Payment card breaches were back in the news again this week as Forever 21 announced that it is investigating a point-of-sale breach (POS) at some of its stores, and several other organizations issued breach announcements related to stolen payment card data.

Forever 21 said that it received a report from a third party about potential unauthorized access to payment cards at some of the company’s stores, and the ongoing investigation is focusing on POS transactions made in stores between March 2017 and October 2017.
“Because of the encryption and tokenization solutions that Forever 21 implemented in 2015, it appears that only certain point of sale devices in some Forever 21 stores were affected when the encryption on those devices was not in operation,” the company wrote.
In addition, organizations continue to submit breach notification letters to various state attorneys general regarding the previously disclosed breach involving Sabre Hospitality Solutions SynXis Central Reservations system, including The Whitehall Hotel and JRK Hotel Group, both of which were impacted from August 10, 2016, through March 9, 2017. The Register also reported that Jewson Direct is notifying customers that their personal and payment card information may have been compromised due to the discovery of unauthorized code on its website. However, the company said the inclusion of card data in the notification was only “an advisory measure” as the investigation is ongoing.
The recent breaches, as well as other breaches such as Sonic, may have led to an increase in payment card fraud activity in the third quarter of 2017. Fraud activity is also expected to increase as consumers buy gift cards and other items over the holiday shopping season.
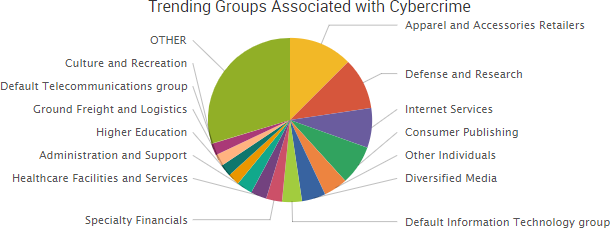
Other trending cybercrime events from the week include:
- Organizations expose data: Researchers discovered a publicly exposed Apache Hive database belonging to ride-hailing company Fasten that contained the personal information of approximately one million users as well as detailed profiles of its drivers. A researcher said the Chinese drone maker DJI has exposed a variety of sensitive information via GitHub for up to four years, in addition to exposing customer information via insecure Amazon S3 buckets. Researchers discovered two insecure Amazon S3 buckets appearing to belong to the Australian Broadcasting Corporation’s commercial division, including information regarding production services and stock files. The Maine Office of Information Technology said that approximately 2,100 residents who receive foster care benefits had their personal information temporarily posted to a public website after an employee at contractor Knowledge Services uploaded a file containing their data to a free file-comparison website without realizing that the information would become publicly accessible. Dignity Health is notifying employees that some of their personal information was accidentally exposed to other employees.
- Employee email accounts compromised: ClubSport San Ramon and Oakwood Athletic Club is notifying employees that their W2 and tax statements were sent to a malicious actor following a phishing attack impersonating an executive. ABM Industries Incorporated is notifying employees that their personal information may have been compromised due a phishing attack that led to multiple email accounts being compromised. Saris Cycling Group is notifying employees that their personal information may have been compromised due a phishing email that led to an employee email account being compromised.
- Extortion-related attacks: The website of Cash Converters was hacked, and the actors behind the attack said they would release the data of thousands of UK consumers unless a ransom is paid. Little River Healthcare Central Texas is notifying patients of a ransomware attack that may have accessed their information and led to some data being irretrievably deleted when the clinic tried to restore the files. Far Niente Winery is notifying individuals of a ransomware attack that may have compromised their personal information.
- Other notable incidents: A group associated with Anonymous hacked the email accounts of an employee of Italy’s Defence Ministry and a member of the Italian police and then published a variety of information allegedly obtained from those accounts. Officials from Catawba County, North Carolina, said that malware shut down a number of county servers and caused temporary interruptions in service, as well as a number of spam emails being sent to county residents. Gallagher NAC is notifying individuals that their personal information may have been compromised due to “a small amount of data” being stolen from a database between June 18 and September 19. CafeMom is notifying customers that email addresses and passwords used to create accounts prior to July 2011 were compromised “at some point in the past.” AppDirect said that a phisher has been impersonating members of the company’s human resources, recruiting, and sales teams on job sites, and several people have applied to those fake listings and received fake job offers.
