HBO was once again the week’s top trending target as the actors behind the company’s breach continued to leak data stolen from the company, including emails that showed HBO attempted to negotiate a $250,000 “bounty payment” in response to the theft.

A source told Reuters that the negotiation email was sent as a stall tactic and that HBO never intended to pay the attackers, who reportedly demanded $6 million in ransom.
“You have the advantage of having surprised us,” HBO’s email read, according to Variety. “In the spirit of professional cooperation, we are asking you to extend your deadline for one week.”
The actors behind the attack claim to have stolen 1.5 terabytes worth of data. In late July, the group leaked several episodes of unaired HBO shows as well as leaked a script for an unaired episode of Game of Thrones. Last Tuesday the group leaked an additional 3.4 GB of data.
As The Guardian reported, that leak included more Game of Thrones scripts, internal HBO documents, and a month’s worth of emails from HBO’s vice president for film programming. Among the documents were technical data detailing HBO’s internal network and administrator passwords, a spreadsheet of legal claims against the TV network, job offer letters to several top executives, slides discussing future technology plans, and a document that appears to list the contact information of Game of Thrones actors.
The group also claimed that HBO was its seventeenth target and that HBO was only the third company to have not paid the ransom demanded by the group. An HBO spokesperson previously said that the company’s ongoing investigation “has not given us a reason to believe that our e-mail system as a whole has been compromised.”

Other trending cybercrime events from the week include:
- Actors target Ireland’s grid: Ireland’s EirGrid said that the country’s electric grid was targeted by state-sponsored actors that managed to gain access to a Vodafone network used by the company and then compromised routers used by EirGrid in Wales and Northern Ireland. The breach of the Vodafone network allowed the hackers to create a type of wiretap known as Generic Routing Encapsulation (GRE) to tunnel into EirGrid’s Vodafone router, the Independent reported.
- Millions of Venezuelans lose cell service: Venezuelan government websites were the target of a massive cyber-attack allegedly carried out by a group known as “The Binary Guardians,” and as a result seven million mobile phone users were left without service, government officials said. The attacks affected the Movilnet’s GSM platform, officials said, leaving seven million of the thirteen million mobile phone users without service.
- New data breaches: Parkbytext is notifying its users that their information may have been compromised due to malware during a service outage. The personal information of 100,000 Dutch drivers was leaked due a flaw in the LeaseWise software created by software company CarWise ICT and used by 52 Dutch car leasing companies. UCLA officials said that a Summer Sessions and International Education Office server was potentially breached in a May 18 cyber-attack and that the personal information of 32,000 students may have been compromised.
- Agencies warn of phishing scams: A new phishing scam is impersonating tax software providers in an attempt to steal credentials from tax professionals, the IRS warned. Scammers are impersonating officials from the National Institutes of Health and telling consumers that they’ve been selected to receive a $14,000 grant in an attempt to get victims to pay a fee via gift cards or their bank account numbers, the FTC warned.
- Arrests and sentences: Two Israeli men were arrested and indicted in Israel on charges believed to be related to operating the DDoS-for-hire service known as vDOS. A former employer of Allen & Hoshall has been sentenced to 18 months in prison for repeatedly accessing the company’s servers over a two-year period in order to obtain proprietary information. An Australian man has been sentenced to an 18-month suspended sentence for his role in operating an illegal network that allowed the selling of unauthorized access to Foxtel service to more than 8,000 people.
- Other notable incidents: Pernod Ricard SA, producer of Absolut vodka and Chivas Regal Scotch whisky, was the target of a cyber-attack, and some employees at the company’s London office had to turn in their computers to be inspected for infections, sources told Bloomberg. Four different anonymous Bloomberg chat rooms were shut down after a user from the investment firm Janus Henderson sent an unmasked list of all the previous day’s 866 participants in the metal and mining chat room to people in the chat room.
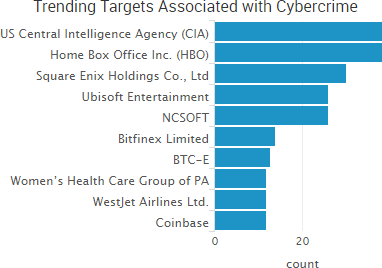
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.

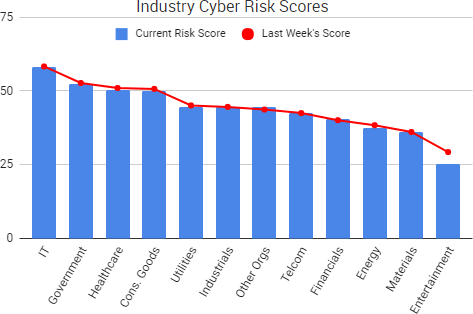
Cyber Risk Trends From the Past Week
 The UK Department for Digital, Culture, Media & Sport (DCMS) released a statement of intent on a new data protection bill last week.
The UK Department for Digital, Culture, Media & Sport (DCMS) released a statement of intent on a new data protection bill last week.
The goal of future data protection acts is to “ensure that we help to prepare the UK for the future after we have left the EU,” wrote DCMS Minister for Digital Matt Hancock.
“The EU General Data Protection Regulation (GDPR) and the Data Protection Law Enforcement Directive (DPLED) have been developed to allow people to be sure they are in control of their personal information while continuing to allow businesses to develop innovative digital services without the chilling effect of over-regulation,” Hancock wrote. “Implementation will be done in a way that as far as possible preserves the concepts of the Data Protection Act to ensure that the transition for all is as smooth as possible, while complying with the GDPR and DPLED in full.”
In short, any changes to UK law will be designed around existing international frameworks such as GDPR, which already includes provisions such as individuals being able to exercise their “right to be forgotten” and request that their personal information be deleted, as well as the potential for much larger penalties for organizations that suffer data breaches. As the BBC reported, the current maximum fine for breaking existing data breach protection laws is £500,000, and that will be increased up to £17 million or 4% of global turnover.
As Daradjeet Jagpal noted, the UK government intends to apply for some exemptions from the GDPR, such as allowing organizations other than police to process personal data on criminal convictions and offences, as well as allowing automated data processing — with the caveat that individuals will have the right to challenge any resulting decisions and request human intervention.
Numerous surveys this year have noted that a significant percentage of organizations remain unprepared for the upcoming implementation of GDPR, which is set to go into effect on May 25, 2018. For example, Veritas reported that only nine percent of UK organizations that believe they are prepared for the GDPR are likely in actual compliance. Organizations should remain aware of any potential changes in data protection laws such as GDPR and work to ensure that they will be in compliance with those changes before they become the law of the land.




 Law enforcement continues to target activity on the dark web following the recent takedown of AlphaBay and Hansa Market, two of the three largest cybercriminal marketplaces on the dark web.
Law enforcement continues to target activity on the dark web following the recent takedown of AlphaBay and Hansa Market, two of the three largest cybercriminal marketplaces on the dark web.