Earlier this month, an undergraduate student in Korea apologized for creating and making public the joke ransomware “Resenware.” The malware didn’t ask for money to decrypt files; instead, it required victims to score more than 200 million points on the “lunatic” level of the shooting game Touhou Seirensen ~ Undefined Fantastic Object.
The student told Kotaku that he released the joke malware on Github before falling asleep and by the time he woke up it had spread and “become a huge accident.” The source code was quickly removed from Github and a tool was released allowing infected users to decrypt their files without having to play the game. The creator then apologized for making a “kind of highly-fatal malware.”
That’s all well and good, but as Will Rogers once said, “Letting the cat out of the bag is a whole lot easier than putting it back in.”

The story highlights how quickly publicly available source code can be spread, copied, and potentially repackaged by malicious actors. That isn’t as likely to happen with Resenware due to the lack of a financial component, though it could be utilized by actors looking to cause harm rather than turn a profit. Nevertheless, profit-driven actors have numerous other recent source code leaks they can pull from.
For example, in December 2016, the source code for a commercial Android banking Trojan, along with instructions on how to use it, was released on a cybercriminal forum. Malicious actors quickly used that code to create the BankBot Trojan, which Dr. Web researchers noted can steal login credentials and payment card details by loading phishing forms and dialogs on top of legitimate applications, as well as intercept and delete text messages sent to the infected device. Since then, BankBot has made several appearances in the Google Play store, confirming Dr. Web’s January conclusion that the leak “may lead to a significant increase in the number of attacks involving Android banking Trojans.” In fact, just last week two malicious applications utilizing BankBot, HappyTimes Videos and Funny Videos 2017, were removed from the Google Play store after receiving thousands of installs.
The BankBot Trojan is just one example of the continuing evolution of malware as the stockpile of effective cybercriminal tools continues to accumulate. The leak of these tools, whether made as a joke by amateurs or for malicious purposes by professional cybercriminals, means that more polished malware is now at the fingertips of malicious actors than ever before.
Even if an inexperienced actor is unable to take and modify public malware source code, they can simply turn to professionally run as-a-service malware options that are likely doing so.
Last week MalwareBytes released a report with an interesting chart on ransomware trends. It shows that the Cerber ransomware-as-a-service (RaaS) has come to dominate the ransomware market with a nearly 90% share as its main competitor, Locky, has declined.
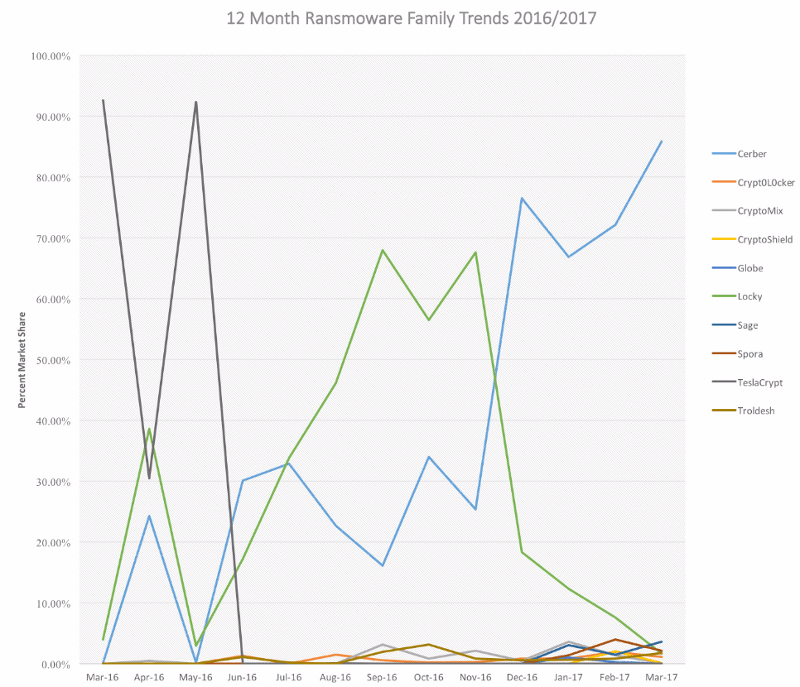
“Cerber [has spread] largely because the creators have not only developed a superior ransomware with military-grade encryption, offline encrypting, and a slew of new features, but by also making it very easy for non-technical criminals to get their hands on a customized version of the ransomware,” the report authors noted.
