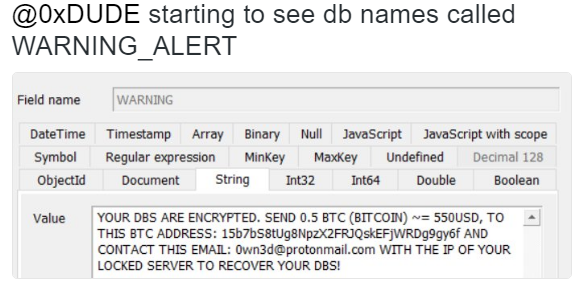
Ransomware made headlines this past week due to several infections that disrupted business operations, as well as a million dollar extortion payment that was negotiated by South Korean web hosting firm Nayana after its servers were infected with Erebus Ransomware on June 10. Nayana said the payment was necessary to restore 150 servers and the 3,400 affected client websites, most of which were for small companies and startups.
The initial ransom demand was for 5 billion won ($4.4 million) in bitcoin, but the company managed to negotiate the payment down to 1.3 billion won ($1.1 million or 397.6 bitcoin). In a statement on the company’s website (Korean language) on Thursday, Nayana CEO Hwang Chilghong said he knows the company should not negotiate with hackers, but that the damage was too widespread and too many people would be harmed if the company did not pay the extortion.
WannaCry was also back in the news this week due to Honda Motor saying that plants in Japan, North America, Europe, China, and other regions were recently infected with the ransomware despite efforts to protect their networks following last month’s WannaCry outbreak. One location, a Sayama automobile plant located near Tokyo, was idled due to the infection. Authorities in Victoria, Australia also announced that 55 traffic and speed cameras were accidentally infected with WannaCry due to a maintenance worker using an infected USB stick. Local media reported that the police have decided to cancel 590 fines sent to road users caught by the WannaCry-infected cameras.
Other ransomware news includes Waverly Health Center in Iowa being infected with an unknown ransomware variant and having to shut down their IT systems for a period of time, and Proofpoint researchers saying that the ransomware infections recently reported at several UK universities were part of a larger malvertising campaign carried out by the AdGholas group that leveraged the Astrum Exploit Kit to spread Mole ransomware.
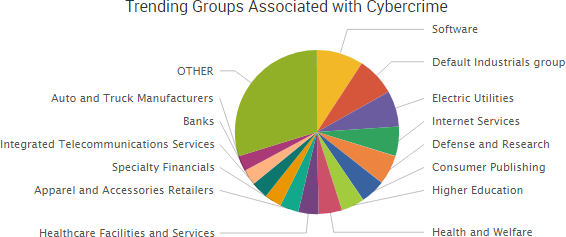
Other trending cybercrime events from the week include:
- Massive voter database leaked: A database containing detailed information on 198 million U.S. voters and compiled by GOP political consultant Deep Root Analytics was left exposed to the Internet for 12 days. The information included data pulled from voter lists maintained by the RNC that was augmented by other sources such as social media sites. The leak includes data on some voters such as ethnicity, religion, contact information, and views on a variety of political issues. In addition, the data included proprietary information such as unique RNC identifiers for each voter.
- POS breach discovered at The Buckle: The clothing store chain The Buckle announced that point-of-sale (POS) malware was discovered on some of its retail POS systems and that some payment cards used between October 28, 2016 and April 14, 2017 may have been affected. The Buckle believes that the malware did not collect data from all transactions or all POS systems for each day within that time period. The company also said that all stores had EMV technology enabled during the time that the incident occurred, which helped to limit the impact of the breach.
- Services disrupted: The CyberTeam hacking group announced on Twitter that it was responsible for the outage that affected Skype on Monday and Tuesday. Microsoft has not confirmed the cause of the outage, but the service was reported down in multiple countries across Europe, as well as Japan, Singapore, India, Pakistan, and South Africa. Square Enix said that Final Fantasy XIV game servers were being repeatedly targeted by DDoS attacks from an anonymous third party.
- More incidents tied to errors and glitches: The email addresses of registered consultancies of the UK government’s Cyber Essentials scheme were exposed due to a configuration error in the Pervade Software platform, according to the IASME Consortium, which runs the accreditation. The sensitive personal information of students was compromised when a staff member at the UK’s University of East Anglia “mistakenly” emailed a spreadsheet with confidential data to 320 American Studies students. A man used a glitch to steal more than £99,000 from the Clydesdale Yorkshire Bank last December when, for approximately one hour, the man’s account showed a credit balance even though he did not have any money.
