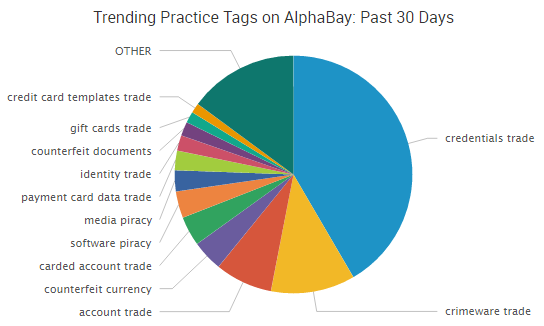
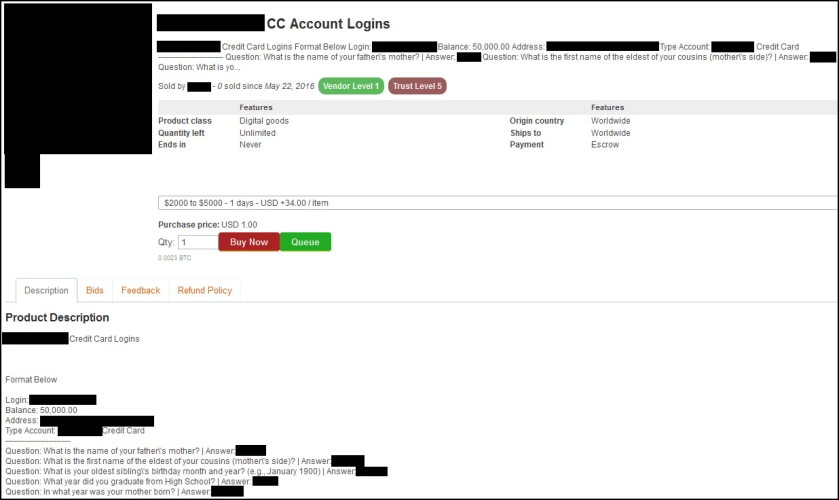
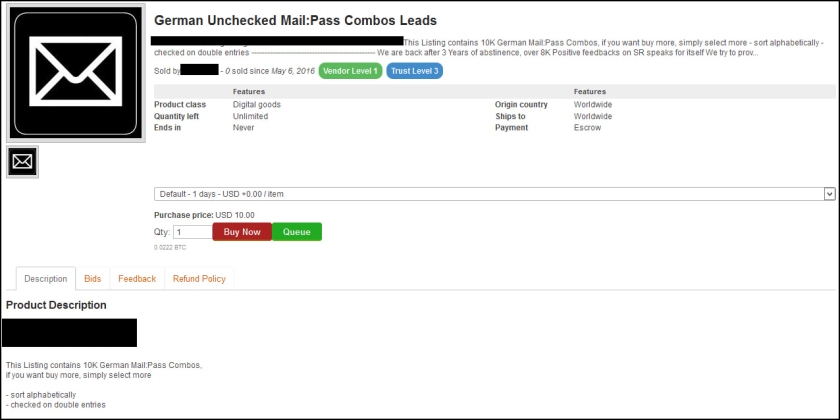
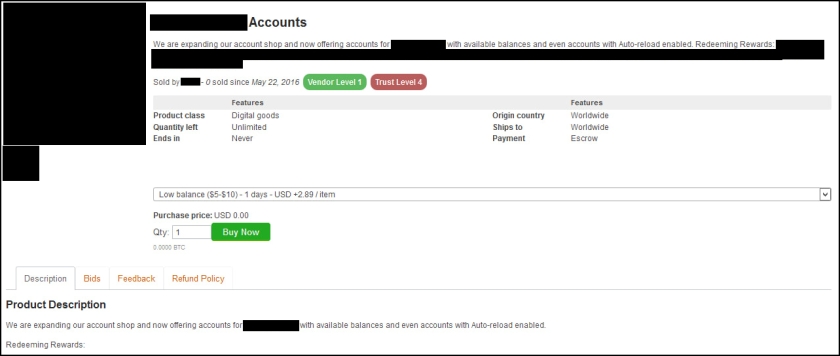
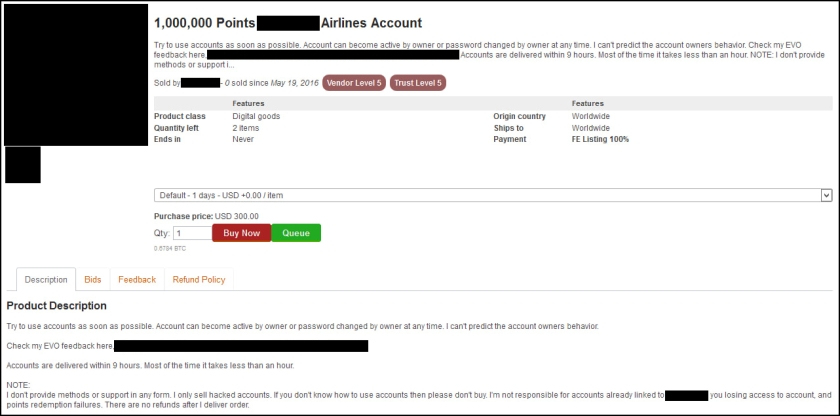
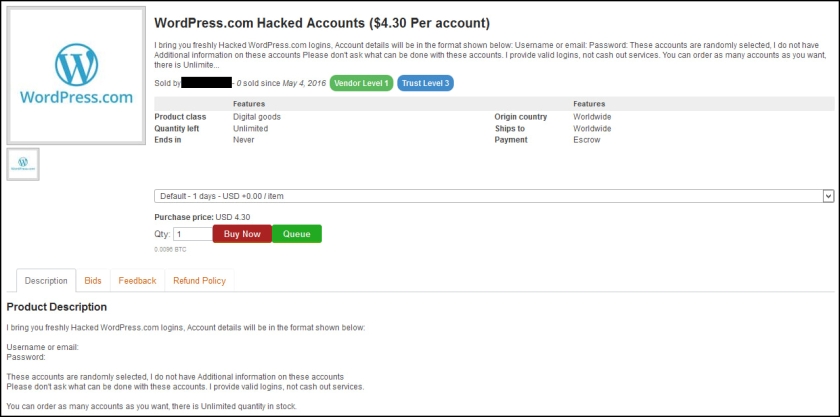
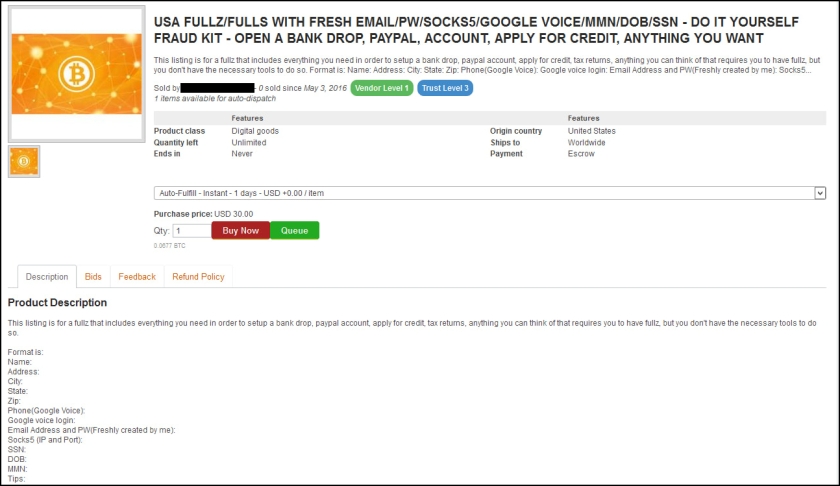
Earlier this month, news outlets across the country reported on the latest mammoth list of stolen credentials — 272 million in total.
“It is one of the biggest stashes of stolen credentials to be uncovered since cyber attacks hit major U.S. banks and retailers two years ago,” Reuters reported.
Turns out, the total number of actual accounts affected is much, much less — a representative for Google put the total number of bogus Google accounts at 98% — however, the story does bring a crucial cybersecurity point back to the forefront: stolen credentials and the collateral damage they cause. Companies are continually finding themselves in the news for data breaches that aren’t really breaches at all.
For example, this year we’ve seen:
- Spotify had a list of user credentials posted to Pastebin, leading to a spate of articles about the company “denying” a data breach. “Spotify has not been hacked and our user records are secure,” the company repeatedly told reporters and bloggers.
- China’s online shopping site Tabao had hackers use a database of previously stolen usernames and passwords to try to access over 20 million active accounts. “Alibaba’s system was never breached,” a spokesperson noted.
