Organizations are making it easy for cybercriminals by putting vast amounts of sensitive data at risk due to improper security configurations, various researchers recently warned, and this past week saw several new data breaches announced due to the public exposure of sensitive customer, patient, and other internal data.
The first warning came from Appthority, which said it discovered a “staggering amount” of leaked enterprise data from apps due to a vulnerability dubbed “HospitalGown.” The researchers said that almost 43 TB of data was found exposed across 1,000 apps due to the app developers’ failure to properly secure the backend servers with which the apps communicate and where sensitive data is stored. As a result, enterprises are leaving themselves open to data exfiltration, leakage of personal information, and potential ransom attempts, the researchers said.
In addition, John Matherly, the founder of Shodan, said that improperly configured HDFS-based servers are exposing over five petabytes of data. Matherly said he found that the smaller number of HDFS servers leak 200 times more data than MongoDB servers. He discovered 4,487 instances of HDFS-based servers exposing over 5,120 TB of data, whereas the 47,820 MongoDB servers leaked 25 TB of data. These warnings came as several organizations announced data breaches due to publicly exposing sensitive data:
- A car dealership database has been publicly exposed for more than 140 days, exposing customer, vehicle, and sales details of more than 10 million car owners, including VIN numbers.
- Victory Medical Center said patient information was discoverable via search engines dating back to 2013, and as a result around 2,000 patients had some of their personal information compromised.
- A Cosmetic Institute in New South Wales exposed the sensitive personal information, including before-and-after photos, of more than 500 female patients after uploading their data to a publicly accessible index of the clinic’s website.
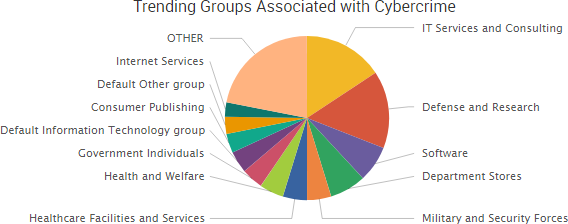
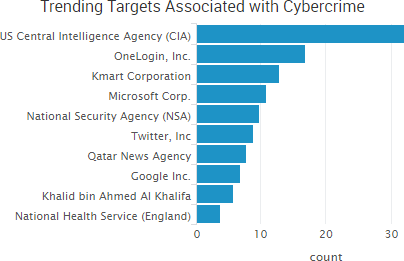
Other trending cybercrime events from the week include:
- IP theft leads to extortion attempts: CD Projekt Red said that internal files such as documents connected to its upcoming game Cyberpunk 2077 were stolen by extortionists and that those files may be released to the general public as the company will not pay the ransom. TheDarkOverlord has leaked eight episodes of ABC’s unaired show “Steve Harvey’s Funderdome” on The Pirate Bay, following through on the group’s promise to release shows stolen from Hollywood-based post-production company Larson Studios late last year.
- Variety of malicious actor arrested: A contractor at Pluribus International Corp. has been charged with leaking a top-secret National Security Agency document that describes Russian efforts to compromise the U.S. election. Chinese authorities have arrested 20 Apple employees for allegedly using the company’s internal computer system to gather and sell customers’ names, phone numbers, Apple IDs, and other data, which they sold as part of a scam worth more than 50 million yuan ($7.36 million). South Korean police have arrested a group of hackers that breached the hotel and guesthouse reservation app “Good Choice” in March and stole the personal data of more than 990,000 users. Two men were indicted for a $12 million identity theft scheme that involved thousands of victims, including students applying for financial aid. The men acquired personal identifying information of victims by either purchasing it or by obtaining the information through the Data Retrieval Tool on the Free Application for Federal Student Aid (FAFSA) website. A guidance counselor at Tryon Elementary School in North Carolina admitted to using information about some of his elementary school students in a $436,0000 Medicare scam.
- Personal data transmitted insecurely: The Mississippi Division of Medicaid is notifying 5,220 individuals that their protected health information may have been exposed due to their information not being securely transmitted when online forms were submitted. HSBC Bermuda said the personal information of customers was compromised when the company sent an email to a small number of retail banking customers that included an attachment containing HSBC Bermuda customer data. The personal information of almost 13,000 employees of Public Services and Procurement Canada was exposed due to a spreadsheet with sensitive data being sent to 180 people in the department via unencrypted email.
