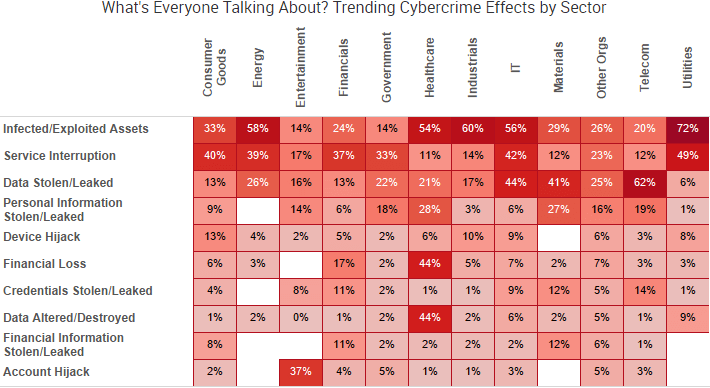
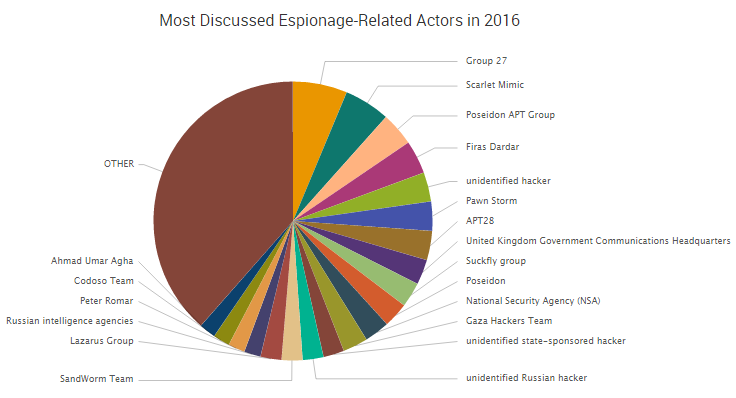
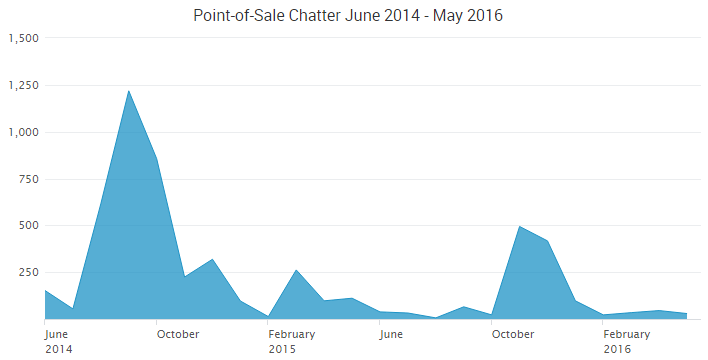
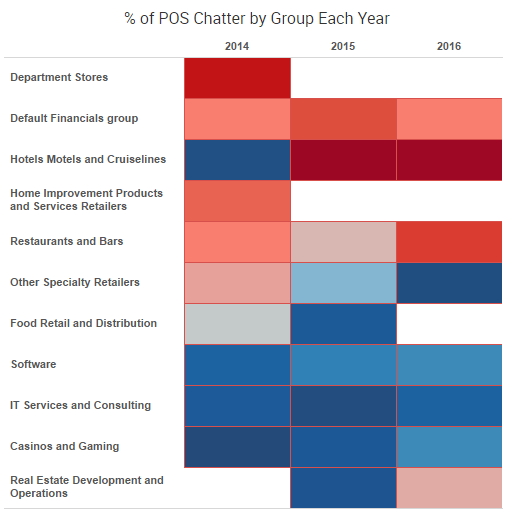
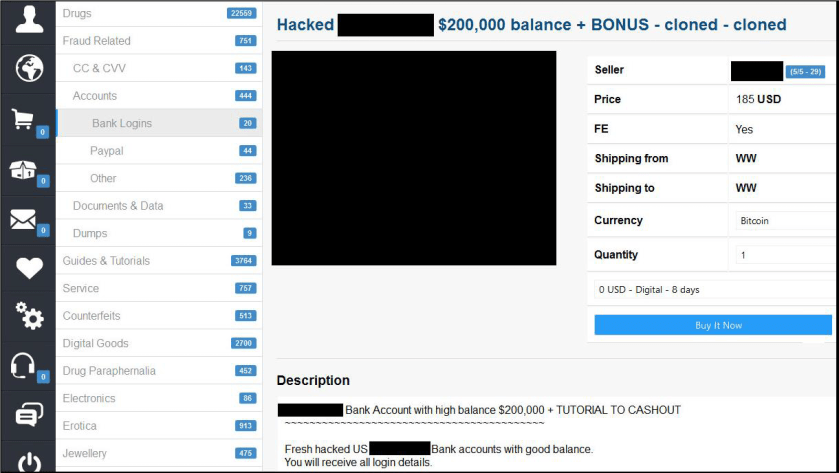
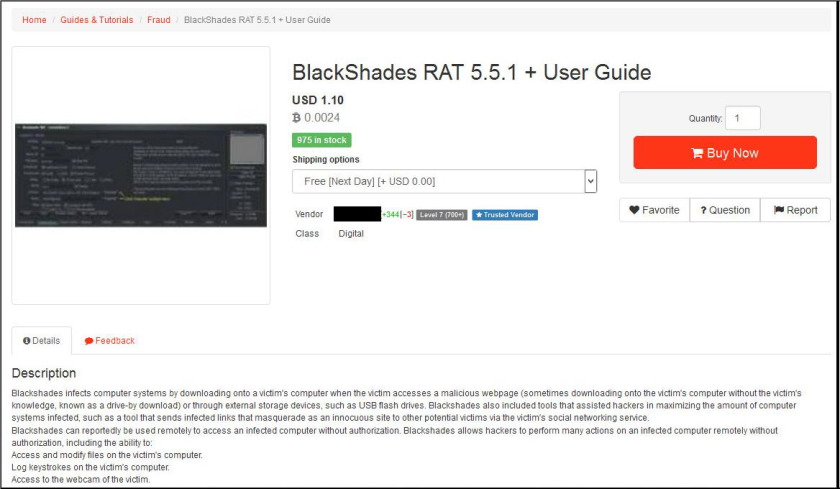
When putting together our recent Mid-Year 2016 Cyber Risk Report, the SurfWatch Labs team began by trying to answer one crucial question: with numerous cybercrime events across thousands of organizations this year, is there a central theme that emerges from all of that data?
In 2014, the data was dominated by a seemingly endless string of point-of-sale breaches. In 2015, the data highlighted a shift towards stolen personal information and more effective ways for cybercriminals to monetize that information. In 2016, the data so far showcases how cybercrime effects often spread beyond the walls of the victim organization.
