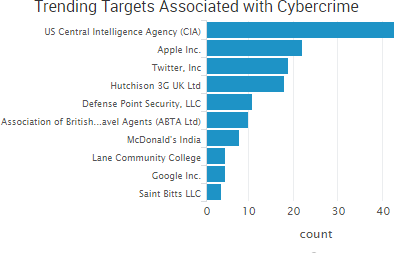
Point-of-sale breaches were once again among the week’s top trending cybercrime targets, as InterContinental Hotels Group (IHG) announced that its previously disclosed POS breach had expanded from the dozen properties reported in February to at least 1,175 properties. Affected hotels include popular brands such as Holiday Inn, Holiday Inn Express, InterContinental, Kimpton Hotels, Crowne Plaza, and more.
 According to the company’s press release, the investigation discovered “malware designed to access payment card data from cards used onsite at front desks for certain IHG-branded franchise hotel locations between September 29, 2016 and December 29, 2016.” The release doesn’t directly state the number of properties affected, instead it directs viewers to a cumbersome breach lookup tool that divides the nearly 1,200-strong list of affected properties into countries, states, and even hundreds of individual cities.
According to the company’s press release, the investigation discovered “malware designed to access payment card data from cards used onsite at front desks for certain IHG-branded franchise hotel locations between September 29, 2016 and December 29, 2016.” The release doesn’t directly state the number of properties affected, instead it directs viewers to a cumbersome breach lookup tool that divides the nearly 1,200-strong list of affected properties into countries, states, and even hundreds of individual cities.
The release also states that hotels that upgraded their technology were not affected by the breach: “Before this incident began, many IHG-branded franchise hotel locations had implemented IHG’s Secure Payment Solution (SPS), a point-to-point encryption payment acceptance solution. Properties that had implemented SPS before September 29, 2016 were not affected. Many more properties implemented SPS after September 29, 2016, and the implementation of SPS ended the ability of the malware to find payment card data and, therefore, cards used at these locations after SPS implementation were not affected.”
That’s a sliver of good news; however, nearly 1,200 hotels were impacted and that list may grow in the future as “a small percentage of IHG-branded franchise properties did not participate in the investigation.” The lookup tool will be updated as new properties are added. Unfortunately, for heavy travelers that means returning to the clumsy tool periodically and checking every city they stayed in over the affected period for new breach updates.
Other trending cybercrime events from the week include:
- More breaches due to poor practices and faulty updates: The accidental posting of a file containing the embedded personal information of 5,600 individuals to Rhode Island’s Transparency Portal and General Assembly website is the third recent data breach tied to UHIP, a new system for state benefits. The cybersecurity company Tanium is apologizing for exposing information related to El Camino Hospital in California in hundreds of presentations for potential customers from early 2012 through mid-2015 as well as several now-deleted YouTube videos. As many as 2,000 individuals in the UK may have had their personal information visible to other customers on the RingGo parking app due to a faulty software update.
- Former employees continue to cause damage: A former employee of engineering firm Allen & Hoshall admitted to accessing the company’s servers repeatedly over a two-year period as well as accessing the email account of a former colleague hundreds of times in order to download and view data from his former employer. A man was arrested for attempting to steal proprietary computer code for a trading platform developed by his employer, an unnamed financial services firm with an office in New York. The online retailer Black Swallow has agreed to pay $60,000 to Showpo to settle a dispute alleging that a former Showpo graphic designer downloaded the company’s entire customer database and gave it to her new employer.
- Old data breaches come to light: Allrecipes is warning its users that their email addresses and passwords may have been compromised when logging into their accounts prior to June 2013, nearly four years ago. There is not a lot information on what happened, as the notification email said that the company “cannot determine with certainty who did this or how this occurred.” While announcing a series of automated attacks against its InCircle, Neiman Marcus, Bergdorf Goodman, Last Call, CUSP, and Horchow websites, Neiman Marcus also noted that a similar automated attack in December 2015 provided access to full payment card details — not just the last four digits as initially reported.
- Physical theft of sensitive data at hotel: Police seized bags of documents containing the personal information of guests staying at the Seasons Hotel at Sydney’s Darling Harbour, and one woman has been charged in relation to the theft, according to police. The information was likely stolen around March 21 and included dozens of guest registration forms, which feature photocopies of passports, driver’s licences, and other forms of personal identification.
- Other notable cybercrime events: Over 2.4 million email addresses and MD5-hashed passwords were stolen from Fashion Fantasy Game, an online game and social network for fashion lovers, in 2016, and the game’s website appears to contain several existing vulnerabilities that could leak data. Cleveland Metropolitan School District is warning some employees, students, guardians, and affiliates that their information may have been compromised when multiple employees fell for a phishing email that compromised their email account credentials. Security and privacy concerns have been raised after London’s Metropolitan Police apparently gave the addresses of 30,000 gun owners to a marketing agency to help promote the sale of a “firearms protection pack.”
