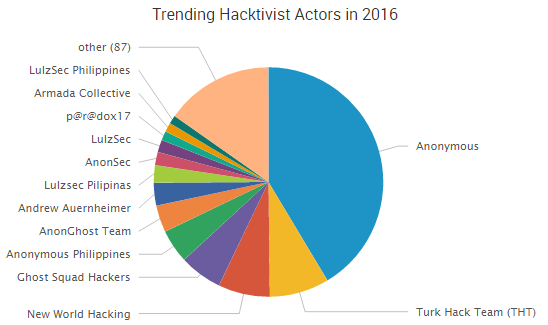
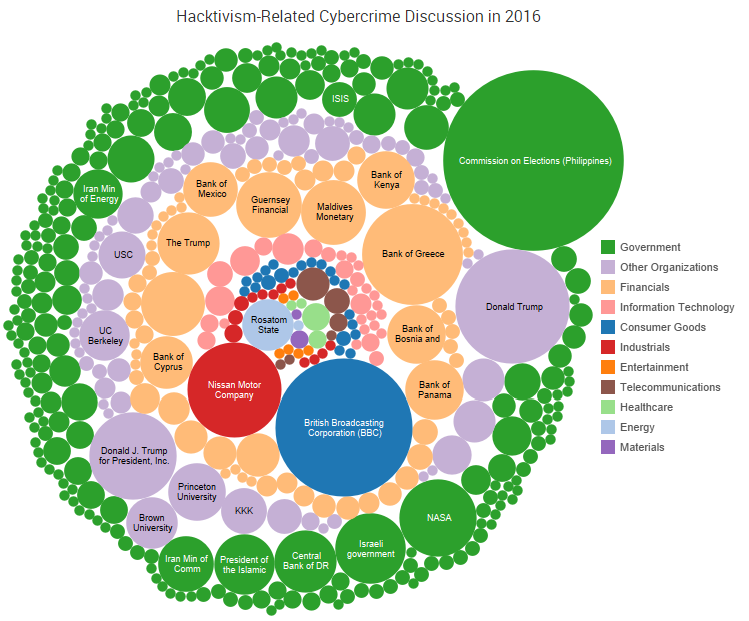
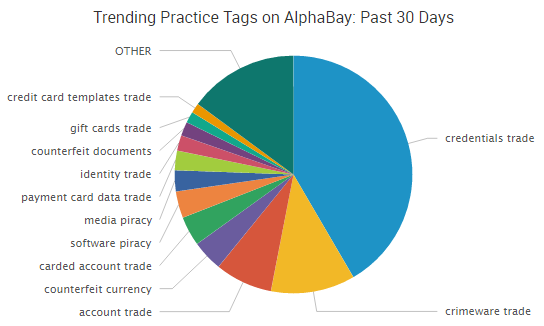
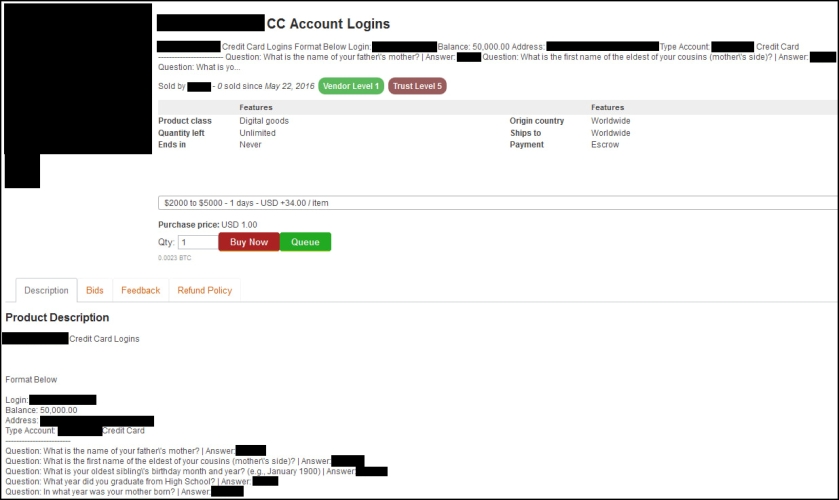
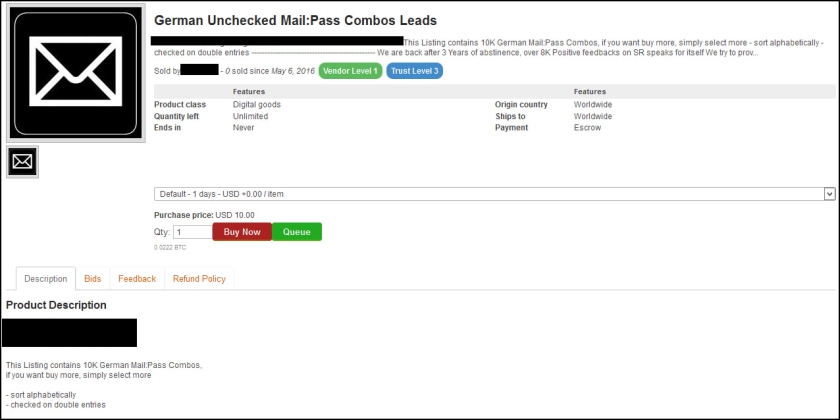
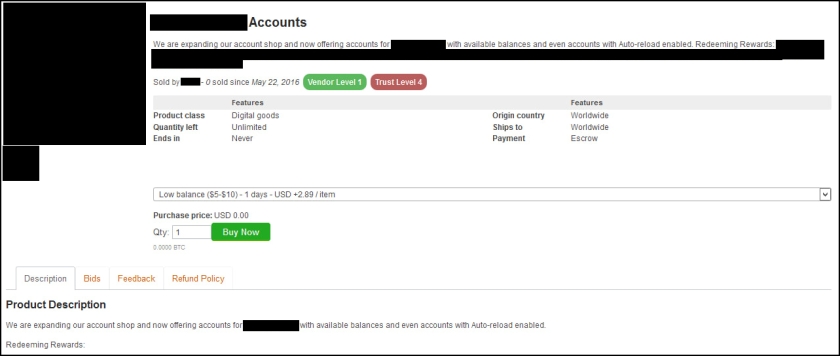
Organizations believe their vulnerability management programs are more mature than they really are, and the time it takes to remediate vulnerabilities remains an issue for many businesses, according to several reports.