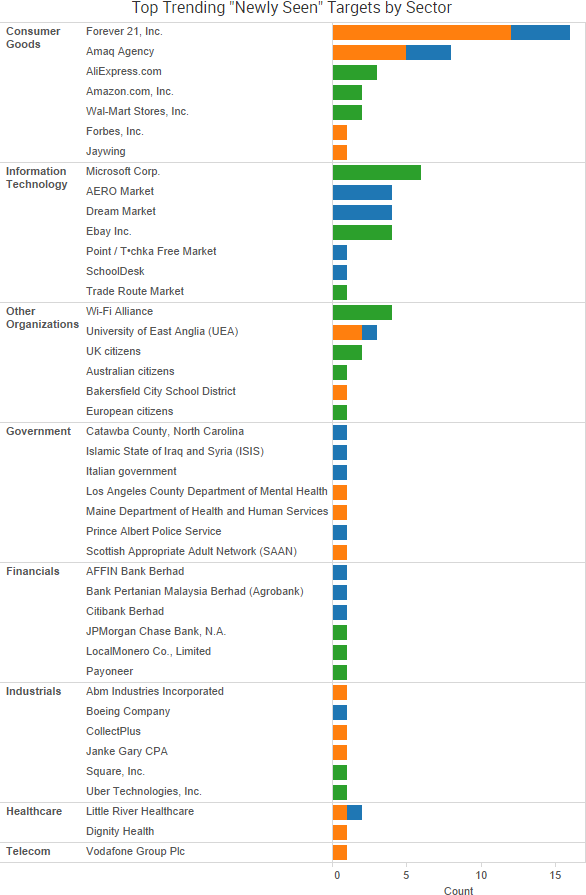
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
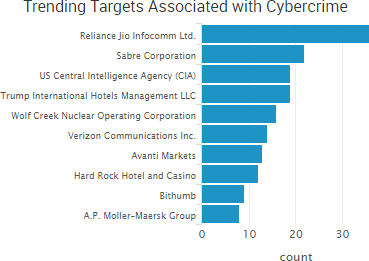
Cyber Risk Trends From the Past Week
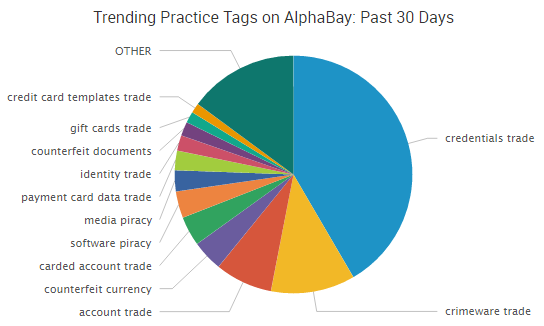
 Dark Web markets continued to make headlines this week as a key player in AlphaBay’s operations was charged and cyber-attacks against other still-active dark web marketplaces temporarily disrupted operations.
Dark Web markets continued to make headlines this week as a key player in AlphaBay’s operations was charged and cyber-attacks against other still-active dark web marketplaces temporarily disrupted operations.
Federal prosecutors allege that Ronald L. Wheeler III, of Streamwood, Illinois, worked as a spokesperson for the now-shuttered Dark Web marketplace AlphaBay. AlphaBay had grown to become the largest-ever Dark Web marketplace before it, along with the popular Hansa Market, were taken offline by law enforcement this past summer.
Wheeler is accused of working alongside Alexandre Cazes, a 25-year-old Canadian who was alleged to be the owner of AlphaBay known as “Alpha02.” Cazes reportedly committed suicide in his Thai jail cell a week after being arrested in July.
The Associated Press reported that Wheeler has pleaded not guilty to the AlphaBay-related charges, but prosecutors allege that he worked with Cazes using the name “Trappy” to moderate the AlphaBay forum on reddit, mediate sales disputes, and provide other non-technical assistance to users.
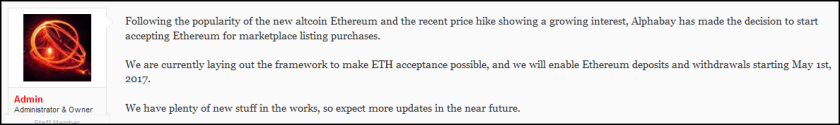
As SurfWatch Labs previously reported, the downfall of AlphaBay and Hansa Market elevated Dream Market to the temporary king of the Dark Web. However, Dream Market other popular markets have been the target of DDoS attacks over the past few weeks, making the sites difficult to access for some users. Those attacks can delay purchases beyond the already congested list of pending Bitcoin transactions, which is slowing down both legitimate and criminal transactions.
