The past week has been full of various data breach announcements that have flown mostly under the radar. One exception is the breach at the World Anti-Doping Agency (WADA). New batches of information on Olympic athletes continue to be leaked, and the Entertainment sector’s cyber risk score has steadily risen to reflect those leaks. Another exception, and one of the biggest data breach stories of the year, is Thursday’s announcement from Yahoo that 500 million users had their information stolen in late 2014 by alleged state-sponsored hackers.
The theft includes names, email addresses, phone numbers, dates of birth, hashed passwords and, in some cases, encrypted or unencrypted security questions and answers.
The New York Times described the Yahoo breach as “the biggest known intrusion of one company’s computer network.” U.S. Sen. Richard Blumenthal said that if claims that Yahoo knew about the breach since August are true, taking two months to inform users is “a blatant betrayal of their users’ trust.” Sen. Mark Warner is using the incident to push for the adoption of a uniform data breach notification standard.
The Yahoo breach is just the latest example of years-old breaches that have come to light in recent months and affected tens or, in Yahoo’s case, hundreds of millions of individuals. The already massive list of potentially exposed passwords continues to grow, making good password hygiene more important than ever. But the Yahoo breach highlights another nagging problem: the use of static, knowledge-based authentication questions.
From Yahoo’s announcement:
“We invalidated unencrypted security questions and answers so they cannot be used to access an account. … Change your password and security questions and answers for any other accounts on which you used the same or similar information used for your Yahoo account.”
Except unlike passwords, static-based questions cannot be changed. How do you change your mother’s maiden name, your favorite teacher, or the name of your first pet? Fake answers can be used – and they are more secure – but what percentage of people will actually take that extra step?
A February survey from password manager LastPass indicates the majority of people are still reusing passwords. Fifty-nine percent of respondents said they reuse passwords across multiple services and 61% said they are more likely to share work passwords than personal passwords.
Organizations need to be aware of recent credential breaches, inform and train users about the threat, and ensure that password policies and procedures reflect the current level of risk surrounding compromised credentials.
What’s Everyone Talking About? Trending Cybercrime Events

In addition to the highly-publicized data breaches from Yahoo and WADA, many other companies made data breach announcements over the past week.
Some of those apparent breaches are sparse on details – such as the FBI seizing computers at Camden County Courthouse in Missouri or office supplies firm AF Smith taking its Apple website offline after fears of a payment card breach – however, many of this week’s announcements showcased the various ways in which data breach can occur.
Data breaches were caused by:
- Unauthorized access: Codman Square Health Center is notifying patients of a data breach after an unauthorized individual accessed information through the New England Healthcare Exchange Network. Mobile review site MoDaCo said a data breach of 875,000 accounts likely occurred by way of a compromised administrator account. A Florida man has been arrested on charges of hacking into computers operated by the Linux Kernel Organization and the Linux Foundation using compromised credentials. A Kennesaw State University student used a professor’s account to hack into the school’s system to change grades and steal personal information. Police also discovered the usernames and passwords of at least 36 faculty members in a notebook in his home. The Pokemon battle simulator Pokemon Showdown was breached and the hacker was able to steal a database dump by compromising administrator’s credentials via social engineering and then using a privilege escalation vulnerability.
- Improper court filings: WakeMed Health and Hospitals has been ordered by a federal judge to notify thousands of patients that their personal and medical information was disclosed in court filings over a six-year period. Most of WakeMed’s bankruptcy claims were filed by now-retired employee Valeria Soles. In court testimony, Soles said she had no training and no supervision with regard to filing claims and that no one else in her department knew how to file bankruptcy claims.
- Missing devices: The University of Ottawa is investigating the disappearance of an external hard drive containing the personal information of approximately 900 students. According to CBC News, the hard drive was used to back up personal information on students with physical or learning disabilities or mental health issues that applied for special academic accommodations.
- Employee error: The recent leak of NSA hacking tools by a group known as Shadow Brokers is suspected to have originated with an employee or contractor who made the mistake three years ago. The theory is that tools were left on a remote computer during an operation and that Russian hackers eventually found them.
- Third parties: A data breach at the payroll service used by Oconee County, South Carolina, led to 230 county employees not receiving their scheduled direct deposits. The investigation is ongoing and the source of the breach is currently unknown.
- Cybercriminal hackers: Hackers claim to have stolen a database from Australian point-of-sale vendor H&L Australia, and the alleged 14.1 gigabytes of data along with an active backdoor to the company’s network was apparently offered for sale more than two months ago.
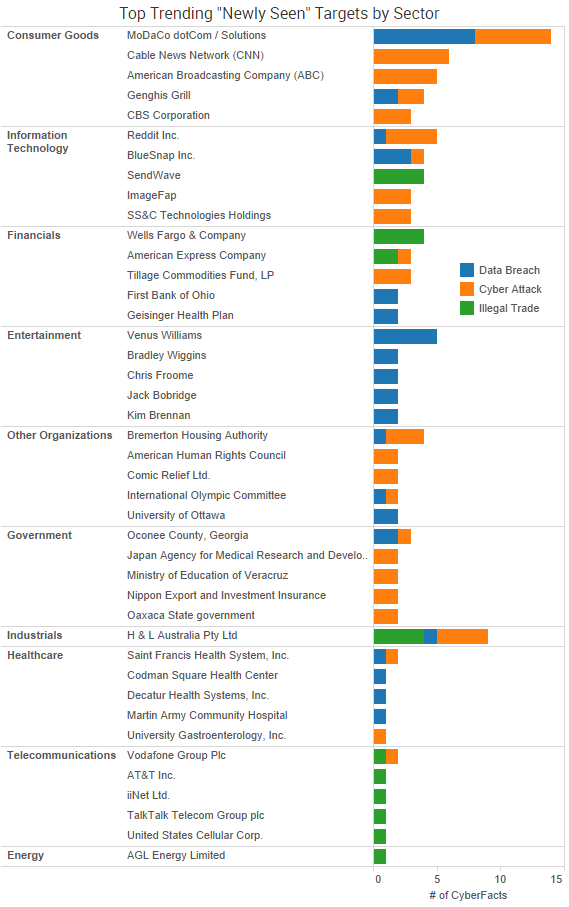
In addition to the data breaches listed above, SurfWatch Labs also collected data on many different companies tied to cyber-attacks and illegal trading over the past week. Some of those newly seen targets are shown in the chart below.



One thought on “Weekly Cyber Risk Roundup: Yahoo One of Many New Data Breaches”