Businesses across the world are still recovering from last Friday’s outbreak of the WannaCry ransomware. On Monday, White House homeland security adviser Tom Bossert said that the ransomware had hit more than 300,000 computers, and security researchers have since detected several new versions of the malware — at least one of which doesn’t have the widely reported “kill switch” built in that has been used to slow the malware’s spread.
Much has been written about the effects of the ransomware on patients at NHS facilities, on downtime at factories, and on disrupted services at numerous other organizations. Various groups have estimated that the potential costs from the WannaCry outbreak may total between several hundred million and $4 billion.
The attention on WannaCry is deserved; however, there is a much smaller piece of ransomware news that emerged last month that highlights the devastating impact ransomware can have on a single organization. In a complaint filed in April against its insurer, the law firm Moses Afonso Ryan Ltd. (MAR) claims that a ransomware infection took more than three months to resolve, costing the firm more than $700,000 in lost billings.
“During the three months that the documents and information of MAR was held captive by the perpetrators of the ransomware attack, the attorneys of the firm were unproductive and unable to work at a reasonable efficiency,” the firm wrote in its complaint. “Year to year billing comparisons reveal a reduction of over $700,000 of billings for the three months of interruption.”
Dispute Over Insurance Policy Coverage
MAR is suing its insurer, Sentinel Insurance Company, claiming that the policy it purchased “is designed to protect MAR against precisely the type of loss it has now incurred as a result of the ransomware attack and interruption of its business.”
Sentinel countered that it did, in fact, pay $20,000 in damages, but it denied the additional claim for the alleged lost “business income” as it exceeded what Sentinel believes are the limits of the policy.
Like the other insurance-related lawsuits — such as the Fourth Circuit ruling against Travelers Insurance in August 2016 — the dispute appears to revolve around the language of the policy and what specifically the policy covers when it comes to cybercrime.
“Sentinel admits that it has not paid for all of the losses MAR has claimed resulted from the ransomware attack it suffered, as certain of the losses claimed are not covered by the policy,” Sentinel argued in court documents. “The only coverage under the policy for loss or damage caused by a computer virus is under the Computers and Media Endorsement [section], which changes the policy to provide additional coverage [up to $20,000] for certain computer-related losses.”
Three Months to Resolve the Ransomware?
The lawsuit is yet another reminder that organizations need to ensure they know what their insurance policies cover in regards to cyber-attacks, but that is not the only cyber risk management lesson worth noting from the lawsuit. The court documents also revealed that it took several months for MAR to recover from the single ransomware incident — far more than the average of 42 hours that Ponemon found most ransomware victims spend.

The long recovery time was due to a variety of reasons, which the law firm outlined in its complaint:
- In May 2016, a ransomware infection led to all of the documents and information stored on the MAR computer network being disabled and the computer network losing all functionality. MAR then hired security experts to fix the problem, but those experts were unable to gain access to the files.
- In June 2016, the firm made contact with the attacker and negotiated a 13 bitcoin ransom. It took several days to purchase the bitcoins and pay the extortionist because the firm said they were unaware that new account holders could only purchase 2 bitcoins per day.
- In July 2016, the firm had to re-establish communication with the attacker after discovering the decryption keys and tools it purchased did not work. A second bitcoin ransom was then negotiated and paid.
- In August 2016, MAR had to recreate documents after discovering that it could not recover documents saved on a temporary server during the three months of business interruption.
All of this resulted due to a combination of events: an attorney at MAR clicking on an email attachment from an unknown source, a lack of proper backups and incident response plan to address a well-known security issue, and a malicious actor that took advantage of the situation by demanding multiple ransom payments.
MAR is just one example of a business that was unprepared for a ransomware attack, and numerous other organizations are likely experiencing similar issues this week. As Elliptic noted, WannaCry has generated over $80,000 in ransom payments since Friday.
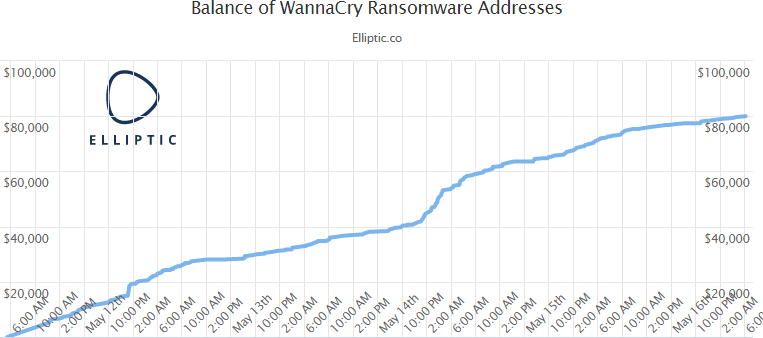
However, organizations that decided to pay the WannaCry ransom were lucky that it only required a $300 or $600 payment depending on how quickly they acted. In addition, multiple researchers have reported that organizations were able to successfully restore their files after payment, even as law enforcement agencies have advised there are no guarantees when dealing with cybercriminals.
This is not the case for many ransomware victims. Some recent ransomware campaigns have been observed charging a full two bitcoin in ransom (around $3,700) for any infections, and some organizations have received targeted ransom demands totaling tens of thousands of dollars — and, in cases like MAR, the decryption keys purchased at those inflated prices may not even work.
Hopefully, WannaCry will help push organizations towards better understanding, preparation, and incident response around ransomware since the problem is not going away any time soon.

