South Korean financial institutions dominated the week’s top trending targets due to a series of extortion demands that have threatened distributed denial-of-service (DDoS) attacks unless those institutions pay between 10 and 15 bitcoins ($24,000 to $36,000) in ransom each.

At least 27 financial institutions received the extortion demands from a group claiming to be the Armada Collective, including major banks, security companies, and the Korea Exchange, the Korea Joongang Daily reported. It is unclear if the group behind the threats is associated with the real Armada Collective, or if it is yet another group that is attempting to leverage the popular extortionists identity in order to gain credibility. In early 2016, a group was able to successfully extort more than $100,000 by threatening DDoS attacks under the Armada Collective name — but researchers concluded that specific threat was empty and the group never actually carried out any attacks — despite being profitable.
According to The Korea Times, the group carried out a small attack last Monday on the Korea Financial Telecommunications & Clearings Institute (KFTC), Suhyup Bank, DGB Daegu Bank, and JB Bank — with a promise of more powerful attacks to come in the future if the institutions do not pay their ransoms by the July 3 deadline. The DDoS attacks did not disrupt any services, the Times reported, and the small DDoS attack against KFTC last Monday lasted for only 16 minutes. Previous extortion campaigns have seen groups using a similar tactic of small DDoS attacks to prove they have some capability and lend credibility to their threats; however, the full capabilities of the group behind the most recent demands is unclear.
It is possible that the group is simply looking for easy blackmail targets following the recent $1.1 million dollar ransom payment that was made by South Korean web hosting firm Nayana. Researchers had previously speculated that the large ransom payment could lead to more South Korean organizations being targeted.

Other trending cybercrime events from the week include:
- Attackers target government: Dozens of email accounts belonging to members of parliament and peers were breached during “a sustained and determined attack on all parliamentary user accounts in an attempt to identify weak passwords.” A hacker going by the name “Vigilance” said that he gained access to 23 state of Minnesota databases and was able to steal 1,400 email addresses and some corresponding “weakly encrypted” passwords. The hacker then published the information in protest of the police officer charged with killing Philando Castile being found not guilty. Multiple government websites were defaced with pro-ISIS propaganda and a logo saying the hack was carried out by “Team System DZ.”
- Organizations expose more data: The personal information of 2,200 Aetna customers in Ohio and Texas was compromised due to their data being “inappropriately available for a period of time.” Corpus Christi Independent School District said that it is notifying 6,100 individuals that employee names and Social Security numbers from late 2016 through early 2017 were inadvertently made visible online. The Campbell River School District is warning parents and guardians of Timberline Secondary students that their personal information may have been “inappropriately accessed” due to a file being left on a shared drive that students and staff could access. Users of the UK government’s data dashboard, data.gov.uk, were asked to change their passwords after a file containing their names, email addresses, and hashed passwords was left publicly accessible on a third-party system.
- Disgruntled employees harm employers: A Pennsylvania man has been sentenced to one year and one day in prison for hacking and damaging the IT networks of several water utility providers across the U.S. East Coast. A disgruntled employee led to a breach of Professional Counseling and Medical Associates’ electronic health records system. The FBI said a former employee of Transformations Autism Treatment Center tried to hack into the company’s computer system and steal the personal information of autistic children.
- Other notable incidents: Internet radio service 8tracks said that a copy of its user database has been leaked, including usernames, email addresses, and SHA1-hashed passwords. The full leaked dataset includes around 18 million accounts. Information security consultant Paul Moore reported a data breach involving Kerv after he received both an email from an “anonymous” Kerv user that “had inside information which wouldn’t otherwise be available” and admin credentials from a Tor address. Acting State Supreme Court Justice Lori Sattler told police that she was scammed out of $1,057,500 when she responded to an email impersonating her real estate lawyer and wired the money to an account at the Commerce Bank of China. Two men who are suspected to be part of an international group that hacked into Microsoft’s network in early 2017 have been arrested by British police.
