In our ongoing series on Preparedness & Cyber Risk Reduction, we’ve discussed an “Introduction to the Preparedness Cycle” and we’ve explored the topics of preparedness and operational planning, and organizing and equipping. In our sustained effort to reduce risk through proper preparedness, we’ll tackle the next critical step in the Preparedness Cycle — training.
To effectively support our efforts to reduce organizational risks — which we defined as the “potential for an unwanted outcome resulting from an incident, event, or occurrence, as determined by its likelihood and the associated consequences” — we want to ensure our personnel are properly trained. Obviously, an organization conducts a variety of types of training and not all is relevant to preparedness (though a lot does impact broader risk management, such as some of the training that may be delivered by Human Resources). The focus of this article is specifically on two types of training: Threat Awareness Training and Operational Training.
FEMA states that, “Training provides first responders, homeland security officials, emergency management officials, private and non-governmental partners, and other personnel with the knowledge, skills, and abilities needed to perform key tasks required by specific capabilities. Organizations should make training decisions based on information derived from the assessments, strategies, and plans developed in previous steps of the Preparedness Cycle.”
I agree with FEMA’s definition, but, regrettably, it is incomplete. Our approach is to certainly encourage Operational Training to arm personnel “with the knowledge, skills, and abilities needed to perform key tasks required by specific capabilities,” often relating to the plans, procedures, systems, and equipment we put in place in the previous steps of the Preparedness Cycle but, in addition to Operational Training, it is critical that personnel have a sound understanding of the threat environment. Our motto at Gate 15 is to apply a “threat-informed, risk-based approach to analysis, preparedness and operations.” To do that right, training needs to include efforts aimed at educating personnel on the varied threats they may encounter in the workplace (and perhaps more broadly). We consider that Threat Awareness Training.
Organizations face a wide array of threats to their operations, people, and facilities. With limited time and resources, training can’t address every threat. To help prioritize training activities and emphasis, leaders should apply a threat-informed but risk-based approach to planning, developing, and conducting training. That means understanding the threats, conducting a risk assessment, and prioritizing the greatest risks as primary areas of focus. In today’s environment, an organization, we’ll call it Acme Innovations, may conduct a risk assessment and determine that Acme’s greatest areas of concern are hostile events at the workplace, a severe earthquake, a significant data breach, and being infected with ransomware.
If you recall from Part Two of this series, we said that, ideally, organizations will have a Preparedness Champion who can help develop and maintain a multi-year training and exercise program. This program — informed by a prioritized risk assessment — should detail a training schedule and progressively challenging exercises over a few years’ period. Developing a multi-year preparedness program helps protect time and allows leaders to plan for and commit funding to support the activities. Even if the details of an event change, the time and resources will be there. In Part Two of this series we met Johnny, who it turns out, is Acme Innovations’ Preparedness Champion. Johnny’s multi-year preparedness program includes Acme’s preparedness priorities, focused on the four areas noted above. For this post, let’s focus on the concerns around ransomware.
- Operational Training: Based on Acme Innovations’ preparedness priorities, Johnny’s multi-year preparedness program includes a deliberate approach to reduce the risks associated with the threat of ransomware. Johnny has worked with colleagues from across Acme Innovations to develop a Ransomware Response Plan, which they’ve included as an annex to the broader Acme Innovations Incident Management Playbook. The Plan includes specific actions for personnel to take upon identifying a possible ransomware infection. Those include immediate individual actions to take, who to report the incident to, what actions Acme’s security team and IT support teams are to take, key decisions and who is responsible for them, and other details developed through the process of Operational Planning. Over the next three months, Johnny and Acme’s corporate trainer are conducting training on that plan and the expected actions of all involved parties, to ensure Acme personnel understand their individual and team responsibilities in the event of a possible ransomware infection. At the end of the three-months, Johnny is leading a tabletop exercise with key leaders and responders to validate the plan and he wants everyone to know their roles and responsibilities ahead of time. But, wait – that’s the next part of this series!
- Threat Awareness Training: While Johnny and the trainer are training the organization on how to respond to a possible ransomware incident, Johnny knows that ideally, Acme will avoid getting infected in the first place. So, Johnny has done his homework, he’s looked at some of the great online resources that address ransomware, and he’s working closely with Acme’s security team to better understand how ransomware works and how it may be delivered. With his colleagues, he’s developed a deliberate Threat Awareness Training Plan to educate Acme Innovations personnel on what ransomware is, how it can enter a network, what the implications of that are, how individuals can help to reduce the risk of infection, and other nuggets he’s learned through his discussions and research. With that, he’s excited as he starts implementing his plan and educating his coworkers! Once again, good job, Johnny!
