Yahoo remained as the top trending cybercrime target due to a data breach affecting more than a billion accounts. The breach is so large that regulators such as the FTC and SEC are facing uncharted territory when it comes to potential fines or other consequences related to the incident, Vice News reported.
 Looking beyond the ongoing Yahoo story, there were several unique cybercrime-related events worth noting from the past week.
Looking beyond the ongoing Yahoo story, there were several unique cybercrime-related events worth noting from the past week.
For starters, a data breach at Kia and Hyundai aided in the physical theft of dozens of cars, Israeli police said. Criminals were able to use the stolen data to make car keys for luxury cars and steal those cars directly from the owners’ homes. The three men who were arrested allegedly looked for the registration numbers on Kia and Hyundai models and then used those number along with stolen anti-theft protection numbers and other codes to make keys for each specific car. Once the keys were made they would visit the owners homes — the information was also in the stolen data — to steal the vehicles and then sell them on the Palestinian car market.
Another interesting story is the recent sudden shutdown of a power distribution station near Kiev, which left the northern part of the city without electricity. Vsevolod Kovalchuk, the acting chief director of Ukrenergo, told Reuters that the outage was likely due to an external cyber-attack. The outage amounted to 200 megawatts of capacity, which is about a fifth of Kiev’s nighttime energy consumption.
If definitively tied to a cyber actor, the incident would be the second time in a year that a Ukrainian power outage was attributed to a cyber-attack. The December 2015 outage at Prykarpattyaoblenergo has been frequently cited as the first power outage directly tied to a cyber-attack.

Other trending cybercrime events from the week include:
- Education Information Compromised: Online learning platform Lynda.com is notifying its 9.5 million users of a data breach after a database was accessed that contained users’ contact information, learning data and courses viewed. The Columbia County School District in Georgia confirmed it was the victim of a data breach after an external actor accessed a server containing confidential employee information such as names, Social Security numbers and dates of birth. A malware infection at Summit Reinsurance Services may have compromised the information of 1,000 current and former employees at Black Hawk College, as well as those employees’ dependents. The University of Nebraska-Lincoln notified approximately 30,000 students that their names and ID numbers may have been compromised when a server hosting a math placement exam was breached.
- More Healthcare Data Breaches: Community Health Plan of Washington is notifying 381,534 people that their information may have been compromised due to a vulnerability in the computer network of NTT Data, which provides the nonprofit with technical services. East Valley Community Health Center in California is notifying patients of a Troldesh/Shade ransomware infection on a server containing patient information. The server contained 65,000 insurance claims from the past six years, which included names, dates of birth, home addresses, medical record numbers, health diagnosis codes and insurance account numbers. A number of employees allegedly attempted to access the medical records of Kayne West during his recent week-long stay at the UCLA Medical Center.
- OurMine Continues to Hijack Popular Accounts: The hacking group known as “OurMine” managed to hijack the Twitter accounts of both Netflix and Marvel on Wednesday. The group posted its usual message about how they were just testing security, along with their contact information.
- DDoS Attacks Used to Protest New Law in Thailand: Thai government websites were hit with DDoS attacks in protest of a new law that restricts internet freedom. The websites of the Defense Ministry, Ministry of Digital Economy and Society, the Prime Minister’s Office, and the Office of the National Security Council were all targeted. In addition, a hacker going by the name “blackplans” posted screenshots of documents allegedly stolen from government websites.
- Other breach announcements: A May 2016 phishing incident led to 108 employees of L.A. County handing over their email credentials, resulting in a data breach affecting 756,000 individuals. A hacker going by “1×0123” claims to have hacked PayAsUGym and is attempting to sell a database of information on 305,000 customers. A database backup from the forum of digital currency Ethereum was stolen after a malicious actor socially engineered access to a mobile phone number and gained access to accounts. About 350 Ameriprise clients had their investment portfolios exposed due to an advisor synchronizing data between between his home and work and neither drive requiring a password. The Bleacher Report announced a data breach affecting an unknown number of users who signed up for accounts on its website. The U.S. Election Assistance Commission (EAC) acknowledged a potential intrusion after a malicious actor was spotted selling information related to an unpatched SQL injection vulnerability.
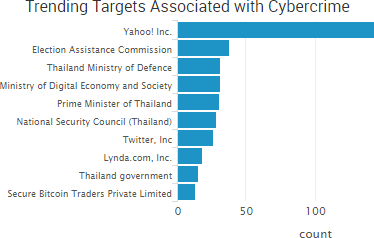
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.

Cyber Risk Trends From the Past Week
 Several stories from the past week once again highlighted the problem of malicious insiders stealing intellectual property and taking that stolen data directly to company rivals in order to give those rivals a leg up on the competition.
Several stories from the past week once again highlighted the problem of malicious insiders stealing intellectual property and taking that stolen data directly to company rivals in order to give those rivals a leg up on the competition.
The first case involves India’s Quatrro Global Services, which recently filed a complaint with local police accusing two former employees of stealing a customer database and using that database to open a rival remote support company, MS Care Limited.
The employees left Quatrro Global Services in late 2014 and early 2015 and opened the rival company in January 2016. The complaint alleges the database was “used to derive unlawful commercial benefit by accessing our customers, leading to our commercial loss while gaining unauthorised access to our customer’s personal information, which could be used for unlawful purposes.”
A separate case involves David Kent, 41, who recently pleaded guilty to stealing more 500,000 user resumes from Rigzone.com, a company that he sold in 2010, and then using the stolen data to boost the membership of his new oil and gas networking website, Oilpro. According to the complaint, Rigzone’s database was hacked twice, and its members were subsequently solicited to join Oilpro. After building up the membership base in this manner, Kent then tried to sell the Oilpro website by stating that it had grown to 500,000 members through traditional marketing methods.
As SurfWatch Labs noted in October, insider threats are one of the most difficult challenges facing organizations. A recent survey of 500 security professionals from enterprise companies found that one in three organizations had experienced an insider data breach within the past year and that more than half of respondents believe that insider threats have become more frequent over the past year.
SurfWatch Labs data confirms those security professionals worry, having collected data on more than 240 industry targets publicly associated with the “insider activity” tag over the past year.


2 thoughts on “Weekly Cyber Risk Roundup: Unique Cyber-Attacks and Insider Theft”