In trying to demystify the Dark Web, we’ve talked about the customer-friendly features of markets, the hand-holding nature of cybercrime-as-a-service, and the secure payment options that can protect anonymous buyers.
As we turn our attention to the exploit-centric TheRealDeal Market, it gives us a chance to examine an aspect of the Dark Web that isn’t so rose-colored: the paranoia that runs deep for many buyers, sellers and market operators.
A Quick Look at TheRealDeal Market
Of the many Dark Web markets, TheRealDeal Market has perhaps the most interesting backstory. While other markets focus on things such as drugs and stolen payment card information, TheRealDeal Market launched in 2015 with a focus on code — from zero-day exploits to known vulnerabilities to source code. This led to stories in high-profile outlets such as Wired, which described TheRealDeal as “a new marketplace [that] hopes to formalize that digital arms trade.”
Shortly after making those headlines, several members were arrested, the site went offline, came back online for a short period, and then disappeared again. Finally, half a year later, it relaunched in December 2015.
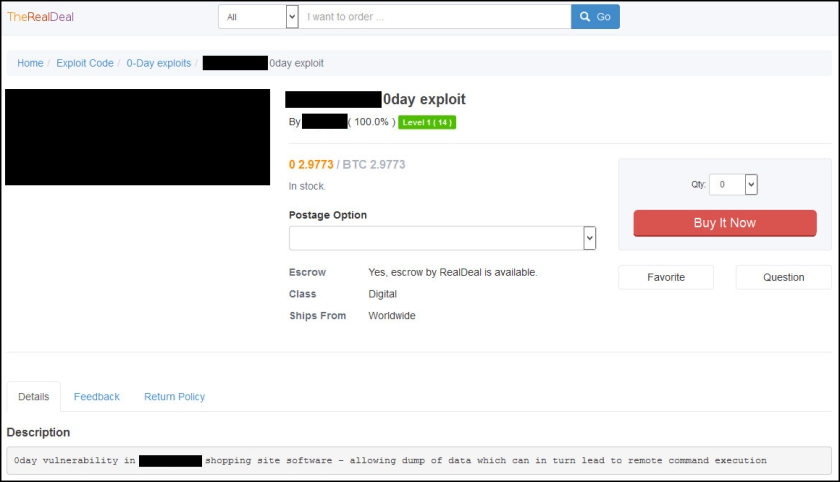
The main reason for the long downtime was “paranoia,” as the site admin put it in an interview. That paranoia was grounded in real world events.
On July 13, 2015, the popular cybercrime forum Hell was shut down after its administrator, Ping, was arrested. A few days later — on July 15, 2015 — the FBI announced the dismantling of a dark web forum known as Darkode, which U.S. Attorney David J. Hickton described as “a cyber hornets’ nest of criminal hackers ” and “one of the gravest threats to the integrity of data on computers in the United States and around the world.” The coordinated law enforcement effort, known as Operation Shrouded Horizon, led to 70 Darkode members and associates across 20 countries being charged, arrested or searched.
As DeepDotWeb reported, those arrests tied up several members of TheRealDeal Market team.
“What I can say is that most of the original team is not with us at the moment,” TheRealDeal admin said in December. “Currently, at least for the time being, the market will be under the management of me (identified in support as admin S.P.), an old vendor that has stuck with us from the beginning, and a couple of trustworthy people from other darknet communities. I can also add that the main reason of the last down time was paranoia, if it turned out to be justifiable or not, I cannot say.”
That paranoia tends to run throughout all dark web markets — paranoia of law enforcement, paranoia of exit scams, paranoia of other users. As one drug vendor from the now-defunct Evolution Market said in a 2014 interview, “In this business it’s always better to be too paranoid than not paranoid enough.”
Feeding into that paranoia is the fact that the main administrator appears to have vanished recently and support has stopped replying to messages, at least according to one popular vendor.
“This [is] very strange by just leaving the market like this without any management or any notice for leaving,” the vendor told Motherboard in an online chat.
Yesterday, TheRealDeal Reddit account said the reason for the absence was an accident.
“Admin not dead, just almost,” the account wrote. “The only guy with the actual keys to the kingdom had a small accident. … More coming soon.”
What’s For Sale on TheRealDeal Market?
