The Swedish Transportation Administration and other related agencies were among the week’s top trending cybercrime targets due to a series of distributed denial-of-service (DDoS) attacks that led to services being disrupted earlier this month.

The DDoS attacks against the Swedish Transportation Administration affected all of its web-based systems, including the IT system that manages train orders, the administration’s email system, Skype, and its website. Officials said the disruption, which led to the driving of trains manually, resulted in the stoppage and delays of some trains.
A spokesperson for the administration said (Swedish) that the DDoS attacks targeted its internet service providers, TDC and DGC; however, the attacks appeared designed to disrupt the administration’s services.
The following day saw additional DDoS attacks against the website of Sweden’s Transport Agency, as well as public transport operators Västtrafik in western Sweden, which briefly crashed the operator’s ticket booking app and online travel planner.
The incident follows warnings from various DDoS mitigation providers about DDoS attacks. CDNetworks – which surveyed organizations in the UK, Germany, Austria, and Switzerland – found that more than half of the organizations were hit by DDoS attacks in the past year. A10 Networks warned that the number of organizations experiencing an average DDoS attack over 50 Gbps has quadrupled in the past two years. In addition, Incapsula researchers recently warned of a new “pulse wave” DDoS attack that provides an “easy way” for attackers to double their attack output. A Neustar report also found that DDoS attacks are frequently accompanied by other malicious activity, such as viruses, malware, ransomware, and lost customer data.