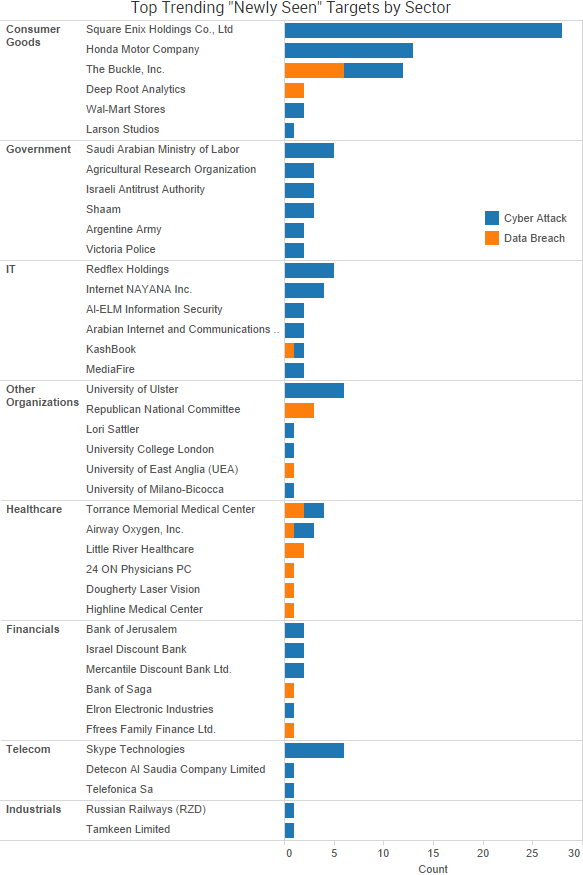
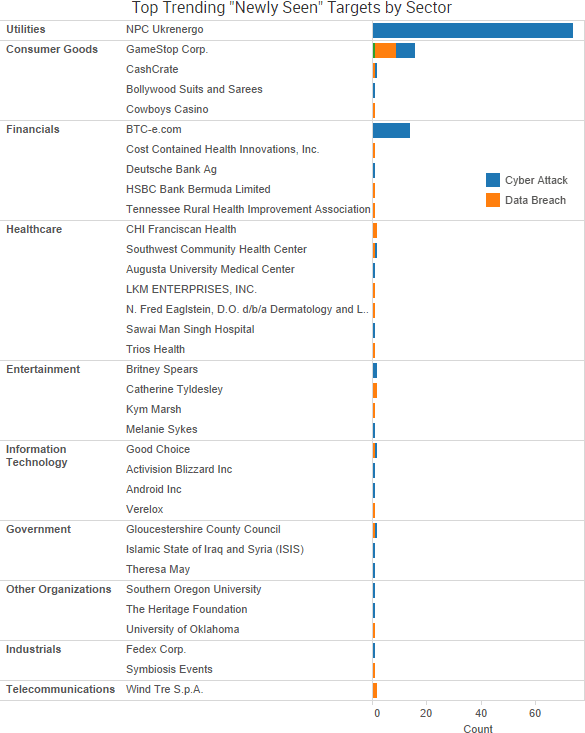
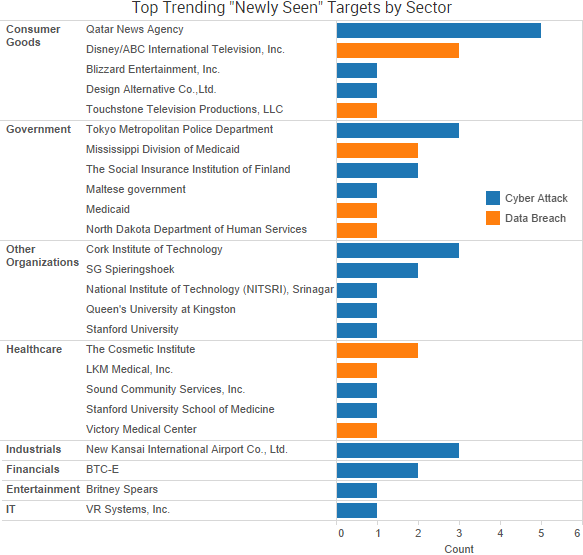
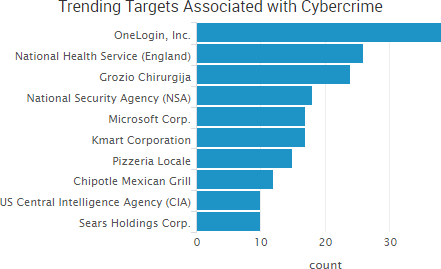
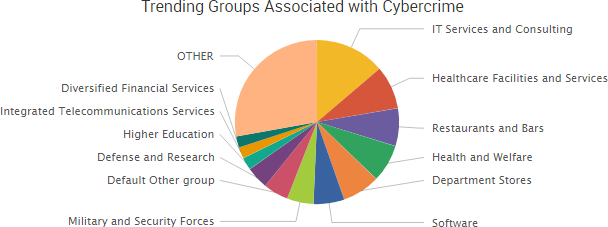
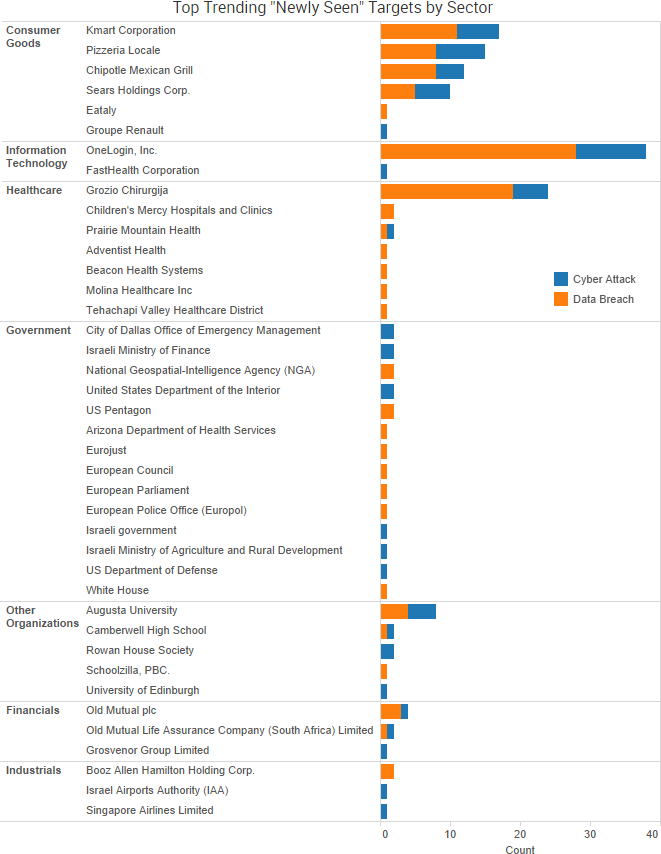
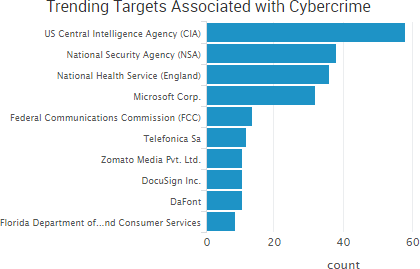
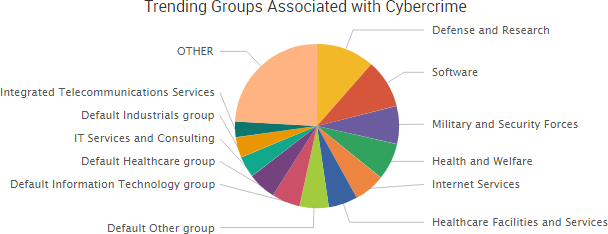
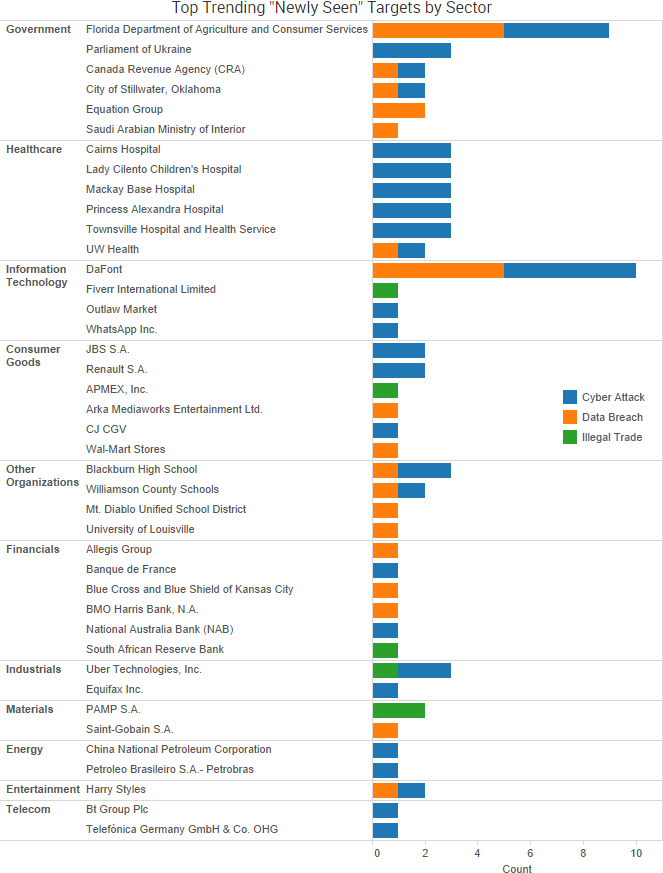
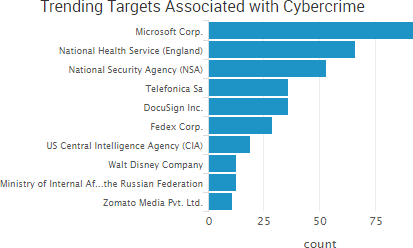
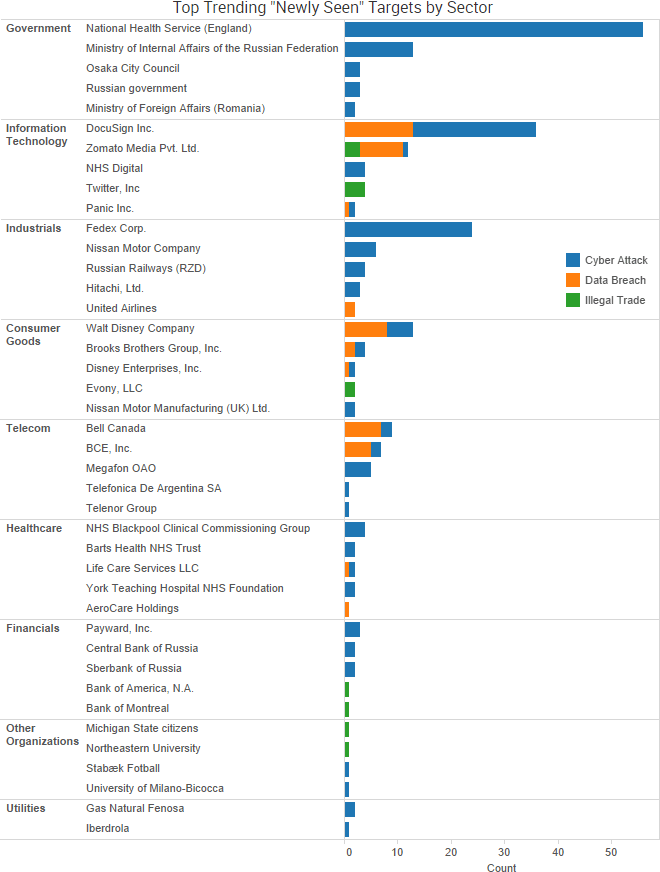
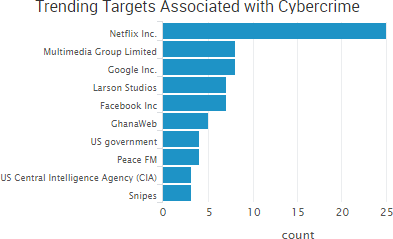
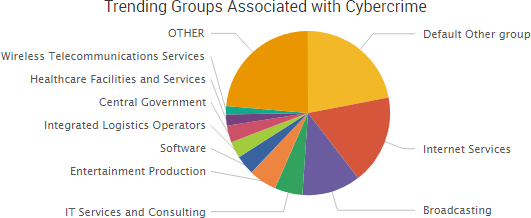
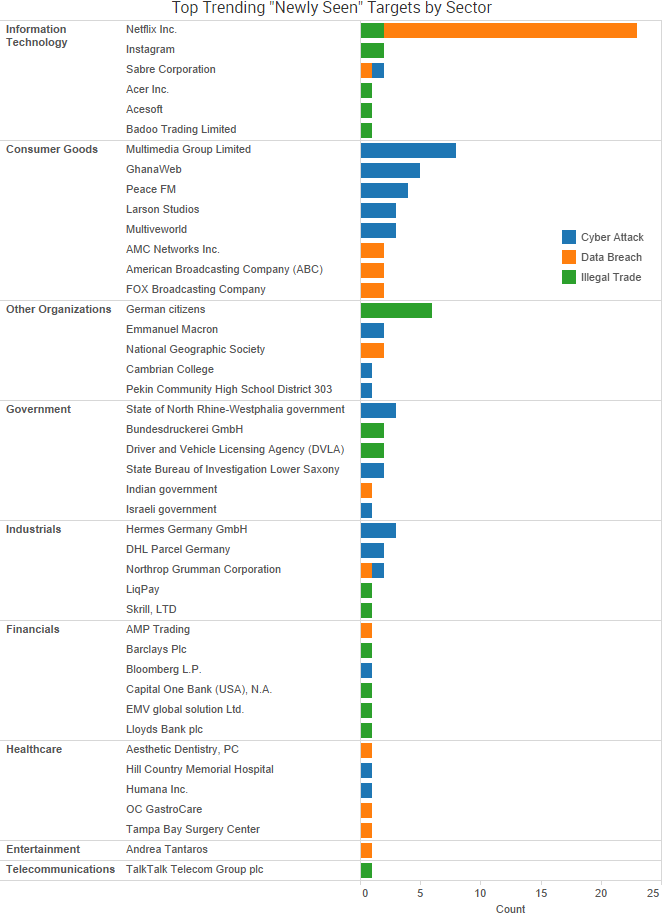
