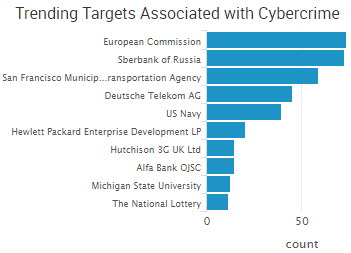
The European Commission is the top trending cybercrime target over the past two weeks after experiencing a distributed denial-of-service attack (DDoS) that brought down Internet access for several hours over two separate periods, making it difficult for employees to work, a staff member told Politico.
 However, the most impactful event from the period is the campaign that targeted organizations in Saudi Arabia with the Shamoon malware and wiped the hard drives of thousands of computers. The campaign targeted six organizations, resulting in extensive damage at four of them. People familiar with the investigation told Bloomberg that thousands of computers were destroyed at the headquarters of Saudi’s General Authority of Civil Aviation and that office operations came to a halt for several days after critical data was erased. Among the other targets were the Saudi Central Bank and several unnamed government agencies.
However, the most impactful event from the period is the campaign that targeted organizations in Saudi Arabia with the Shamoon malware and wiped the hard drives of thousands of computers. The campaign targeted six organizations, resulting in extensive damage at four of them. People familiar with the investigation told Bloomberg that thousands of computers were destroyed at the headquarters of Saudi’s General Authority of Civil Aviation and that office operations came to a halt for several days after critical data was erased. Among the other targets were the Saudi Central Bank and several unnamed government agencies.
Saudi authorities said evidence suggests Iran is to blame. The attackers used the exact same Shamoon malware that hit Saudi Aramco in 2012 and destroyed 35,000 computers, according to people familiar with the investigation. Ars Technica noted that Shamoon attempts to spread across networks by turning on file sharing and attempting to connect to common network file shares. In addition, the attackers used stolen credentials hard-coded into the malware.
Shamoon is made up of three components. The dropper component determines whether to install a 32-bit or 64-bit version of the malware. The wiper component uses RawDisk, the same driver that was used against Sony Pictures in 2014. The communications component was not used in this attack as the malware was configured with the IP of 1.1.1.1.
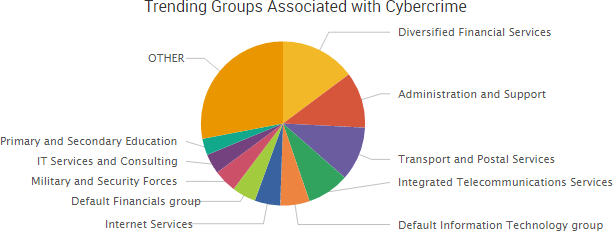
Other trending cybercrime events from the week include:
- Another week of “oops” breaches: Security researcher Chris Vickery discovered a file repository for Allied-Horizontal exposed to the Internet and requiring no authentication that contained sensitive information related to explosives. Confidential police files on 54 terrorist cases were copied onto a staffer’s private storage device that was connected to the Internet without a password. The U.S. Department of Housing and Urban Development accidentally made the personal information of almost 600,000 individuals temporarily available to the public via its website.
- Individuals and organizations face blackmail: Hackers have allegedly stolen data from Valartis Bank Liechtenstein and are threatening individual customers that they will leak their stolen information to financial authorities and the media if they do not pay ransom demands. The hacking group known as TheDarkOverlord said they gained access to Dropbox and email accounts for Gorilla Glue and stole 500 GB of information, including intellectual property and product designs. TheDarkOverlord said they offered the company “a handsome business proposition,” which is the group’s way of saying they demanded ransom.
- Ransomware disrupts organizations: The computer systems of the San Francisco Municipal Transportation Agency were infected with ransomware, and the actor behind the attack demanded $73,000 in ransom. Passengers unable to pay fares due to locked machines were temporarily given free rides. Bigfork School District in Montana recently experienced a ransomware infection due to a malicious email attachment, but the district said it would not pay any ransom demands. Computers at Carleton University in Canada were infected with ransomware, bringing research to a halt. The attackers asked for around $39,000 to decrypt the data.
- Business-to-business cybercrime: Gaming company Zynga is suing two former employees over the theft of “extremely sensitive” information, which was then allegedly taken to rival company Scopely. James Frazer-Mann, a 35-year-old former operator of Elite Loans, was sentenced by a UK court for hiring a hacker to DDoS his former company’s competitors and the website of the Consumer Action Group.
- More data breaches announced: The Madison Square Garden Company announced a point-of-sale data breach affecting customers who used payment cards to purchase food and merchandise at Madison Square Garden, the Theater at Madison Square Garden, Radio City Music Hall, Beacon Theater and Chicago Theater. The Navy was notified by Hewlett Packard that the names and Social Security numbers of more than 130,000 sailors were compromised. An unauthorized party gained access to a Michigan State University server containing personal information on 400,000 individuals, but only 449 of those records are confirmed to have been accessed. The hacker behind the data breach at Casino Rama has uploaded a five gigabyte file containing more than 14,000 documents to a torrent website. UK Telecom company Three announced a data breach after cybercriminals were able to gain access to its upgrade system using authorized logins.The sensitive personal information of 17,000 students was compromised in a data breach at Erasmus University in the Netherlands.
