Technology advances continue to push boundaries — remember when a phone was just a phone?! More “smart” devices, more interconnectivity between businesses and customers, businesses and suppliers, businesses and partners … all of this speeds transactions and the way business is conducted. Information is shared, items are purchased — all with the click of a button these days.
Inherent in all this productivity goodness is that your digital presence is expanding across many channels that are outside the traditional company boundaries. With this expanding presence comes greater risk. It’s become much harder to have visibility of the level of risk your organization faces across the many digital channels. You of course have physical risks that have been around in the past, but now can be tied into cyber activity. You have cybercriminals (and potentially other types of adversaries) looking to exploit weaknesses for financial or competitive gains. Social media. Your supply chain. Insider risks (whether malicious or negligent). On and on …
The more connections you have, the more presence you have, the more opportunity that exists for malicious actors. This isn’t to say close your business off from the world. That’s obviously not realistic and not a good way to do business. But there two essential things you can do to minimize this issue:
- Get an understanding of your level of presence and the level of risk associated to different areas. Having this intel sets the stage for how to stay on top of your risk and proactively address it.
- Identify people, processes and technology to help continuously monitor and manage these risks — so they don’t become larger issues for your business.
Some questions to pose to your organization as a starting point:
- Who in the organization has accountability for digital risk? Corporate security? Info security? Risk management? Legal? Compliance? Executive suite and/or board level? Brand officer?
- What about “smart” building devices? Who owns these?
- What about “smart” devices brought in by your employees? How are these managed? And by whom?
- How does digital risk play into the organization’s overall risk management process?
- What processes are in place to limit the risk?
- What processes are in place to address a threat?
This list isn’t exhaustive, but you get the idea of how you need to think about this issue.
We recently announced a strategic partnership with PlanetRisk to deliver comprehensive cybersecurity and enterprise risk analytics and visualization for Fortune 1000 and government customers. Together we’re hosting a live webinar discussion on How to Mitigate Risk from Your Expanding Digital Presence.
I look forward to seeing you on the webinar. For more information and to sign up for the webinar, visit: http://info.surfwatchlabs.com/Webcast/How-to-Mitigate-Risk-from-Your-Expanding-Digital-Presence/05102017









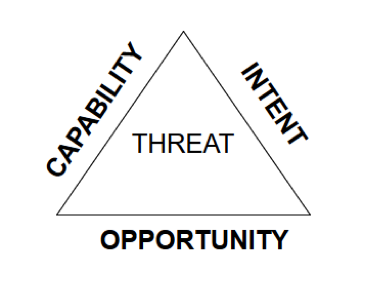 There are many ways to evaluate threats, but I tend to revert to my Navy training when thinking about the cybersecurity of our customers. Our rules of engagement dictated evaluating threats from three avenues: the capability, intent and opportunity to cause harm.
There are many ways to evaluate threats, but I tend to revert to my Navy training when thinking about the cybersecurity of our customers. Our rules of engagement dictated evaluating threats from three avenues: the capability, intent and opportunity to cause harm.