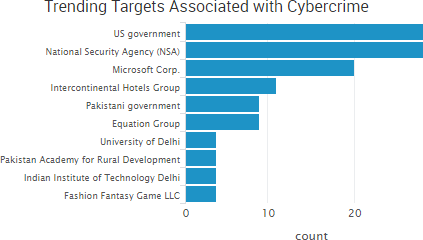
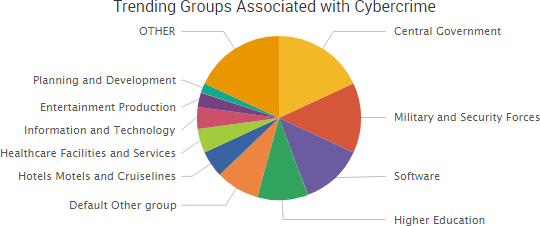
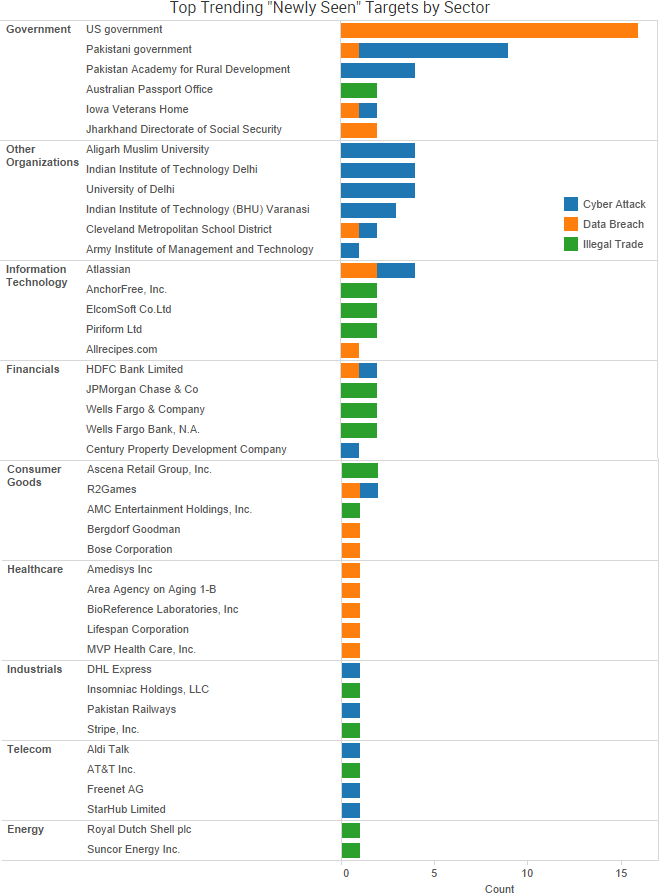
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of those “newly seen” targets, meaning they either appeared in SurfWatch Labs’ data for the first time or else reappeared after being absent for several weeks, are shown in the chart below.

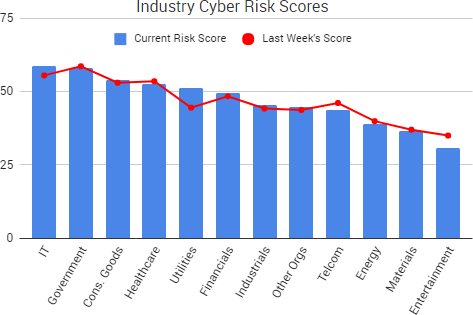
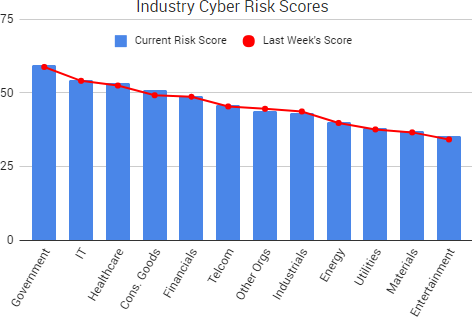
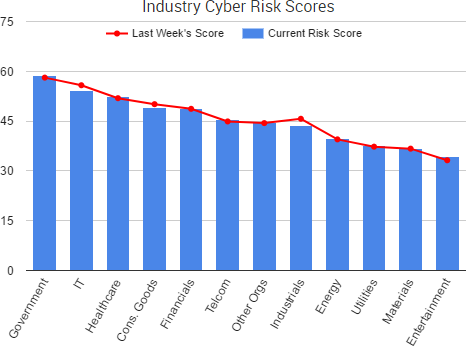
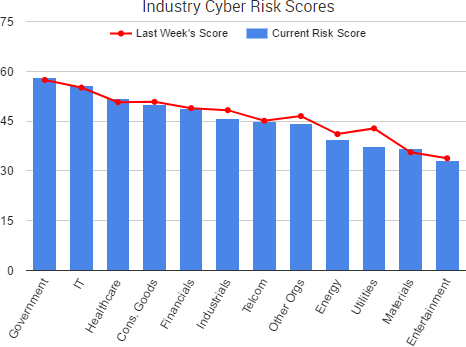
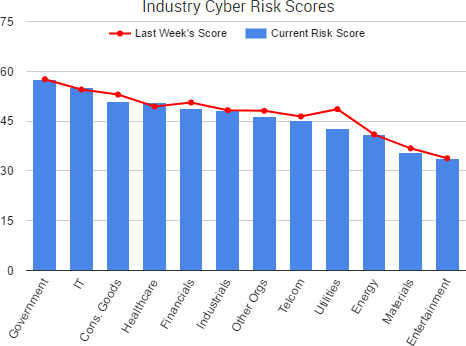