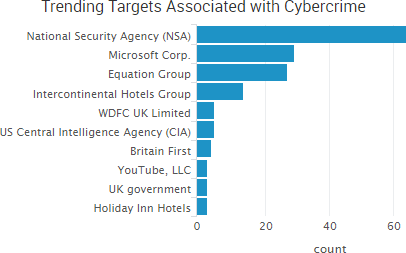
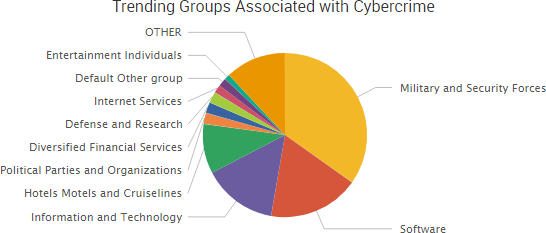
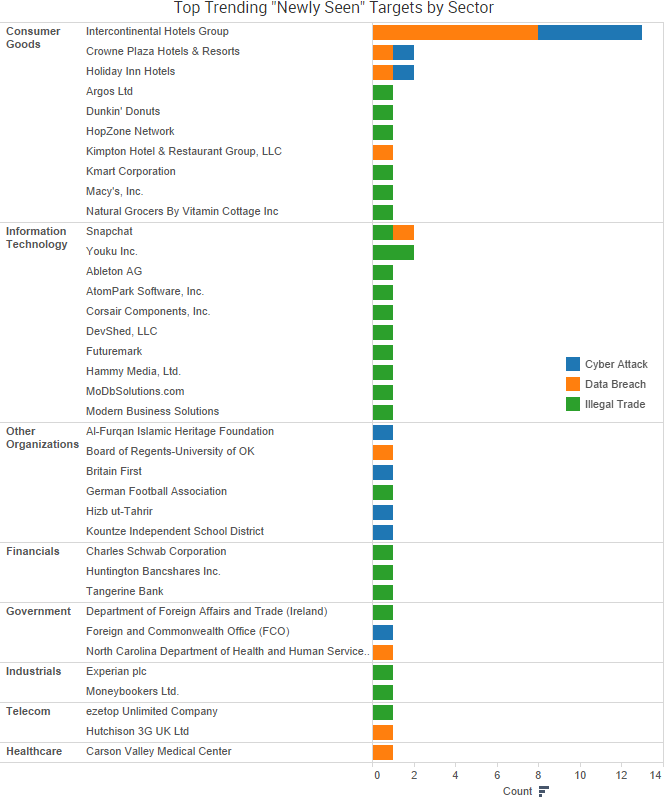
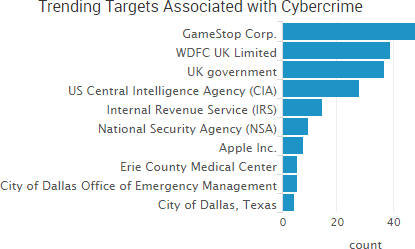
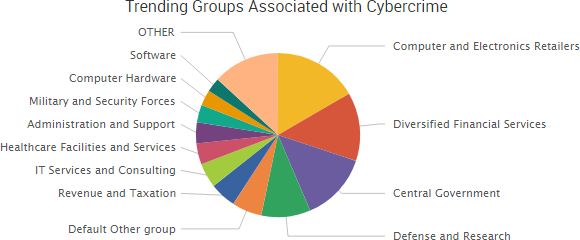
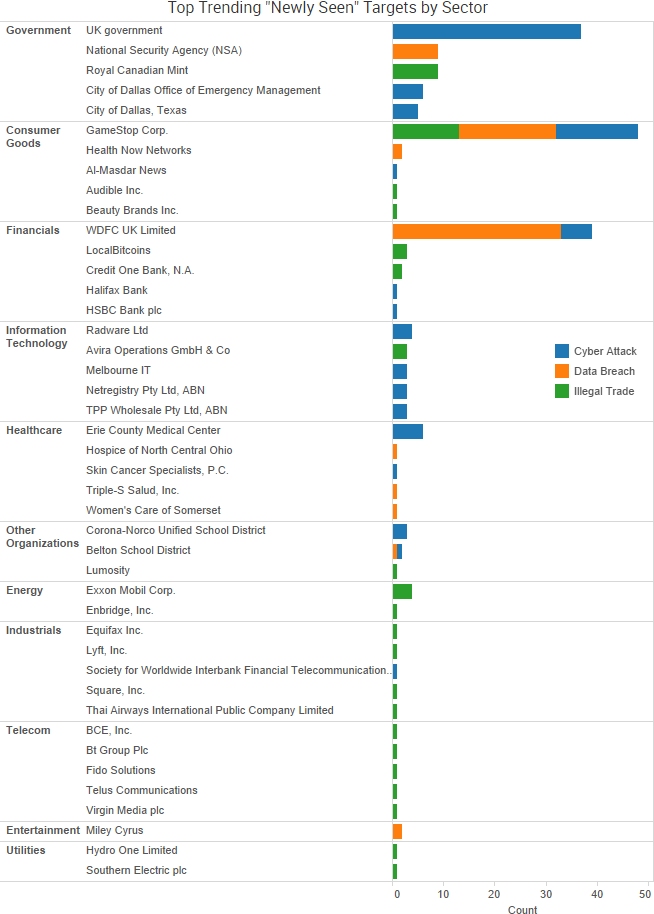
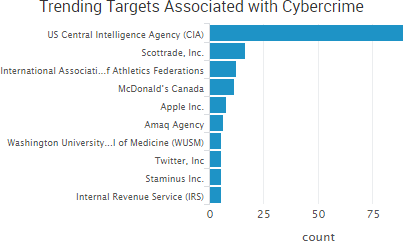
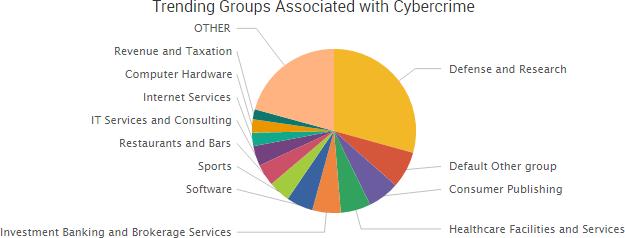
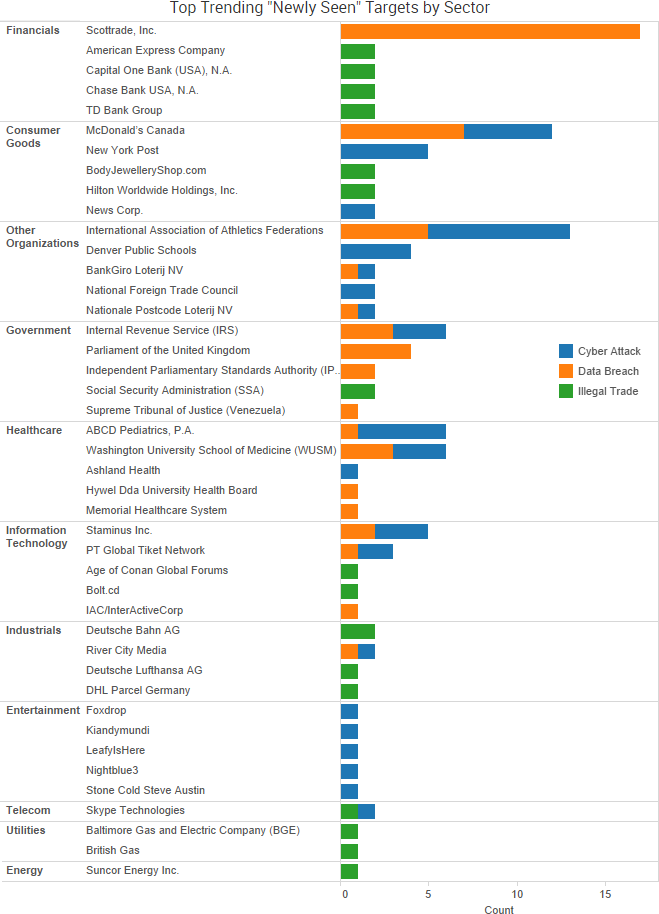