- Other notable incidents: Online banking service Ffrees notified its users that some of their personal information was “temporarily exposed” due to an “information security incident.” Virgin Media is advising more than 800,000 customers using the Super Hub 2 router to change both their network and router passwords if they are using the default passwords shown on the device’s attached sticker. Torrance Memorial Medical Center said a phishing attack compromised email accounts containing “work-related reports” and the personal data of patients. The latest batch of CIA documents released by WikiLeaks, dubbed “Brutal Kangaroo,” revolves around “a tool suite for Microsoft Windows that targets closed networks by air gap jumping using thumbdrives.” A joint law enforcement action known as the eCommerce Action 2017 led to the arrest of 76 professional fraudsters and members of Internet-based criminal networks across 26 countries.
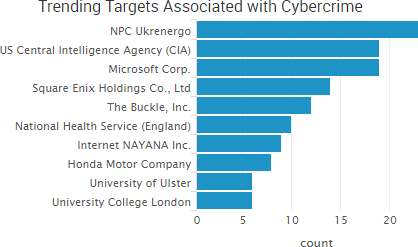
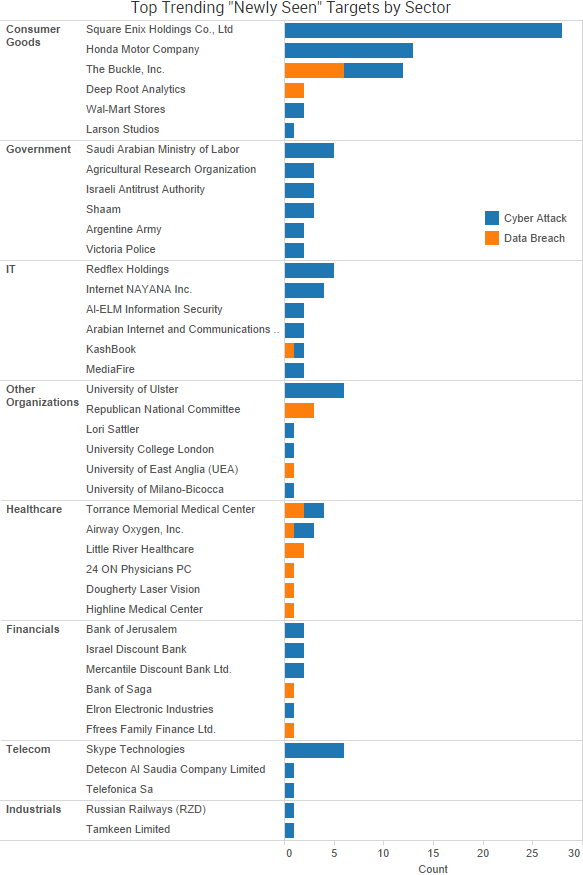
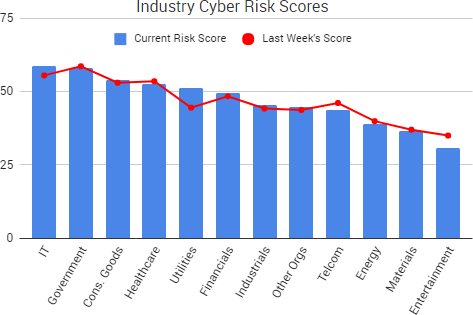
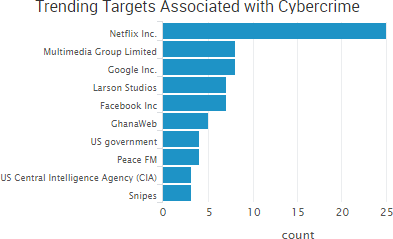
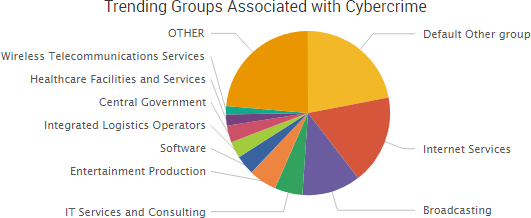
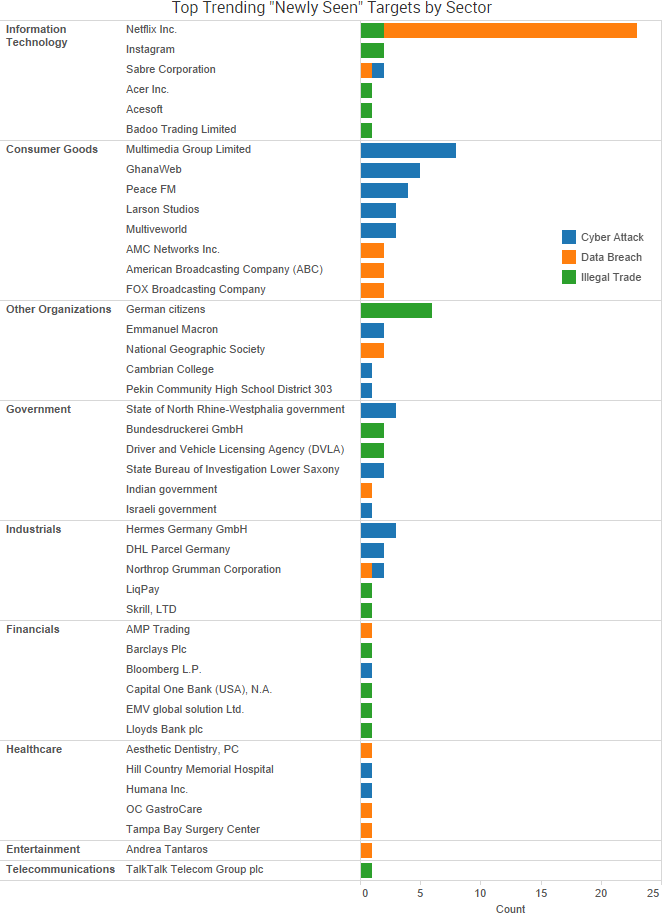
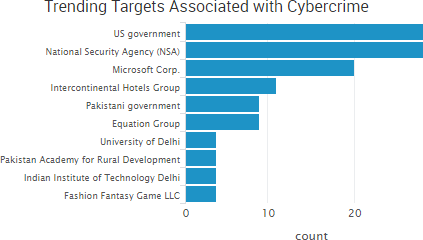
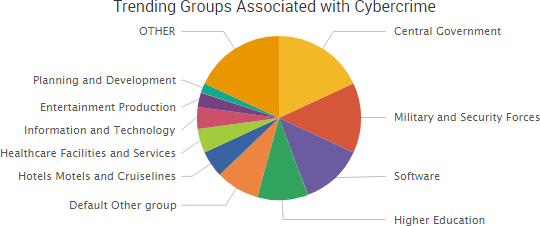
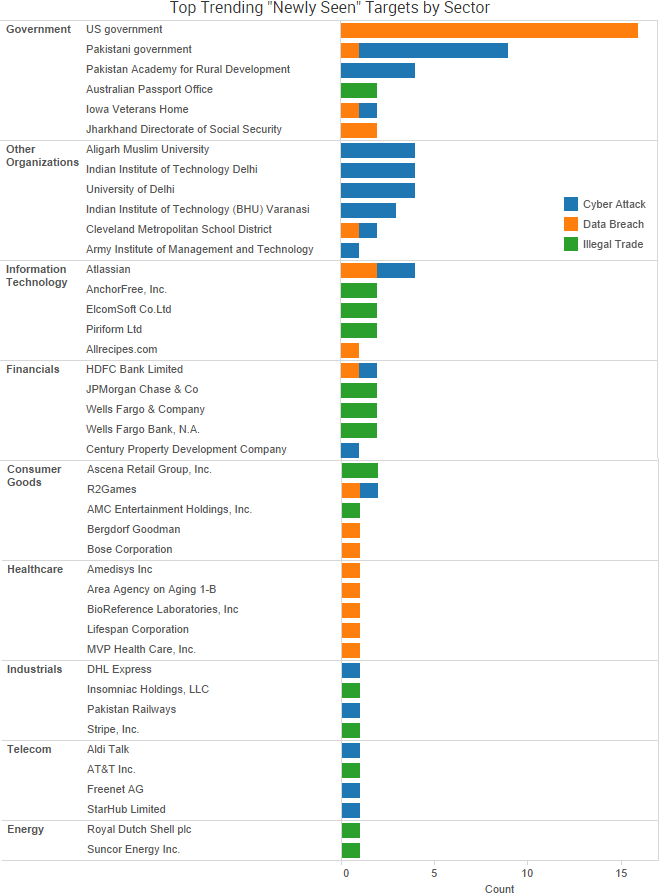
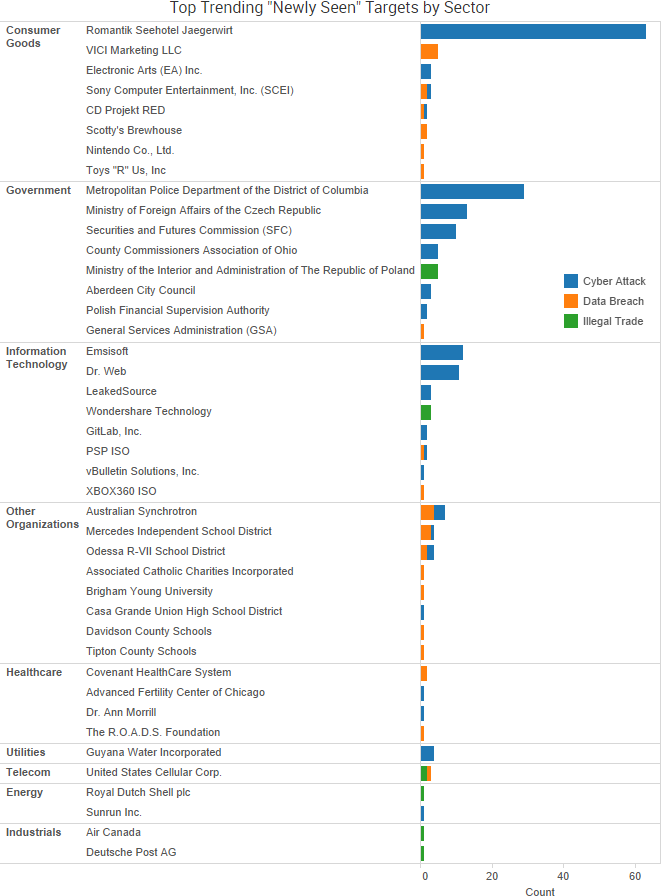
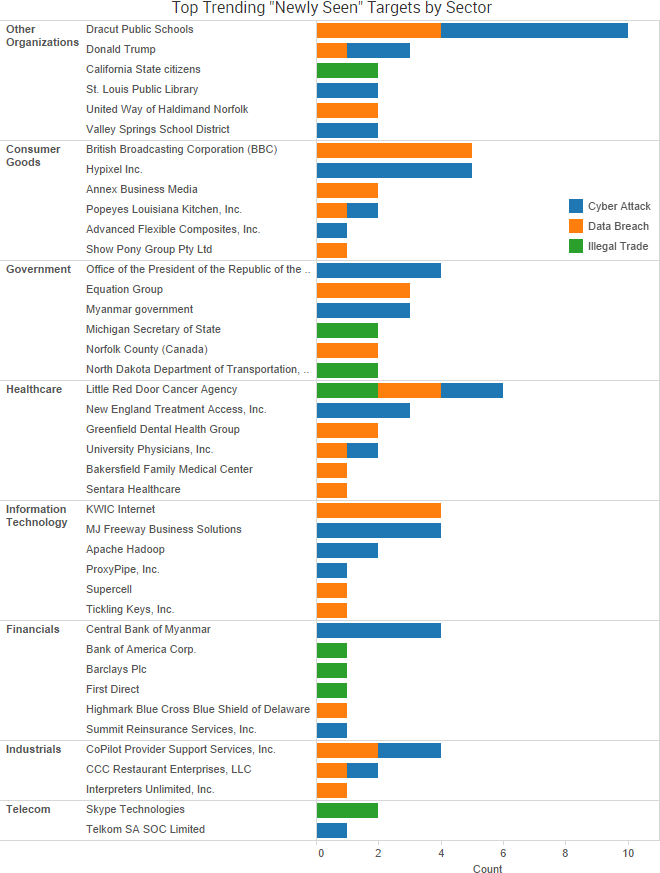
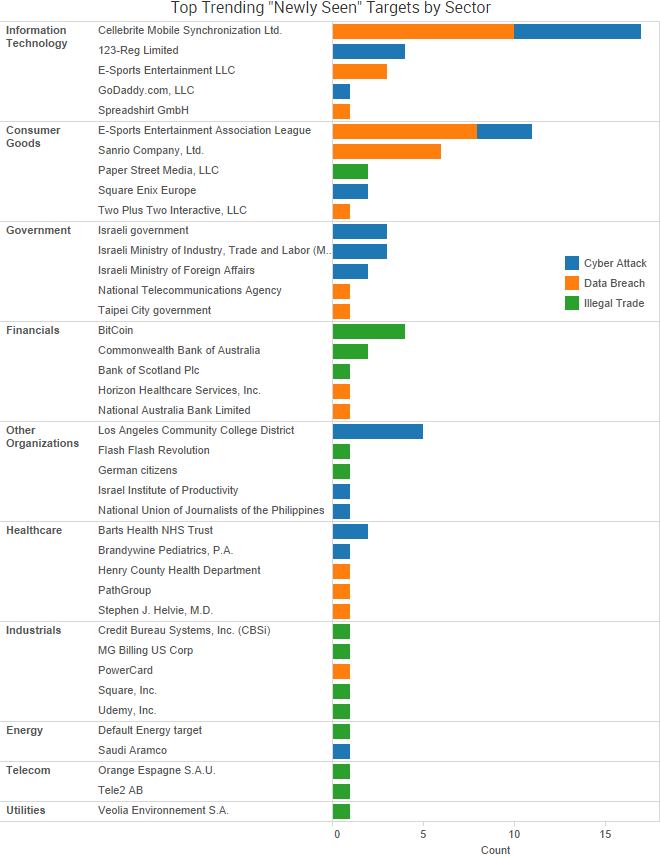
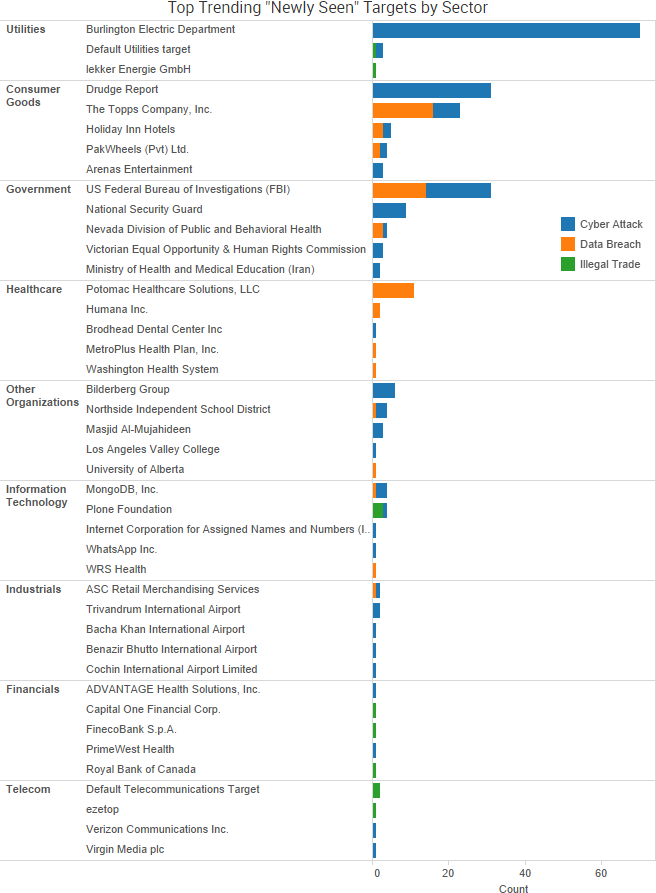
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
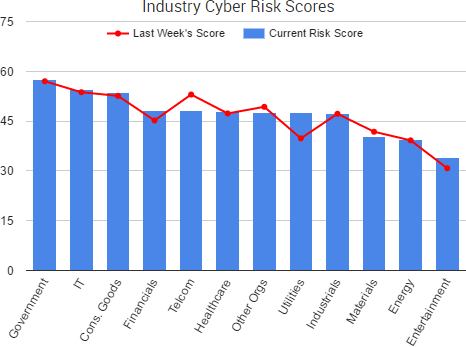
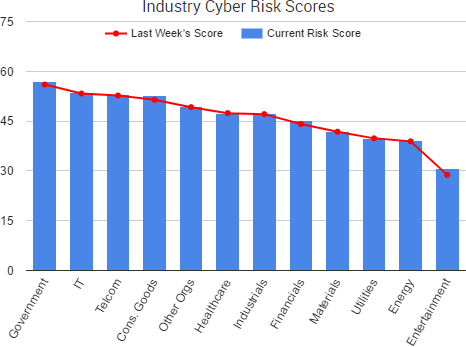
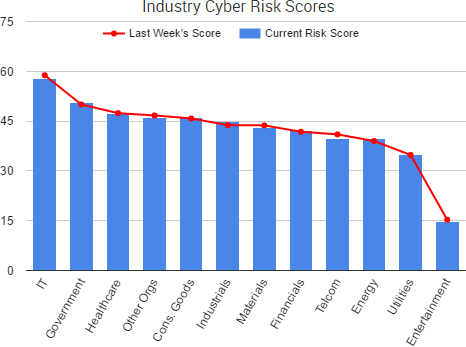