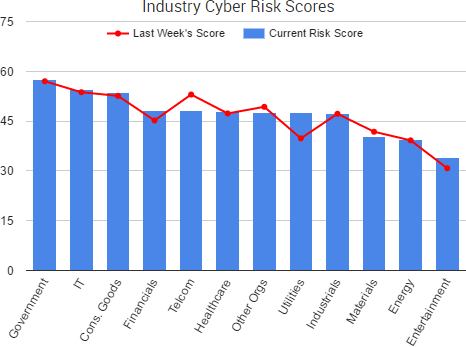
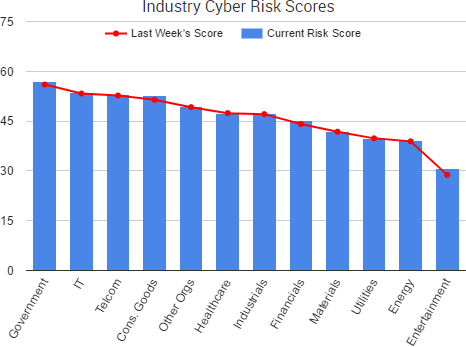
Cyber Risk Trends From the Past Week
 One of the biggest stories that occurred last week was the spread of a ransomware/wiper malware known as NotPetya.
One of the biggest stories that occurred last week was the spread of a ransomware/wiper malware known as NotPetya.
The outbreak was similar to May’s quick spread of the WannaCry ransomware, and those that were infected across the Ukraine, the UK, the Netherlands, India, Spain, Denmark, and elsewhere were shown a ransom demand asking for $300 in