The recent theft and potential sale of various healthcare databases has once again put the sector at the forefront of cybercrime — and makes many wonder how their information is affected by criminal activity on the dark web. While healthcare-related data is not nearly as prevalent on the dark web as other sectors like financial services, SurfWatch Labs has observed a variety of items being offered up for sale in addition to this week’s headline-making healthcare databases.
As previously noted, common threat intelligence found on the dark web includes compromised credentials, stolen financial information, stolen intellectual property, threats stemming from an organization’s supply chain, and information on a wide range of hacking services and other cybercrime tools. These same categories also apply to healthcare organizations.
Over the past year SurfWatch Labs has observed direct healthcare breaches, third-party breaches that have impacted healthcare organizations’ employee accounts, fraudulent prescriptions, and other healthcare-related cyber threats.
What’s Being Sold on the Dark Web Now?
This week, several healthcare databases were put up for sale on the dark web by an actor going by the name “TheDarkOverlord” — along with a hefty price tag for that information.
On Monday, after previously posting three different databases that contain names, addresses, Social Security numbers, birth dates and some phone numbers of 655,000 individuals, the hacker told the Daily Dot that he was sitting on a “large” number of other databases. On Tuesday he followed through on that claim, adding for sale a database of 34,000 records from a New York Clinic as well as a health insurance database with 9.3 million patients, which he said was stolen using a zero-day vulnerability “within the RDP protocol that gave direct access to this sensitive information.” On Wednesday he again made headlines by naming one of the companies breached, Midwest Orthopedic Clinic in Farmington, Missouri, and said that the owner “should have just paid up to prevent this leak from happening.”

A posting of more than 9 million records is on the extreme end of the price spectrum, and it could be that the actor is trying to spin up some media attention in order to better extort potential victims or drive future sales — if he is indeed sitting on many more databases to sell.
More typical of the type of healthcare-related information found for sale on the dark web is counterfeit documents and other identity information that can be used for different types of fraudulent purposes, including but not limited to medical. Although this information does not sell for hundreds of thousands of dollars and make national headlines, it is much more prevalent.
For example, fraudulent medical cards from around the world are available for approximately a few hundred dollars.
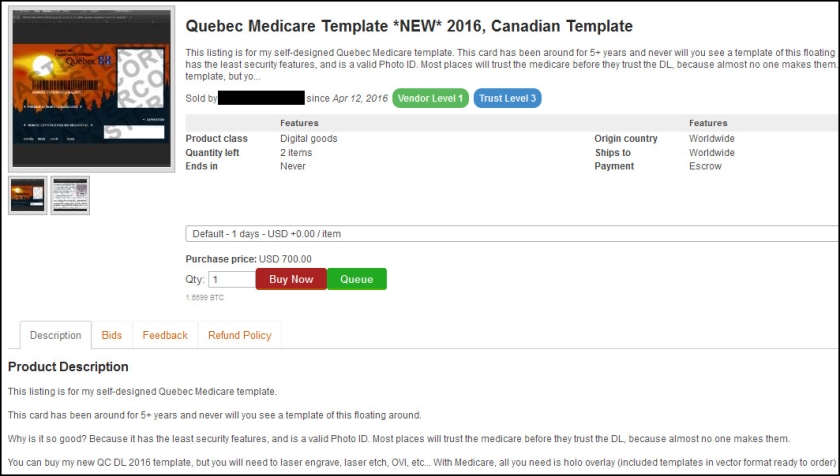
In the posting below, a vendor is selling a Quebec Medicare card template for $700. “Why is it so good?” the vendor asks rhetorically. “Because it has the latest security features, and is a valid photo ID. Most places will trust the Medicare [card] before they trust the DL [driver’s license] because almost no one makes them.”
Likewise, non state-sponsored health cards are available. The listing below, from a now-defunct dark web marketplace, is selling a U.S. health insurance card for $40.
Why? “These are to provide proof that you have health insurance in the United States,” the seller wrote, adding that an insurance card like the one provided is an excellent way to round out a fake identity. “If a fake ID is questioned, this can be pulled out to back it up and eliminate any question. [It] may save you. In addition it may be used as a secondary form of ID to open up a PO box under a false identity.”

Some items for sale on the dark web leverage physicians’ identities. The posting below is from a vendor who is currently selling a signed California drug prescription form from a medical group with six different doctors. “These are REAL doctors Rx Scripts, from a REAL CA medical practice,” the vendor wrote. “These are extremely hard to come by.”
The form, which includes up to three prescriptions, is selling for $75, and the vendor will even fill out the script for an extra $100 if the buyers are unsure how to do so.

Additionally, the dark web is often associated with illegal drugs – and for good reason. Reporting on dark web markets such as Silk Road tends to focus on hard drugs; however, prescription drugs are readily available. They can be purchased from a variety of sellers on nearly every dark web marketplace.

Utilizing Cyber Threat Intelligence
In addition to the postings from open marketplaces shown above, there is information to be gained from the private cybercriminal forums and markets on the dark web. As more researchers and law enforcement turn to the dark web for intelligence gathering purposes, cybercriminals have begun to take more precautions. Some markets require a referral to gain access. Some require a user fee. This chatter, both the public postings and more restrictive groups, can provide important insight into the most active cyber threats facing your organization.
For example, SurfWatch Labs has previously observed certain forum members requesting health insurance records from specific companies – presumably to assist in perpetrating insurance fraud as one actor was specifically looking for “high cost treatments.” Knowing which actors are targeting an organization, what those actors are looking for, and other chatter around potential cyber threats can be invaluable when it comes to planning, budgeting and implementing a company’s cyber risk management strategy.
This type of dark web threat intelligence provides direct insight into the malicious actors that target healthcare organizations, and it goes beyond the big ticket items that generate news headlines and spark a national conversation. Those stories are important, but in many ways the dark web shines a light on a cybercrime problem that is much more insidious: death by a thousand cuts.
With so many different threats out there, knowing which threats to focus on is critical. In many ways cybersecurity is simply about effective prioritization, and to that point, cyber threat intelligence and the dark web is a vital aspect.