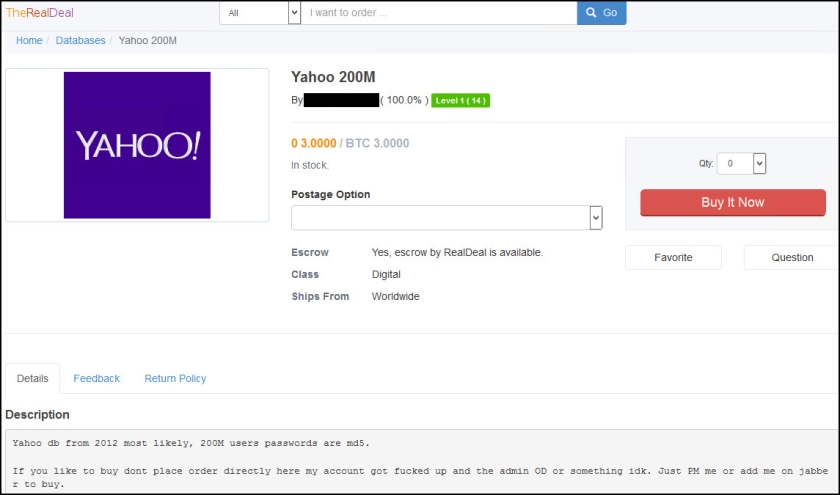
Since its December 2015 relaunch, TheRealDeal Market has once again been making national news. Most recently was a vendor selling a 200 million-strong database of alleged Yahoo user credentials, most likely stolen in 2012, for 3 bitcoin (around $1800). A Yahoo spokesperson said the company is aware of the listing and is investigating whether the data is legitimate.
The same vendor has recently sold massive databases of credentials from LinkedIn and MySpace.
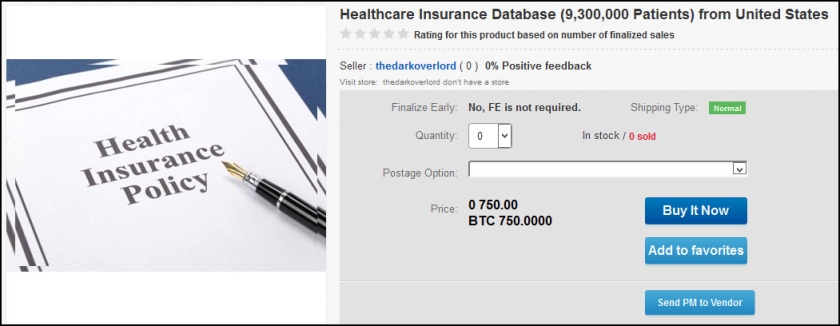
TheRealDeal Market sparked another national story this summer when a different vendor began offering a series of healthcare databases for sale. That actor was able to use the media — along with initial price tags in the hundreds of thousands of dollars — to generate a significant amount of attention around the postings, his or her alias, and TheRealDeal Market. A half dozen databases have since been posted ranging from 23,000 records to 9.3 million records.
One of the more recent postings is from a healthcare organization in Fairview, Illinois.
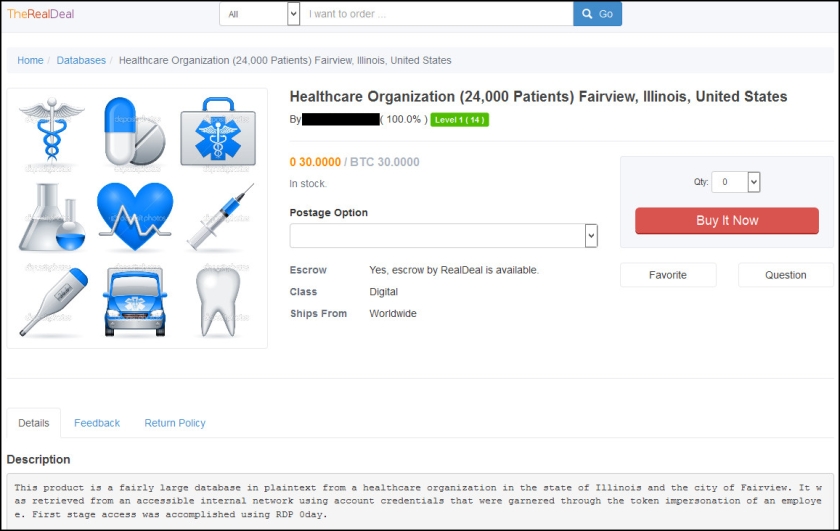
“[The data] was retrieved from an accessible internal network using account credentials that were garnered through the token impersonation of an employee,” the listing reads. “First stage access was accomplished using RDP 0day.”
