Hurricane Matthew is over — having been officially downgraded on Sunday — and a clearer picture of the aftermath has begun to emerge. More than 1,000 people were killed by the hurricane, including at least 35 in the United States. Although the storm has moved out to sea, flooding continues here in the U.S., and in Haiti, which was hit hardest by the storm, officials are warning of the possibility of starvation and the spread of Cholera.
With the world’s attention focused on the natural disaster, cybercriminals are once again capitalizing on the devastation with a wave of phishing attacks and other scams. The South Carolina Emergency Management Division is warning Hurricane Matthew victims to be wary of any emails, phone calls and text messages — as well as scams impersonating one of the thousands of disaster workers expected to travel to the state.
US-CERT is also warning of deceptive donation requests that attempt to steal financial information from those who wish to help the victims.

As US-CERT noted, this type of activity commonly occurs after natural disasters. Cybercriminals are always looking for new individuals to target, and national disasters provide a large bucket of concerned people that can potentially be exploited.
Similar warnings were issued following:
- August flooding in Louisiana, which led to concern over fraudulent charity requests that attempt to steal personal and banking information or infect devices with malware.
- The May wildfire in Alberta, Canada, which forced 90,000 people to evacuate and led to individuals impersonating evacuees and using fake websites and Go Fund Me pages to mimic disaster relief programs.
- April floods in Texas, which FEMA warned would likely lead to scammers impersonating building contractors, FEMA employees, and volunteer groups in order to steal sensitive personal information.
“Fraud is an unfortunate reality in post-disaster environments,” said National Insurance Crime Bureau CEO Joe Wehrle in a press release warning of Hurricane Matthew rebuilding scams. “The last thing victims of disaster need is to be victimized again.”
As SurfWatch Labs noted earlier this year, social engineering is one of the most difficult problems related to cybersecurity. It’s also one of the most common tags in SurfWatch Labs’ cybercrime data.

Social engineers often use a few simple and effective tactics in order to dupe their victims. These include having a simple backstory, appearing as though they belong and projecting authority.
One of the reasons cybercriminals capitalize on events such as Hurricane Matthew is that it is very easy for them to use that trifecta of tactics. The natural disaster provides an instant backstory that is immediately understood by a large number of people. People are expecting to see a wide variety of victims and volunteers both seeking and offering help, so its easy for fraudsters to appear as though they belong. Victims are expecting to have to deal with authority figures, making it easy to impersonate government officials, insurance agents or other disaster workers.
Some tips to help stay safe when it comes to social engineering include.
- Never click on links or open attachments unless you know who sent it and what it is. Malicious email attachments and links are among the most common ways for cybercriminals to spread malware and steal information.
- Never reply to emails, text messages, or pop-ups that ask for personal information.
- Cybercriminals may use a combination of fraudulent emails and phone numbers to increase their appearance of authority. Always verify that communication is valid by contacting the organization directly before providing any sensitive information.
- If donating to a charity, make sure it is one you know and trust. The FTC recommends checking out charities via the Better Business Bureau’s (BBB) Wise Giving Alliance, Charity Navigator, Charity Watch or GuideStar.