Those types of criminal operations can greatly benefit from the large amount of exploits and malware source code that has made its way into the public domain this year.
For example, since March 2017 we’ve seen:
- The release of the source code for the NukeBot banking Trojan, a modular Trojan that comes with a web-based admin panel to control infected endpoints.
- New allegedly NSA-developed exploits leaked by TheShadowBrokers, including last week’s release of a series of now-patched Windows exploits and a critical vulnerability that can hijack Solaris systems that was released a week prior (and patched today by Oracle).
- More leaks of alleged CIA exploits and tools, some of which claim the CIA benefited by repackaging components of the Carberb malware source code, which was leaked in 2013, into CIA hacking tools.
- A report last week claimed that the Callisto APT Group used tools leaked from the surveillance company HackingTeam, which was breached in 2015, in a series of targeted attacks last year.
Whether it’s nation-state actors, cybercriminal groups, or amateur hackers, they can all benefit by the leak of these tools over the past month. If past leaks are any indication, malicious actors will incorporate any effective tools and techniques from the recent leaks into their already-existing cyber arsenals.
As the collective knowledge grows on the cybercriminal side, it’s crucial that organizations harness their own threat intelligence in order to have their finger on the pulse of malicious actors. With that information they can more effectively counter the slew of new vulnerabilities, exploits, and as-a-service tools being used to infiltrate their networks and damage their organization.


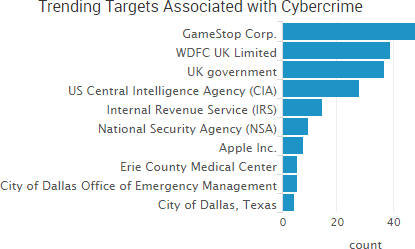
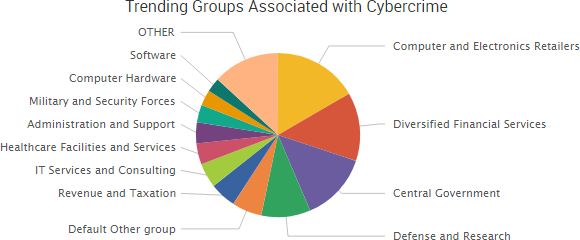
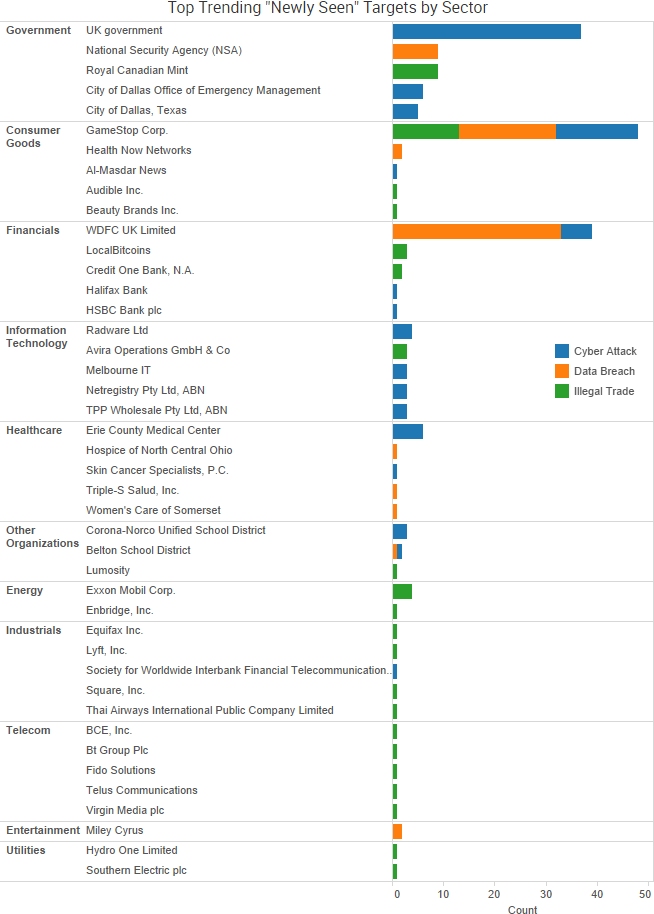
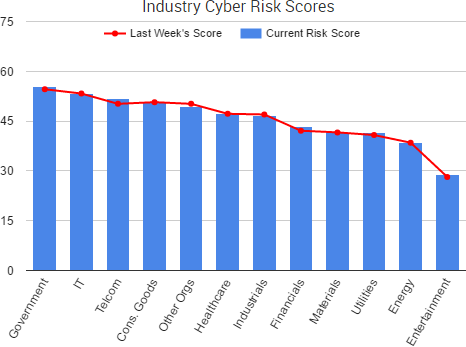 A variety of stories from the past week once again highlighted threats that originate not from external hackers, but from organizations’ employees and poor risk management practices.
