What’s Everyone Talking About? Trending Cybercrime Events
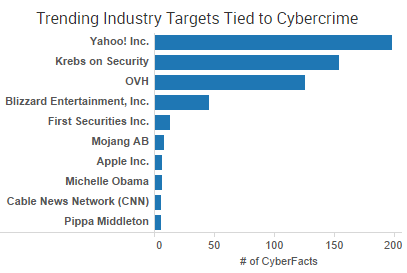 Yahoo was the week’s top trending cybercrime target as the fallout of a breach affecting more than 500 million accounts continues to play out. CEO Marissa Mayer has faced intense scrutiny from lawmakers and others over the handling of the company’s cybersecurity.
Yahoo was the week’s top trending cybercrime target as the fallout of a breach affecting more than 500 million accounts continues to play out. CEO Marissa Mayer has faced intense scrutiny from lawmakers and others over the handling of the company’s cybersecurity.
A Wednesday New York Times article citing a group of current and former employees painted a picture of Mayer as a CEO that often clashed with the security side of the organization over spending and refused to take action in several instances – including rejecting an automatic reset of user passwords after discovering a breach.
“Employees say the move was rejected by Ms. Mayer’s team for fear that even something as simple as a password change would drive Yahoo’s shrinking email users to other services,” the Times wrote.
A group of senators issued a letter to Mayer calling the two-year gap between the initial breach and announcement of the breach “unacceptable.” Sen. Mark Warner is also urging the Securities and Exchange Commission to investigate whether Yahoo properly informed investors of its data breach after reports surfaced indicating that Mayer was aware of the breach as early as July of this year.
“Yahoo has been engaged in an effort to sell its Internet business, including the unit affected by the breach, to Verizon since at least July 25, 2016, yet Yahoo reportedly did not inform Verizon of the breach until September 20, 2016,” Sen. Warner wrote in a letter to the SEC. “More puzzlingly, the company noted in a proxy statement as recently as September 9, 2016 that, ‘To the knowledge of Seller, there have not been any incidents of, or third party claims alleging, (i) Security Breaches, unauthorized access or unauthorized use of any of Seller’s or the Business Subsidiaries’ information technology systems.’”
Mayer isn’t the only CEO to come under fire from lawmakers this week. Wells Fargo CEO John Strumpf has become the butt of jokes on late night talk shows after being publicly lambasted by members of the House Financial Services Committee over the bank fraudulently opening more than 2 million customer accounts without their knowledge. Sen. Elizabeth Warren has repeatedly called for Strumpf to resign, and Rep. Michael Capuano said yesterday that Stumpf is “clearly and unequivocally guilty” of a range of crimes related to the scheme, including conspiracy to commit fraud, conspiracy to commit identity theft and racketeering. The backlash led to Wells Fargo announcing this week that Strumpf and former head of community banking Carrie Tolstedt would not receive a total of $60 million in unvested equity awards.
In addition to angry lawmakers, a group of former employees is suing the company, saying that they were forced to choose between either committing fraud by opening unauthorized accounts or losing their job. That lawsuit adds to a growing list of lawsuits that have filed against both Wells Fargo and Yahoo.
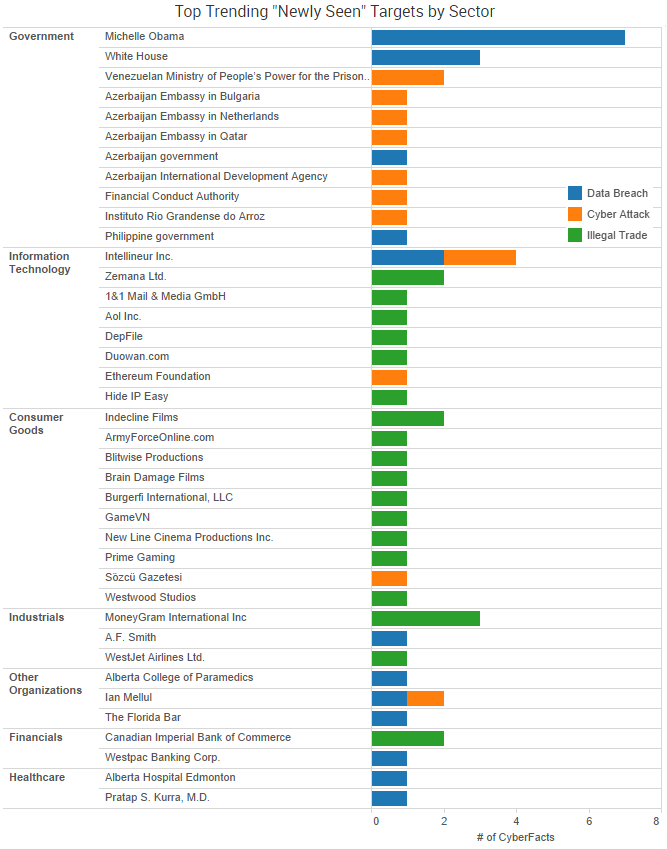
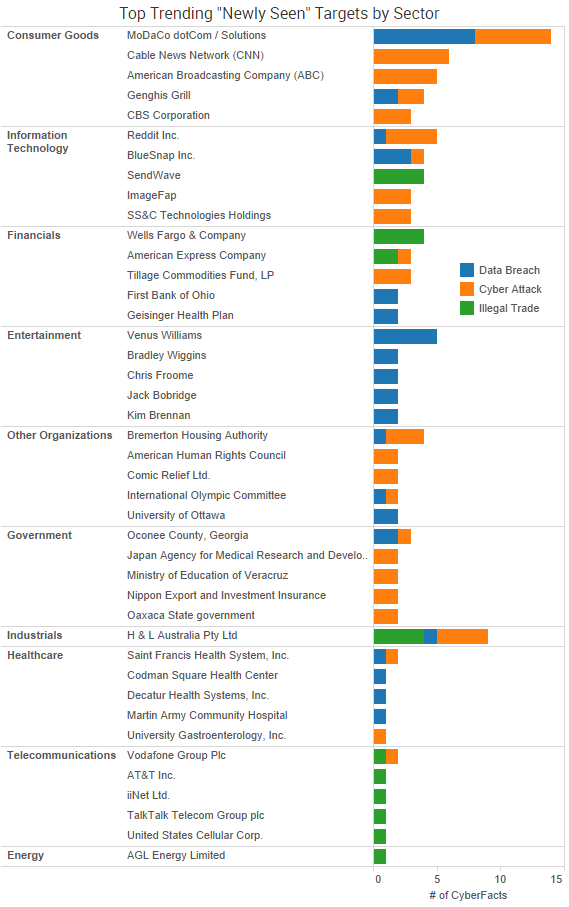
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart above.
Cyber Risk Trends From the Past Week

