On Friday, 32-year-old Russian hacker Roman Seleznev was sentenced to 27 years in prison for running a cybercriminal operation that stole millions of payment cards, resulting in at least $169 million in damages to small business and financial institutions. It’s the longest sentence ever issued in the U.S. for cybercrime, and the court documents and testimony that led to the sentence revealed the inner workings of a decade-long operation that helped to grow and evolve payment card fraud into what it is today.
Earlier this month, in documents urging the judge to issue a lengthy sentence, the prosecution said Seleznev may have harmed more victims and caused more financial losses than any other defendant that ever appeared before the court:
“Seleznev is the highest profile long-term cybercriminal ever convicted by an American jury. His criminal conduct spanned over a decade and he became one of the most revered point-of-sale hackers in the criminal underworld. … Unlike smaller players in the carding community, Seleznev was a pioneer in the industry. He was not simply a market participant – he was a market maker whose automated vending sites and tutorials helped grow the market for stolen card data.”
In total, the government was able to identify 2,950,468 unique credit card numbers that Seleznev stole, possessed, or sold related to more than 500 U.S. business, subsequently affecting 3,700 financial institutions around the world. And — as the government pointed out — that is just the known losses.
Driving Small Businesses to Bankruptcy

As we wrote when Seleznev was convicted on 38 of the 40 counts he faced last year, many of the organizations he targeted were small businesses, and the testimony of seven of those businesses were heard in the court case.
Seattle’s Broadway Grill has perhaps been the most publicized of the point-of-sale breaches. Owner CJ Saretto testified that bad publicity from the breach instantly reduced the restaurant’s revenue by 40 percent and eventually forced him to “walk away from the business, shutter the doors, [and file] personal bankruptcy.” Other owners testified that the effect on business was “horrendous,” that the breach forced them into heavy debt, and that business “has never been the same” since the incident.
It’s no coincidence those that testified in the case against Seleznev were small business owners. Seleznev tended to target small businesses in the restaurant and hospitality industry, particularly if they had poor password security around their point-of-sale devices.
Seleznev “developed and used automated techniques, such as port scanning, to identify retail point of sale computer systems … that were connected to the Internet, that were dedicated to or involved with credit card processing, and that would be vulnerable to criminal hacks,” the indictment stated.
“He quickly learned that many of these businesses’ point of sale systems were remotely maintained by vendors with poor password security,” the government said in its sentencing memorandum. “Because most of his victims were small businesses, they were unlikely to have in-house IT or security personnel. As a result, these companies made extremely attractive targets for someone with Seleznev’s skills as a hacker.”
Track2, Bulba, 2Pac, and POS Dumps
However, Seleznev went far beyond merely stealing payment card information, he also helped to develop and operate websites to market the stolen data and promote more individuals to get into payment card fraud. Seleznev was 18 years old when he began participating in the Russian underground “carding” community under the alias “nCuX,” and seven years later, in 2009 when the U.S. Secret Service tried and failed to coordinate his arrest, he had become a major provider of stolen credit card data, according to court documents.
Just three months after being tipped off to the potential arrest by contacts inside the FSB and retiring his “nCuX” alias, Seleznev was back in the game under the name “Track2.” He soon unveiled two new automated vending websites, “Track2” and “Bulba,” which allowed buyers to to automatically search and purchase his stolen credit card data by using filters such as a particular financial institution or card brand.

Those features have become commonplace now, but as the prosecution noted, it was “a major innovation” at the time and the “Track2 and Bulba websites achieved instant success.”
“[The sites] made it possible for criminals to efficiently search for and purchase stolen credit card data through a process as easy as buying a book on Amazon,” the prosecution wrote. “Automated vending sites increased the efficiency [of] credit card data trafficking, and remain the gold standard for credit card trafficking to this day.”

The popular dark web marketplace AlphaBay adopted a similar automated shop for stolen payment card information in May 2015, but it includes more search options and a more user-friendly interface than Seleznev’s 2009 Bulba site.
In April 2011, Seleznev was injured in a terrorist bombing in Marrakesh, Morocco, and hospitalized for several months. His co-conspirators ran the Track2 and Bulba websites in his absence until they closed up shop in January 2012 citing no new dumps to sell.
Once again, Seleznev choose to return to cybercrime by innovating his operations. Switching monikers to “2Pac,” he launched a new automated vending site that would not only sell his stolen data but would offer stolen cards from “the best sellers in one place.” Seleznev would take a portion of the proceeds for each sale, and he used this model to resell credit data stolen in popular breaches such as Target, Michaels, and Nieman Marcus on the 2Pac site.

In addition, Seleznev needed a continuous stream of dumps and customers to fuel his 2Pac site, so he began teaching others the basics of payment card fraud via a sister site, called “POS Dumps.”

