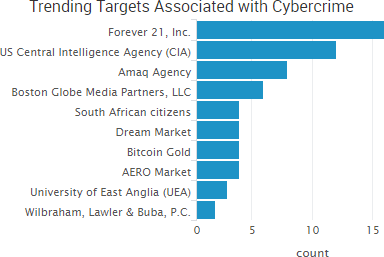
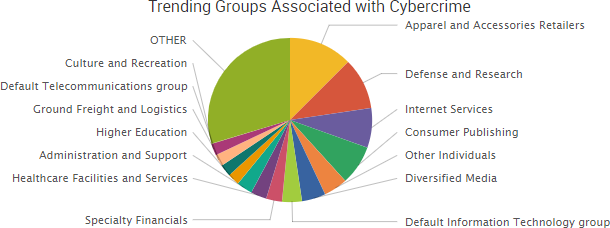
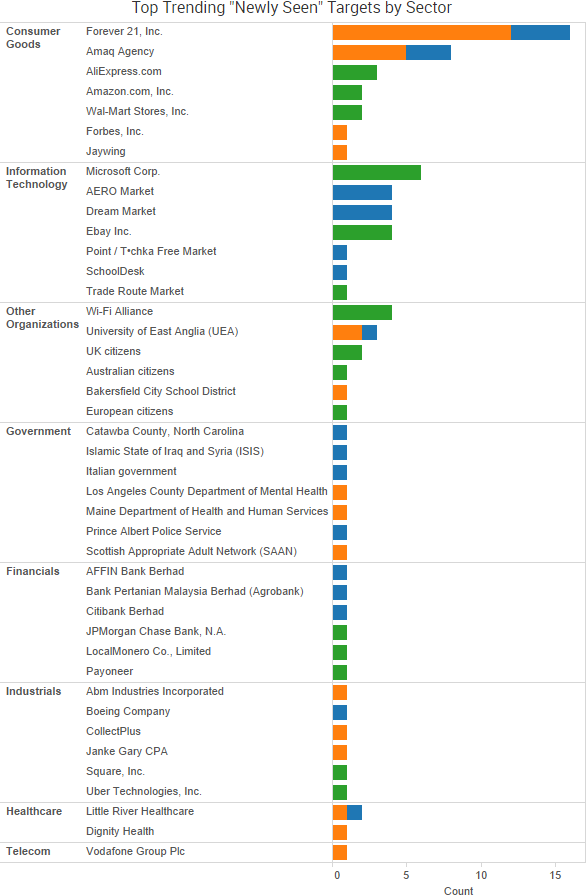
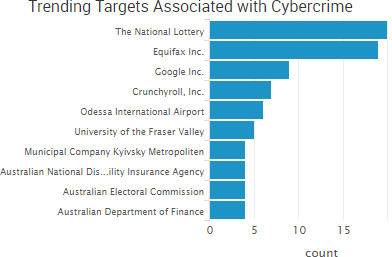
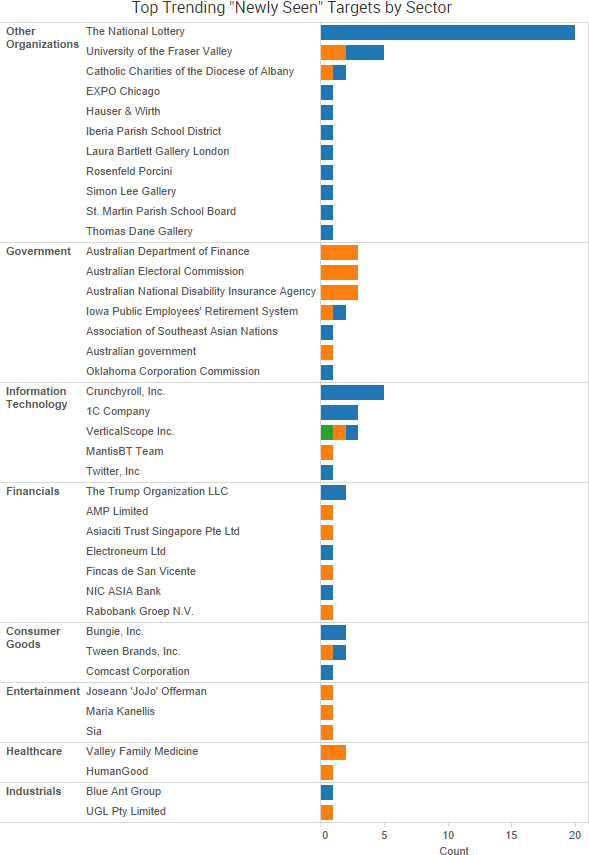
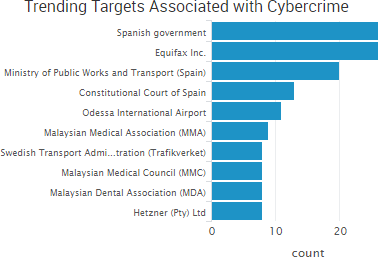
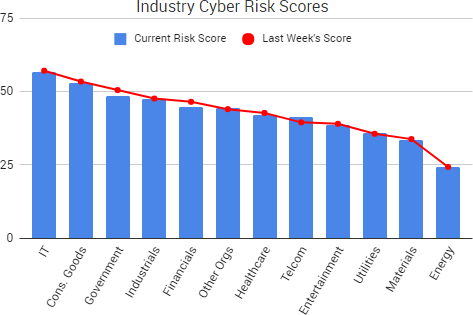
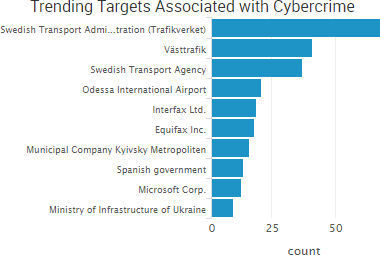
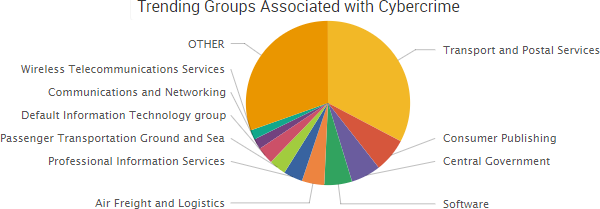
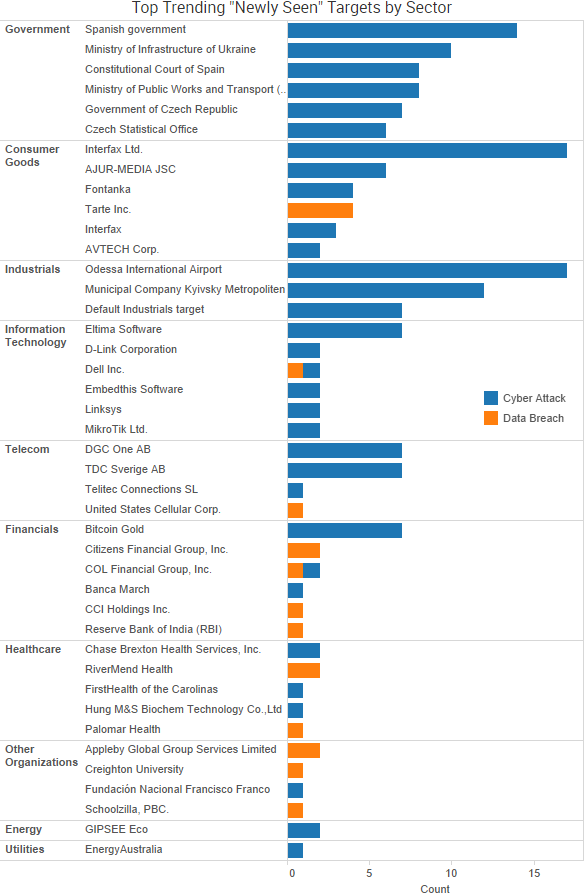
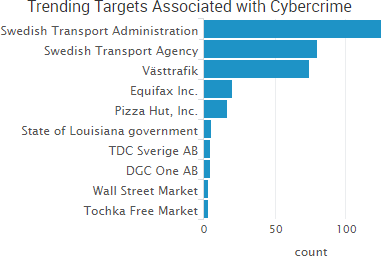
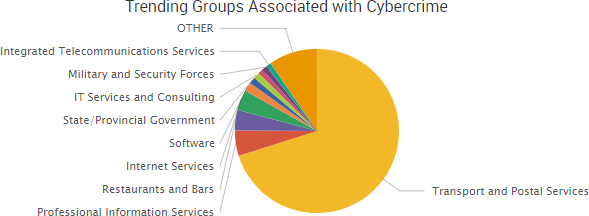
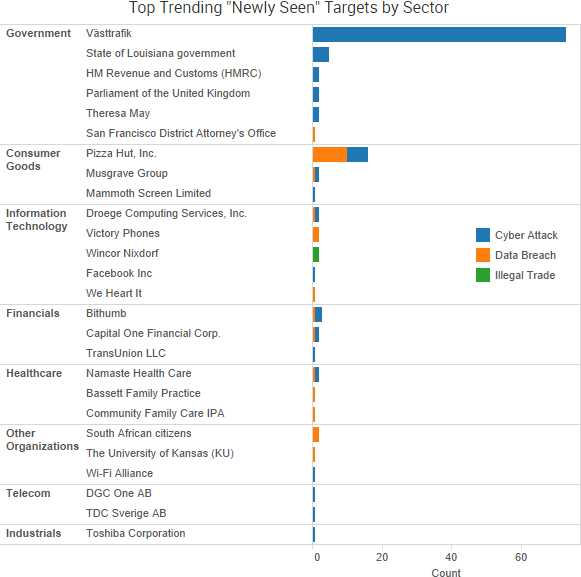
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
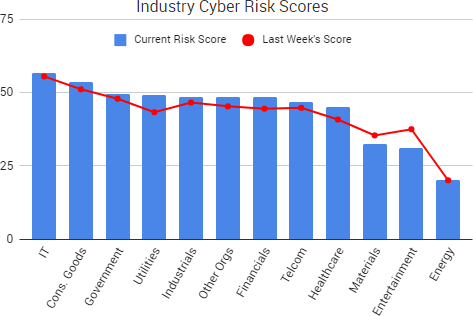
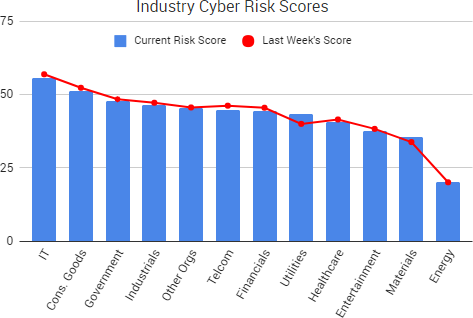
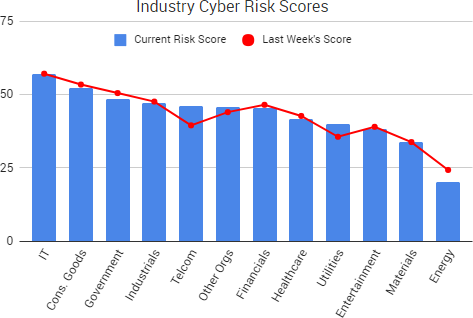
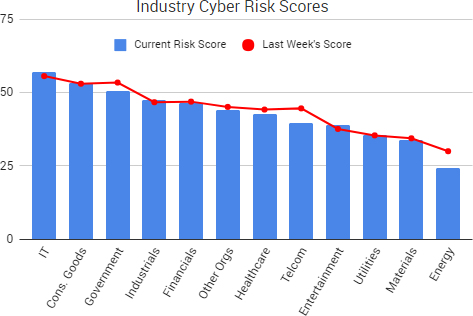
Cyber Risk Trends From the Past Week
 This past week saw several notable legal actions against cybercriminals.
This past week saw several notable legal actions against cybercriminals.
The most prominent figure was Roman Valeryevich Seleznev, aka Track2, who was sentenced to 14 years in prison for his role in the 2008 defrauding of Atlanta-based payment card processor RBS