The week’s top trending event was the compromise at Freedom Hosting II, which has been estimated to host as much as 20 percent of active dark web sites. As a result, thousands of dark web sites were taken offline, and the stolen data has since been widely shared.
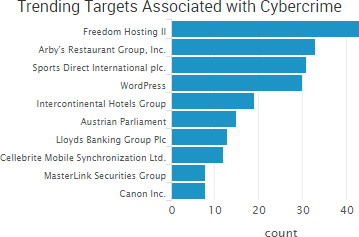 Security researcher Troy Hunt, who reviewed some of the data, said that 381,000 email addresses were exposed along with a 2.2GB MySQL file that contained database backups of customers with “a very broad range of data from different systems.” Hunt added that “a significant amount” of that data is illegal. The hacker taking credit for the incident told Motherboard that the discovery of 10 sites hosting child pornography was the impetus for escalating the attack from read-only access to gaining system privileges, which was done using a 21-step process.
Security researcher Troy Hunt, who reviewed some of the data, said that 381,000 email addresses were exposed along with a 2.2GB MySQL file that contained database backups of customers with “a very broad range of data from different systems.” Hunt added that “a significant amount” of that data is illegal. The hacker taking credit for the incident told Motherboard that the discovery of 10 sites hosting child pornography was the impetus for escalating the attack from read-only access to gaining system privileges, which was done using a 21-step process.
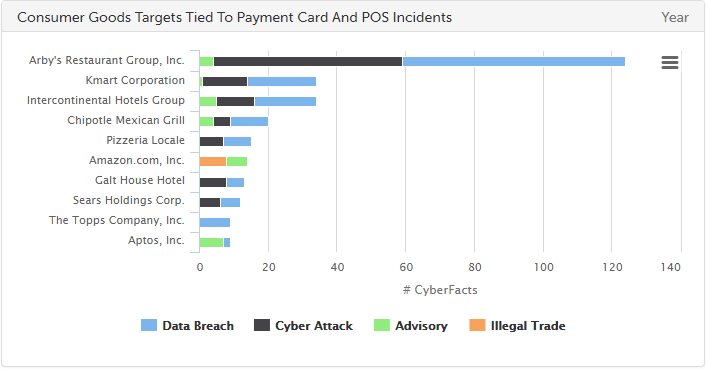
The other big news of late is the announcement of several new point-of-sale data breaches. InterContinental Hotels Group announced a point-of-sale breach affecting customers who used payment cards at the restaurants and bars of 12 properties, and fast-food chain Arby’s confirmed that malware was discovered on the payment systems of corporate locations. The incidents mirror the beginning of 2016, which saw similar breach announcement from Hyatt hotels and fast-food chain Wendy’s. The IGH breach is smaller than last year’s Hyatt announcement, which likely affected guests at 250 hotels, but the Arby’s breach may be comparable to the Wendy’s breach, which affected 1,025 locations.
More than 1,000 of the 3,300 total Arby’s restaurants are corporate owned; however, not every corporate location was affected, an Arby’s spokesperson said. Arby’s has yet to release official numbers or dates of the incident, but PSCU, a service organization that serves more than 800 credit unions, issued a non-public alert saying that more than 355,000 payment cards issued by PCSU member banks were compromised due to an incident at “a large fast food restaurant chain, yet to be announced to the public.” PCSU also estimated that the fast-food chain breach occurred between Oct. 25, 2016, and January 19, 2017.
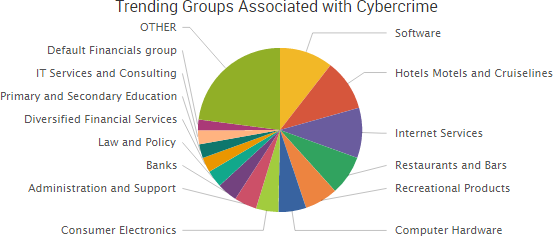
Other trending cybercrime events from the week include:
- Polish financial regulator used to spread malware: A malicious actor compromised the internal systems of the Polish Financial Supervision Authority and used the financial regulator to spread malware to Polish banks. According to The Register, a modified JavaScript file likely resulted in visitors to the regulator’s site loading an external file that led to malicious payloads. A spokesperson said the regulator decided to take its entire system offline “in order to secure evidence.” Polish media have described the incident as the most serious attack ever on the Polish banking industry.
- Extortion attacks continue: Taiwan brokerages are receiving DDoS extortion emails claiming to be from the group known as the “Armada Collective,” and several brokerages have reported DDoS attacks following those ransom demands. A malicious actor gained accessed to millions of messages and documents from the computer system of Doyen Global and leaked numerous emails from soccer star David Beckham after a failed blackmail attempt of “between €500,000 and a million.”
- More government attacks: An attack against the Italian foreign ministry last spring compromised email communications for many months, but it did not affect the encrypted system used for classified communications. The Russian-linked APT 29 hacking group has been targeting Norwegian organizations with spear phishing emails. The attorney for Little Egg Harbor believes someone within the township is stealing data from the municipal computer systems and handing that confidential information over to a local political blogger. Hackers may have used stolen passwords to gain access to a Bureau of Consular Affairs email account that serves as a contact window to 117 Taiwanese overseas offices around the world. The former NSA contractor who faced charges in 2016 relating to the theft of 50 terabytes of highly sensitive data, allegedly stole more than 75 percent of the hacking tools belonging to the NSA’s elite hacking group known as the Tailored Access Operations.