A variety of stories from the past week once again highlighted threats that originate not from external hackers, but from organizations’ employees and poor risk management practices.
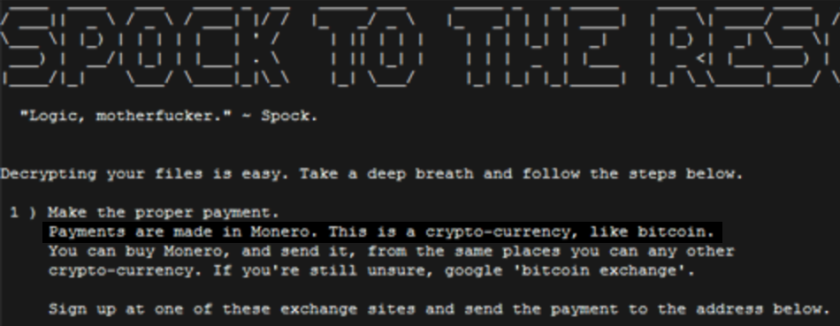
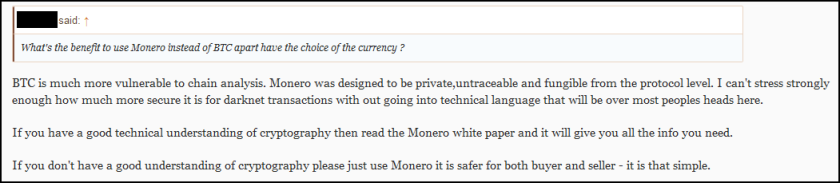


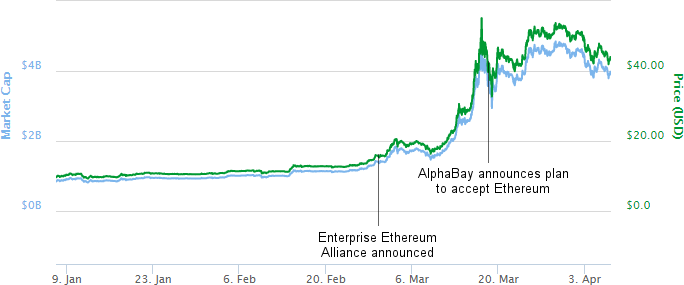

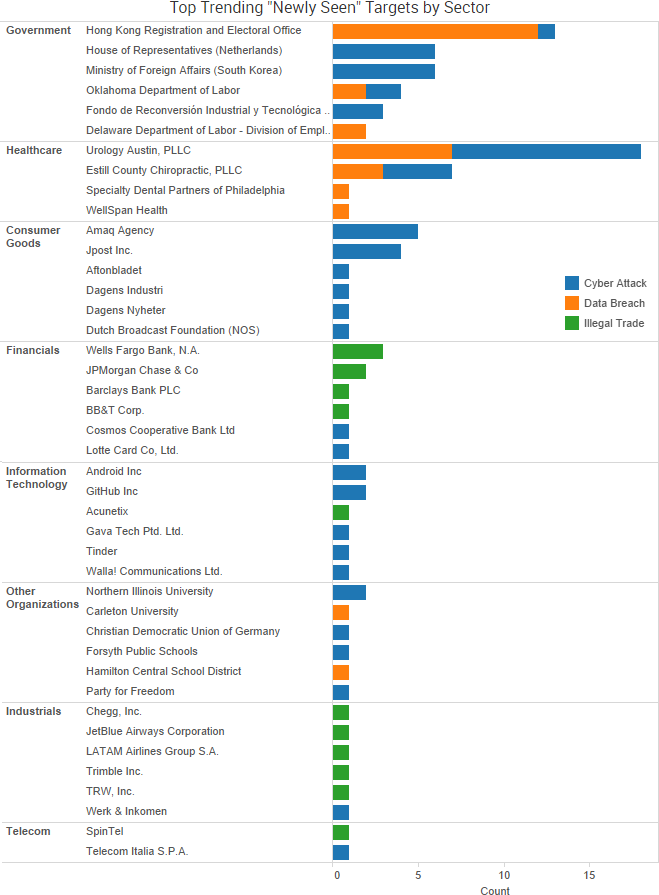
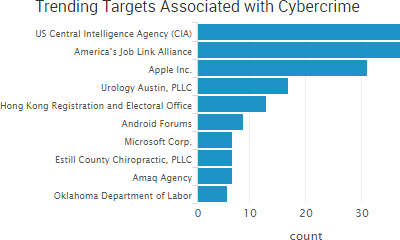 “The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi,”
“The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi,” 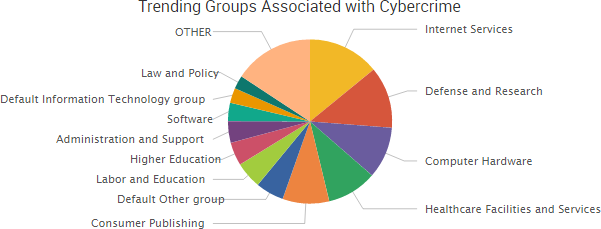
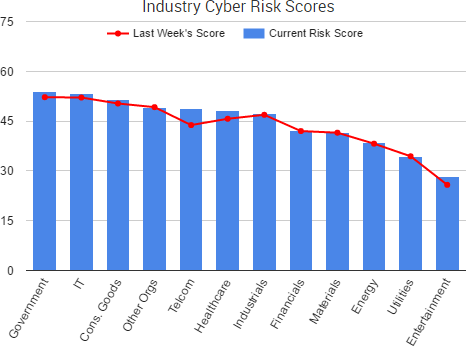 The password manager LastPass has addressed a series of vulnerabilities that were discovered by Google Project Zero researcher Tavis Ormandy, including one now-patched “unique and highly sophisticated” client-side vulnerability in the LastPass browser extension.
