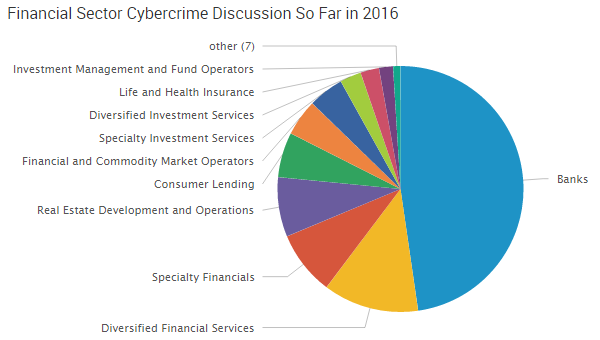
Although the financials sector hasn’t been as widely discussed as others this past quarter, cyber-attacks in the sector are having a greater impact, according to SurfWatch Labs’ data.

Since March 2016, the financials industry has made big headlines for high-profile cyber events involving the Central Bank of Bangladesh and most recently, Qatar National Bank. These two banks have contributed enormously to the amount of cybercrime discussion surrounding banks.
The Central Bank of Bangladesh is the top trending financials sector target so far in 2016. The multiple cyber-attacks against the Trump Organization – including an Anonymous campaign – and the January DDoS attack against HSBC Bank round out the top three targets.

Latest on Bangladesh Bank Heist
The $81 million bank heist of the Central Bank of Bangladesh is one of the most successful cyber bank thefts in history. The bank was attacked via SWIFT, a well-known and utilized international bank messaging system.
SWIFT stands for the Society for Worldwide Interbank Financial Telecommunication. The system authorizes payments between accounts and is recognized for its security. According to Michael Corkery of The New York Times, one financial analyst even called SWIFT “the Rolls-Royce of payments networks.”
Unfortunately for banks, SWIFT issued a warning to customers that cybercriminals have attempted similar bank thefts through its system.
“SWIFT is aware of a number of recent cyber incidents in which malicious insiders or external attackers have managed to submit SWIFT messages from financial institutions’ back-offices, PCs or workstations connected to their local interface to the SWIFT network,” the warning read.
One of the main problems with SWIFT is that not all banks put security features in place to protect against potential threats.
“SWIFT is a great organization,” said Chris Larsen, the founder of Ripple, to The New York Times. “But the system is fractured and antiquated. The way it is set up, you cannot totally isolate problems in a place like Bangladesh from the whole network.”
HSBC U.K. Banking System Taken Offline
In January 2016 Europe’s largest financial lender HSBC suffered a DDoS attack, keeping several banking customers unable to access their accounts. The attack took place on Friday, January 29, and services were restored on January 30.
This was the second website outage suffered by the bank in January.
The attack was particularly damaging due to its timing. HSBC was attacked on the last Friday in January, a particularly busy day for banks as the end of the fiscal year approaches. Millions of customers -– both online and mobile app users –- were affected by the attack.
HSBC never released any technical data about the incident. DDoS attacks can have an impact on brand reputation as well as loss of revenue. On average, a DDoS attack can cost about $40,000 per hour, according to a study conducted by Incapsula.
New Hybrid Malware Used In Bank Attacks
Cybercriminals are always looking for new, sophisticated ways to attack organizations. A new threat called GozNym malware has been identified targeting banks in the North America, Asia, and Europe. As SurfWatch Labs recently reported to customers, the malware has stolen over $4 million between 24 banks in North America alone.
The GozNym banking Trojan has been discussed frequently over the past 30 days.

GozNym is a hybrid malware, containing code from both the Nymaim and Gozi ISFB variants. The source code from the Nymaim malware is used to steal user data and login credentials. Once this data is obtained, the source code from the Gozi ISFB malware manipulates web sessions and conducts online banking fraud attacks. This nasty threat not only perpetrates bank fraud, it can also open the door for further malware attacks, including ransomware.
Like most malware, GozNym relies heavily on one factor to promote infection – human behavior. The malware is spread through exploit kits and Office macros, both of which require human interaction for its operation to take place.
Banks are an especially ripe target for cybercriminals due to the amount of transactions and data transferred between individuals and other organizations. Hacking tools such as malware and DDoS services can be purchased on the dark web for a surprisingly low price and used to create havoc and devastating financial loss for organizations. As demonstrated in the Central Bank of Bangladesh theft, it only takes one vulnerability to crack a company’s security, and the impact of those attacks is often more far reaching than other sectors.