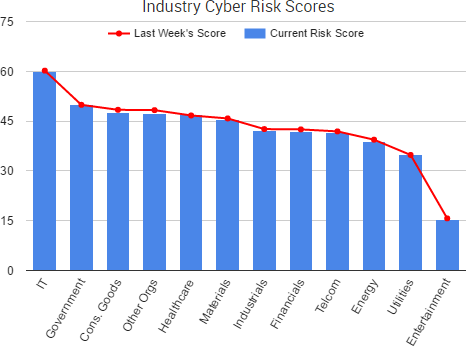
Cyber Risk Trends From the Past Week
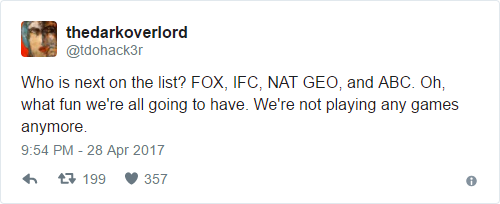
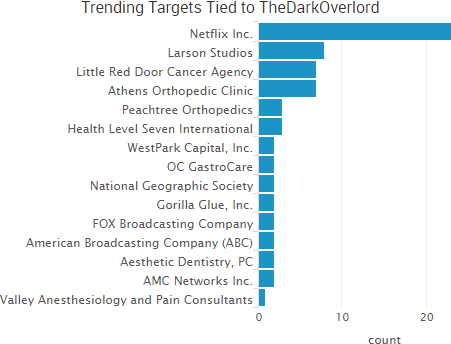
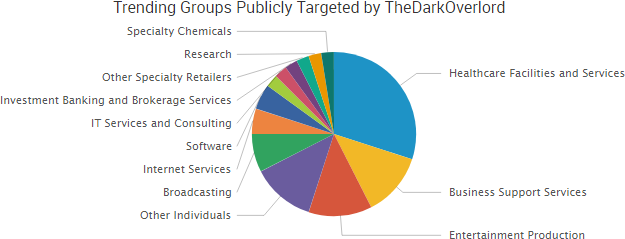
 Larson Studios, the family-owned audio post-production business that was hacked by TheDarkOverlord, has finally provided public comments about the December 2016 attack that led to the theft of a variety of unaired episodes from major studios. That incident led to leak of ten episodes of Netflix’s Orange is the New Black and eight episodes of ABC’s Steve Harvey’s Funderdome.
Larson Studios, the family-owned audio post-production business that was hacked by TheDarkOverlord, has finally provided public comments about the December 2016 attack that led to the theft of a variety of unaired episodes