The holiday shopping season is right around the corner, and gift cards are expected to remain as the most requested holiday gift for the tenth year in a row. It should come as no surprise then that gift card fraud has become a booming business for cybercriminals as they attempt to grab a slice of that $140 billion pie.
In fact, gift cards are one of the most frequently listed items on dark web marketplaces, and SurfWatch Labs expects the number of compromised gift cards for sale to rise in the coming months. As we noted last week in “How Cybercriminals Perpetuate Gift Card Fraud,” fraudsters employ a variety of simple tricks to find active gift card numbers and codes to steal — and millions of gift cards will soon be loaded with active balances across the country.
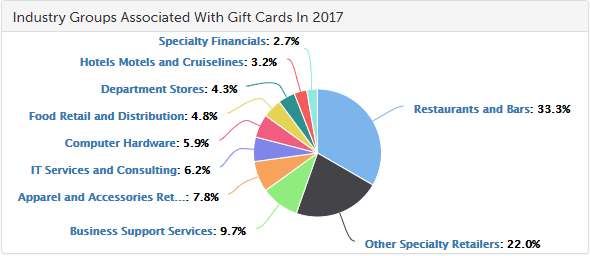
SurfWatch Labs’ threat intelligence data has already shown a significant increase in fraud in the third quarter, and those fraud concerns will remain elevated throughout the holiday season.
Stolen Gift Cards on Marketplaces
Compromised gift cards are often sold on cybercriminal markets; however, legitimate gift card marketplaces have grown rapidly over the past few years and criminals have begun leveraging them to sell stolen gift cards or to aid in laundering money.
Marketplaces like Raise often provide customers links to help check gift card balances before listing. However, researchers have shown that balance-checking websites can be exploited by cybercriminals to determine active cards if the websites do not implement proper security measures.
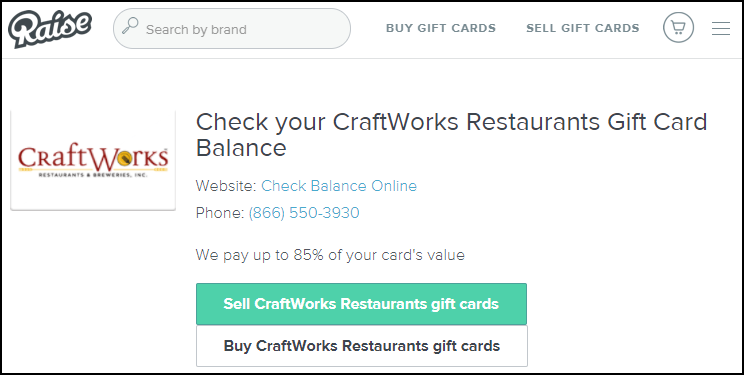
As Raise has grown in popularity, customers have reported multiple instances of gift cards having their balances completely or partially gone by the time buyers used them, as well as instances of tens of thousands of gift cards being used to launder stolen credit card money through the site. Those issues may have helped push the company to expand its money-back guarantee on gift cards last year from 100 days to 365 days in order to help assuage some of the concerns users had about buying potentially compromised cards.
Stolen Gift Cards on the Dark Web
The dark web is in a more fluid state heading into this holiday season than it was in 2016, and that’s largely due to the law enforcement takedown of two of the top three most popular markets, AlphaBay and Hansa Market, this past summer. However, finding gift cards for sale on various smaller marketplaces is still relatively easy.
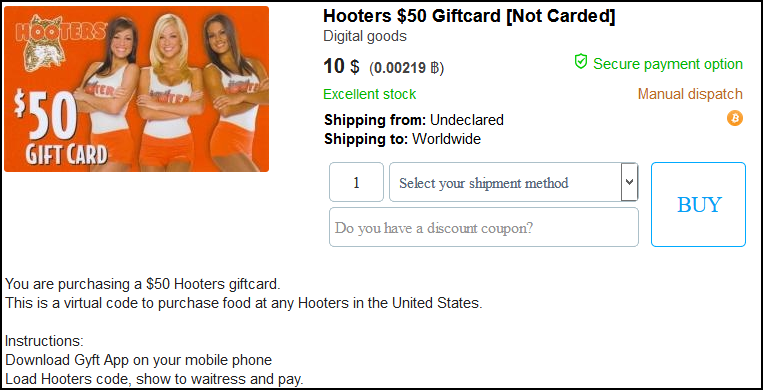
Over the past few months, SurfWatch Labs has observed a variety of gift cards for sale for popular organizations on cybercriminal markets. SurfWatch Labs has not purchased the cards or verified the legitimacy of the postings, but they include:
- gift cards for popular chains such as Whole Foods ($100 for $35), Hooters ($50 for $10), and Starbucks ($10-$20 for $3);
- various gift cards that may be partially used, such as a $17 Applebee’s gift card for $6.80, and a $32 Five Guys gift card for $12.80;
- and sellers claiming to have gift cards for dozens of other restaurants, specialty retailers, hospitality organizations, entertainment venues, and more at similarly discounted prices.
It’s unclear how the numerous gift cards for sale were stolen — or what percentage are actually legitimate — but a quick search of a dozen random companies listed found that nearly all had websites where users could check their balances. And of those, only a few required CAPTCHAs, which researchers have suggested be implemented to help slow down automated attacks.
Other common gift card fraud prevention tactics include making sure that unactivated gift cards are not easily accessible and that their numbers are hidden behind scratch-off coverings, that organizations don’t use sequential numbering or other easily recognizable patterns with their gift cards, and that consumers who have gift cards use them in a reasonable time so the window for potential attacks is shortened. In addition, some stores have implemented limits on the amount of gift cards that can be purchased at once, have begun requiring photo ID for high-dollar purchases, and are attempting to warn buyers of potential scams related to gift cards.
However, until those increased protections become more widespread, we will likely once again see a rise in gift cards being leveraged for fraud and other illicit purposes this holiday season.