Worldpay – which led to the theft of 45.5 million debit card numbers and $9.4 million in fraudulent ATM withdrawals – as well as his role in selling stolen payment card and personal data to members of carder.su – a cybercriminal website that resulted in victims losing at least 50 million dollars.
As SurfWatch Labs noted in April, Seleznev is already serving a 27-year prison sentence, the longest ever related to cybercrime, for his role in a separate $170 million payment card fraud operation. The prosecutors in that case described Seleznev as “the highest profile long-term cybercriminal ever convicted by an American jury” and a “pioneer” and “revered” point-of-sale hacker in the criminal underworld. Seleznev’s two sentences will be served concurrently.
In addition, the U.S. government has charged three Chinese nationals with hacking into Siemens AG, Trimble Inc, and Moody’s Analytics between 2011 and 2017 to steal business secrets. According to the indictment, the three defendants were associated with the Chinese cybersecurity firm Guangzhou Bo Yu Information Technology Company Ltd. Government officials told Reuters that most if not all of the firm’s hacking operations are state-sponsored and directed; however, the case is not being prosecuted as state-sponsored hacking.
The week also saw the guilty plea of one of the four men indicted earlier this year on charges related to the hacking of Yahoo. Karim Baratov, 22, a Canadian national and resident, pleaded guilty for his role in assisting the three other men who are charged and remain at large in Russia. The three other men are accused of hacking Yahoo’s network, and Baratov said in his plea agreement that he hacked more than 11,000 webmail accounts in total from around 2010 until March 2017, including accounts of individuals of interest to the FSB as directed by one of the other men. Baratov’s sentencing hearing is scheduled for February 20, 2018.
Finally, Europol announced that a joint law enforcement action across 26 countries had led to the arrest of 159 individuals and the identification of 766 money mules and 59 money mule organizers. The money mule transactions accounted for total losses of nearly €31 million, more than 90 percent of which was cybercrime related.