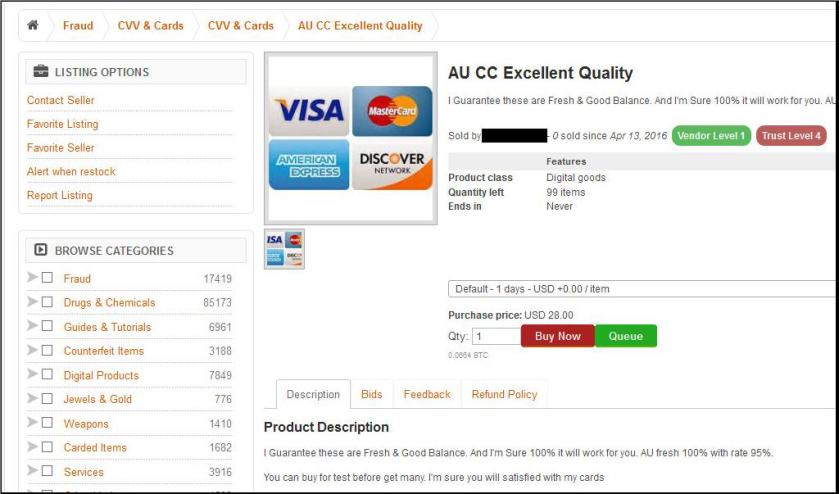
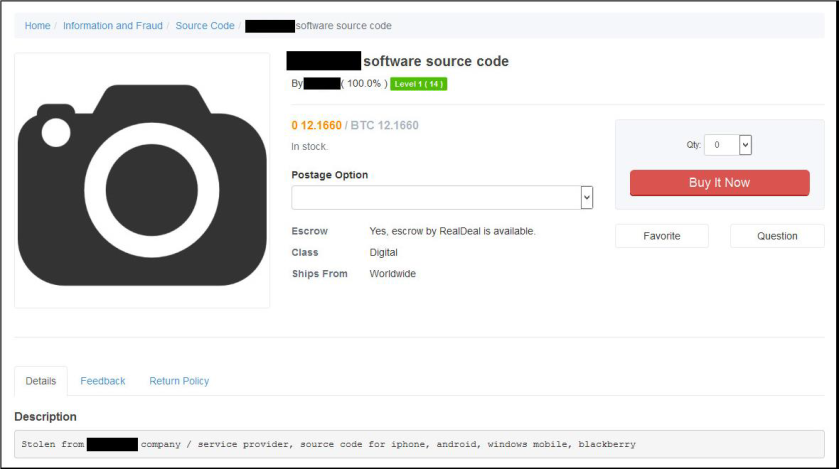
Although various stolen databases have generated most of the media attention around TheRealDeal Market, code-related items are a staple of the market — and one of the reasons it was founded.
“We actually tried selling such information and codes ourselves at some point [on established marketplaces] but it seems that all people want on those markets is credit cards and tutorials on how to make money with credit cards,” an admin said in an interview in April 2015. “The problem is that 90% of these dealers are scammers. People with a lot of experience can always do their best to determine if what they are buying is real based on technical information and demos but some of these ‘vendors’ are very clever and very sneaky. We decided it would be much better if there was a place where people can trade such pieces of information and code combined with a system that will prevent fraud and also provide high anonymity.”
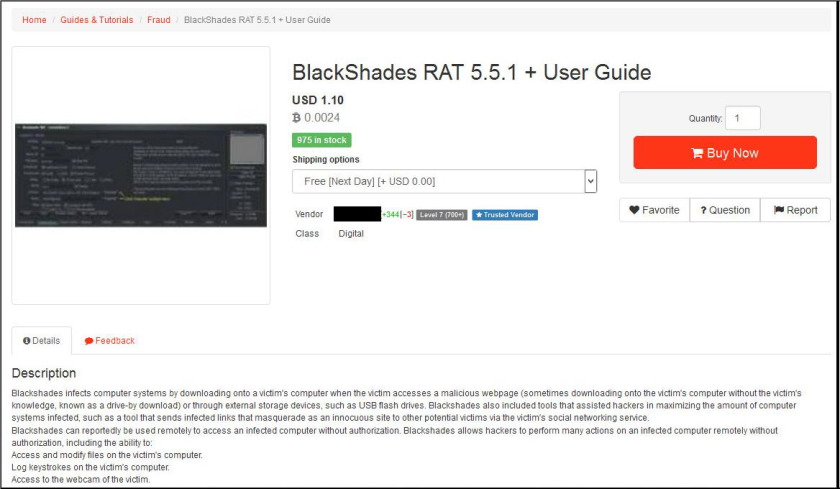
The past month SurfWatch Labs has observed various alleged zero-day exploits for sale on TheRealDeal Market.