from major studios. That incident led to leak of ten episodes of Netflix’s Orange is the New Black and eight episodes of ABC’s Steve Harvey’s Funderdome.
The takeaway from company president Rick Larson following the ordeal: “Don’t trust hackers.”
He learned that lesson after Larson Studios eventually paid TheDarkOverlord a $50,000 ransom as part of an agreement between the two to keep the breach private. However, a few months later the FBI told Larson Studios that TheDarkOverlord was attempting to extort the company’s clients with the stolen video, and the group then tried to publicly pressure Netflix and others into paying a ransom demand.
Why TheDarkOverlord would attempt to double-dip on the group’s ransom demand is somewhat puzzling. As SurfWatch Labs has noted in multiple blogs, the group has spent the past year carefully projecting an image of professionalism, framing its extortion demands as straightforward “business proposals” and using the media to try to spread the group’s message: pay up and everything will quietly go away. For example, in June 2016 when the group first began making headlines, TheDarkOverlord used the media to warn companies, “Next time an adversary comes to you and offers you an opportunity to cover this up and make it go away for a small fee to prevent the leak, take the offer.” They also warned that the ransom payment would be “a modest amount compared to the damage that will be caused” from a public leak. The group’s tone did not change when it came to extorting Netflix nearly a year later: “You’re going to lose a lot more money in all of this than what our modest offer was.”