The POS Dumps website contained four categories to teach amateurs how to successfully commit payment card fraud:
- Choosing and buying equipment
- Choosing and buying dumps
- How to generate Track1 and why it is needed
- Writing the dumps onto cards
The website even had links to eBay to purchase the necessary equipment (an MSR206 manual swipe magnetic card reader/writer) and custom malware to help write the stolen payment card data onto other cards.
The prosecution wrote that the POS Dumps website “trained thousands of new criminals in the basics of how to use the data to commit fraud.” Similar types of tutorials related to fraud and cybercrime remain among the most commonly listed items on dark web markets today, according to SurfWatch Labs’ data.
A Record 27-Year Prison Sentence

Court documents from the defense called the long prison sentence “draconian.” However, Seleznev clearly knew his actions could have serious consequences. He monitored the U.S. court’s PACER system for any criminal indictments against him, and when agents arrested him in the Maldives as he attempted to board a plane in 2014, he immediately asked if the U.S. had an extradition treaty. The U.S. did not have a formal treaty with the Maldives, but an agreement was obtained in the days prior to take custody of Seleznev.
The prosecution described Seleznev’s sentencing guideline calculation as “literally off the charts.” A score of 43 recommends a life sentence, and Seleznev scored 16 points above that — a 59.
The judge agreed with the prosecution and sentenced Seleznev to 27 years in prison last Friday.
“The notion that the Internet is a Wild West where anything goes is a thing of the past,” said U.S. Attorney Annette L. Hayes. “As Mr. Seleznev has now learned, and others should take note – we are working closely with our law enforcement partners around the world to find, apprehend, and bring to justice those who use the internet to steal and destroy our peace of mind. Whether the victims are multi-national banks or small pizza joints, we are all victims when our day-to-day transactions result in millions of dollars ending up in the wrong hands.”


 According to the company’s
According to the company’s 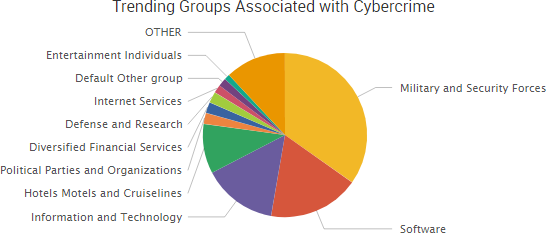

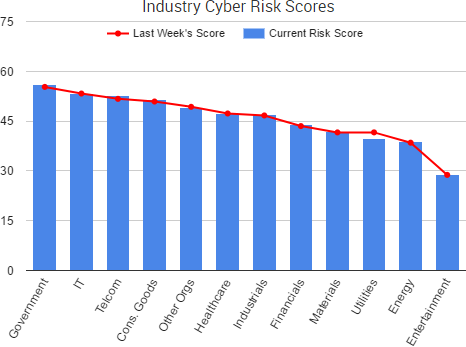








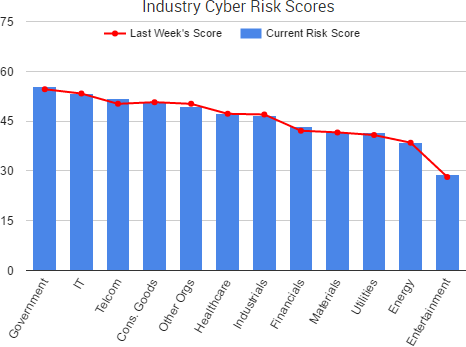 A variety of stories from the past week once again highlighted threats that originate not from external hackers, but from organizations’ employees and poor risk management practices.
A variety of stories from the past week once again highlighted threats that originate not from external hackers, but from organizations’ employees and poor risk management practices.




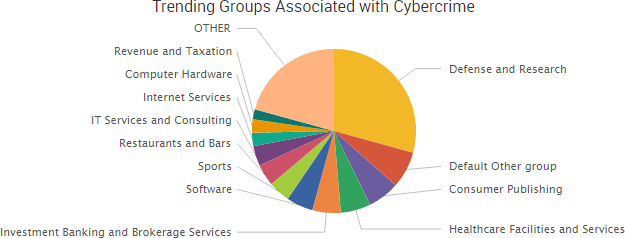





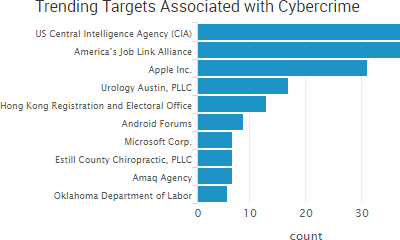 “The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi,”
“The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi,” 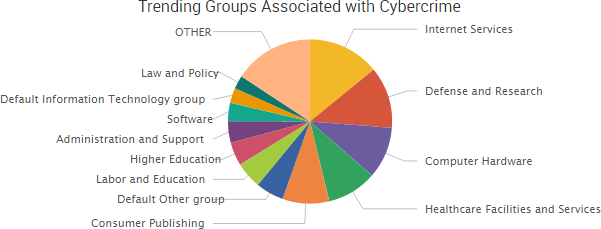
 The password manager LastPass has addressed a series of vulnerabilities that were discovered by Google Project Zero researcher Tavis Ormandy, including one now-patched “unique and highly sophisticated” client-side vulnerability in the LastPass browser extension.
The password manager LastPass has addressed a series of vulnerabilities that were discovered by Google Project Zero researcher Tavis Ormandy, including one now-patched “unique and highly sophisticated” client-side vulnerability in the LastPass browser extension.