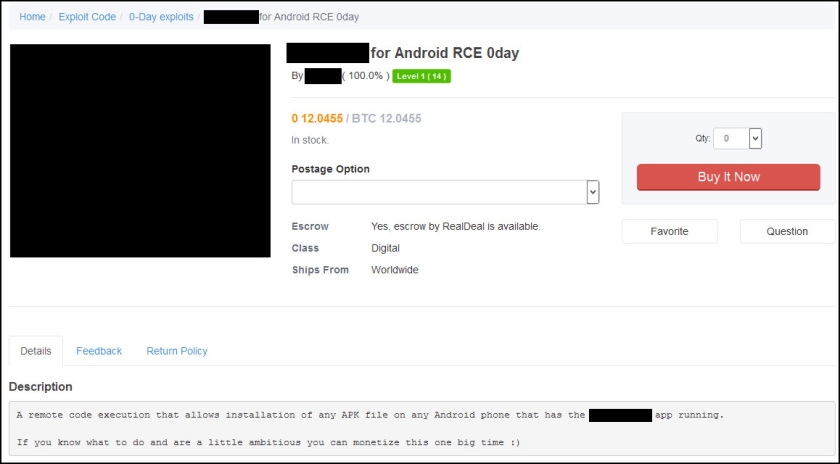
These include a listing claiming “a remote code execution that allows installation of any APK file on any Android phone that has [a certain gambling application] running.”
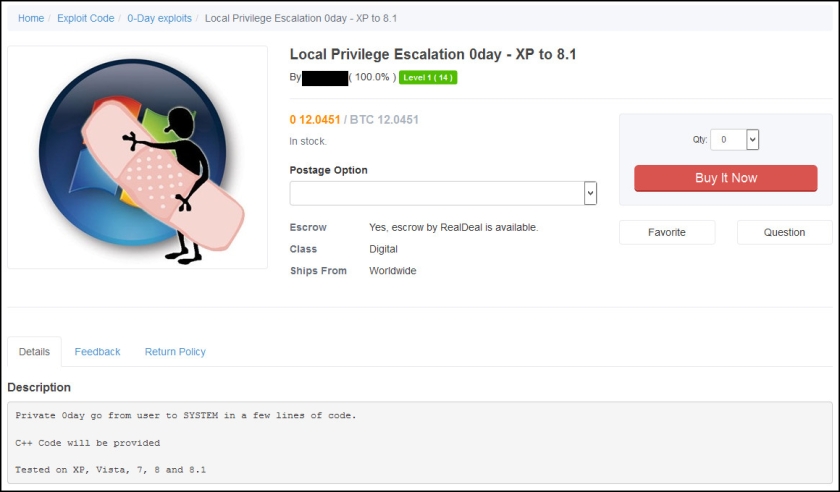
There is also a posting claiming a local privilege escalation zero-day that will “go from user to SYSTEM in a few lines of code.”
Then there is an alleged zero-day in a popular messaging app, which can lead to denial of service.
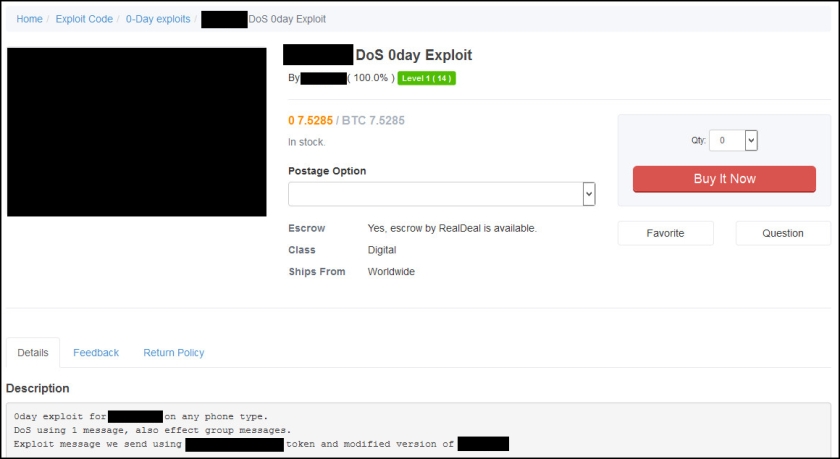
In addition to zero-days and known exploits, there is also a variety of source code and other listings that can be found on the TheRealDeal Market.