Prior to being seized, AlphaBay had grown to accept multiple payment options, including Ethereum and Monero; however, Dream Market still only accepts Bitcoin, and that restriction may help push some users towards other markets that have more, and quicker, payment options as the Dark Web marketplace continues to evolve in AlphaBay’s absence.








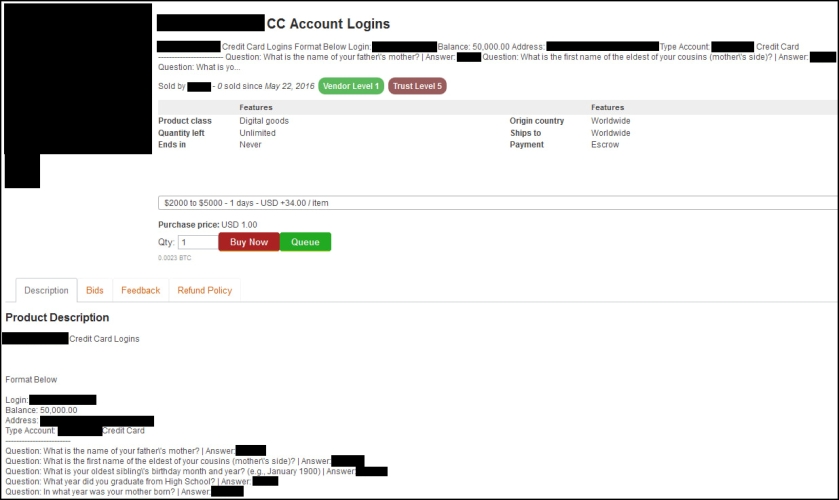
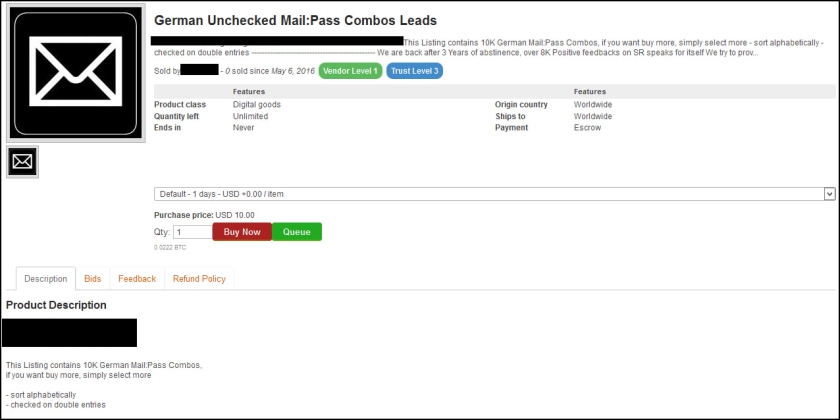
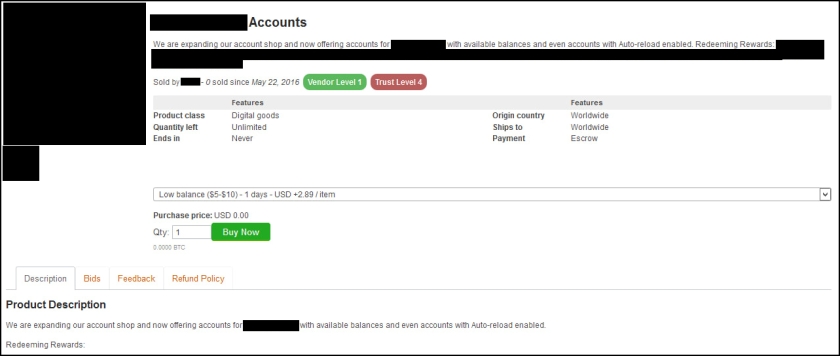
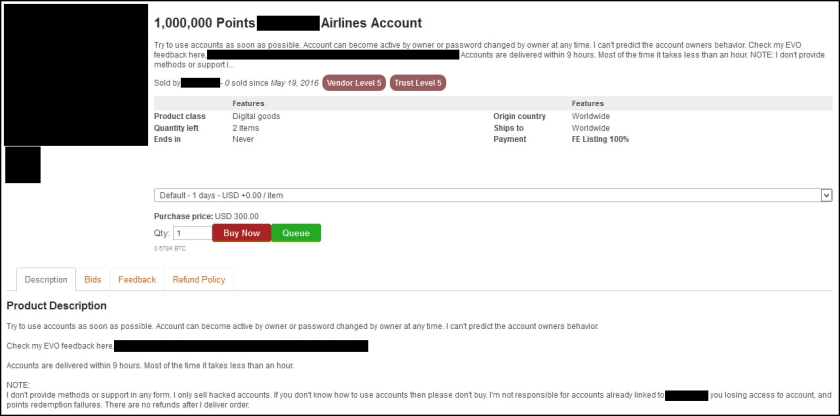
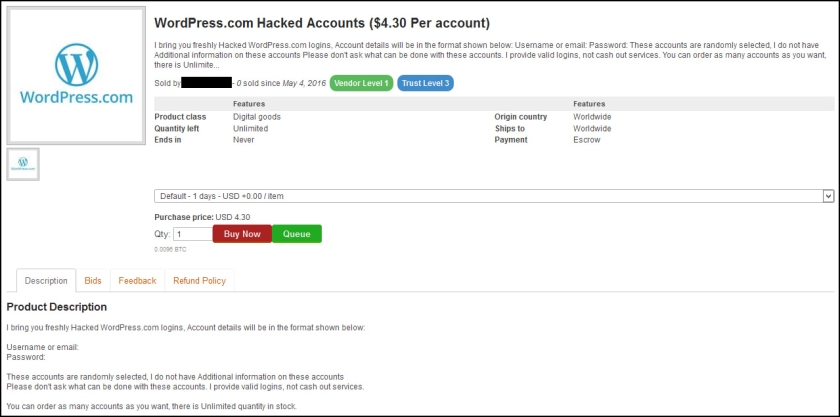
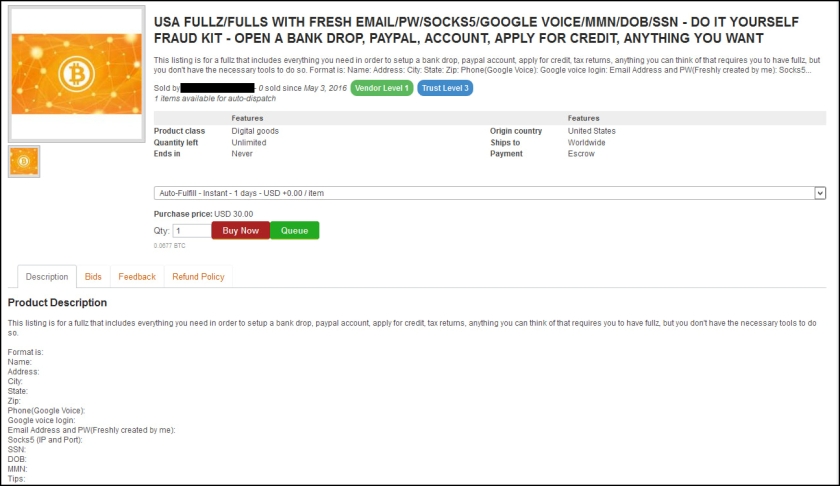
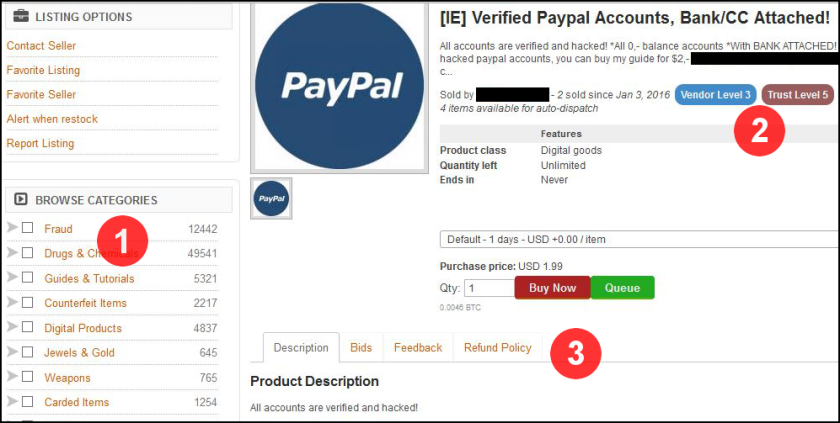
 The dark web marketplace
The dark web marketplace