The password manager LastPass has addressed a series of vulnerabilities that were discovered by Google Project Zero researcher Tavis Ormandy, including one now-patched “unique and highly sophisticated” client-side vulnerability in the LastPass browser extension. 
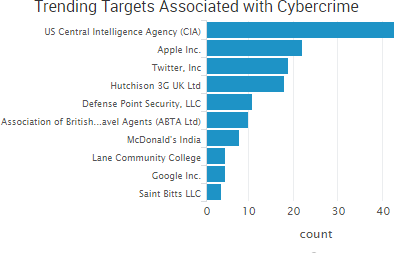 “On February 20, 2017, a hacker created a job seeker account in an America’s JobLink (AJL) system,” the
“On February 20, 2017, a hacker created a job seeker account in an America’s JobLink (AJL) system,” the 
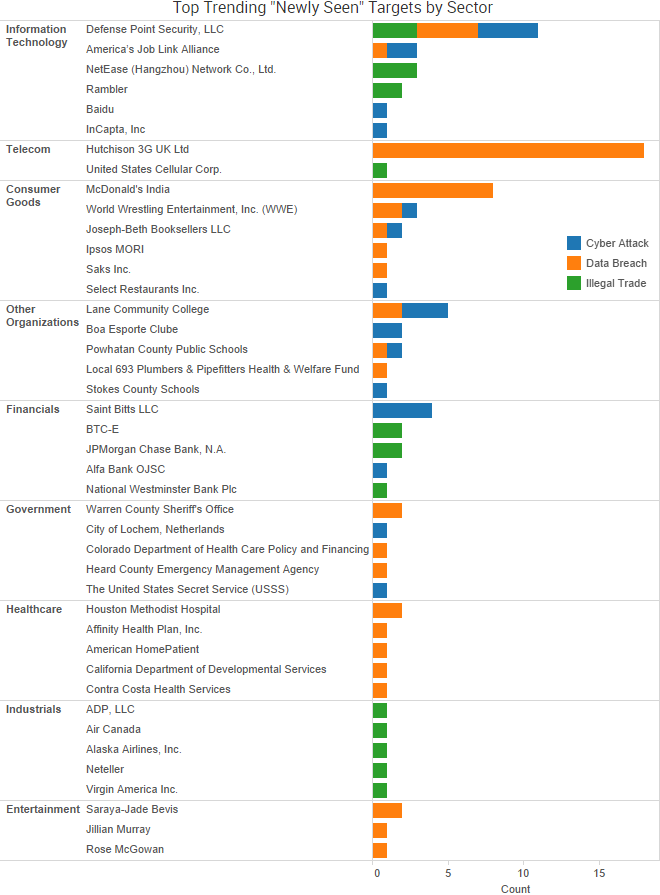
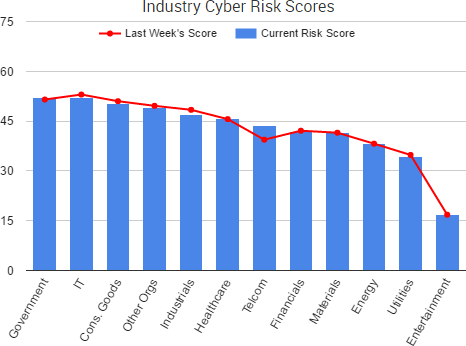 One of the most profitable cybercriminal tactics is
One of the most profitable cybercriminal tactics is 


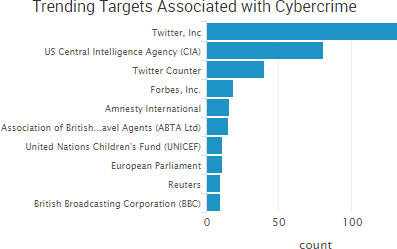
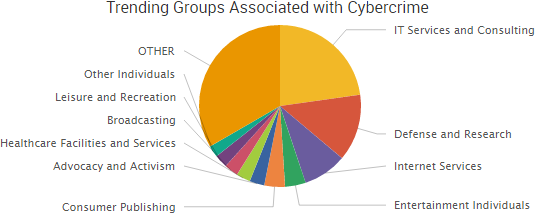
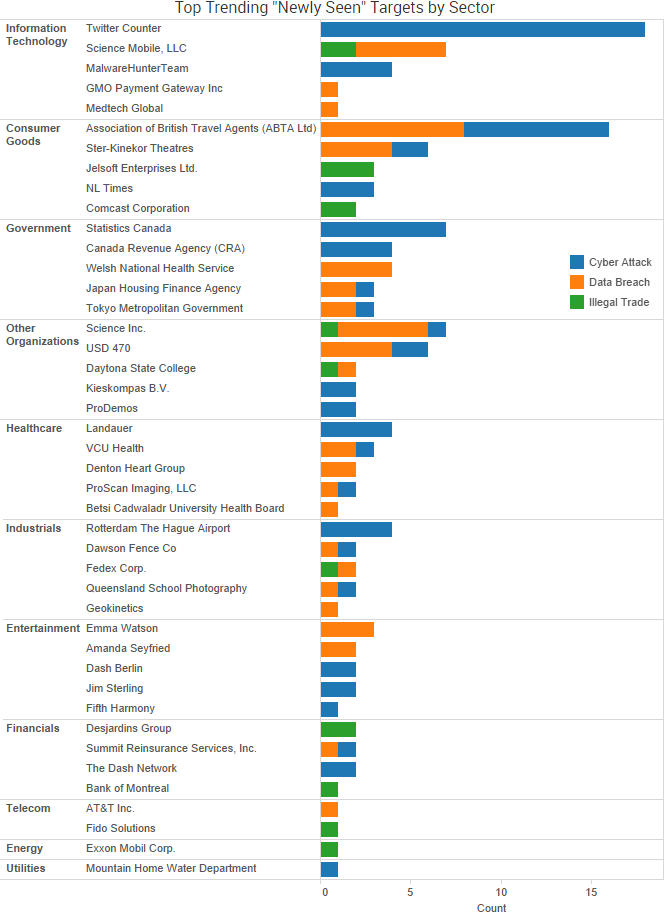
 Earlier this month, a patch was issued to address a high-impact vulnerability in Apache Struts Jakarta Multipart parser that allowed attackers to remotely execute malicious code. Shortly after the patch, an exploit appeared on a Chinese-language website,. Researchers then confirmed that attackers were “widely exploiting” the vulnerability. Since then, the issue has continued to affect numerous organizations through data breaches and service downtime.
Earlier this month, a patch was issued to address a high-impact vulnerability in Apache Struts Jakarta Multipart parser that allowed attackers to remotely execute malicious code. Shortly after the patch, an exploit appeared on a Chinese-language website,. Researchers then confirmed that attackers were “widely exploiting” the vulnerability. Since then, the issue has continued to affect numerous organizations through data breaches and service downtime.