Other trending cybercrime events from the week include:
- Large data leaks: The Republican phone polling firm Victory Phones had 223 GB worth of data stolen in what appears to be an attack against an unsecured MongoDB database that occurred in January 2017. The incident exposed data on hundreds of thousands of Americans who submitted donations to political campaigns. A researcher has discovered the personal information of millions of South Africans among a large dump of other data breaches. The data includes 30 million unique South African ID numbers, about 2.2 valid email addresses, and other personal information. We Heart It announced a data breach affecting 8 million accounts created between 2008 and November 2013.
- Payment card breaches: Pizza Hut is warning that customers who used the company’s website or mobile app to place an order during a 28-hour period in early October may have had their information compromised. The online e-commerce platform Spark Pay is notifying customers of a payment card breach involving merchant websites after discovering malicious code on a server. Citizens Financial Group is notifying customers of an ATM skimming incident that occurred at a Citizens Bank ATM located in Cambridge, Massachusetts.
- Other data breaches: Microsoft’s internal database for tracking bugs was hacked in 2013 revealing descriptions of critical and unfixed vulnerabilities for widely used software such a Windows. Transamerica Retirement Solutions is notifying some customers that it discovered unauthorized access to their retirement plan online account information due to the use of compromised third-party user credentials. Officials said the cryptocurrency exchange Bithumb was targeted with phishing emails containing malware and that led to the personal and financial information of at least 30,000 users being exposed. Chase Brexton Health Care is notifying 16,000 patients of a breach due to a phishing attack that led to the compromise of four employee email accounts and the attackers rerouting the victims’ paychecks to a bank account under their control. Namaste Health Care in Missouri is notifying approximately 1,600 patients of a ransomware infection that may have led to the attacker accessing their information. Rivermend Health is notifying 1,300 patients that their personal information may have been compromised due to a breach of an employee’s email account.
- Other notable events: The British TV production firm Mammoth Company was hacked by North Korean hackers after reports the company was creating a TV show about a British nuclear scientist taken prisoner in North Korea. The attack did not cause any harm, but it did cause widespread alarm, the BBC reported. Domino’s Australia said that it is investigating a potential issue with a former supplier’s system after a number of customers received unauthorized spam emails. A University of Kansas student was expelled after using a keylogger device to steal faculty credentials and change his grades.
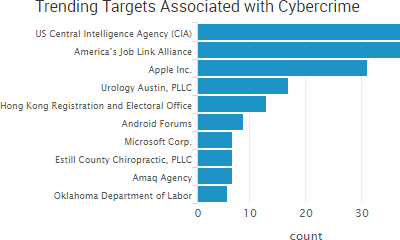
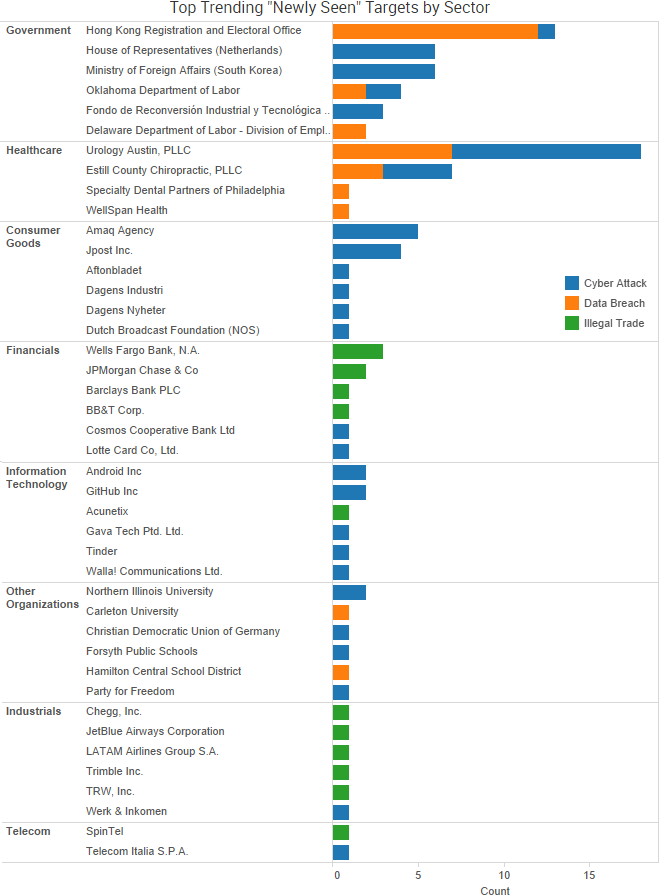
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
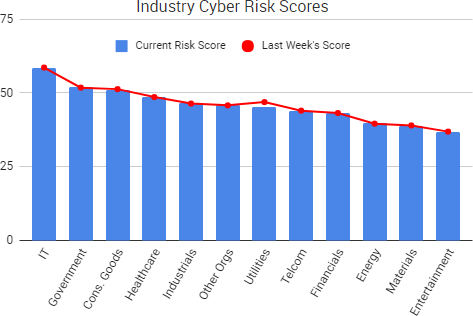
 Cyber Risk Trends From the Past Week
Cyber Risk Trends From the Past Week
 Researchers have discovered a vulnerability, dubbed “ROCA” (CVE-2017-15361), in the cryptographic smartcards, security tokens, and other secure hardware chips manufactured by Infineon Technologies AG, and that vulnerability could allow an attacker to calculate the private portion of an RSA key.
Researchers have discovered a vulnerability, dubbed “ROCA” (CVE-2017-15361), in the cryptographic smartcards, security tokens, and other secure hardware chips manufactured by Infineon Technologies AG, and that vulnerability could allow an attacker to calculate the private portion of an RSA key.
The vulnerability is due to the way the Infineon Trusted Platform Module firmware “mishandles RSA key generation, which makes it easier for attackers to defeat various cryptographic protection mechanisms via targeted attacks,” the CVE states.
Chips manufactured as early as 2012 are affected by the vulnerability, the researchers said.
“The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable,” the researchers said. “We found and analyzed vulnerable keys in various domains including electronic citizen documents, authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP.”
Researchers said that malicious actors could feasibly use what’s known as a “practical factorization attack” against key lengths of up to 2048 bits, and if the attack is improved it could be used against 4096-bit RSA keys in the future. According to the researchers, the time and complexity cost associated with selected key lengths are:
- 512 bit RSA keys – 2 CPU hours (the cost of $0.06);
- 1024 bit RSA keys – 97 CPU days (the cost of $40-$80);
- 2048 bit RSA keys – 140.8 CPU years (the cost of $20,000 – $40,000).
If a vulnerable key is found, organizations should contact their device vendor for further advice, the researchers said. Forbes reported that Fujitsu, Google, HP, Lenovo, and Microsoft have all pushed out fixes for their relevant hardware and software. The researchers will present their full findings at the ACM Conference on Computer and Communications Security later this month.