- Reddit recently had more than 100 subreddits defaced when a hacker went on a spree of taking over moderator accounts. The Register speculated that it was “possible the hacker is testing breached passwords against the accounts to pop weak or reused credentials.”
In nearly every case, along with the negative — and some may argue unfair — breach-related headlines, a spokesperson steps up to say the same thing: we weren’t breached and the theft is likely due to customers reusing credentials that were stolen elsewhere.
Verizon’s recent Data Breach Investigations Report highlighted the issue as well: 63% of confirmed data breaches involved weak, default or stolen passwords. The report authors noted, “The use of stolen, weak or default credentials in breaches is not new, is not bleeding edge, is not glamorous, but boy howdy it works.”
As we repeatedly see, the reuse of stolen credentials puts many companies in the unfavorable position of having to deny a data breach happened — even as customer accounts are getting taken over.
Easy-to-Use Tools
Automated tools have made it easy for cybercriminals to take these massive lists of stolen credentials — such as the list of over 100 million LinkedIn credentials — and test those credentials against popular websites until they find cases of password reuse.
How often does that work? It varies depending on who you ask, but Shape Security recently wrote about its experience examining one of the popular tools used in these “credential stuffing” attacks.
“We have found that most combo lists have a 1% to 2% success rate, meaning that if an attacker purchases a list from a breach on site A (or a combination of site breaches) and then uses Sentry MBA (or another credential stuffing tool) with that list to attack site B, 1% to 2% of the usernames and passwords from site A will work on site B,” wrote Shape Security chief security scientist Xinran Wang.
One percent may not seem like much, but as Wang points out, if an attacker has a list of one million credentials, they may be able to hijack 10,000 accounts on any popular website using these readily available tools.
In some cases, this amounts to a massive number of fraudulent logins. According to Shape Security researchers, over a one week period last December, attackers made five million log-in attempts at the website of a Fortune 100 company using the Sentry MBA tool.
That’s why some of these recent legitimate breaches have been so widely criticized. The companies in question often are not taking into account the potential collateral damage.
Big Breaches and Collateral Damage
Last month security researcher Troy Hunt reported that over seven million user accounts for the Minecraft community “Lifeboat” were compromised. According to Motherboard, Lifeboat didn’t bother telling its users about the potential issue — and how it may affect other accounts with similar credentials.
“When this happened [in] early January we figured the best thing for our players was to quietly force a password reset without letting the hackers know they had limited time to act,” said a Lifeboat representative, not clarifying to Motherboard when pressed why the company never informed its users. “We have not received any reports of anyone being damaged by this.”
But would they know if someone used those stolen credentials to log into someone’s email or social media or bank account?
Likewise, Brian Krebs recently criticized LinkedIn’s handling of its massive breach of user credentials. In 2012, LinkedIn discovered a data breach that it thought affected 6.5 million users. The company contacted those users to force a password reset. However, last week they discovered the breach actually impacted more than 117 accounts.
“Inexplicably, LinkedIn’s response to the most recent breach is to repeat the mistake it made with original breach, by once again forcing a password reset for only a subset of its users,” Krebs wrote.
“We did at the time what we thought was in the best interest of our member base as a whole, trying to balance security for those with passwords that were compromised while not disrupting the LinkedIn experience for those who didn’t appear impacted,” LinkedIn spokesman Hani Durzy said in an email to Krebs about the 2012 incident.
But what about the more than 100 million potentially compromised credentials that may have been used for years without users even being aware they may have been stolen?
Looking Forward
There will always be a subset of users that reuse credentials, and those users will always be at increased risk of their accounts being hijacked. Unfortunately for companies, their names are often associated with a data breach or a hack even if it is an event driven largely by a combination of other organizations’ breaches and bad password habits.
Implementing additional layers of security such as two-factor authentication can help protect those customers. Or organizations can follow the lead of proactive companies like Amazon, which recently reset some users passwords after finding a list of leaked credentials online.
“While the list was not Amazon-related, we know that many customers reuse their passwords on multiple websites,” Amazon wrote to impacted users. “Since we believe your email addresses and passwords were on the list, we have assigned a temporary password to your Amazon.com account out of an abundance of caution.”
Until organizations get more proactive or force users to implement more layers of security, with so many stolen credentials available to cybercriminals, expect organizations to continue to make negative headlines due to these “non-breach breaches.”