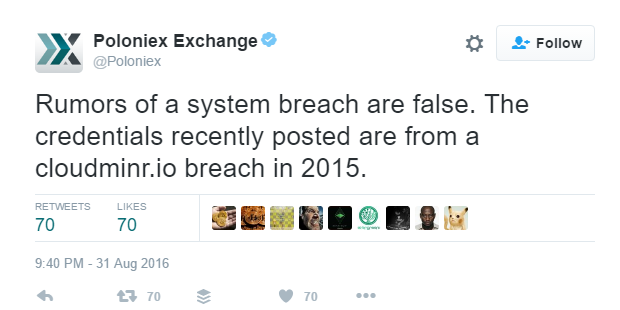

 The botnet includes a variety of compromised home and small office items such as routers, DVRs and security cameras – many of which use default usernames and passwords. The IoT devices are aimed at users often more concerned about convenience than security, and
The botnet includes a variety of compromised home and small office items such as routers, DVRs and security cameras – many of which use default usernames and passwords. The IoT devices are aimed at users often more concerned about convenience than security, and 
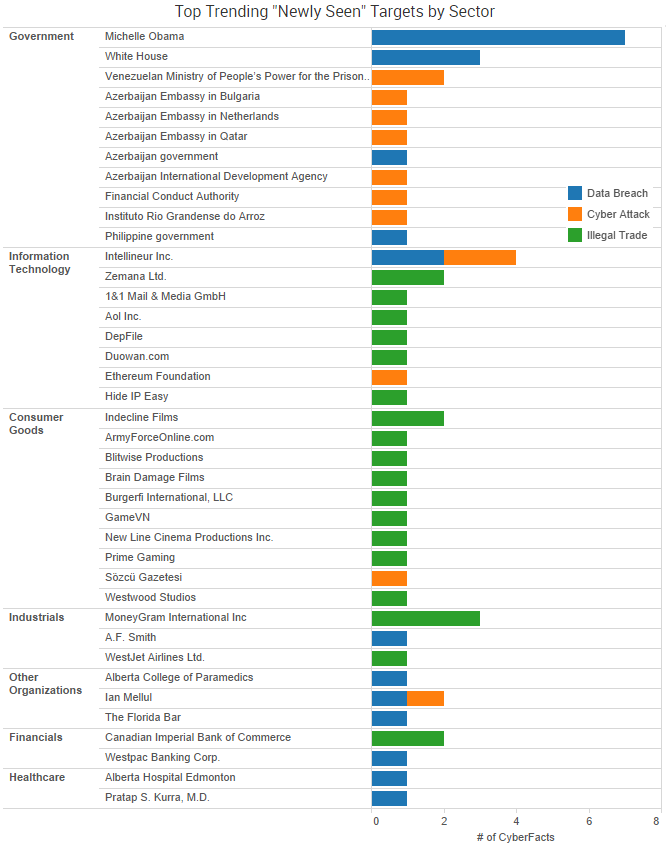
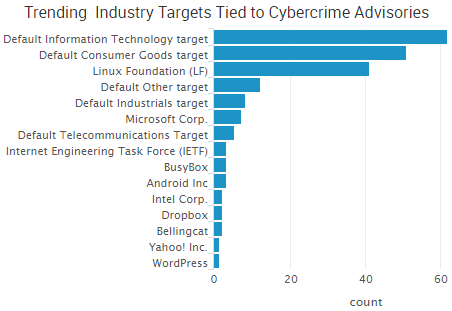 The
The 


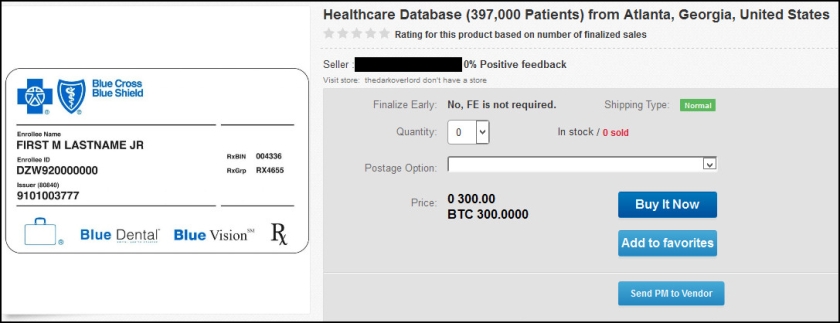
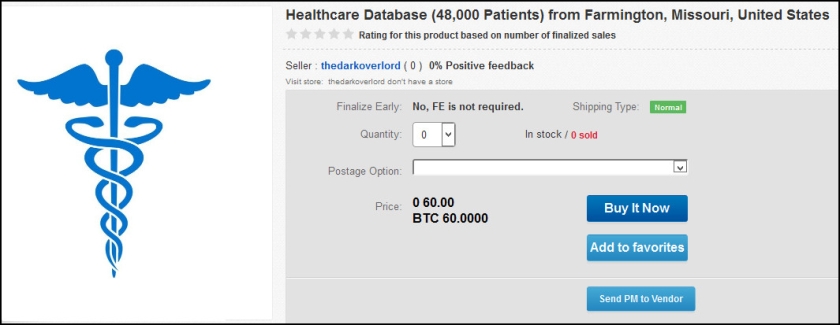
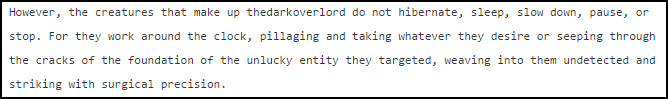
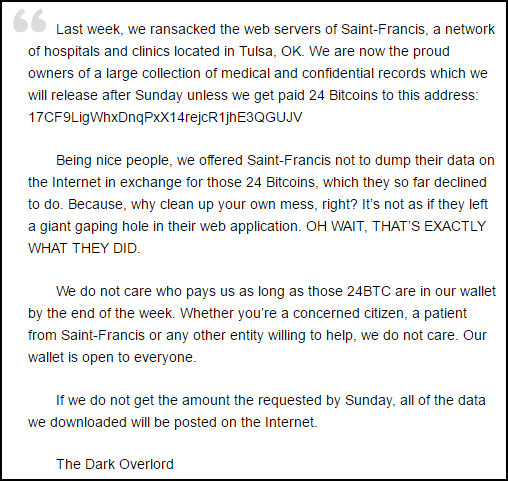

