Third-party cybersecurity issues were once again front and center this past week as America’s JobLink, a web-based system that links jobs seekers with employers, was compromised by a malicious actor, leading to a series of data breach announcements from states that use the system.
 “On February 20, 2017, a hacker created a job seeker account in an America’s JobLink (AJL) system,” the company wrote. “The hacker then exploited a misconfiguration in the application code to gain unauthorized access to certain information of other job seekers.”
“On February 20, 2017, a hacker created a job seeker account in an America’s JobLink (AJL) system,” the company wrote. “The hacker then exploited a misconfiguration in the application code to gain unauthorized access to certain information of other job seekers.”
Millions of individuals may have been affected by the vulnerability, which was introduced in an AJL system update in October 2016. When exploited, it allowed the malicious actor to view the names, Social Security numbers, and dates of birth of job seekers in the AJL systems of up to ten states: Alabama (600,000), Arizona, Arkansas (19,000), Delaware (200,000), Idaho (170,000), Illinois (1.4 million), Kansas, Maine (conflicting media reports on total number affected), Oklahoma (430,000), and Vermont (186,000).
Vermont Gov. Phil Scott said at a Thursday press conference that the state was looking into the contract with ALJ, which has been in effect for about 16 years, and may potentially pursue legal recourse. At the same press conference Vermont Department of Labor Secretary Lindsay Kurrle noted potential AJL issues that may have compounded the breach, such as older Joblink accounts not being deleted.
Third-party cybersecurity issues continue to be one of the most pressing challenges facing organizations, as the numerous breaches in this roundup each week demonstrate. Despite the challenges, the digital footprints of organizations continue to grow: an issue that Adam Meyer, chief security strategist with SurfWatch Labs, and Kristi Horton, senior risk analyst with Gate 15 & Real Estate ISAC, will discuss on a Webinar tomorrow.
Other trending cybercrime events from the week include:
- WikiLeaks’ dump brings legal issues, more CIA documents: Julian Assange criticized companies for not responding to WikiLeaks’ request that they comply with certain conditions in order to receive technical information on the leaked CIA exploits; however, multiple tech companies said the issue is caught up in their legal departments. WikiLeaks also continued to leak more CIA data by publishing documents that “explain the techniques used by CIA to gain ‘persistence’ on Apple Mac devices, including Macs and iPhones and demonstrate their use of EFI/UEFI and firmware malware.” The documents are mostly from the last decade, except for a couple that are dated 2012 and 2013.
- Variety of issues lead to oversharing, data breaches: The UK’s Information Commissioner’s Office is investigating reports that data sharing options in SystmOne may have exposed the medical records of up to 26 million patients. The system’s “enhanced data sharing” option, which doctors turned on so that medical records could be seen by local hospitals, also allowed those records to be accessed by thousands of other workers. Mobile phone company Three is investigating a technical issue that led to some customers who logged into their accounts seeing the personal data of other customers. Med Center Health in Kentucky announced a data breach due to a former employee accessing encrypted patient billing information by falsely implying it was needed for job-related reasons.
- Bots lead to gift card fraud, stock manipulation: Nearly 1,000 customer websites were targeted by a bot named “GiftGhostBot” that automatically checks millions of gift card numbers to determine which card numbers exist and contain balances. Recent pump-and-dump spam messages from the Necurs botnet falsely claimed that InCapta was about to be bought out for $1.37 per share and that people could buy shares for less than 20 cents before the buyout would be announced.
- Malware spread via Ask.com toolbar: For the second time in a one month period, malicious actors were able to compromise the Ask Partner Network (APN), creators of the Ask.com toolbar, in order to spread malware that was signed and distributed as though it were a legitimate Ask software update. The first attack was discovered in November 2016, and in December 2016 researchers discovered that the “sophisticated adversary” was continuing its earlier activity “to deliver targeted attacks using signed updates containing malicious content.”
- Other notable cybercrime events: Hackers going by the name ‘Turkish Crime Family’ claim to have access to a large cache of iCloud and other Apple email accounts and say they will reset accounts and remotely wipe devices on April 7 unless Apple pays a ransom. The McDonald’s India app leaked the personal information of more than 2.2 million users, and data is still allegedly being leaked despite the company’s claims that it fixed the issue. Lane Community College health clinic is notifying approximately 2,500 patients that their personal information may have been compromised due to one of its computers being infected with malware. A gang of hackers-for-hire tried to steal Baidu’s driverless car technology. The FBI believes that North Korea is responsible for the February 2016 theft of $81 million from Bangladesh Bank, and U.S. prosecutors are building potential cases that may both formally accuse North Korea of directing the theft and charge alleged Chinese middlemen
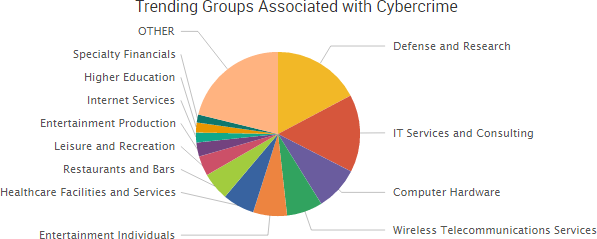
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.

