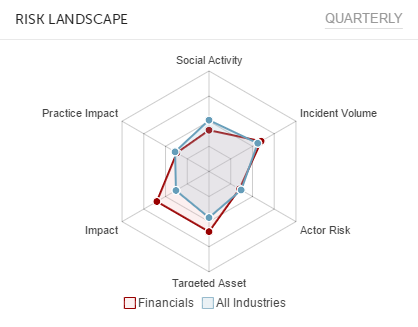
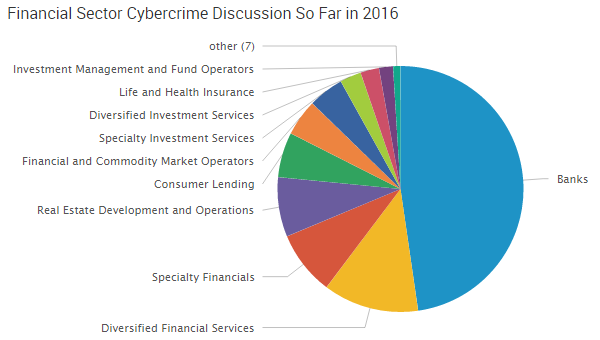
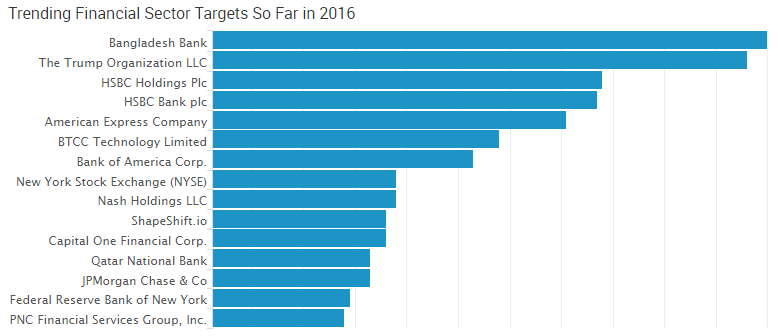
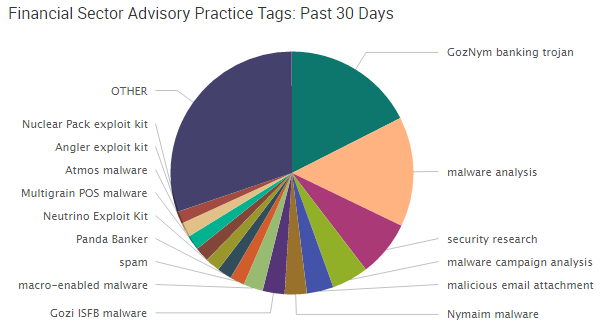
Over the past year, the number two Dark Web market in terms of activity was Nucleus. As of late 2015, this market had more than 25,000 vendor listings, but on April 13 of this year, Nucleus disappeared.
While it’s not the first time Nucleus has been down and it’s not uncommon for Dark Web markets to go offline, we are now one month into this “downtime.” As recently as May 8 there are still more than 5000 Bitcoins in the Nucleus wallet (a value of more than $2.25M USD). Here are some possible explanations:
- Exit Scam? There is a lot of talk from Nucleus Market buyers and sellers of an “exit scam.” Exit scams occur when the marketplace vendor wants out of the game and closes up shop, but doesn’t tell users and continues to accept payments in Bitcoin. If this is case, the owner of Nucleus Market may have pulled off quite the heist. However, there is a substantial quantity of bitcoins associated with the Nucleus Market and they continue to build each day. Since the market went offline there have been no withdrawals from the Nucleus wallet; however, there has been continuous deposits. Is the owner planning to grab that money and run? Or not?
- Hacked? Another possibility is that Nucleus was hacked and subsequently brought down. Legit business aren’t the only ones being victimized. There is some speculation that an actor who goes by the handle “theDmaster” exacted revenge on the market after he was kicked out. If this occurred, it’s possible that a) the access to the Bitcoins has been blocked as part of the attack or b) that the owners of Nucleus are in fact trying to get the market back up and running and thus have not run off with the Bitcoins.
- Busted? It’s also possible the Nucleus market was busted by law enforcement and/or the site’s owners are in hiding. The alleged administrators of Nucleus recently posted a comment about Interpol seizing their servers and that they were now working with Dream Market (another dark web marketplace) but this could just as easily be a plug from competitor Dream Market in the hopes of winning Nucleus market customers.
Investigations will of course continue into Nucleus Market but how does what we know now impact dark web trade?
Before its disappearance from the Dark Web, Nucleus market was one of the top places to go for:
- Drugs and paraphernalia
- Fraud related activity (such as payment card information, stolen accounts)
- Guides & tutorials (How to card; Get rich quick schemes; Black Hat SEO; Drug manufacturing)
- Services (such as hacking for hire, fraud related services)
- Counterfeits (i.e. money, apparel, tickets, etc.)
- Digital goods, media piracy
- Electronics
- Erotica
- Jewelry
- Lab supplies
- Weapons
Nucleus vendors now need to get their wares ready for sale on other markets. There has been significant buyer and vendor chatter about moving to AlphaBay, Dream Market, Hansa, Oasis, Valhala, Acropolis and new markets such as LEO. If they do, these vendors must re-establish street cred on the markets where they set up shop. It may also take time for buyers to find their preferred vendors.
What does this mean for you?
First, recognize there is no honor among thieves. Second, and more importantly, this highlights the “intelligence challenge” of dark web surveillance as markets and vendors disappear and sometimes reappear. By tracking the commodities being sold on the black markets, organizations can gauge the underground market economy and get an idea of what commodities are being actively sold, what prices they are being sold for, and how much volume they are moving. No different than a legitimate business, you can get a sense of what commodities are the top desired items and therefore gain an understanding of what the future targets may be. Most importantly, you will know if you look similar to those targets.
When markets such as Nucleus cease operations, the actors who were operating in that area will quickly scatter to new locations and start anew. From an intelligence perspective this creates an instance where past history measurements lose some steam and causes a moment of chaos until the market places begin to settle down.
While the Nucleus Market going offline is most impactful to the users who lost their money, it does illustrate the need for continuous monitoring of the black markets to understand the potential fraud footprint and how it shifts. For organizations that have to continuously battle a large fraud footprint, it is critical to maintain situational awareness of the ebb and flow of market change.