It appears that after a full year of trying to build that image as a “trustworthy” extortionist, TheDarkOverlord has now lost its credibility — and, it should be noted, that credibility is what pushed companies like Larson Studios over the edge when deciding if the company should pay. As Rick Larson told Variety, previous media reports suggested that paying TheDarkOverlord actually worked.
TheDarkOverlord appears to be in damage control now, and the group is trying to regain that credibility by arguing that Larson Studios violated its agreement by contacting the FBI. The group also continues to leak data on other organizations, but hopefully those organizations will take heed of the message from Rick Larson to never put their trust in hackers — and it’s clear that now includes TheDarkOverlord.



 Several recent cybercrime events have proven that although two-factor authentication is an effective way to prevent fraudulent transactions, malicious actors are focusing their efforts on ways to defeat that increasingly popular layer of security.
Several recent cybercrime events have proven that although two-factor authentication is an effective way to prevent fraudulent transactions, malicious actors are focusing their efforts on ways to defeat that increasingly popular layer of security.
 Facebook and Google confirmed this week that they were the victims of the $100 million phishing scheme announced by the Department of Justice of
Facebook and Google confirmed this week that they were the victims of the $100 million phishing scheme announced by the Department of Justice of 




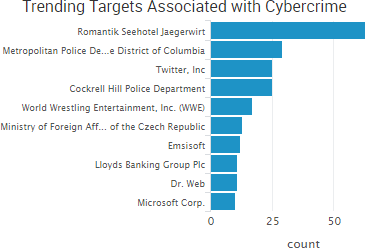 The Austrian hotel Romantik Seehotel Jägerwirt paid approximately $1600 in ransom after ransomware locked the hotel out of its computer systems and the hotel was unable to issue new key cards to arriving guests. The hotel’s reservation system was down for 24 hours; however, the initial media reports that customers were locked in their rooms due to the incident were false, the owner told
The Austrian hotel Romantik Seehotel Jägerwirt paid approximately $1600 in ransom after ransomware locked the hotel out of its computer systems and the hotel was unable to issue new key cards to arriving guests. The hotel’s reservation system was down for 24 hours; however, the initial media reports that customers were locked in their rooms due to the incident were false, the owner told 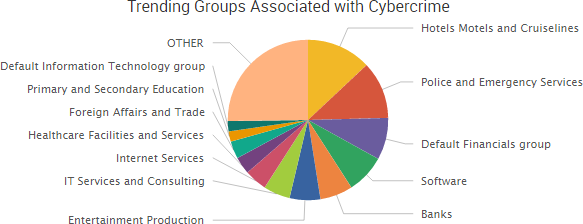
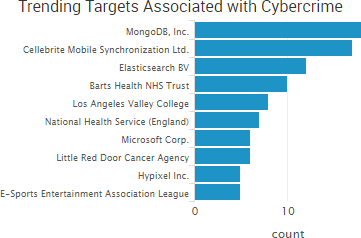
 The past week once again saw numerous organizations exposing data due to insecure public databases, and several of those databases reportedly contained data that was no longer in use.
The past week once again saw numerous organizations exposing data due to insecure public databases, and several of those databases reportedly contained data that was no longer in use. 
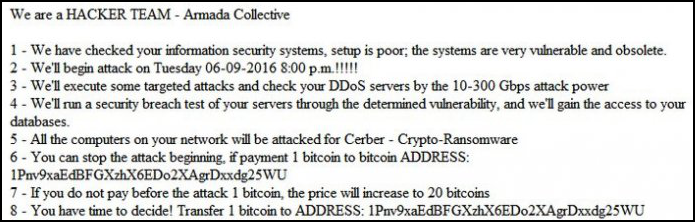
 The most impactful, publicly known ransomware attack of late involves the
The most impactful, publicly known ransomware attack of late involves the 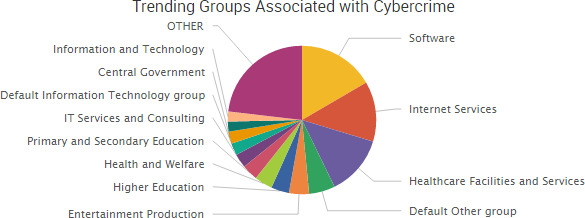
 Security researchers frequently discover private data being exposed to the Internet due to technical errors such as poorly secured data backups, and this past week several new incidents along those lines.
