The end of the year is drawing nearer, and with that comes a handful of traditions: family gatherings, eggnog by the fire, and everyone’s annual list of cybersecurity “predictions.” While it’s a bit semantic, I’m personally not a big fan of the term “predictions.” As someone who lives in the intel world, it’s more about looking at the data and making forecasts using probabilities. In all of the cyber threat intelligence that we provide our customers, we include a confidence level based on what we’re seeing and the probability of that threat impacting a specific customer.
I start out with the above just to level set the rest of this blog (and the next several blogs around 2017 cyber forecasts). When it comes to identifying trends and making a forecast on probability of what threats make waves in 2017, based on the success of ransomware attacks I have moderate confidence that we will see growth of more traditional extortion-related cybercrime.
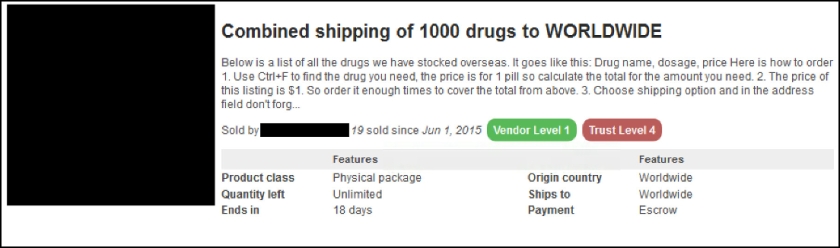
SurfWatch Labs has seen a steady growth in the number of targets publicly associated with extortion, blackmail and ransoms over the past few years, and we expect that number to rise even higher in the coming year.
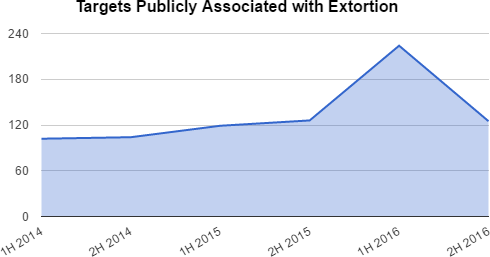
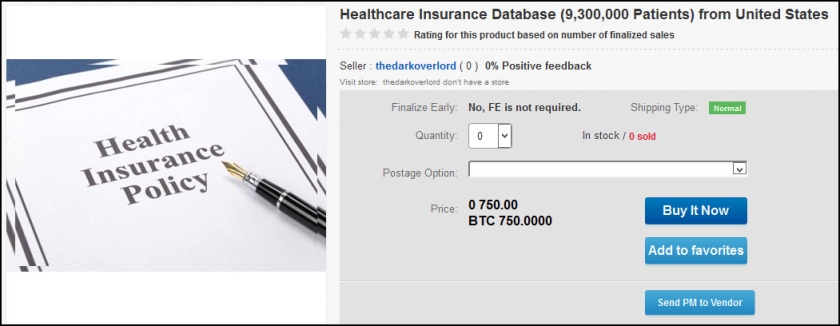
One of the best and most recent examples of malicious actors using extortion is the hacking group known as TheDarkOverlord, which has breached, attempted to extort and then publicly shamed a variety of organizations over the second half of 2016.
The latest incident is the November breach of Gorilla Glue. TheDarkOverlord claimed to have stolen more than 500 GB of data, including research and development material, intellectual property, invoices and more. The group then offered Gorilla glue its signature “business proposition.” As we wrote in a SurfWatch Labs blog earlier this year, the proposition is simple: pay the blackmail or face further data leaks and public shaming. After what TheDarkOverlord described as “a moderate dispute” with Gorilla Glue over payment — we’re guessing Gorilla Glue refused to pay — TheDarkOverlord shared a 200 MB cache of files with the media to help spread the story.
The evolving use of the media is actually one of the more interesting tactics used by TheDarkOverlord and other successful extortion groups this past year. Extortionists have referenced news coverage in their demands, prompted users to research past victims, and impersonated cybercriminals with established media coverage — all in an effort to lend credibility to their threats.
For example, back in April CloudFlare reported that a group using the “Armada Collective” name was blackmailing businesses with an extortion email that read, in part:
We are Armada Collective.
http://lmgtfy.com/?q=Armada+Collective
Your network will be DDoS-ed starting [date] if you don’t pay protection fee – 10 Bitcoins @ [Bitcoin Address].
If you don’t pay by [date], attack will start, yours service going down permanently price to stop will increase to 20 BTC and will go up 10 BTC for every day of attack.