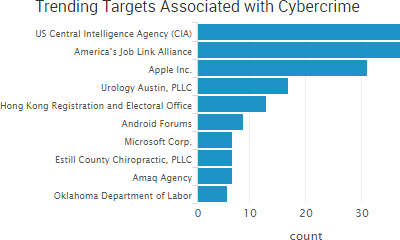
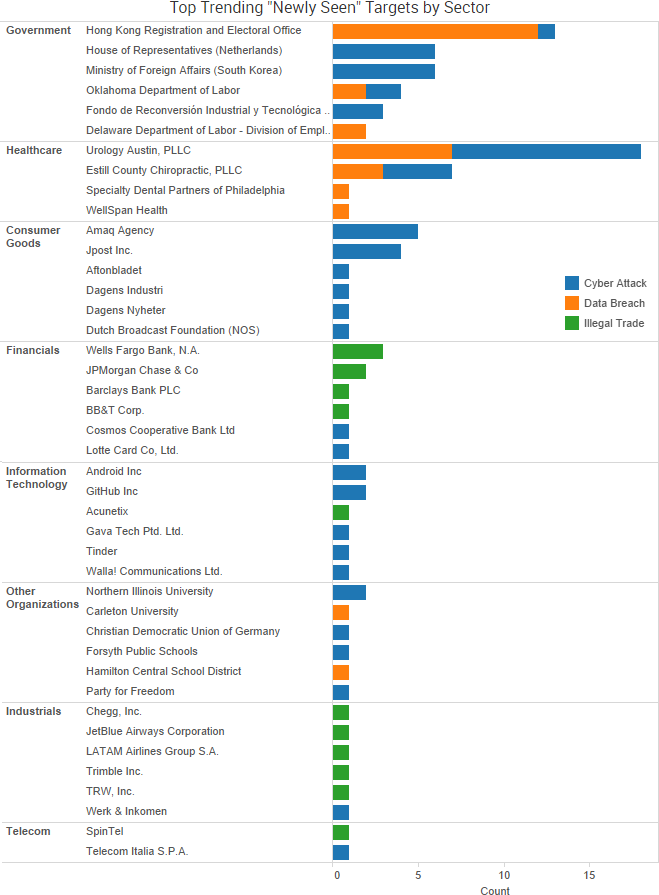
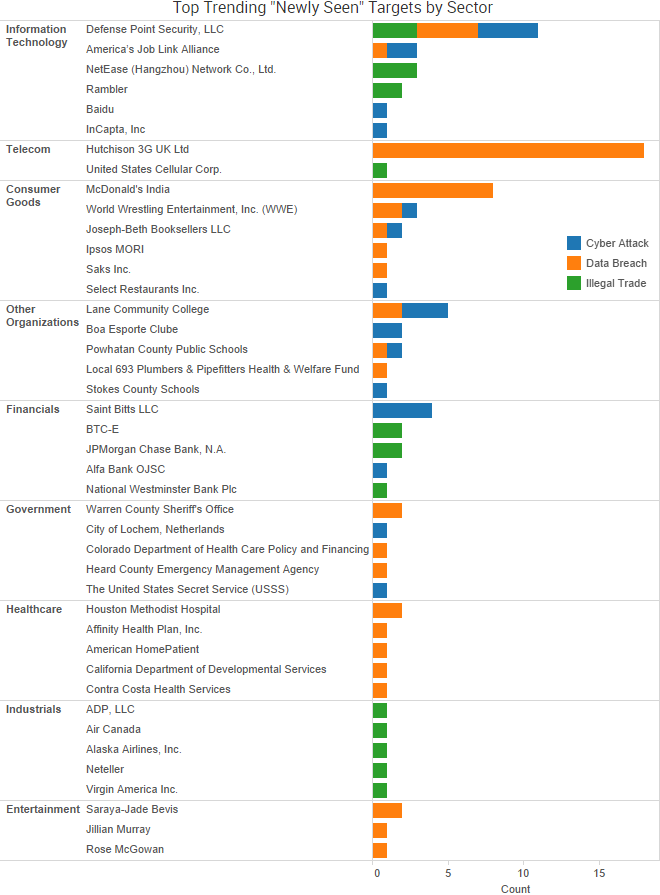
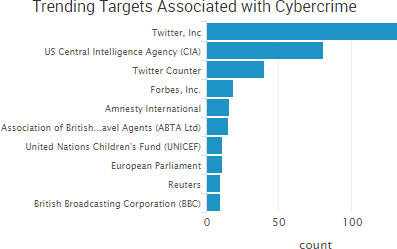
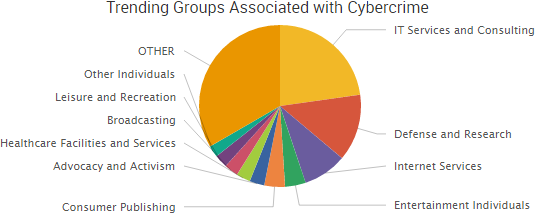
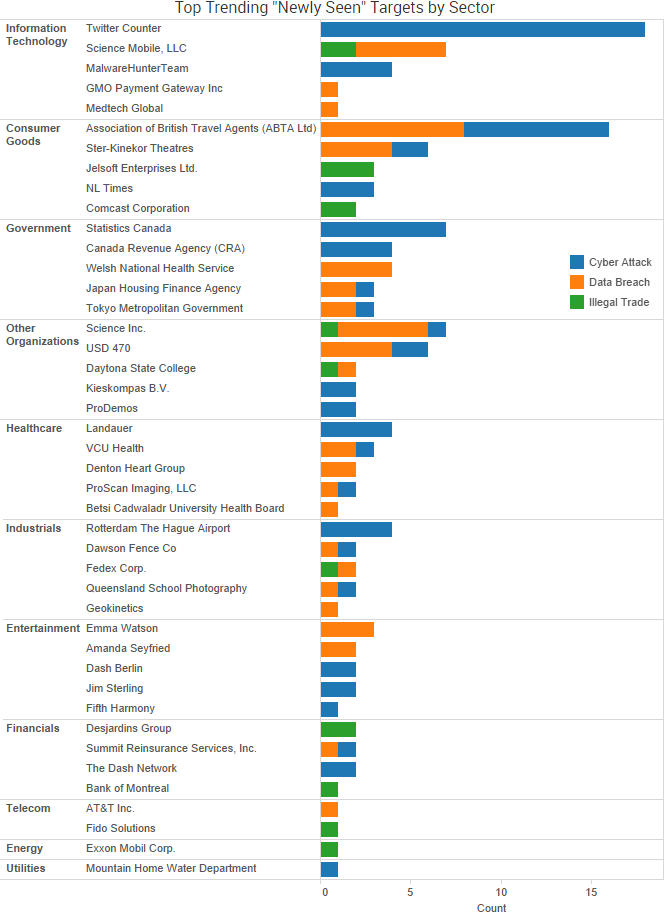
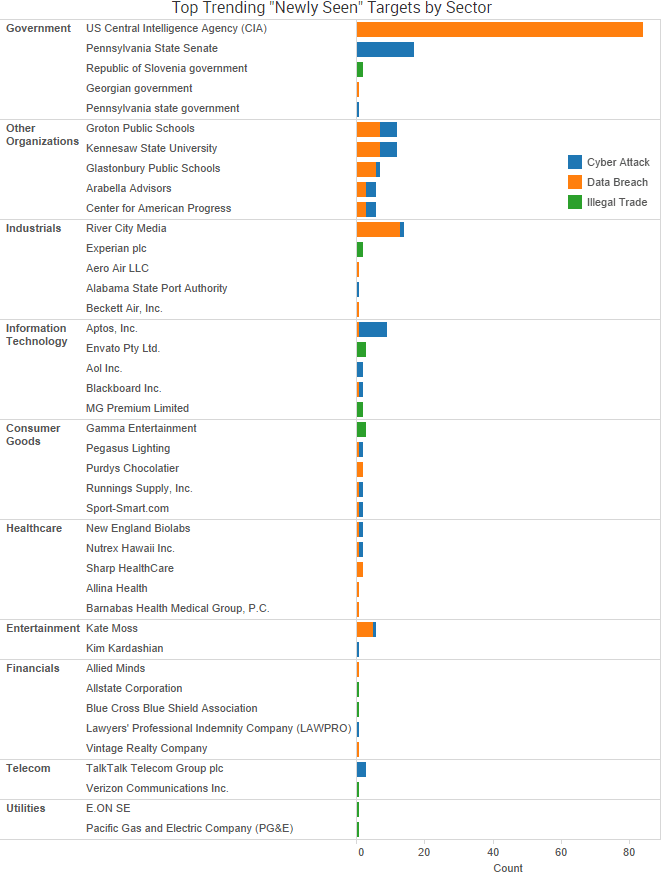
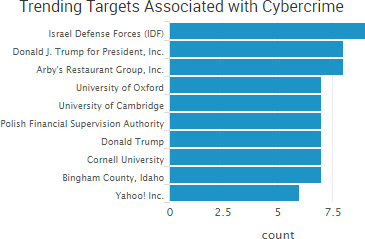