bitcoin along with contact details. However, various researchers quickly concluded that the intention behind the attack was likely disruption, not monetary gain.
Previous versions of similar ransomware like Petya used a personal infection ID that contained crucial information for the key recovery, Kaspersky explained in its analysis. However, the NotPetya malware uses randomly generated data in place of that personal key. That means that the attackers have little hope of actually recovering their data, even if they wanted to do so.
As Ars Technica noted, other researchers have come to similar conclusions about NotPetya. Matt Suiche of Comae Technologies concluded that the ransomware aspect of NotPetya may a have been a front to push the media narrative towards the attacker being an unknown cybercriminal group rather than a nation-state attacker with data destruction in mind.
The head of the Center for Cyber Protection within Ukraine’s State Service for Special Communications and Information Protection agreed with that assessment, saying “I think this [NotPetya malware] was directed at us” and that the event was definitely not a criminal attack, but likely a state-sponsored one carrying over from Ukraine’s ongoing cyberwar with Russia. That theory is not confirmed, but as SurfWatch Labs noted, “strong evidence points to the attack beginning with the hacking of the Ukrainian accounting software MeDoc where the automatic update feature was used to download the worm.”
Ukraine’s security service SBU announced that a number of international organizations are helping to investigate the NotPetya attacks and identify the culprits, so more information about the attacks will likely be announced in the near future.