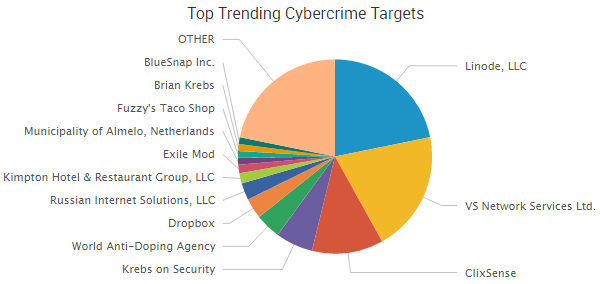
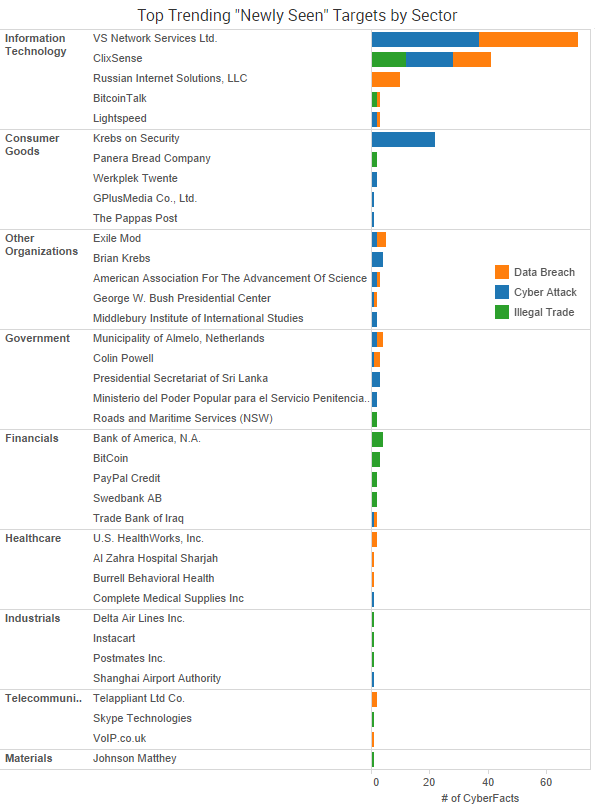
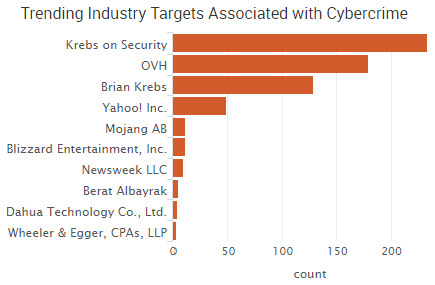
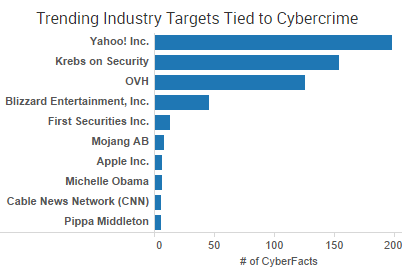 Yahoo was the week’s top trending cybercrime target as the fallout of a breach affecting more than 500 million accounts continues to play out. CEO Marissa Mayer has faced intense scrutiny from lawmakers and others over the handling of the company’s cybersecurity.
Yahoo was the week’s top trending cybercrime target as the fallout of a breach affecting more than 500 million accounts continues to play out. CEO Marissa Mayer has faced intense scrutiny from lawmakers and others over the handling of the company’s cybersecurity. 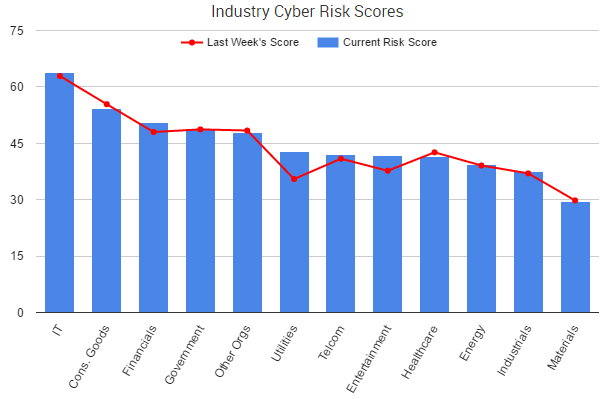
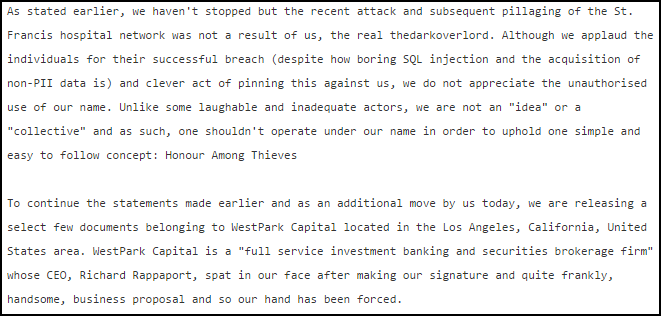