As we noted in Part Three, FEMA describes the core capability cybersecurity as protecting, and if needed, restoring, “electronic communications systems, information, and services from damage, unauthorized use, and exploitation.” Johnny’s efforts are directly supporting that for Acme Innovations but Acme knows that their threats are more than just cybersecurity. We identified Acme’s concerns above but for your organization, whether your emphasis is on health issues – such as the impacts of a potential pandemic, or natural disasters – maybe annual spring flooding or perhaps you’re in an area that is more likely to experience high-impact hurricanes, or physical security threats – such as workplace violence, the same approach to training applies. Addressing your prioritized risk concerns, both Operational Training and Threat Awareness Training should be included in your multi-year preparedness program.
But, wait, we said above that we only have limited time and resources for training. How do we get all this done?!?! Well, different organizations will approach training, and all aspects of preparedness, differently and will allocate varying amounts of time for it. Some will choose to conduct annual training days, whereas others will approach things in smaller, more frequent iterations. Some will conduct all training with internal resources, whereas some may bring in professional trainers for some, or all, of the training. Different approaches will make more or less sense for different organizations and for different threat concerns. Hurricane training may be something your organization does on an annual basis, whereas ransomware training may come in the form of a quick update every couple weeks. It will be up to you to determine the approach that makes the most sense for your organization based on your understanding of the threats, your risk assessment, your priorities, and your available time and resources.
With cybersecurity, there is abundant information available online about the array of potential threats and easy-to-find examples of real incidents. There is also a lot of great information on how to conduct training. Yes, of course, our team at Gate 15 is happy to help you develop your multi-year preparedness program and to support your operational and threat awareness training (!) but you can leverage some great free resources to help inform and support your program as well.
What’s most important is that as an organization, you follow Acme’s example, assign a responsible champion and dedicate the necessary time to plan and conduct both operational and threat awareness training. As you progress through the Preparedness Cycle, each step builds and enhances the work of the previous step. Having effective plans, people, and equipment in place, it is vital that you give them the necessary training to understand the threats your organization is most concerned about, the risks those threats pose, and the actions you need them to take. This further enhances our preparedness and resilience, minimizing the impacts of incidents and