- Stolen and leaked databases: A database from the law enforcement forum PoliceOne was stolen in 2015 and the information of 700,000 members has been publicly distributed. A group of hackers claim to have a database of 20 million records stolen in 2014 from Bin Weevils, a British online children’s game owned by 55 Pixels. An actor using the name “zerodark70” is selling a database of 83,000 accounts from UPI.com, the website of the news agency United Press International. A large portion of the anti-piracy company Denuvo’s web database content is unsecured, and as a result information submitted via the company’s public contact form dating back to April 2014 has been posted online.
- Other cybercrime announcements: A vulnerability in an October 2016 software update for the Michigan Data Automated System has exposed as many as 1.87 million Michigan workers’ information to a third-party vendor. UK sports retailer Sports Direct experienced a breach due to an attacker exploiting vulnerabilities in the unpatched version of the DNN platform the company was using to run a staff portal. Computer supplier Logic Supply announced there was unauthorized access to the company’s website on February 6, 2017. UK magazine publisher Future announced that its FileSilo website was breached. Singn and Arora Oncology Hematology in Michigan announced a data breach affecting 22,000 individuals.
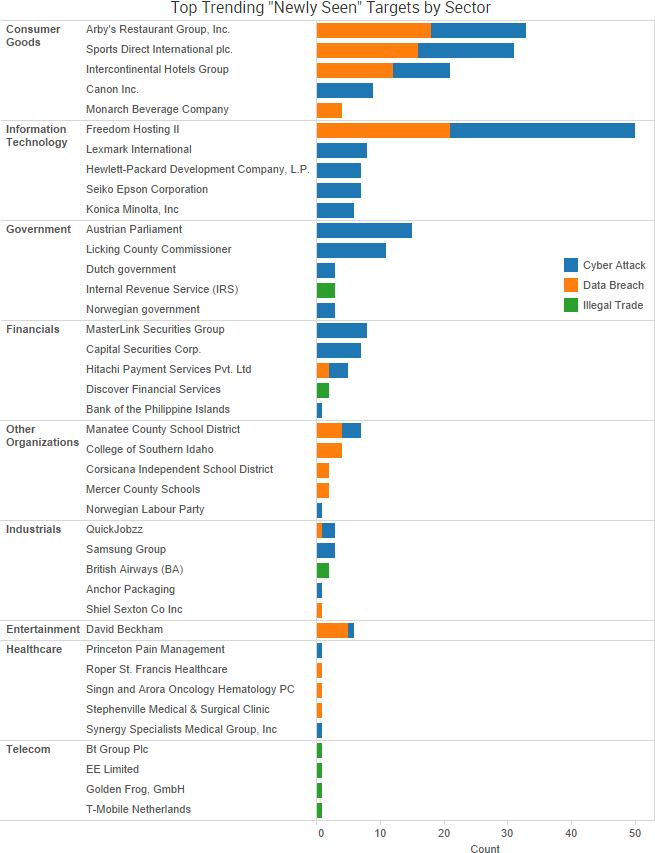
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
Cyber Risk Trends From the Past Week
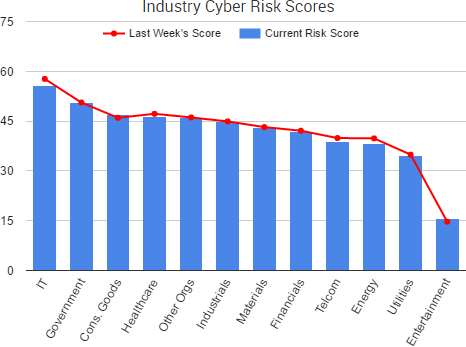 The past week saw the continuation of several stories highlighted in recent risk reports.
The past week saw the continuation of several stories highlighted in recent risk reports.
For starters, malicious actors are exploiting the recently announced severe content injection vulnerability found in the WordPress REST API, which was fixed in the WordPress 4.7.2 update. At least twenty-four different campaigns are actively defacing WordPress sites. WordFence, which said that this is “one of the worst WordPress related vulnerabilities to emerge in some time,” reported that nearly 1.9 million defaced web pages have been indexed by Google as of February 10.
WordPress has an automatic update feature to protect against newly announced exploits being used by malicious actors, but a large number of websites appear to have disabled that feature and have not updated to version 4.7.2, which has been available since January 26.
As SurfWatch Labs continues to stress in blogs and articles, cyber threat intelligence clearly shows that the security threats are not as complex as some media and vendors make them out to be. Another example of simple but effective attacks is the growing number of organizations publicly tied to W-2 related breaches. Two weeks ago we wrote that the 2017 W-2 breach count had rose to 24 organizations. By last Friday that number had risen to 40. By Monday morning, it rose again to 48 – including school districts, colleges, healthcare organizations, manufacturers, payroll providers, restaurants, retailers and more.
IRS Commissioner John Koskinen warned that “this is one of the most dangerous email phishing scams we’ve seen in a long time.” These impersonation emails, also known as business email compromise scams, have proven to be effective, and they are costly for the organizations that fall victim to them. But they are not complex. They rely on three simple and straightforward aspects all good impersonators utilize:
- A simple backstory – The malicious actors utilize the built-in story of tax season.
- Appearing as though they belong – The emails matter-of-factly request information that is relevant to the payroll and human resource departments being targeted.
- Projecting authority – The requests appear to come from a higher-up such as a school superintendent or executive.
Many attacks that lead to data breaches are not sophisticated efforts carried out by actors using zero-day exploits; rather, they are opportunistic attacks leveraging public vulnerabilities and simple social engineering tactics. When it comes to managing cyber risk, ensure your organization can defend against these basic attacks before addressing more advanced – and often far less relevant – cyber threats.


 Security researcher
Security researcher 

 The past week saw the continuation of several stories highlighted in recent risk reports.
The past week saw the continuation of several stories highlighted in recent risk reports.