This is not a joke.
The link in the email led to a Google search of the group, allowing victims to quickly see that some security researchers had described Armada Collective as a “credible threat.” Except the attackers were not part the original Armada Collective. They were copycats simply exploiting the original group’s already established name. As CloudFlare later discovered, there was not “a single incident where the current incarnation of the Armada Collective has actually launched a DDoS attack.” Despite the lack of follow through, the group managed to extort hundreds of thousands of dollars from the victims.
Leveraging the media in that manner is something the SurfWatch analyst team has observed more frequently over the past year. However, news outlets and victims are starting to become more skeptical of claims. That’s one of the reasons threat actors such as TheDarkOverlord have evolved their tactics to establish a more direct and somewhat dysfunctional “relationship” with the media. Bloggers and news outlets get access to a direct source of stolen data that can help help generate headlines. Extortion groups receive the platform necessary to incite worry in the partners and consumers of the victim organization, adding pressure to pay extortion demands.
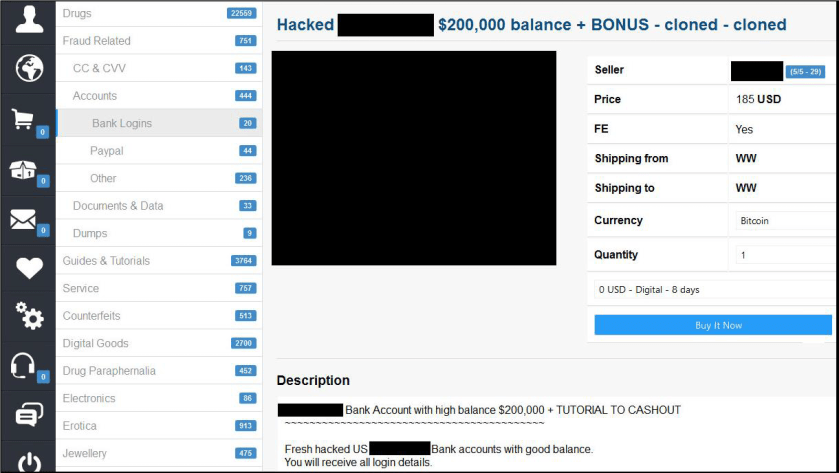
With cybercrime events seeing more mainstream coverage each year and extortion proven to be a successful, low-effort tactic, expect that dysfunctional relationship to continue to develop in the coming year. Extortion has proven particularly useful when it comes to the theft of sensitive customer data as it provides multiple additional ways for a threat actor to monetize information. If the victim organization doesn’t provide immediate compensation via an extortion payment, individual customers may then become targets of blackmail — sometimes years into the future.
Adultery site Ashley Madison announced its data breach in the summer of 2015, but individuals exposed in that breach were still being sent blackmail letters and emails nearly a year later. Some victims reported that when they didn’t pay, the blackmailers then followed through on their threats by sending letters about the individuals’ alleged infidelity to family, friends, and workplaces.
More recently, hackers stole customer information from Valartis Bank Liechtenstein and were reportedly threatening individual customers — including politicians, actors and high net worth individuals — that their personal information will be leaked if they do not pay 10 percent of their account balances in ransom.
These extortion and blackmail attempts are not nearly as prevalent as ransomware, but they follow the same principle of quick and easy monetization via the victims themselves. The past year has proven that the media can be successfully used as a tactic to better extort both organizations and individuals, particularly when it comes to sensitive information that may lead to brand damage or embarrassment. That trend will likely grow in 2017 as threat actors look to take advantage of every avenue when attempting to monetize future data breaches.


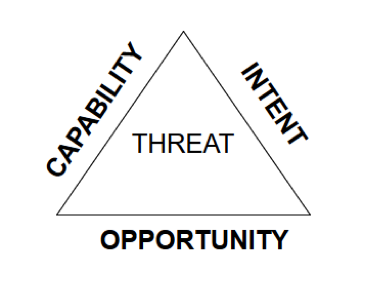 There are many ways to evaluate threats, but I tend to revert to my Navy training when thinking about the cybersecurity of our customers. Our rules of engagement dictated evaluating threats from three avenues: the capability, intent and opportunity to cause harm.
There are many ways to evaluate threats, but I tend to revert to my Navy training when thinking about the cybersecurity of our customers. Our rules of engagement dictated evaluating threats from three avenues: the capability, intent and opportunity to cause harm.