facilitating a quick return to normal operations when they do occur. With a solid training program in place, we move onto the next step in the Preparedness Cycle. In the next installment we’ll address exercises, where we have the opportunity to test and validate all the good work we’ve done!




 New York’s attorney general Eric Schneiderman announced last Thursday that
New York’s attorney general Eric Schneiderman announced last Thursday that 

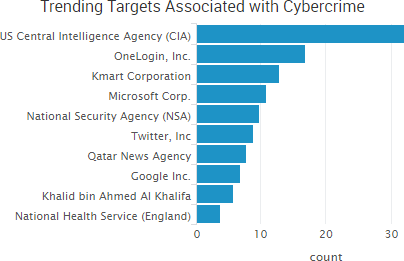
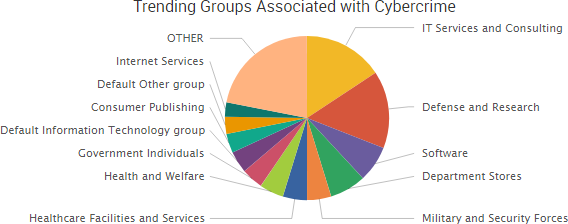
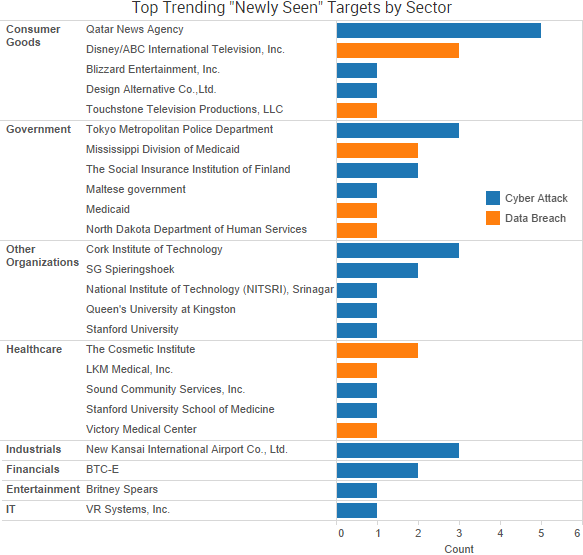
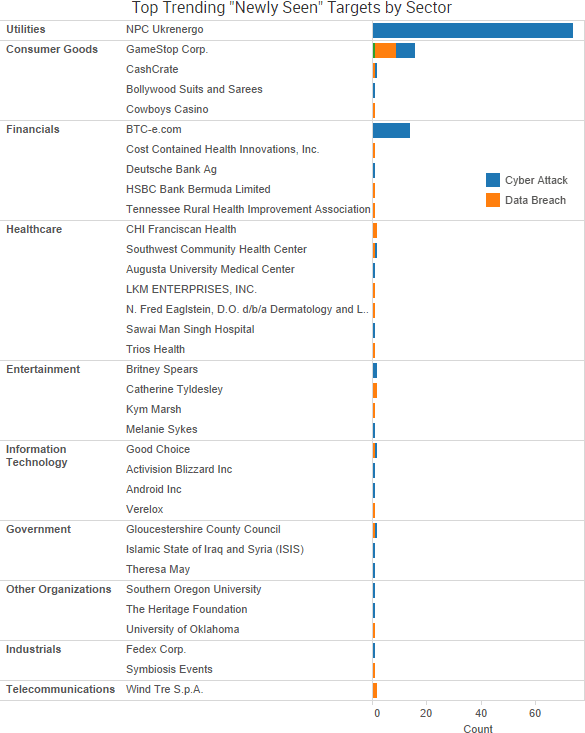
 Recent incidents have confirmed that malicious actors are using cyber-attacks and data leaks to both blatantly fabricate entire news stories and discreetly drop small pieces of fake information that can potentially have wide-reaching geopolitical implications.
Recent incidents have confirmed that malicious actors are using cyber-attacks and data leaks to both blatantly fabricate entire news stories and discreetly drop small pieces of fake information that can potentially have wide-reaching geopolitical implications.
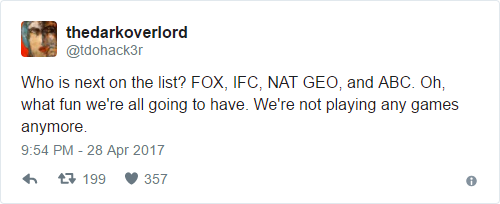
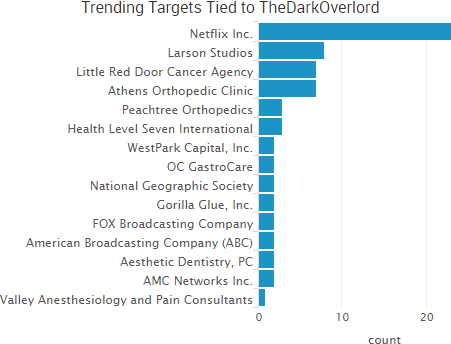
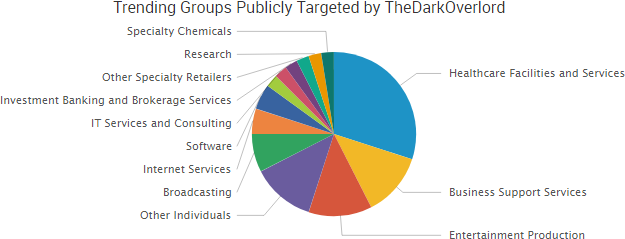

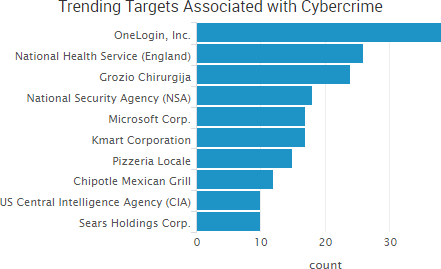
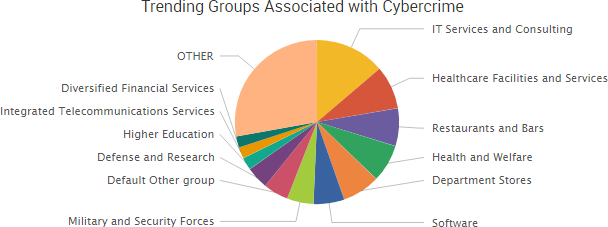
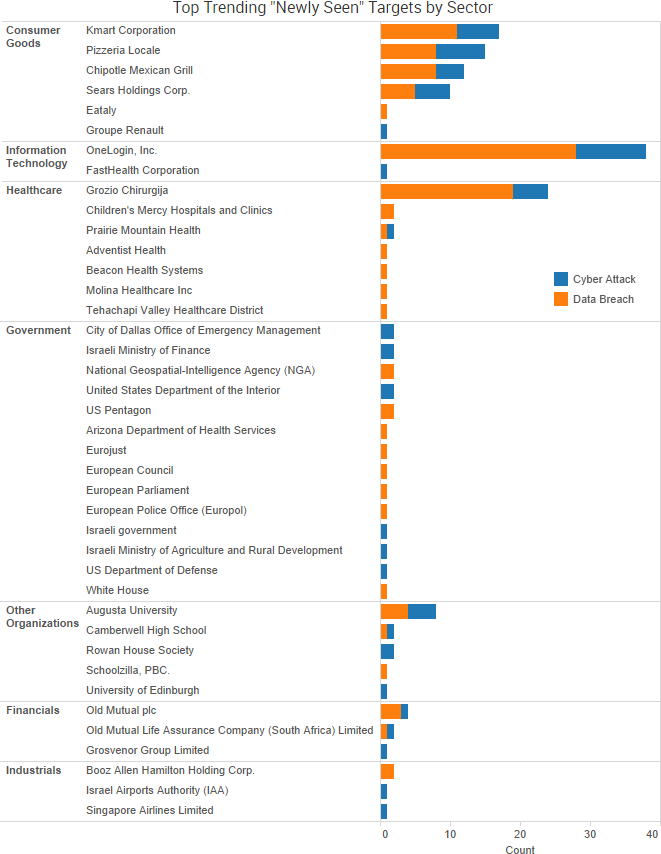
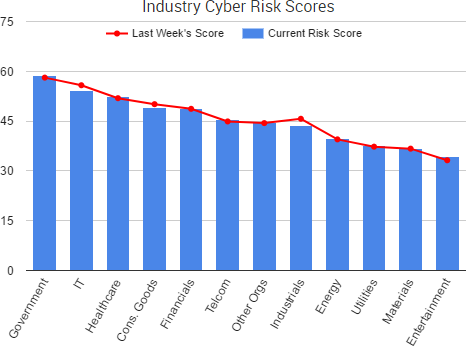 TheShadowBrokers continued to make headlines over its
TheShadowBrokers continued to make headlines over its 


