The FBI is once again warning organizations that there has been an increase in phishing campaigns targeting employee W-2 information. In addition, this week saw new breach notifications related to W-2 theft, as well as reports of a threat actor targeting Fortune 500 companies with business email compromise (BEC) scams in order to steal millions of dollars.
The recent breach notification from Los Angeles Philharmonic highlights how W-2 information is often targeted during the tax season: attackers impersonated the organization’s chief financial officer via what appeared to be a legitimate email address and requested that the W-2 information for every employee be forwarded.
“The most popular method remains impersonating an executive, either through a compromised or spoofed email in order to obtain W-2 information from a Human Resource (HR) professional within the same organization,” the FBI noted in its alert on W-2 phishing scams.
In addition, researchers said that a threat actor, which is likely of Nigerian origin, has been successfully targeting accounts payable personnel at some Fortune 500 companies to initiate fraudulent wire transfers and steal millions of dollars. The examples observed by the researchers highlight “how attackers used stolen email credentials and sophisticated social engineering tactics without compromising the corporate network to defraud a company.”
The recent discoveries highlight the importance of protecting against BEC and other types of phishing scams. The FBI advises that the key to reducing the risk is understanding the criminals’ techniques and deploying effective mitigation processes, such as:
- limiting the number of employees who have authority to approve wire transfers or share employee and customer data;
- requiring another layer of approval such as a phone call, PIN, one-time code, or dual approval to verify identities before sensitive requests such as changing the payment information of vendors is confirmed;
- and delaying transactions until additional verification processes can be performed.

Other trending cybercrime events from the week include:
- Spyware companies hacked: A hacker has breached two different spyware companies, Mobistealth and Spy Master Pro, and provided gigabytes of stolen data to Motherboard. Motherboard reported that the data contained customer records, apparent business information, and alleged intercepted messages of some people targeted by the malware.
- Data accidentally exposed: The University of Wisconsin – Superior Alumni Association is notifying alumni that their Social Security numbers may have been exposed due to the ID numbers for some individuals being the same as their Social Security numbers and those ID numbers being shared with a travel vendor. More than 70 residents of the city of Ballarat had their personal information posted online when an attachment containing a list of individuals who had made submissions to the review of City of Ballarat’s CBD Car Parking Action Plan was posted online unredacted. Chase said that a “glitch” led to some customers’ personal information being displayed on other customers’ accounts.
- Notable data breaches: The compromise of a senior moderator’s account at the HardwareZone Forum led to a breach affecting 685,000 user profiles, the site’s owner said. White and Bright Family Dental is notifying patients that it discovered unauthorized access to a server that contained patient personal information. The University of Virginia Health System is notifying 1,882 patients that their medical records may have been accessed due to discovering malware on a physician’s device. HomeTown Bank in Texas is notifying customers that it discovered a skimming device installed on an ATM at its Galveston branch.
- Other notable events: The Colorado Department of Transportation said that its Windows computers were infected with SamSam ransomware and that more than 2,000 computers were shut down to stop the ransomware from spreading and investigate the attack. The city of Allentown, Pennsylvania, said it is investigating the discovery of malware on its systems, but there is no reason to believe personal data has been compromised. Harper’s Magazine is warning its subscribers that their credentials may have been compromised.
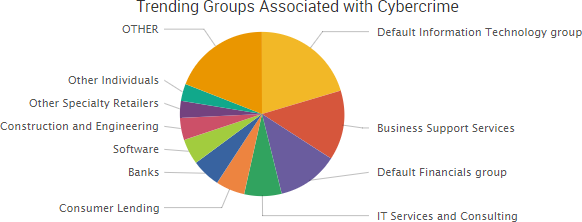
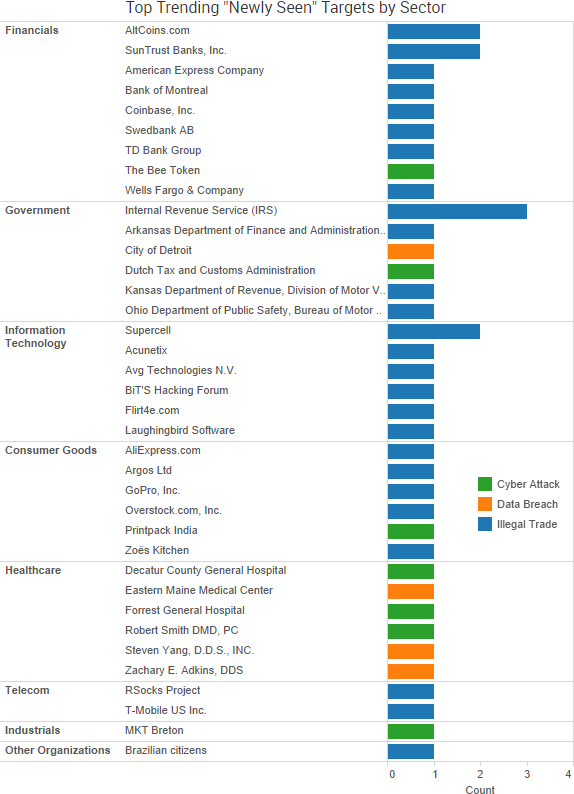
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of the top trending targets are shown in the chart below.