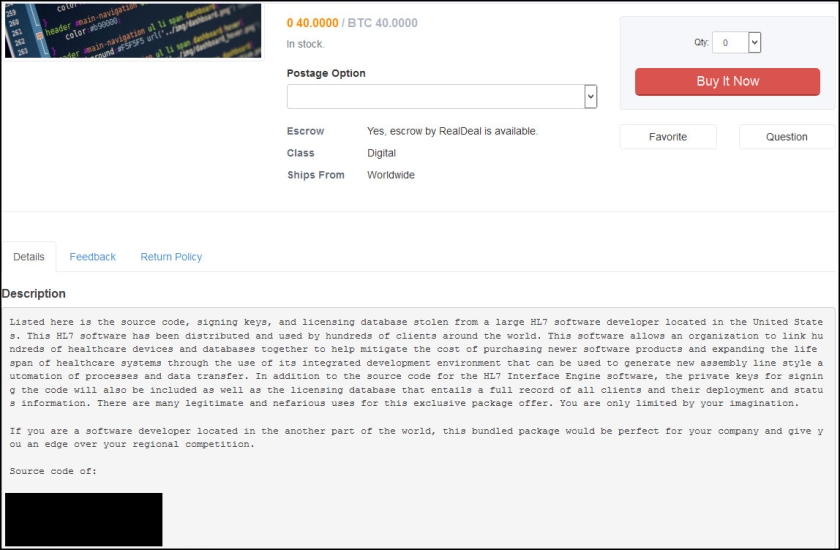
For example, a recent listing claims to be selling information stolen from a large HL7 developer located in the United States.
“In addition to the source code for the HL7 Interface Engine software, the private keys for signing the code will also be included as well as the licensing database that entails a full record of all clients and their status information,” the listing reads. “There are many legitimate and nefarious uses for this exclusive package offer. You are only limited by your imagination.”
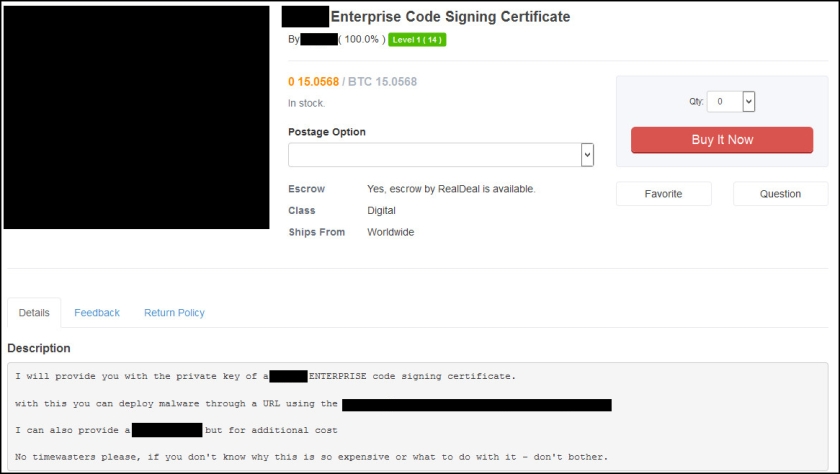
Another listing offers an enterprise code signing certificate.
“No timewasters please, if you don’t know why this is so expensive or what to do with it — don’t bother,” the seller wrote.
These are just a sampling of the many recent listings on TheRealDeal Market.
Although TheRealDeal Market may not be as popular as AlphaBay or other markets that we’ve profiled over recent months — which tend to be dominated by things such as illegal drugs, hacking tutorials, payment card information and stolen credentials — TheRealDeal Market has managed to frequently make headlines for the types of information sold there, connections to other high-profile arrests, and now, the recent disappearance of the current admin.