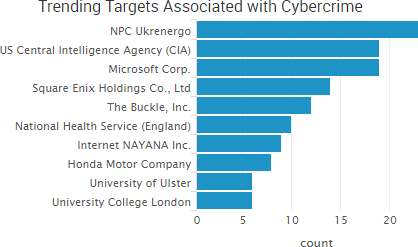
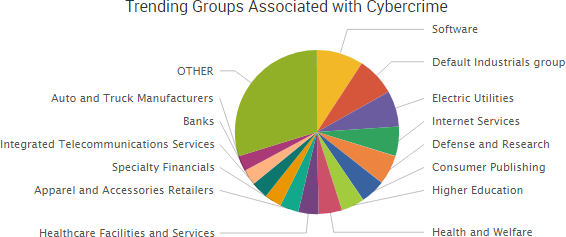
 Larson Studios, the family-owned audio post-production business that was hacked by TheDarkOverlord, has finally provided public comments about the December 2016 attack that led to the theft of a variety of unaired episodes from major studios. That incident led to leak of ten episodes of Netflix’s
Larson Studios, the family-owned audio post-production business that was hacked by TheDarkOverlord, has finally provided public comments about the December 2016 attack that led to the theft of a variety of unaired episodes from major studios. That incident led to leak of ten episodes of Netflix’s 


 New York’s attorney general Eric Schneiderman announced last Thursday that
New York’s attorney general Eric Schneiderman announced last Thursday that 
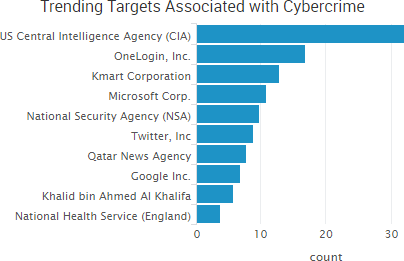
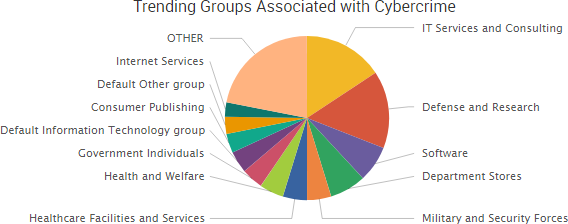
 Recent incidents have confirmed that malicious actors are using cyber-attacks and data leaks to both blatantly fabricate entire news stories and discreetly drop small pieces of fake information that can potentially have wide-reaching geopolitical implications.
Recent incidents have confirmed that malicious actors are using cyber-attacks and data leaks to both blatantly fabricate entire news stories and discreetly drop small pieces of fake information that can potentially have wide-reaching geopolitical implications.
 TheShadowBrokers continued to make headlines over its
TheShadowBrokers continued to make headlines over its 
 It is now less than one year until the EU General Data Protection Regulation (GDPR) goes into effect, yet some organizations are either unaware of the upcoming privacy changes or believe they will have issues meeting next year’s deadline, according to recent research.
It is now less than one year until the EU General Data Protection Regulation (GDPR) goes into effect, yet some organizations are either unaware of the upcoming privacy changes or believe they will have issues meeting next year’s deadline, according to recent research. 

 As WannaCry continues to dominate cybercrime news, the past week saw even more leaks of government-created malware and promises of additional leaks to come in the future. WikiLeaks has continued to dump files allegedly stolen from the CIA, and TheShadowBrokers group has announced a new monthly service providing various data dumps and exploits to its customers.
As WannaCry continues to dominate cybercrime news, the past week saw even more leaks of government-created malware and promises of additional leaks to come in the future. WikiLeaks has continued to dump files allegedly stolen from the CIA, and TheShadowBrokers group has announced a new monthly service providing various data dumps and exploits to its customers.
 By Saturday researchers reported more than
By Saturday researchers reported more than 

 On Thursday, President Donald Trump issued an
On Thursday, President Donald Trump issued an 
 Several recent cybercrime events have proven that although two-factor authentication is an effective way to prevent fraudulent transactions, malicious actors are focusing their efforts on ways to defeat that increasingly popular layer of security.
Several recent cybercrime events have proven that although two-factor authentication is an effective way to prevent fraudulent transactions, malicious actors are focusing their efforts on ways to defeat that increasingly popular layer of security.
 Facebook and Google confirmed this week that they were the victims of the $100 million phishing scheme announced by the Department of Justice of
Facebook and Google confirmed this week that they were the victims of the $100 million phishing scheme announced by the Department of Justice of