“The diversity of cyber threats can seem overwhelming when viewed in isolation,” the report noted. “Collectively, they paint a picture of an increasingly connected cybercrime world. Malicious actors excel on taking one piece of information and leveraging it to perform further attacks, gain more information, and widen their reach. The stories so far in 2016 clearly demonstrate this approach, with numerous cyber incidents tied to previous data breaches.”
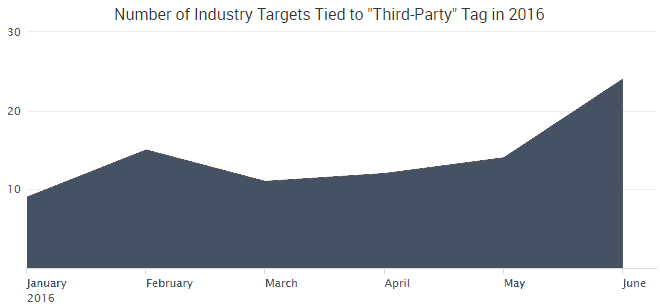
In fact, the number of cybercrime targets tied to “third-party” tags spiked the month before we published our report. As we noted in our previous blog, many of these incidents were connected to previous data breaches and the tactic of “credential stuffing” — where automated tools are used to exploit large batches of known user credentials to discover new accounts to take over.
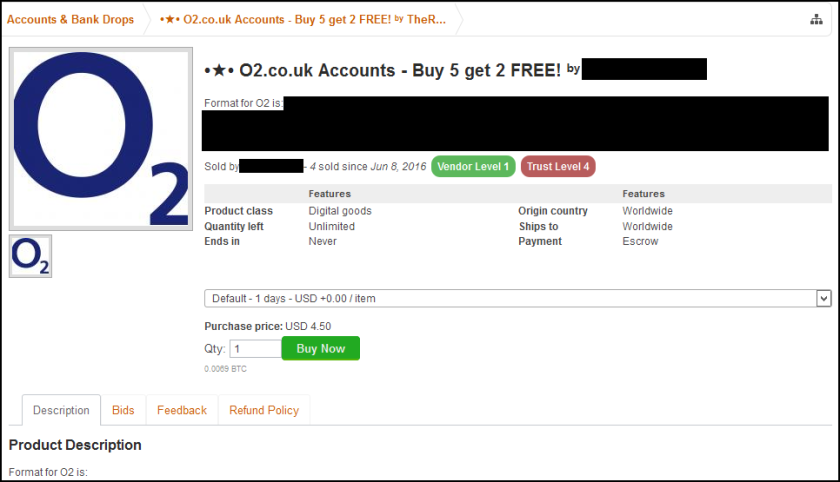
On Tuesday another company was added to the growing list of third-party victims after its customer data was discovered being sold on the dark web. This time it was UK telecommunications company O2. Once again, the incident was attributed to credential stuffing.