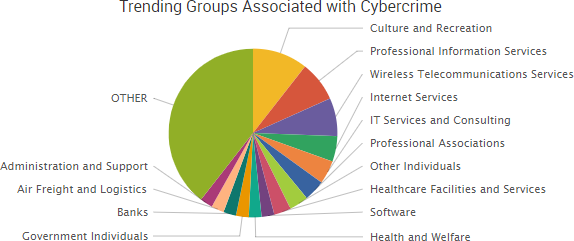
 Dark Web markets continued to make headlines this week as a key player in AlphaBay’s operations was charged and cyber-attacks against other still-active dark web marketplaces temporarily disrupted operations.
Dark Web markets continued to make headlines this week as a key player in AlphaBay’s operations was charged and cyber-attacks against other still-active dark web marketplaces temporarily disrupted operations.
 The hack of a large cache of sensitive documents from the offshore law firm Appleby, which was first
The hack of a large cache of sensitive documents from the offshore law firm Appleby, which was first 
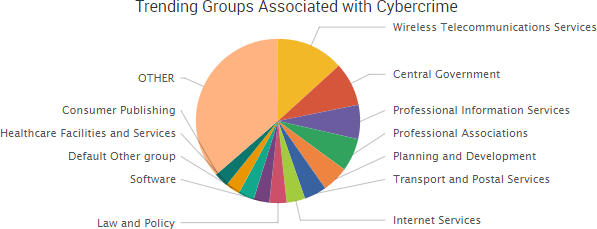
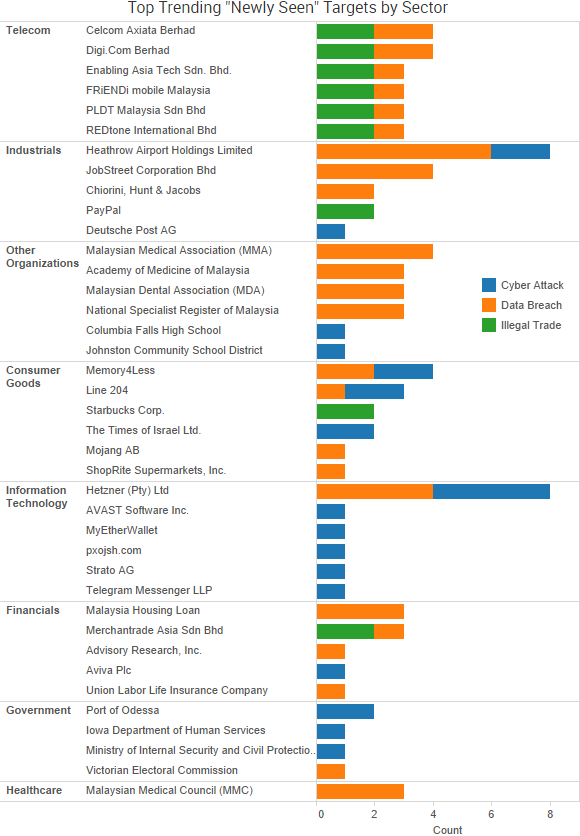
 The investigation into Russia’s alleged election-related hacking brought several new developments this past week.
The investigation into Russia’s alleged election-related hacking brought several new developments this past week.
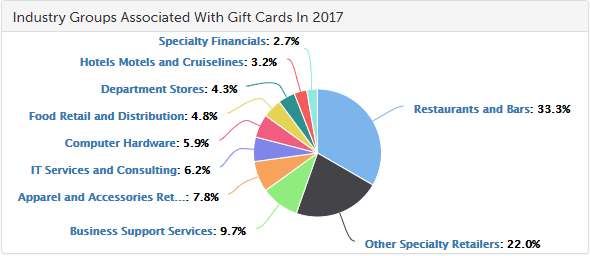

 The offshore law firm Appleby said that client data was stolen last year, and the International Consortium of Investigative Journalists (ICIJ), which obtained the hacked data, has contacted the firm over allegations of wrongdoing and says it plans on publishing a series of stories related to the breach.
The offshore law firm Appleby said that client data was stolen last year, and the International Consortium of Investigative Journalists (ICIJ), which obtained the hacked data, has contacted the firm over allegations of wrongdoing and says it plans on publishing a series of stories related to the breach. 



 Cyber Risk Trends From the Past Week
Cyber Risk Trends From the Past Week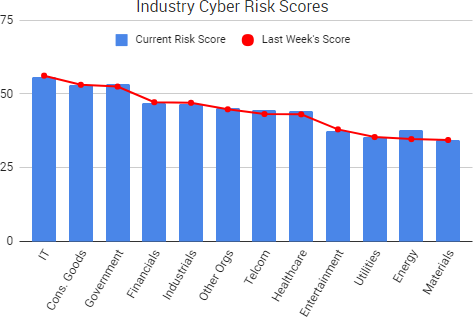 Researchers have discovered a vulnerability, dubbed “
Researchers have discovered a vulnerability, dubbed “