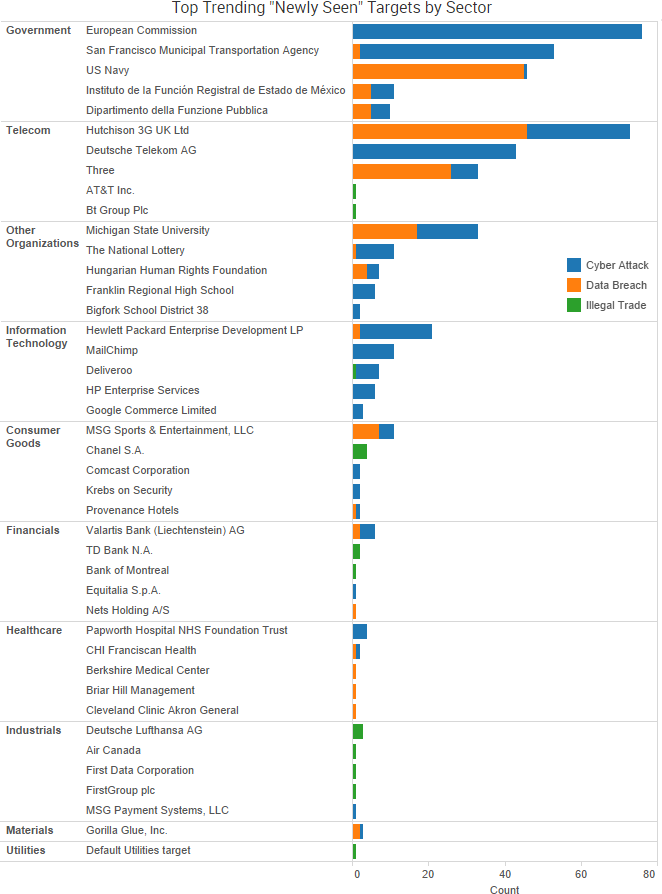
SurfWatch Labs collected data on many different companies tied to cybercrime over the past two weeks. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.
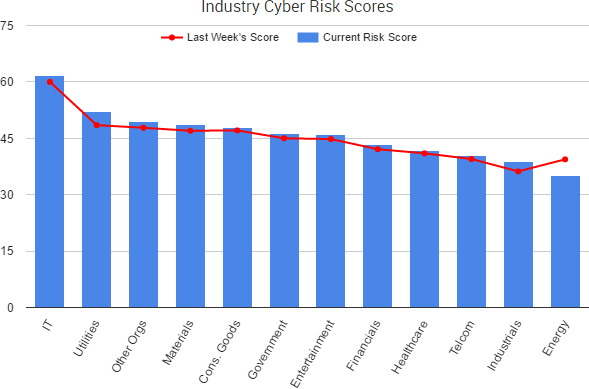
Cyber Risk Trends From the Past Week
Over the past two weeks, most industry sectors have seen an increase in their SurfWatch Labs’ cyber risk scores. The IT sector, once again, has the highest overall score. That is due, in part, to ongoing worry over DDoS attacks tied to Marai and other botnets compromised of Internet-of-Things devices.
Around 900,000 customers of Deutsche Telekom had their service disrupted due to external actors trying and failing to infect routers with malware, the company said. The attack caused crashes or restrictions on approximately four to five percent of all routers. Thousands of KCOM customers also lost their Internet access due to routers being targeted in a cyber-attack. KCOM issued a statement about the incident:
“We have now identified that the root cause of the problem was a cyber attack that targets a vulnerability in certain broadband routers, causing them to crash and disconnect from the network. The only affected router we have supplied to customers is the ZyXel AMG1302-T10B. The vast majority of our customers are now able to connect to and use their broadband service as usual.”
Researchers have identified other companies that use routers made by ZyXel and may be vulnerable to similar attacks, including Irish telecom operator Eir and Vodafone Group Plc in Britain.
Two hackers have since claimed credit for the attack against Deutsche Telekom and apologized for the outage. They were trying to enlist those routers in a growing Marai botent, which they claim is now the most powerful Marai-based botnet. One of the hackers told Motherboard the botnet included over a million devices; however, other researchers have estimated that number to be around 400,000.
The hackers, going by the name BestBuy and Popopret, are advertising a DDoS service powered by their new botnet with attacks allegedly ranging up to 700 Gbps.
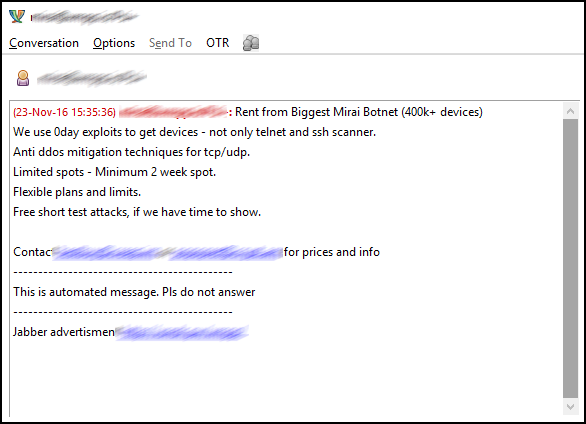
Popopret told BleepingComputer that the price for a two-week long attack using 50,000 bots — and an attack duration of one hour along with a 5-10 minute cooldown time between attacks — is approximately $3000-$4,000. BestBuy reported similarly high fees, telling Motherboard that a similar attack using 600,000 bots would cost $15,000-$20,000.
It is unclear exactly how many devices the group controls at the moment, but it is clear that various groups are competing to infect and retain control over a growing number of Internet-connected devices.