Security researchers frequently discover private data being exposed to the Internet due to technical errors such as poorly secured data backups, and this past week several new incidents along those lines.
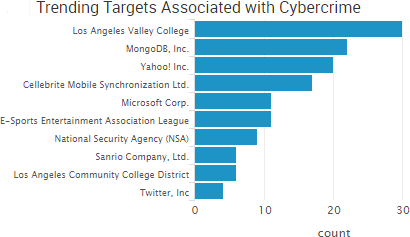 It was less than a year ago that
It was less than a year ago that 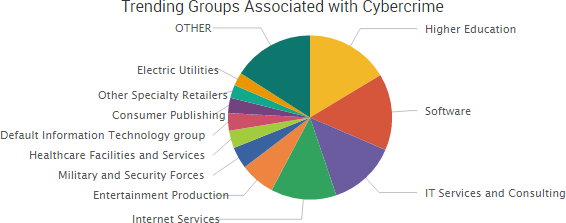
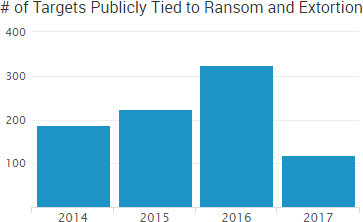
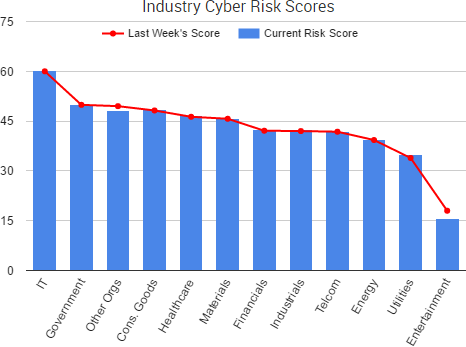 As SurfWatch Labs noted in its annual report, organizations are increasingly
As SurfWatch Labs noted in its annual report, organizations are increasingly 
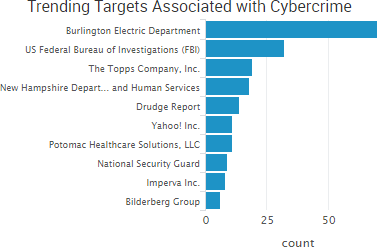 “We uploaded the indicators to our scanning system to look for the types of things specified,” Burlington Electric Department general manager Neil Lunderville
“We uploaded the indicators to our scanning system to look for the types of things specified,” Burlington Electric Department general manager Neil Lunderville 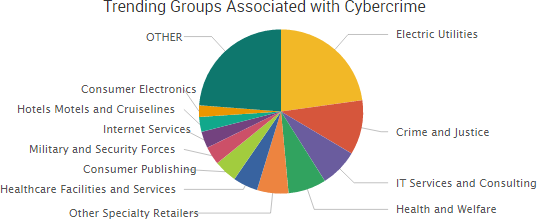
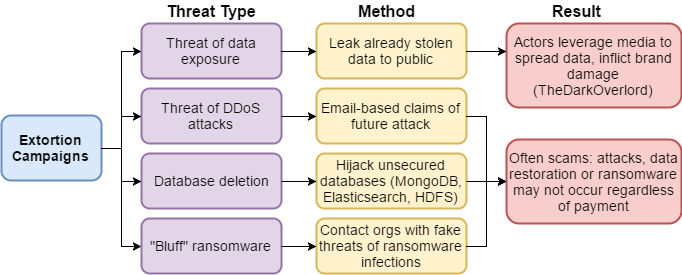
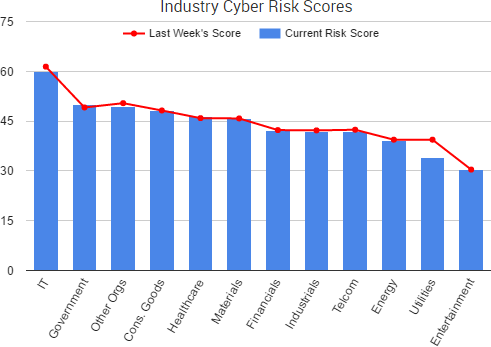 Organizations once again are being blackmailed by threat actors who are either threatening to release stolen data or else holding data hostage unless a ransom payment is made.
Organizations once again are being blackmailed by threat actors who are either threatening to release stolen data or else holding data hostage unless a ransom payment is made.