A SANS whitepaper, What Are Their Vulnerabilities?: A SANS Survey on Continuous Monitoring, concluded that security practitioners are overconfident in their current state of continuous monitoring:
… survey results starkly illustrate that we are approaching a dangerous state in which we believe we have appropriately addressed problems, though we have, in fact, not adequately remediated them—therefore unknowingly leaving a window of opportunity open for attackers.
“Each of the questions taken on their own – there’s nothing really major that’s unsound. But looking at those questions together is very interesting,” said David Hoelzer, SANS Fellow Instructor, author of the paper, and founder and CISO of CyberDefense, the parent company of Enclave Forensics.
“More than half of these [organizations] are saying that they are mature or maturing. They say that, but then when we look at the coverage of assets … no one is even willing to say that they are covering 100% of their publicly exposed systems.”
Hoelzer, who was a guest on our vulnerability management podcast last October, said that gap in perception is a cause of concern.
“I would not define what we’re seeing in that report as anything like mature,” he said. “It seems as though our criteria or the bar we’re trying to reach is not high enough.”
Closing the Remediation Gap
One of the biggest challenges around vulnerability management is the time it takes organizations to remediate those vulnerabilities, or the remediation gap.
According to a 2015 Kenna Security report, The Remediation Gap: Why Companies Are Losing the Battle Against Non-targeted Attacks, even “conservative” estimates found that the window of opportunity for many exploits remains significant:
- On average, it takes businesses 100-120 days to remediate vulnerabilities.
- At 40-60 days, the probability of a vulnerability being exploited reaches over 90 percent – indicating that most successfully exploited vulnerabilities are likely to be exploited in the first 60 days.
- The gap between being likely exploited and closing a vulnerability is around 60 days.
“The gap that we’re looking at is getting much bigger, and I think that is happening because attackers are getting really, really good at automated attacks,” said Kenna Security’s senior data scientist Michael Roytman, who was also featured on the podcast.
Old Vulnerabilities, New Problems
According to Roytman, enterprises often have a huge backlog of vulnerabilities. That “security debt” is one of the primary reasons for the remediation gap. In addition, it can be difficult to know which of those vulnerabilities are actually being exploited.
For example, attackers continue to exploit old vulnerabilities, as pointed out in the report:
- CVE-2010-3055 was exploited 121,000 times in 2014. It allows attackers to run arbitrary code in phpmyadmin via a POST request, and phpmyadmin runs millions of sites worldwide. It’s a CVSS 7.5, which means it’s bound to fly under the radar more often than not. But it shouldn’t.
- CVE-2002-0649 is an ancient worm that exploits SQL Server 2000 and Microsoft Desktop Engine 2000. Reading the Wikipedia article on the worm makes it seem like it’s a long forgotten problem, but we witnessed 156,000 successful exploitations in 2014. It’s not new, it’s not hip, it’s not current, so one talks about it – but it’s a significant threat.
- CVE-2000-1209 is also not to be forgotten, with 272,000 successful exploitations. It exploits Microsoft SQL Server 2000, SQL Server 7.0, and Data Engine (MSDE) 1.0, including third party packages that use these products such as Tumbleweed Secure Mail (MMS), Compaq Insight Manager, and Visio 2000.
The report concluded: “These vulnerabilities are not new – in fact, they’re extremely old – and yet they perfectly represent the kind of unremediated vulnerabilities that automated attacks attempt to find. They’re the windows that the criminals rattle around and try to pry open.”
“Huge Opportunity” for Threat Intelligence
Integrating threat intelligence into vulnerability management is recent development, Roytman said, as the data available now wasn’t available five or ten years ago. But threat intel can help provide the biggest bang for the buck in terms of deciding which of the potentially thousands of actions an organization should take first.
“What’s surprising to me is the lack of information about what is being exploited,” Roytman said. “Integrating those data sources, disseminating that knowledge, is something that can really shorten the remidation gap, and it was surprising to me to see how many enterprises don’t have that information integrated.”
He added: “We’re kind of at this crossroads where the data is flowing in, but maybe we’re not integrating it into our vulnerability managment practices, and that’s a huge opportunity.”
You can listen to our previous podcast on vulnerability management below for more information:
About the Podcast:
This special episode is all about the challenges and issues around vulnerability management. David Hoelzer – SANS Fellow Instructor, dean of faculty for the SANS Technology Institute, and founder and CISO of CyberDefense, the parent company of Enclave Forensics – discusses the recent SANS survey and whitepaper “What Are Their Vulnerabilities?: A SANS Survey on Continuous Monitoring.” Among the findings is that “we are approaching a dangerous state” where companies believe they are doing better than they are – leaving a window of opportunity for attackers.
Kenna Security’s senior data scientist Michael Roytman also joins the podcast to discuss their recent report, “The Remediation Gap: Why Companies Are Losing the Battle Against Non-targeted Attacks.” The report estimated that most companies take an average of 100-120 days to remediate vulnerabilities. We chat about the state of vulnerability management, the challenges facing organizations, and what businesses can do to improve on that front.