Massive database leaks were once again among the week’s top trending cybercrime targets, including incidents involving U.S. Verizon customers, France’s Orange S.A, and India’s Reliance Jio Infocomm.
The Verizon leak was caused by a third-party engineer at NICE Systems and affected as many as 14 million U.S. customers. The engineer appears to have created a publicly available Amazon Web Services S3 bucket that logged customer call data for unknown purposes. As a result, personal information, account information, and Verizon account PIN codes were potentially exposed. A Verizon spokesperson acknowledged the breach, but said only 6 million customers had their data exposed by the incident.
In addition, French-language text files stored in the server show internal data from Paris-based telecommunications corporation Orange S.A., also a NICE Systems partner. However, the researchers said it “appears this internal Orange data is less sensitive.”
In addition, Reliance Jio Infocomm, an Indian telecom company with over 100 million subscribers, is investigating a potential incident after local news sites reported that names, telephone numbers and email addresses of Jio users were visible on a site called “Magicapk.” However, an initial investigation showed that Jio’s apps and websites were secure, ET Telecom reported. Last week the police brought in a suspect who was in possession of partial details of Jio subscribers, including their names, email IDs, alternate mobile phone numbers, and the dates of activation of SIM cards. That data may have been taken from a Jio retailer, since they have access to that type of subscriber data, the deputy commissioner of police for Navi Mumbai said.

Other trending cybercrime events from the week include:
- More payment card breaches: A breach of Avanti Markets internal networks allowed malicious actors to push malware to self-checkout devices used in corporate break rooms, and as a result payment card information may have been compromised. Avanti said that it believes the malware was only active between July 2 and July 4 of this year. B&B Theatres, which operates 50 locations across seven states, discovered a point-of-sale breach that appears to date back two years. A recent alert estimated the window of exposure of the breach to be between April 2015 and April 2017. Real Estate Business Services (REBS) notified 1,033 California Association of Realtors members that their personal and payment card information may have been stolen when the online store they use was compromised with malware. The infection occurred between March 13 and May 15.
- Medical information exposed: The County Commissioners Association of Pennsylvania (CAAP) said that the details of approximately 1,800 child welfare cases were exposed online by third-party vendor Avanco International. University of Iowa Health Care is notifying 5,292 patients that a limited set of their protected health information was “inadvertently saved in unencrypted files that were posted online through an application development site” and exposed for nearly two years. A former employee of the St. Charles Health System is accused of the unauthorized access and viewing of thousands of patient records.
- More ransomware infections: Community Care of St. Catharines and Thorold in Ontario had its systems infected by NW4 ransomware, which demanded a $3,000 ransom payment. A Community Care spokesperson said that it backs up its data regularly so there was no need to pay the extortion. However, it still took nearly a week for Community Care to restore full access to its computers, and some data that was not captured in the most recent backup was lost. The dental office of Dr. Douglas Boucher, DDS, and Dr. Andrea Yaley, DDS, is notifying patients of a ransomware attack that may have compromised their patient information. The office said that its computer systems were believed to have been hacked around May 19, 2017, and on June 2 it received a ransomware notice. Records were restored from a backup; however, the office said the hacker did access its email system and may have accessed its patient dental health records.
- Other notable incidents: A hacker going by the name Dhostpwned was able to use a PHP shell to compromise the dark web hosting provider Deep Hosting and said he obtained “the majority” of files and SQL databases on the server. An employee at the Australian Tax Office (ATO) published an ATO guide on how to hack mobile phones that included instructions on how to bypass passwords and obtain data even if the phone battery is depleted and it does not have a sim card. A Russian-born cybercriminal living in Los Angeles was sentenced to 110 months in prison for running a sophisticated scheme to steal and traffic sensitive personal and financial information in the online criminal underground.
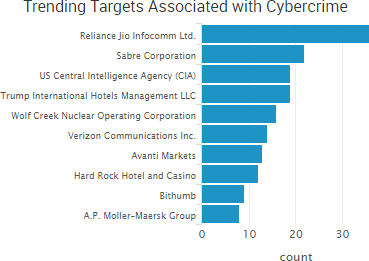
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.

Cyber Risk Trends From the Past Week
 The dark web marketplace AlphaBay has been taken down in a law enforcement raid and one of the alleged leaders of the site has been found dead in his Thai prison cell in an apparent suicide.
The dark web marketplace AlphaBay has been taken down in a law enforcement raid and one of the alleged leaders of the site has been found dead in his Thai prison cell in an apparent suicide.
(See “AlphaBay and Hansa Brought Down by Basic Mistakes, Indictment Reveals” for more information.)
As SurfWatch Labs has noted in the past, AlphaBay was by far the largest and most popular dark web marketplace before it suddenly went dark earlier this month, leading concerned users to speculate if its owners had either been arrested or performed an exit scam. It is not uncommon for dark web markets to disappear without notice. However, AlphaBay had built up a reputation for reliability and become the undisputed king of the dark web marketplaces over the past two years.
Alexandre Cazes, the man who committed suicide in his jail cell, is alleged to be the operator of AlphaBay known as “Alpha02.” U.S. authorities issued a warrant for Cazes arrest on June 30, and he was arrested in Bangkok on July 5, the Bangkok Post reported, the same day the dark web market suddenly went offline. Arrangements were being made for his return to the United States to face charges when Cazes reportedly used a towel to hang himself.
Wired reported that conservative estimates put AlphaBay’s daily transactions between $600,000 and $800,000 a day. With the site suddenly gone, a significant percentage of the cybercriminal ecosystem is now in search of a new home. That influx of traffic forced the dark web market Hansa to close its doors to new businesses due to “technical issues.” Users of Dream Market also reported issues accessing the site following AlphaBay’s takedown.
The next few months will certainly be an interesting time on the dark web as those users look for a new place to buy, sell, and trade their goods and services — and as the story and fallout around the takedown begin to take shape.

