TheDarkOverlord was back in the news this week due to leaking data from multiple companies after failed extortion attempts. The most prominent leak involved Netflix, which had the first 10 episodes of the fifth season of its show Orange is the New Black leaked after it refused to cave to the actor’s ransom demands. The group also claims to have unreleased shows from ABC, Fox, National Geographic, and IFC. Media outlets reported that the shows appear to have been stolen from post-production studio Larson Studios in late 2016.
It’s unclear exactly how much TheDarkOverlord demanded from Netflix to not release the episodes, but the actor once again framed its response to the failed extortion attempt by trying to appeal to future victims, essentially arguing that paying up will cost them a lot less money than having their data released.
“It didn’t have to be this way, Netflix,” the actor wrote in a post on April 29. “We figured a pragmatic business such as yourselves would see and understand the benefits of cooperating with a reasonable and merciful entity like ourselves. … And to the [other networks]: there’s still time to save yourselves. Our offer(s) are still on the table — for now.”
TheDarkOverlord has not yet released episodes allegedly stolen from other networks. However, three healthcare providers had data dumped by the actor on May 4. Aesthetic Dentistry in New York City and OC Gastrocare in California were both hacked last year by TheDarkOverlord, databreaches.net reported, and their dumps from last week contained 3,496 patient records and 34,100 patient records, respectively. The third dump was the biggest, containing more than 142,000 patient records allegedly stolen from Tampa Bay Surgery Center.
That large dump appears to be tied to a previously undisclosed breach, and TheDarkOverlord tweeted that the “clinic didn’t do anything wrong except annoy us.” That annoyance likely stemmed from the fact that the center did not cave to the group’s ransom demands, just like numerous other organizations targeted over the past year.

Other trending cybercrime events from the week include:
- Payment card breaches continue: Sabre announced that it is investigating a data breach after discovering “unauthorized access to payment information contained in a subset of hotel reservations processed through our Hospitality Solutions SynXis Central Reservations system.” More than 32,000 properties use Sabre’s SynXis reservations system, which is described as an inventory management Software-as-a-Service application. Sabre told customers that the unauthorized access has been “shut off” and that there are not any additional details to share at this time.
- Numerous ransomware infections reported: An April 22 ransomware infection at electronic health records vendor Greenway Health disrupted services to 400 client organizations using the vendor’s Intergy cloud-hosted platform, and half of those customers were still waiting to have a full EHR services restored on Monday, May 1. Pekin Community High School’s computer systems were infected with ransomware, and the actor demanded $37,000 in order to restore the encrypted files. Ransomware infected the computer systems of Cambrian College in Ontario and demanded a $54,000 payment. The school’s web portals, grade report, and student learning management systems were disrupted, and final grades and spring semester registration had to be postponed for several days. The law firm Moses Afonso Ryan Ltd was infected with ransomware last year that demanded a $25,000 ransom payment, and after paying a negotiated ransom payment the firm then had to renegotiate an additional payment when the first key purchased to decrypt the documents did not work.
- Large amounts of data exposed: Around 135 million Aadhaar ID numbers and around 100 million bank account numbers have been leaked from four Indian government portals, according to a report released by The Centre for Internet and Society. The four government portals examined in the report include: National Social Assistance Programme, National Rural Employment Guarantee Act, Daily Online Payment Reports under NREGA, and Chandranna Bima Scheme. Data belonging to Alliance Direct Lending Corporation was found publicly available online and as a result at least 550,000 customers have had their personal information exposed. According to MacKeeper, the leaked data contained 124 files (with five to ten thousands records each) that contained financing records broken down by dealerships as well as 20 audio recordings of customers agreeing to auto loans or refinancing of auto loans.
- Other notable cybercrime news: Retina-X Studios announced that in February 2017 a malicious actor was able to break into a server that held database tables for its Net Orbit, PhoneSheriff, and TeenShield products, and the actor then wiped “any data that he was able to force access to.” According to the company, the actor was able to find a vulnerability in a decompiled and decrypted version of a now-discontinued product in order to achieve the unauthorized access. Grey Eagle Resort & Casino in Calgary has had an additional 1.7 GB of data dumped, and the hackers behind the dump indicated that the data would be uploaded to torrent sites “soon” and that more data dumps would follow in the coming weeks. The casino initially had data released by hackers in January, and the new dump appears to include more data that was stolen prior to the first leak.
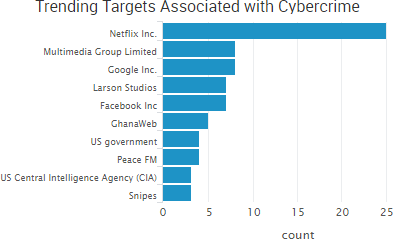
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.

Cyber Risk Trends From the Past Week
 Several recent cybercrime events have proven that although two-factor authentication is an effective way to prevent fraudulent transactions, malicious actors are focusing their efforts on ways to defeat that increasingly popular layer of security.
Several recent cybercrime events have proven that although two-factor authentication is an effective way to prevent fraudulent transactions, malicious actors are focusing their efforts on ways to defeat that increasingly popular layer of security.
German newspaper Süddeutsche Zeitung reported that customers of O2-Telefonica had funds removed from their bank accounts due to malicious actors exploiting a flaw in Signalling System No. 7 (SS7) — which is used by telecom companies around the world use to ensure their networks interoperate — in order to intercept the text message authentication codes sent to customers and then use those codes to successfully steal funds from customers’ bank accounts. The attack was carried out from the network of an unnamed “foreign provider,” and one expert told the German paper that insider access could be bought for as little as €1000 in order to carry out similar attacks.
The flaw in SS7 has been known since 2014, and in 2015 60 Minutes aired a segment in which researchers demonstrated how U.S. Representative Ted Lieu’s phone messages and conversations could be intercepted. Lieu said the recent theft is yet another example of the insecurity of text-based, two factor authentication:
“Everyone’s accounts protected by text-based two-factor authentication, such as bank accounts, are potentially at risk until the FCC and telecom industry fix the devastating SS7 security flaw. Both the FCC and telecom industry have been aware that hackers can acquire our text messages and phone conversations just knowing our cell phone number. It is unacceptable the FCC and telecom industry have not acted sooner to protect our privacy and financial security. I urge the Republican-controlled Congress to hold immediate hearings on this issue.”
In addition, the UK’s National Fraud & Cyber Crime Reporting Centre is warning that malicious actors are continuing to use “SIM splitting” attacks to take control of victims’ phone numbers, authenticate transactions, and steal money from bank accounts. Like the SS7-based attacks, malicious actors first gain access to the victim’s bank accounts via phishing, malware, or cybercriminal markets — but in this case the actors then successfully report their phone lost or stolen in order to active the SIM card on a new phone and intercept communications. The fraudsters then transfer money from the victim’s account to a parallel business account they opened, and when the bank calls or texts to verify the transactions, they are in control of the victim’s phone number and can confirm the fraudulent transactions. In both cases, malicious actors have proven that they can successfully circumvent two-factor authentication with a little extra legwork.
