DDoS attacks are growing in size and sophistication, says a new report from Arbor Networks, and those attacks have continued to impact a variety of organizations over the past few weeks.
According to Arbor networks, a current average-sized DDoS attack is capable of taking down almost any organization’s server at about 1 Gbps. The average attack size in the first half of 2016 was 986 Mbps, which was a 30% increase over 2015. It is project that the average size of a DDoS attack will reach 1.15 Gbps by the end of 2016.
Some highlights from the report include:
- An average of 124,000 DDoS events per week over the last 18 months.
- A 73% increase in peak attack size over 2015, to 579 Gbps.
- 274 attacks over 100 Gbps monitored in the first half of 2016 compared to 223 throughout all of 2015.
- 46 attacks over 200 Gbps monitored in the first half of 2016 compared to 16 throughout all of 2015.
- The U.S., France and Great Britain are the top targets for attacks over 10 Gbps.
Lastly, reflection amplification attacks have continued to grow in popularity. The majority of larger DDoS attack utilize this technique by using attack vectors such as DNS servers. Because of this, DNS was the most used protocol in 2016, taking over from NTP and SSDP in 2015, according to the report. The highest recorded reflection amplification attack size during the first half of 2016 was 480 Gbps.
DDoS attacks have been conducted for monetary gain, notoriety, retaliation, and even for personal pleasure.
Trending DDoS Attacks
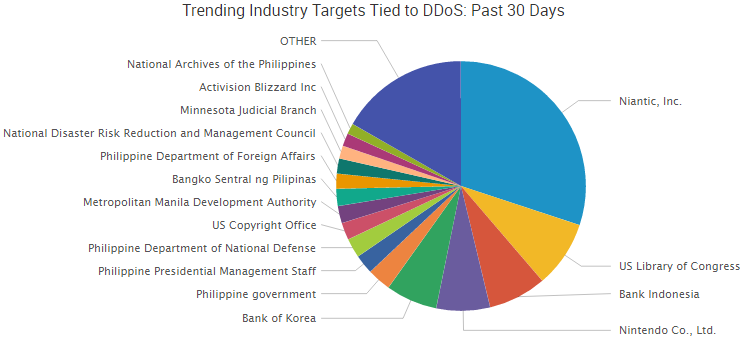
Over the last couple weeks, many organizations have been targeted with DDoS attacks. The most talked about DDoS attack over the last 30 days is tied to the controversial and very popular Pokemon GO. A group called PoodleCorp claimed credit for the attack, with a motivation very similar to another infamous hacking group called Lizard Squad — they did it for the LULZ.
Not all the recent DDoS attacks were done for the LULZ, as many appear to be out of retaliation for past events. Here is a breakdown of some of the top trending DDoS attacks over the past 30 days.
Pokemon GO Server
On Saturday, July 16 a DDoS attack took down all Pokemon GO servers, which left many players unable to hunt for their Pokemon. The group behind the attack is a newer hacktivist group known as PoodleCorp. The servers were down for several hours before reestablishing a connection for players.
On July 18, the Pokemon servers were hit with another DDoS attack, this time from the group known as OurMine. The group said that “no one will be able to play this game till Pokemon Go contact us on our website to teach them how to protect it!”
On July 20, PoodleCorp announced plans for an upcoming attack against the Pokemon servers that is scheduled for August 1.
MIT
Security researchers have discovered more than 35 DDoS attacks targeting the Massachusetts Institute of Technology (MIT) so far in 2016. The attack vectors used in these campaigns involved devices vulnerable to reflection and amplification attacks and spoofed IP addresses. It appears the bulk of attacks were carried out using booter or stresser services. Stresser services are a concern for organizations and the proliferation of DDoS attacks, as the cost to utilize these services are often extremely low.
Philippines Government Websites
The Filipino government announced this week that 68 separate websites tied to the Philippines government were hit with DDoS attacks. The attacks started July 12 and carried over to the next few days.
It is believed that China is responsible for the attacks as they correspond with a ruling made by the Permanent Court of Arbitration at the Hague in the Netherlands that favored unanimously for the Philippines over China. The ruling was over newly created islands located in the West Philippine Sea that China claimed even though those islands were in Philippines’ maritime territories.
Some of the government websites affected by the DDoS attacks were also defaced, signed with the words “Chinese Government.” There is no actual evidence at this time that China was behind the attacks, but it appears this is likely the case due to the extremely tense international relationship between the two countries.
Steemit
The social network Steemit announced on July 14 that an unknown attacker was able to hack into user accounts and steal the crypto-currency known as Steem Power and Steem Dollars. More than 260 users were affected by the attack, and about $85,000 of the crypto-currency was obtained.
In response to the attacks, Steemit fixed the issue and restored all stolen funds to the users. As soon as the company made this announcement, it was targeted with a DDoS attack. The attack did little to affect the social network, as the company used the attack as an opportunity to take down its servers for maintenance and other upgrades.
WikiLeaks
WikiLeaks servers suffered a DDoS attack last Monday that lasted through Wednesday. The DDoS attack appears to be in response to WikiLeaks’ announcement of an upcoming data dump belonging to Turkey’s biggest political party — AKP (Justice and Development Party).
The cache of data contained 300,000 emails and 500,000 documents that belonged to the party. The announcement came three days after the failed military coup in Turkey which saw the deaths of 208 people.
The DDoS attack prevented WikiLeaks from posting the information. As of July 20, WikiLeaks servers were back online and the data was released.
U.S. Congress Websites
The U.S. Congress website along with two adjacent websites — the U.S. Library of Congress and the U.S. Copyright Office — were the victims of a DDoS attack that lasted for three days. The attack started with the Library of Congress website on the evening of July 17 and slowly enveloped the other websites over the next couple of days.
As of Wednesday the websites are up and running normally. It is not known who is behind the attack or what the motivation for the attack was.
Brazil
A Rio court in Brazil was the target of a DDoS attack perpetrated by Anonymous. The attack took place on Tuesday and only lasted a few hours. Anonymous attacked the Rio court for its decision to block the controversial Whatsapp throughout Brazil. The decision told ISPs to block the app, and Brazil’s five major ISP operators — Claro, Nextel, Oi, TIM, and Vivo — all complied with the order.
The tensions between WhatsApp and Brazil go back to February 2015 when Whatsapp was unable to help Brazilian law enforcement by decrypting messages sent over the social network. Brazilian courts have fined and temporarily banned Whatsapp, arrested a Vice President for Facebook Latin America for being linked with the social network, and now a permanent ban is put in place. However, due to the Anonymous DDoS attack the Brazil court lifted the ban on Whatsapp.