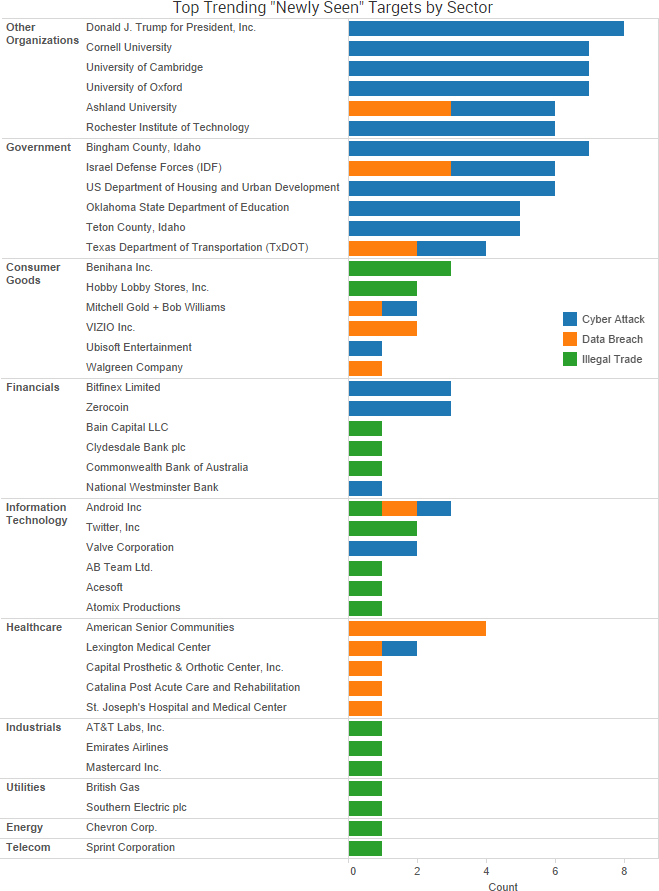
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
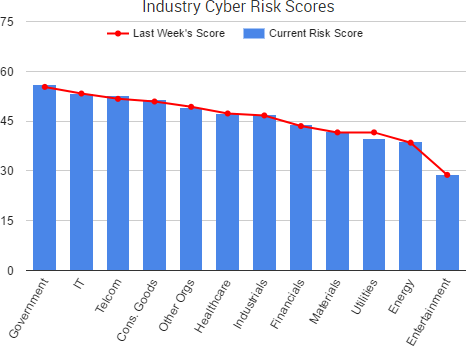
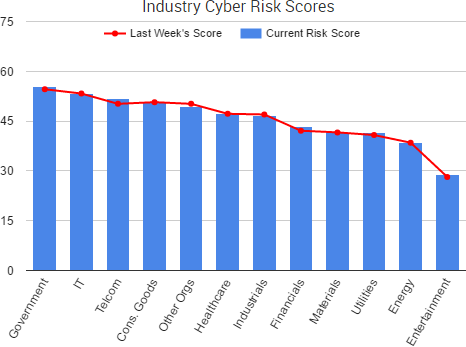
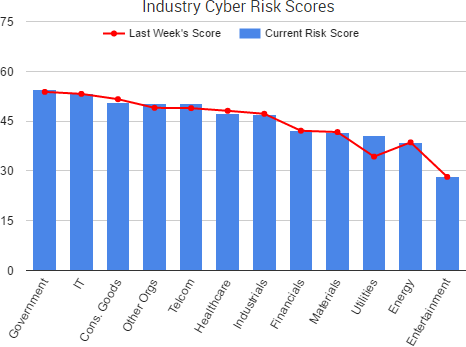
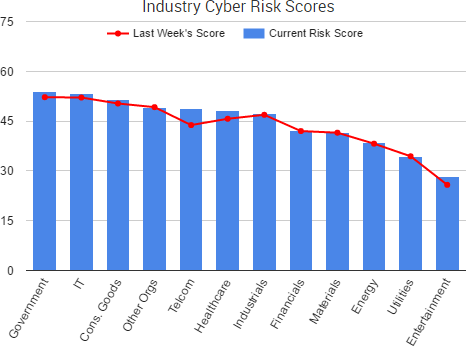
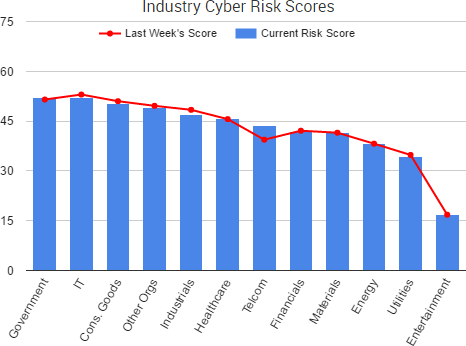
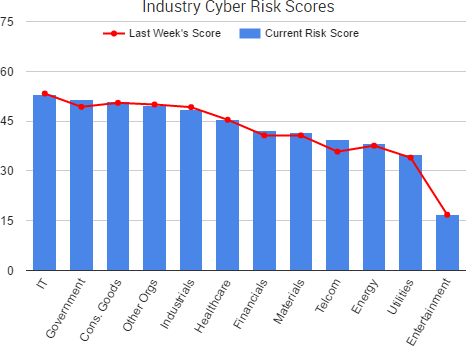
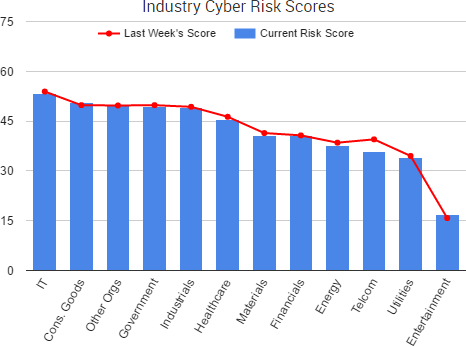
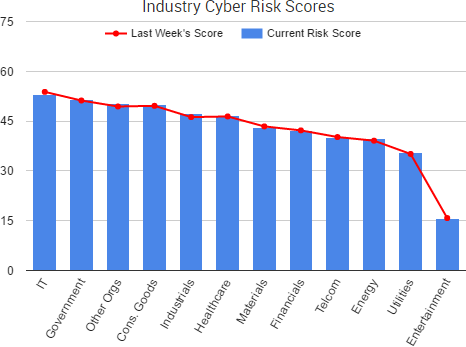
Cyber Risk Trends From the Past Week
In addition to the wide-reaching POS breach that IHG announced this week, online retailers may also be at risk of potential payment card breaches due to an unpatched zero-day vulnerability in the Magento ecommerce platform.
Security researchers at DefenseCode said they discovered the high-risk vulnerability during a security audit of Magento Community edition. The researchers said the vulnerability “could lead to remote code execution and thus the complete system compromise including the database containing sensitive customer information such as stored credit card numbers and other payment information.”