- Other notable incidents: Al Jazeera said that it faced a large-scale cyber-attack on Thursday against all of its systems, websites, and social media platforms. The University of Alaska is notifying 25,000 students, staff, and faculty members that their names and Social Security numbers were compromised due to a successful phishing attack in December 2016. The Maltese government has seen a significant increase in attacks believed to be carried out by Russian hacking groups in recent months — ever since Malta assumed the important position of presidency of Europe’s Council of Ministers in January. Since then, the Maltese government’s IT systems have seen a rise in phishing attacks, DDoS attempts, and malware on computer systems.
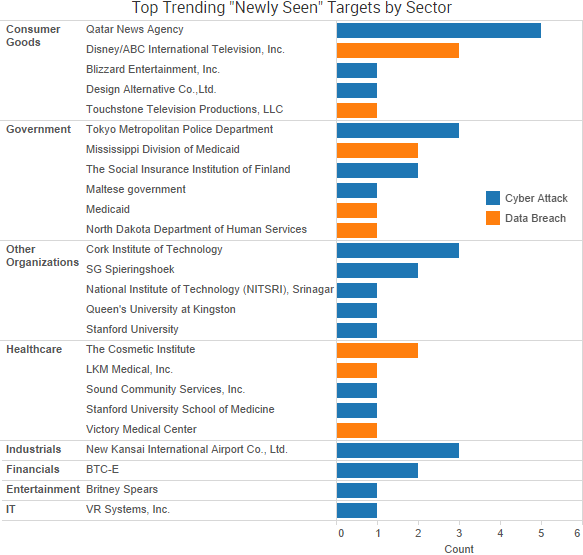
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
Cyber Risk Trends From the Past Week
 Recent incidents have confirmed that malicious actors are using cyber-attacks and data leaks to both blatantly fabricate entire news stories and discreetly drop small pieces of fake information that can potentially have wide-reaching geopolitical implications.
Recent incidents have confirmed that malicious actors are using cyber-attacks and data leaks to both blatantly fabricate entire news stories and discreetly drop small pieces of fake information that can potentially have wide-reaching geopolitical implications.
For example, on May 24, a report appeared on the official Qatari news agency’s website describing a variety of statements made by the emir of Qatar, including tensions with U.S. President Donald Trump, a desire for friendship with Iran, and praise for both Hamas militants and the leader’s relationship with Israel.
The statements received widespread attention, but Qatari officials claimed they were false — a claim now backed by the FBI, which believes the fake news operation and subsequent diplomatic crisis was orchestrated by Russian officials. The New York Times described the incident as “the opening skirmish in a pitched battle among ostensible Gulf allies.” The Times also reported that the false comments led to Saudi Arabia and U.A.E. rallying dependent Arab states to cut off diplomatic relations, travel, and trade with Qatar, as well as the fracturing of the American-backed alliance against the Islamic State and Iran.
Other Russian-tied disinformation campaigns have been more subtle. Citizen Lab recently detailed a series of “tainted leaks” tied to documents stolen from journalist David Satter. Satter had his email account compromised in a targeted phishing attack in October 2016, and those emails were then selectively modified and “leaked” on the blog of CyberBerkut, a pro-Russian hacktivist group. The modified documents were designed to both cause the programs they examined to appear more subversive of Russia than they actually were as well as to discredit specific opposition individuals and groups critical of Russian President Putin and his confidants.
Both incidents are yet another example of how much impact a disinformation campaign mixed with a little bit of hacking can have on governments around the world. As the Times warned, “Any country can get in the game for the relatively low price of a few freelance hackers.”
Motivated actors could use similar tactics to impact specific organizations with tainted data leaks. A single fake email — or even a few lines modified in a legitimate email — could easily be slipped into a larger dump and then shared with news outlets. That could lead to a crisis similar to the one facing Qatar, where leaders are forced to defend themselves against statements that were never actually made before those statements spread far and wide.