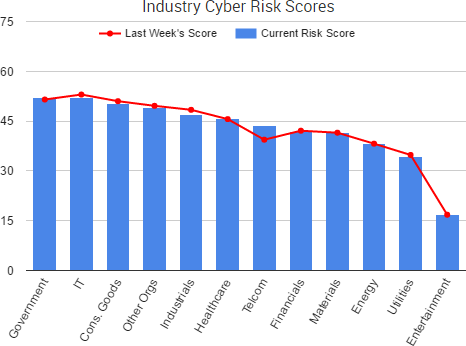
Cyber Risk Trends From the Past Week
 One of the most profitable cybercriminal tactics is business email compromise scams, which has accounted for several billion dollars worth of actual and attempted losses over the past few years.
One of the most profitable cybercriminal tactics is business email compromise scams, which has accounted for several billion dollars worth of actual and attempted losses over the past few years.
A reminder of that ongoing threat surfaced this past week when the Department of Justice announced the arrest of a Lithuanian man on charges that he had successfully duped two U.S.-based companies into wiring a total of over $100 million to bank accounts that he controlled.
The DOJ noted in its press release that the case “should serve as a wake-up call” to even the most sophisticated companies that they may be the target of advanced phishing attempts from malicious actors.
Evaldas Rimasauskas, the arrested Lithuanian man, allegedly registered and incorporated a company in Latvia with the same name as an Asian-based computer hardware manufacturer, and then opened and maintained various bank accounts using that copycat company name. He then is alleged to have sent fraudulent phishing emails to employees of companies that regularly conducted multimillion-dollar transactions with the hardware manufacturer, asking that those companies direct payments for legitimate goods and services to the bank accounts using the copycat name. The indictment also alleges that Rimasauskas submitted forged invoices, contracts, and letters that falsely appeared to have been executed and signed by executives and agents of the victim companies to banks in support of the large volume of funds that were fraudulently transmitted via wire transfer.
As the FBI and others have repeatedly warned, the lure of multi-million dollar payout leads to cybercriminals going to great lengths to successfully social engineer companies. This includes more time spent researching things such as the roles of employees and their language in written communications, as well as company authority figures, policies and procedures, and supply chains. This allows the social engineers to craft a message, or series of messages, that fits within the expected culture and communication patterns of an organization — increasing their chances of a large, fraudulent payday.








 Earlier this month, a patch was issued to address a high-impact vulnerability in Apache Struts Jakarta Multipart parser that allowed attackers to remotely execute malicious code. Shortly after the patch, an exploit appeared on a Chinese-language website,. Researchers then confirmed that attackers were “widely exploiting” the vulnerability. Since then, the issue has continued to affect numerous organizations through data breaches and service downtime.
Earlier this month, a patch was issued to address a high-impact vulnerability in Apache Struts Jakarta Multipart parser that allowed attackers to remotely execute malicious code. Shortly after the patch, an exploit appeared on a Chinese-language website,. Researchers then confirmed that attackers were “widely exploiting” the vulnerability. Since then, the issue has continued to affect numerous organizations through data breaches and service downtime.



 “Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized ‘zero day’ exploits, malware remote control systems and associated documentation,”
“Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized ‘zero day’ exploits, malware remote control systems and associated documentation,” 

 Nearly every week researchers discover new data breaches due to publicly exposed databases that require no authentication, and this past week insecure Rync backups exposed the entire operation of River City Media (RCM), providing a rare glimpse inside what security researcher
Nearly every week researchers discover new data breaches due to publicly exposed databases that require no authentication, and this past week insecure Rync backups exposed the entire operation of River City Media (RCM), providing a rare glimpse inside what security researcher 










 Several companies have issued breach notification letters related to a malware incident at Aptos, Inc., which provides e-commerce solutions for a number of online stores. The breach at Aptos was discovered in November 2016, and notification by the various companies affected was delayed until recently at the request of law enforcement.
Several companies have issued breach notification letters related to a malware incident at Aptos, Inc., which provides e-commerce solutions for a number of online stores. The breach at Aptos was discovered in November 2016, and notification by the various companies affected was delayed until recently at the request of law enforcement.