DefenseCode did not examine the Magento Enterprise version, but a researcher told Threatpost that both versions share the same underlying vulnerable code. The researcher also said that they have made repeated attempts to notify Magento of the issue since November 2016, but it has yet to be patched. In an email to customers, Magento said it plans on addressing the vulnerability soon:
This vulnerability will be addressed in our next release targeted for early May. Until then, we recommend enforcing the use of “Add Secret Key to URLs” to mitigate potential attacks. To turn on this feature:
1. Logon to Merchant Site Admin URL (e.g., your domain.com/admin)
2. Click on Stores > Configuration > ADVANCED > Admin > Security > Add Secret Key to URLs
3. Select YES from the dropdown options
4. Click on Save Config
Magento is used by approximately 200,000 online retailers, so the vulnerability is a cause for concern, particularly since it is now public and likely will not be patched for at least several weeks. In addition, an attack could be carried out by targeting any Magento admin panel user.
“Full administrative access is not required to exploit this vulnerability as any Magento administrative panel user regardless of assigned roles and permissions can access the remote image retrieval functionality [at the root of the vulnerability],” the advisory noted. “Therefore, gaining a low privileged access can enable the attacker to compromise the whole system or at very least, the database.”


 A variety of stories from the past week once again highlighted threats that originate not from external hackers, but from organizations’ employees and poor risk management practices.
A variety of stories from the past week once again highlighted threats that originate not from external hackers, but from organizations’ employees and poor risk management practices.

 “The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi,”
“The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi,” 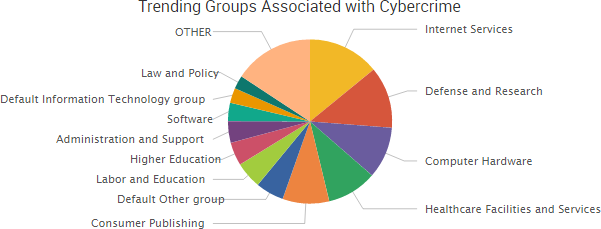
 The password manager LastPass has addressed a series of vulnerabilities that were discovered by Google Project Zero researcher Tavis Ormandy, including one now-patched “unique and highly sophisticated” client-side vulnerability in the LastPass browser extension.
The password manager LastPass has addressed a series of vulnerabilities that were discovered by Google Project Zero researcher Tavis Ormandy, including one now-patched “unique and highly sophisticated” client-side vulnerability in the LastPass browser extension. 
 “On February 20, 2017, a hacker created a job seeker account in an America’s JobLink (AJL) system,” the
“On February 20, 2017, a hacker created a job seeker account in an America’s JobLink (AJL) system,” the 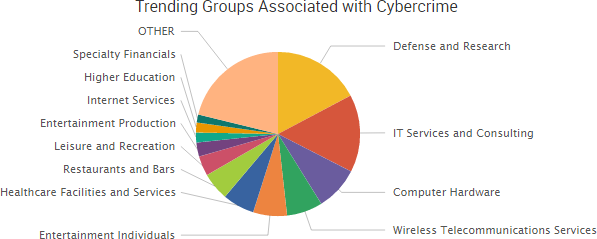
 One of the most profitable cybercriminal tactics is
One of the most profitable cybercriminal tactics is 
 Earlier this month, a patch was issued to address a high-impact vulnerability in Apache Struts Jakarta Multipart parser that allowed attackers to remotely execute malicious code. Shortly after the patch, an exploit appeared on a Chinese-language website,. Researchers then confirmed that attackers were “widely exploiting” the vulnerability. Since then, the issue has continued to affect numerous organizations through data breaches and service downtime.
Earlier this month, a patch was issued to address a high-impact vulnerability in Apache Struts Jakarta Multipart parser that allowed attackers to remotely execute malicious code. Shortly after the patch, an exploit appeared on a Chinese-language website,. Researchers then confirmed that attackers were “widely exploiting” the vulnerability. Since then, the issue has continued to affect numerous organizations through data breaches and service downtime.
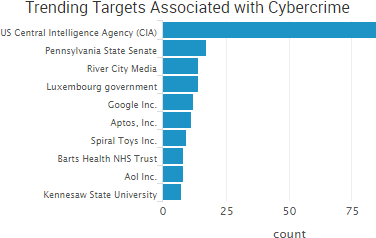 “Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized ‘zero day’ exploits, malware remote control systems and associated documentation,”
“Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized ‘zero day’ exploits, malware remote control systems and associated documentation,” 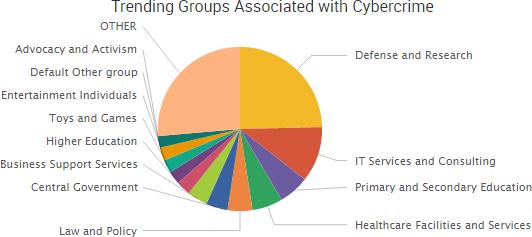
 Nearly every week researchers discover new data breaches due to publicly exposed databases that require no authentication, and this past week insecure Rync backups exposed the entire operation of River City Media (RCM), providing a rare glimpse inside what security researcher
Nearly every week researchers discover new data breaches due to publicly exposed databases that require no authentication, and this past week insecure Rync backups exposed the entire operation of River City Media (RCM), providing a rare glimpse inside what security researcher 



 Several companies have issued breach notification letters related to a malware incident at Aptos, Inc., which provides e-commerce solutions for a number of online stores. The breach at Aptos was discovered in November 2016, and notification by the various companies affected was delayed until recently at the request of law enforcement.