 It is now less than one year until the EU General Data Protection Regulation (GDPR) goes into effect, yet some organizations are either unaware of the upcoming privacy changes or believe they will have issues meeting next year’s deadline, according to recent research.
It is now less than one year until the EU General Data Protection Regulation (GDPR) goes into effect, yet some organizations are either unaware of the upcoming privacy changes or believe they will have issues meeting next year’s deadline, according to recent research. 
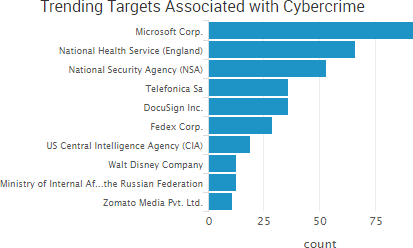

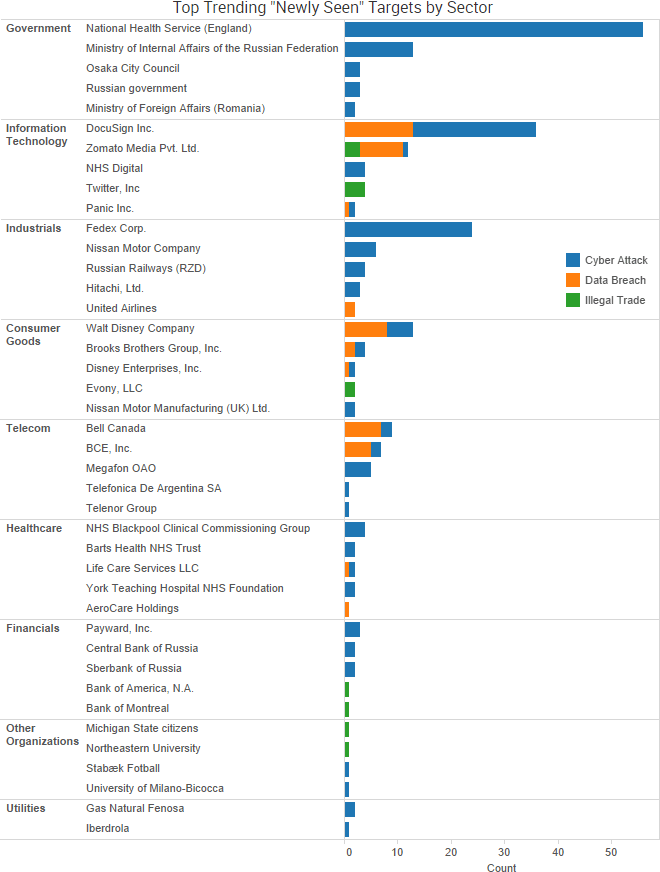
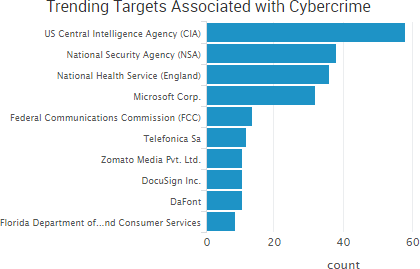
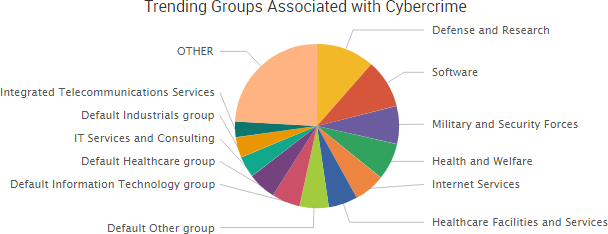
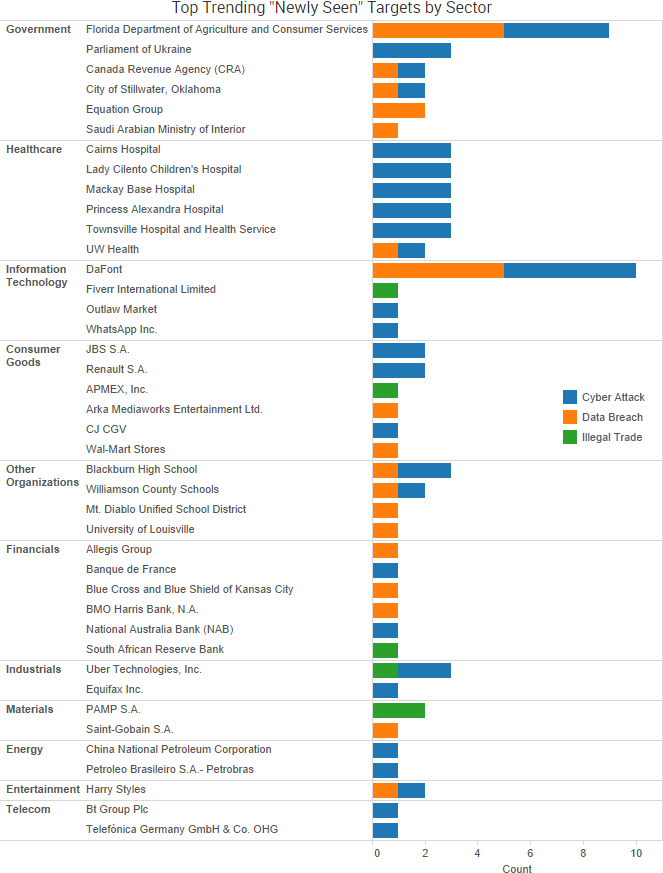
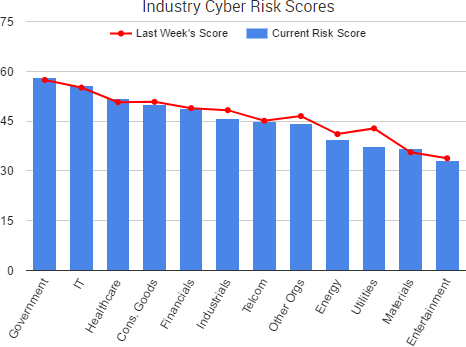
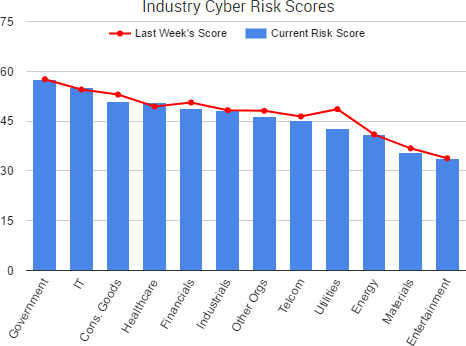 As WannaCry continues to dominate cybercrime news, the past week saw even more leaks of government-created malware and promises of additional leaks to come in the future. WikiLeaks has continued to dump files allegedly stolen from the CIA, and TheShadowBrokers group has announced a new monthly service providing various data dumps and exploits to its customers.
As WannaCry continues to dominate cybercrime news, the past week saw even more leaks of government-created malware and promises of additional leaks to come in the future. WikiLeaks has continued to dump files allegedly stolen from the CIA, and TheShadowBrokers group has announced a new monthly service providing various data dumps and exploits to its customers.