The financials sector was among the biggest risers in cyber risk this week as its SurfWatch Labs’ cyber risk score rose nearly 5.7 percent compared to the previous week. Much of that was driven by chatter on the Dark Web and data leaks such as the one impacting California investment bank WestPark Capital.
On Sunday, a hacker or group of hackers known as TheDarkOverlord released about 20 files allegedly stolen from WestPark Capital after an unsuccessful ransom attempt against the company. They also claimed other groups were using their name to perform attacks in a Pastebin post.

The “signature” business proposal referenced in the Pastebin post is likely similar to the series of extortion attempts the group made earlier this year against various healthcare organizations. TheDarkOverlord has frequently used the media and leaked samples of stolen data to build up a reputation as a legitimate threat and to put pressure on victim companies in hopes that they will decide to pay the group’s ransom demands.
This is the first instance SurfWatch Labs has observed TheDarkOverlord targeting financial organizations, but – if the group’s Pastebin post is to be believed – the media attention is leading to copycats using both TheDarkOverlord’s name and extortion methods. Similar attacks may occur in the future.
Other trending cybercrime events from the week include:
- State-Sponsored Actors Target Government: Data breaches previously attributed to nation-state actors trying to de-legitimize the outcome of the upcoming U.S. elections have widened. Law enforcement officials now believe about 10 state election databases have had their systems probed or breached, and the FBI is reaching out to some Democratic Party staffers to investigate possible hacking into cell phones. However, despite all the attention on state-sponsored actors, a new SurfWatch Labs report noted that hacktivists tend to make up the bulk of government-related cyber-attacks, such as the Monte Melkonian Cyber Army leaking data claiming to be from Azerbaijani military, police and bank servers this week.
- Employees Continue to Cause Data Breaches: A former Verizon Wireless technician pleaded guilty to using Verizon computer systems to access call records and locations of customers and then sending that information to a private investigator. Congressman Mike Honda is suing Ro Khanna, the man he’s running against in the November 2016 election, over a former intern allegedly stealing thousands of donors’ information from an old Dropbox account years after his access should have been revoked. A former employee of Alberta Hospital Edmonton inappropriately accessed the records of 1,309 patients over an 11+ year period. A former employee of Mastic Beach village impersonated the chief of police and illegally accessed information on 488 Mastic Beach residents. Sensitive Medicare information on Australian citizens was uploaded to the Internet several months ago, potentially putting patients at risk. A software update to the Alberta College of Paramedics’ (ACP) navigation portal led to a security breach.
- Hackers Cause Plenty of Data Breaches Too: A hacker said he downloaded more than 2.2 million email addresses and plaintext passwords from social hangout site i-Dressup and that the entire database of 5.5 million entries could be stolen using an SQL injection attack. The entire Florida Bar Association database appears to have been stolen including email addresses, phone numbers, fax numbers, mailing addresses and more, according to databreaches.net. NZME, a media company in New Zealand, said that details of competition entrants may have been accessed due to a cyber-attack on a third-party cloud server. Software company Jive is asking some users of its task management software Producteev to reset their passwords after an August data breach that exposed some email addresses and passwords.
- Worry Over Terrorism and Hacking: A hacker who helped to publish a “kill list” of 1,300 U.S. military and other government personnel has been sentenced to 20 years in prison. “This case represents the first time we have seen the very real and dangerous national security cyber threat that results from the combination of terrorism and hacking,” said Assistant Attorney General Carlin.




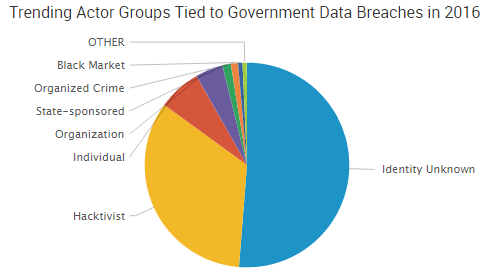
 Hacktivists are often characterized as graffiti artists or vandals that simply deface websites and cause other nuisance-level problems for organizations.
Hacktivists are often characterized as graffiti artists or vandals that simply deface websites and cause other nuisance-level problems for organizations.
 The first two, the capability and intent of threat actors, are mostly external aspects that you have no control over, but the third pillar, the opportunity for actors to exploit your organization, is something that can be controlled, evaluated and improved upon.
The first two, the capability and intent of threat actors, are mostly external aspects that you have no control over, but the third pillar, the opportunity for actors to exploit your organization, is something that can be controlled, evaluated and improved upon.