Several companies have issued breach notification letters related to a malware incident at Aptos, Inc., which provides e-commerce solutions for a number of online stores. The breach at Aptos was discovered in November 2016, and notification by the various companies affected was delayed until recently at the request of law enforcement. 
 “The bug was serious because the leaked memory could contain private information and because it had been cached by search engines,” wrote John Graham-Cumming, the CTO of Cloudflare, which provides performance and security services to numerous major websites. “We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence.”
“The bug was serious because the leaked memory could contain private information and because it had been cached by search engines,” wrote John Graham-Cumming, the CTO of Cloudflare, which provides performance and security services to numerous major websites. “We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence.”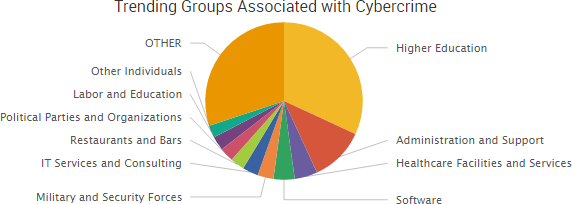
 The Cloudflare bug can be traced back to a single character of code, which resulted in a buffer overrun, the company said.
The Cloudflare bug can be traced back to a single character of code, which resulted in a buffer overrun, the company said.
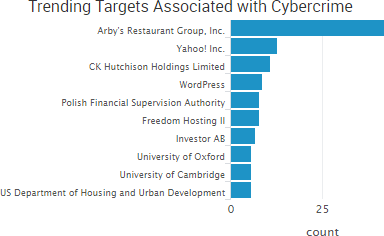
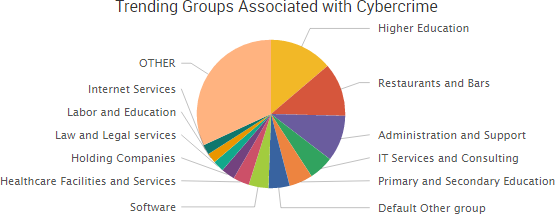
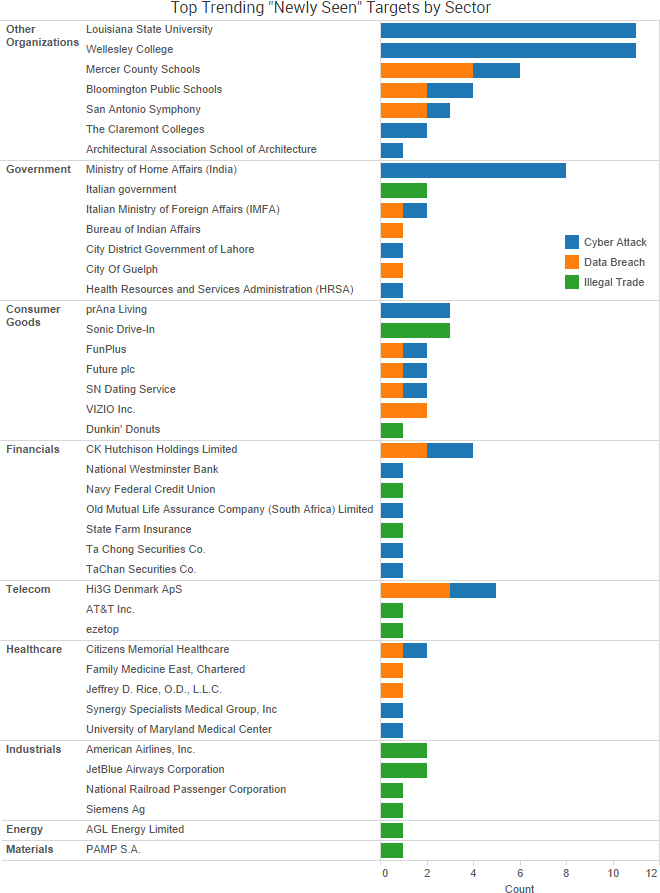
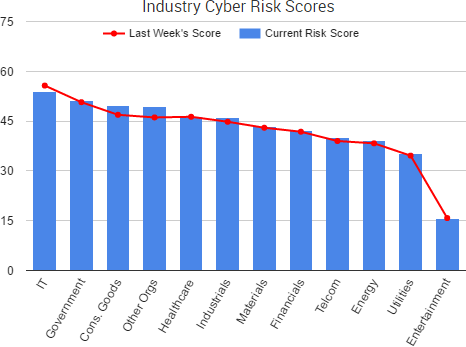 In addition to Yahoo, the past few weeks have seen several new regulatory announcements and fines related to data breaches.
In addition to Yahoo, the past few weeks have seen several new regulatory announcements and fines related to data breaches.