 Researchers have published the details of a yet-to-be patched SQL injection vulnerability affecting BPC Banking Technologies’ SmartVista product suite after numerous reports of the bug went unanswered.
Researchers have published the details of a yet-to-be patched SQL injection vulnerability affecting BPC Banking Technologies’ SmartVista product suite after numerous reports of the bug went unanswered.



 Security researchers are advising people to ensure their Bluetooth connections are turned off when not in use after the discovery of a series of vulnerabilities that can be used to compromise billions of Bluetooth-enabled devices.
Security researchers are advising people to ensure their Bluetooth connections are turned off when not in use after the discovery of a series of vulnerabilities that can be used to compromise billions of Bluetooth-enabled devices.
 “The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi,”
“The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi,” 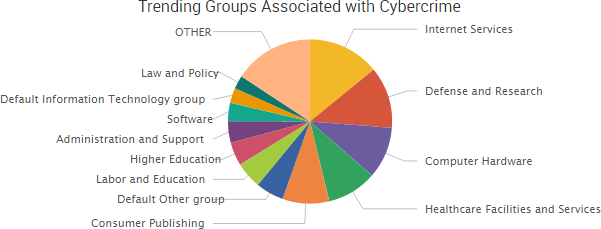
 The password manager LastPass has addressed a series of vulnerabilities that were discovered by Google Project Zero researcher Tavis Ormandy, including one now-patched “unique and highly sophisticated” client-side vulnerability in the LastPass browser extension.
The password manager LastPass has addressed a series of vulnerabilities that were discovered by Google Project Zero researcher Tavis Ormandy, including one now-patched “unique and highly sophisticated” client-side vulnerability in the LastPass browser extension. 



 Earlier this month, a patch was issued to address a high-impact vulnerability in Apache Struts Jakarta Multipart parser that allowed attackers to remotely execute malicious code. Shortly after the patch, an exploit appeared on a Chinese-language website,. Researchers then confirmed that attackers were “widely exploiting” the vulnerability. Since then, the issue has continued to affect numerous organizations through data breaches and service downtime.
Earlier this month, a patch was issued to address a high-impact vulnerability in Apache Struts Jakarta Multipart parser that allowed attackers to remotely execute malicious code. Shortly after the patch, an exploit appeared on a Chinese-language website,. Researchers then confirmed that attackers were “widely exploiting” the vulnerability. Since then, the issue has continued to affect numerous organizations through data breaches and service downtime.



 Several companies have issued breach notification letters related to a malware incident at Aptos, Inc., which provides e-commerce solutions for a number of online stores. The breach at Aptos was discovered in November 2016, and notification by the various companies affected was delayed until recently at the request of law enforcement.
Several companies have issued breach notification letters related to a malware incident at Aptos, Inc., which provides e-commerce solutions for a number of online stores. The breach at Aptos was discovered in November 2016, and notification by the various companies affected was delayed until recently at the request of law enforcement. 
 “The bug was serious because the leaked memory could contain private information and because it had been cached by search engines,” wrote John Graham-Cumming, the CTO of Cloudflare, which provides performance and security services to numerous major websites. “We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence.”
“The bug was serious because the leaked memory could contain private information and because it had been cached by search engines,” wrote John Graham-Cumming, the CTO of Cloudflare, which provides performance and security services to numerous major websites. “We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence.”

 The Cloudflare bug can be traced back to a single character of code, which resulted in a buffer overrun, the company said.
The Cloudflare bug can be traced back to a single character of code, which resulted in a buffer overrun, the company said.