“We have not suffered a data breach,” O2 said in a statement. “Credential stuffing is a challenge for businesses and can result in many [companies’] customer data being sold on the dark net. We have reported all the details passed to us about the seller to law enforcement and we continue to help with their investigations.”
As the BBC noted, “The data was almost certainly obtained by using usernames and passwords first stolen from gaming website XSplit three years ago.”
That XSplit breach occurred in November 2013 and affected 2,983,472 accounts, according to Have I Been Pwned? The breach led to names, email addresses, usernames and hashed passwords being compromised.
That batch of three-year old credentials appears to be the cause of the current breach of O2 accounts — as malicious actors leveraged that old information in order to gain even more personal information on the victims. In addition to names, email addresses and passwords, the O2 accounts for sale on the dark web include users’ phone numbers and dates of birth.
This is a similar scenario to what happened at LinkedIn, the most discussed company related to cybercrime so far this year. A 2012 data breach exposed more than 100 million user credentials. Over the past few months we’ve seen a variety of companies force password resets or otherwise report data theft due to those four-year-old credentials still being reused by customers or employees.
In short, old data breaches are leading to a surge of fresh attacks. However, credential reuse isn’t the only concrete example of the ripple effect of cybercrime, although it certainly is a major issue. This year has also seen more traditional incidents of supply chain cybercrime — where one partner or vendor is exploited to compromise another organization. In fact, SurfWatch Labs has collected data on “third-party” cybercrime impacting dozens of different industry groups so far in 2016.
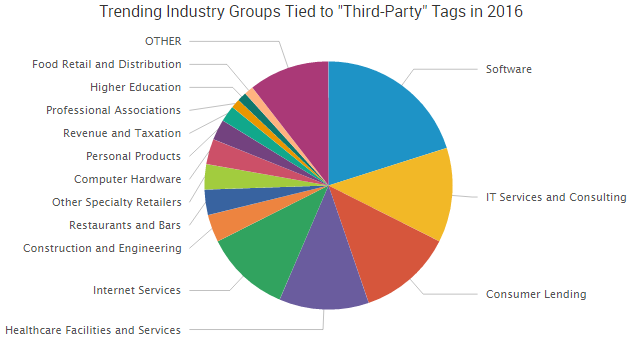
For example, in June we wrote about several healthcare organizations that were victimized by an actor going by the name “TheDarkOverlord,” who was attempting to sell data stolen from healthcare databases on the dark web. This week two of those healthcare organizations publicly confirmed they were victims. As databreaches.net noted, both cited third-parties as a source of the compromise in their repsective statements.
- Midwest Orthopedics Group: “… To date, our investigation has determined that on May 4, 2016, a hacker, or hackers, likely gained access into our secured database system through a third party contractor and may have obtained some personal information of our patients …”
- Athens Orthopedic Clinic: “Athens Orthopedic Clinic recently experienced a data breach due to an external cyber-attack on our electronic medical records using the credentials of a third-party vendor. …”
Various agencies and government groups are taking notice of the trend. The Federal Energy Regulatory Commission recently proposed revisions to the critical infrastructure protection (CIP) Reliability Standards, writing in a press release that “recent malware campaigns targeting supply chain vendors highlight a gap in protection under the [current] CIP.” In addition, the new guidelines from the automotive industry’s ISAC call for more transparent supply chains and increased involvement with third-party researchers. Lastly, Air Force chief information officer Lt. Gen. William Bender noted at a recent forum that the supply chain remains a concern that can span across many different companies.
“It’s not just primary vendors, it’s secondary, tertiary and even further down,” he said.
Having threat intelligence on those various partners, vendors and others who may indirectly affect an organization’s cybersecurity is more important than ever. As SurfWatch Labs’ Mid-Year Risk Report concluded, “The effects of cybercrime continue to ripple outwards – affecting those in the supply chain and beyond.”