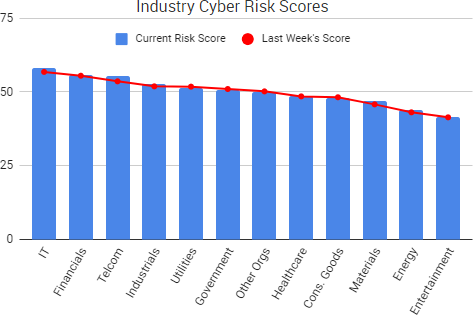
Cyber Risk Trends From the Past Week

The U.S. Securities and Exchange Commission (SEC) issued updated guidance on how public organizations should respond to data breaches and other cybersecurity issues last week.
The document, titled “Commission Statement and Guidance on Public Company Cybersecurity Disclosures,” states that “it is critical that public companies take all required actions to inform investors about material cybersecurity risks and incidents in a timely fashion, including those companies that are subject to material cybersecurity risks but may not yet have been the target of a cyber-attack.”
The SEC also advised that directors, officers, and other corporate insiders should not trade a public company’s securities if they are in possession of material nonpublic information — an issue that arose when it was reported that several Equifax executives sold shares in the days following the company’s massive data breach. The SEC said that public companies should have policies and procedures in place to prevent insiders from taking advantage of insider knowledge of cybersecurity incidents, as well as to ensure a timely disclosure of any related material nonpublic information.
“I believe that providing the Commission’s views on these matters will promote clearer and more robust disclosure by companies about cybersecurity risks and incidents, resulting in more complete information being available to investors,” said SEC Chairman Jay Clayton. “In particular, I urge public companies to examine their controls and procedures, with not only their securities law disclosure obligations in mind, but also reputational considerations around sales of securities by executives.”
The SEC unanimously approved the updated guidance; however, Reuters reported that there was reluctant support from democrats on the commission who were calling for much more rigorous rulemaking to be put in place.




 The U.S. government issued a formal statement this past week blaming the Russian military for the June 2017 outbreak of NotPetya malware. Then on Friday, the day after the NotPetya accusations, the Justice Department indicted 13 Russian individuals and three Russian companies for using information warfare to interfere with the U.S. political system, including the 2016 presidential election. Those stories have once again pushed the alleged cyber activities of the Russian government into the national spotlight.
The U.S. government issued a formal statement this past week blaming the Russian military for the June 2017 outbreak of NotPetya malware. Then on Friday, the day after the NotPetya accusations, the Justice Department indicted 13 Russian individuals and three Russian companies for using information warfare to interfere with the U.S. political system, including the 2016 presidential election. Those stories have once again pushed the alleged cyber activities of the Russian government into the national spotlight.
 For starters, researchers discovered a new cryptocurrency miner, dubbed
For starters, researchers discovered a new cryptocurrency miner, dubbed