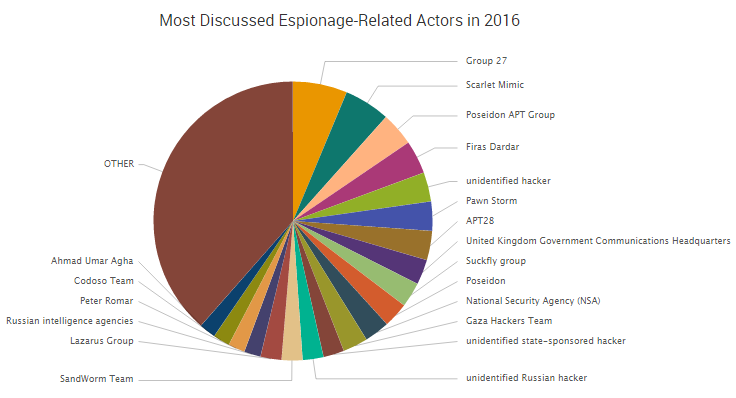
Despite recent media attention surrounding nation-state hackers infiltrating government organizations and attempting to influence elections, the bulk of government-related cybercrime tends to be driven by less sophisticated and more ideologically-motivated campaigns carried out by hacktivist actors, according to a new report from SurfWatch Labs.

Government is the third most active sector when it comes to cybercrime, behind only information technology and consumer goods, and more than a third of the government CyberFacts collected by SurfWatch Labs this year have been related to hacktivist activity — far more than any other sector.
“The global reach of the Internet and social media along with the relative anonymity of cyber-attacks has provided hacktivists with a larger platform than ever to share their message, recruit new actors, and ultimately impact organizations,” noted the report, Cybercrime Gets Political: Automated Tools and Growing Reach Empowers Hacktivists.
It continued: “As a result, the most common cybercrime story in the government sector has involved websites and data being targeted by hacktivist groups resulting in service downtime, website defacement, and various types of information being stolen and publicly leaked.”

Hacktivist-driven data breaches are not a new problem for the government sector. In 2013, the FBI warned that anonymous hacktivists using Adobe exploits were able to infiltrate agencies such as the U.S. Army, the Department of Energy, and the Department of Health and Human Services in order to steal sensitive information.
“It is a widespread problem that should be addressed,” the 2013 alert stated.
Three years later, hacktivists remain as a top source of government-sector data breaches.
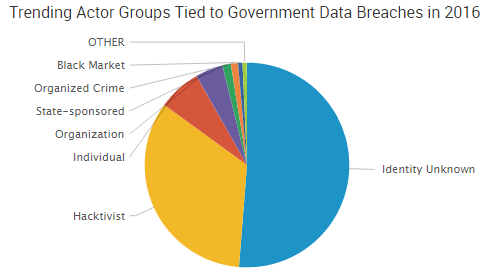
Government agencies across the world have been targeted by hacktivists using well-known attack vectors such as SQL injections, social engineering and stolen credentials.
For example:
- Shortly after Anonymous Philippines defaced the COMLEC website in protest of “questions and controversies” surrounding the country’s electoral process, LulzSec Pilipinas posted the entire COMLEC database online. The incident has been described as the largest government-related data breach in history – affecting more than 55 million people.
- A hacker supporting Palestine published the names and personal information of FBI and Department of Homeland Security employees. The hacker said he first compromised the email account of a Department of Justice employee. Then he socially engineered access to the portal by pretending to be a new employee. Finally, he was able to find databases of employee information on the DOJ intranet.
- The Anonymous #OpAfrica campaign led to several breaches including a one terabyte dump of information from Kenya’s Ministry of Foreign Affairs and International Trade. Kenya’s Ministry of Information and Communications Technology cabinet secretary Joseph Mucheru said the information was stolen due to a phishing attack that duped employees into clicking a link to change their credentials, which provided the hacktivist access to email accounts.
- A hacker known as Hanom1960 breached several government agencies – including the Costa Rica Ministry of Culture and Foreign Affairs, the Columbia Ministry of Information Technologies and Communications, and Columbia’s Ministry of National Education – and subsequently leaked information on various government employees. “I see many mistakes in [their IT] systems,” the hacker told news outlets. “It is something that does not concern governments.”
 Hacktivists are often characterized as graffiti artists or vandals that simply deface websites and cause other nuisance-level problems for organizations.
Hacktivists are often characterized as graffiti artists or vandals that simply deface websites and cause other nuisance-level problems for organizations.
Those types of attacks are common, with SurfWatch Labs’ data showing that website downtime and website defaced are the most popular effects of hacktivism; however, the threats from hacktivists go beyond those simple attacks.
According to the report:
“Government officials noted in 2015 that the bulk of the cybercrime-as-a-service economy may be powered by as few as 200 individuals, yet those services put traditional cybercrime tools such as malware, botnets and DDoS attacks at the fingertips of a vastly larger pool of actors. … This trend, along with the large number of federal, state and local government agencies across the world, the global reach of hacktivist actors, and a never-ending series of political causes means that hacktivists have the ability, reach and will to cause harm to government organizations on a level never before seen.”
Hacktivists don’t have the resources of state-sponsored actors, but they are much more open about their attacks — often using public channels to coordinate attacks, gain media attention and recruit other actors to the campaign.
“This chatter can lead to valuable threat intelligence around what types of organizations are being targeted, how those attacks are impacting organizations and, ultimately, what can be done to better protect your organization,” the report concludes. “Monitoring hacktivist chatter and utilizing external cyber threat intelligence, along with your own internal data, can help to paint a full picture of the cyber risks facing your organization, determine what assets are at greatest risk, and inform where cyber defense efforts should be focused in the future.”
For more information, download the full report, Cybercrime Gets Political: Automated Tools and Growing Reach Empowers Hacktivists.