 Hacktivists are often characterized as graffiti artists or vandals that simply deface websites and cause other nuisance-level problems for organizations.
Hacktivists are often characterized as graffiti artists or vandals that simply deface websites and cause other nuisance-level problems for organizations.
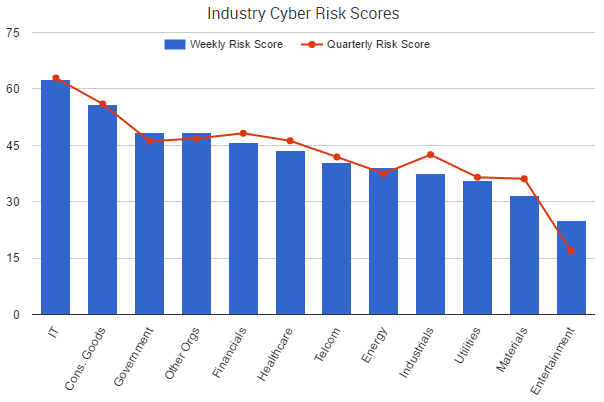
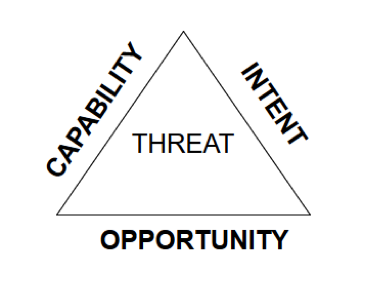 The first two, the capability and intent of threat actors, are mostly external aspects that you have no control over, but the third pillar, the opportunity for actors to exploit your organization, is something that can be controlled, evaluated and improved upon.
The first two, the capability and intent of threat actors, are mostly external aspects that you have no control over, but the third pillar, the opportunity for actors to exploit your organization, is something that can be controlled, evaluated and improved upon.